系统 : Windows xp
程序 : cytom!c's
程序下载地址 :http://pan.baidu.com/s/1nulAYBv
要求 : 伪造KeyFile
使用工具 :IDA & OD & Hex Workshop
可在看雪论坛中查找关于此程序的破文:http://bbs.pediy.com/showthread.php?t=30229
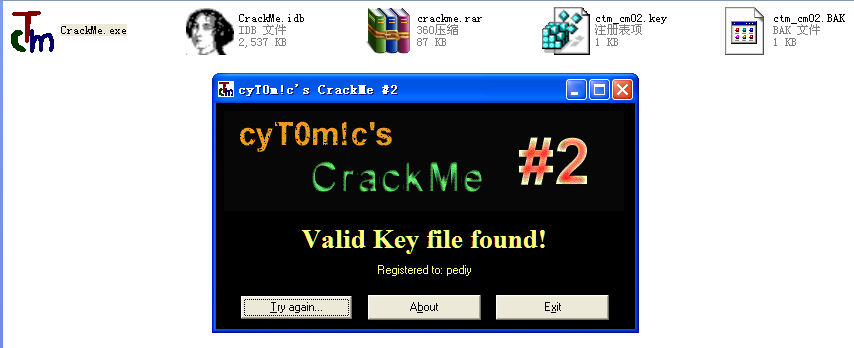
IDA载入程序,找出提示破解成功的字串“Valid Key file found!”并定位关键代码:
00426572 . BA 4C674200 mov edx, 0042674C ; ASCII "ctm_cm02.key"
00426577 . 8D85 A8FEFEFF lea eax, dword ptr [ebp+FFFEFEA8]
0042657D . E8 3FD8FDFF call 00403DC1
00426582 . BA 01000000 mov edx, 1
00426587 . 8D85 A8FEFEFF lea eax, dword ptr [ebp+FFFEFEA8]
0042658D . E8 1EDCFDFF call 004041B0
00426592 . E8 4DC1FDFF call 004026E4
00426597 . 85C0 test eax, eax
00426599 . 0F85 66010000 jnz 00426705
0042659F . 8D85 A8FEFEFF lea eax, dword ptr [ebp+FFFEFEA8]
004265A5 . E8 5AD9FDFF call 00403F04 ; CreateFile,并获取长度
004265AA . E8 F9C0FDFF call 004026A8
004265AF . 8945 FC mov dword ptr [ebp-4], eax
004265B2 . 837D FC 00 cmp dword ptr [ebp-4], 0 ; 长度为0?
004265B6 . 75 15 jnz short 004265CD
004265B8 . BA 64674200 mov edx, 00426764 ; ASCII "Key file is empty!"
004265BD . 8B83 B0010000 mov eax, dword ptr [ebx+1B0]
004265C3 . E8 CCB6FEFF call 00411C94
004265C8 . E9 28010000 jmp 004266F5
004265CD > 817D FC 00000>cmp dword ptr [ebp-4], 10000 ; UNICODE "#envTSLOGsss1964=1032992"
004265D4 . 7E 07 jle short 004265DD
004265D6 . C745 FC 00000>mov dword ptr [ebp-4], 10000 ; UNICODE "#envTSLOGsss1964=1032992"
004265DD > 6A 00 push 0
004265DF . 8D95 FCFFFEFF lea edx, dword ptr [ebp+FFFEFFFC]
004265E5 . 8B4D FC mov ecx, dword ptr [ebp-4]
004265E8 . 8D85 A8FEFEFF lea eax, dword ptr [ebp+FFFEFEA8]
004265EE . E8 71D8FDFF call 00403E64 ; 读取文件内容
004265F3 . E8 B0C0FDFF call 004026A8
004265F8 . 53 push ebx
004265F9 . 57 push edi
004265FA . 56 push esi
004265FB . 8D75 FC lea esi, dword ptr [ebp-4]
004265FE . 8B0E mov ecx, dword ptr [esi]
00426600 . 8DB5 FCFFFEFF lea esi, dword ptr [ebp+FFFEFFFC]
00426606 . 8DBD FBFFFEFF lea edi, dword ptr [ebp+FFFEFFFB]
0042660C . 31C0 xor eax, eax
0042660E . 83CA FF or edx, FFFFFFFF
00426611 . 31DB xor ebx, ebx
00426613 . 40 inc eax ; eax = 1
00426614 . F7D2 not edx
00426616 > 8A1C16 mov bl, byte ptr [esi+edx] ; 迭代字串
00426619 . 84DB test bl, bl ; 字符值为0x0?
0042661B . 74 29 je short 00426646 ; 结尾字节设置为0x0才能跳转正确流程
0042661D . E8 16000000 call 00426638 ; 将文件内容写入一段内存
00426622 . 52 push edx
00426623 . F7E3 mul ebx ; eax * 字符值
00426625 . 5A pop edx
00426626 . 35 326D5463 xor eax, 63546D32 ; eax 再进行异或
0042662B . FEC2 inc dl ; 循环变量自增
0042662D . 39CA cmp edx, ecx ; 迭代完毕?
0042662F . 74 42 je short 00426673
00426631 . 80FA FF cmp dl, 0FF ; 迭代了255次?
00426634 . 74 3D je short 00426673
00426636 .^ EB DE jmp short 00426616
00426638 /$ 57 push edi
00426639 |. 8DBD F4FFFEFF lea edi, dword ptr [ebp+FFFEFFF4]
0042663F |. 8B3F mov edi, dword ptr [edi]
00426641 |. 881C17 mov byte ptr [edi+edx], bl
00426644 |. 5F pop edi
00426645 . C3 retn
00426646 > E8 EDFFFFFF call 00426638
0042664B . 42 inc edx ; 0x0结尾后还要加上4个字节才能跳转正确流程
0042664C . 83C2 04 add edx, 4
0042664F . 39D1 cmp ecx, edx
00426651 . 75 20 jnz short 00426673
00426653 . 83EA 04 sub edx, 4 ; 还原循环变量
00426656 . 85C0 test eax, eax
00426658 . 76 02 jbe short 0042665C
0042665A . D1E8 shr eax, 1
0042665C > 3B0416 cmp eax, dword ptr [esi+edx] ; 与最后的4个字节进行对比
0042665F . 75 09 jnz short 0042666A
00426661 . B8 00000000 mov eax, 0
00426666 . 8907 mov dword ptr [edi], eax
00426668 . EB 10 jmp short 0042667A
0042666A > B8 01000000 mov eax, 1
0042666F . 8907 mov dword ptr [edi], eax
00426671 . EB 07 jmp short 0042667A
00426673 > B8 02000000 mov eax, 2
00426678 . 8907 mov dword ptr [edi], eax
0042667A > 5E pop esi
0042667B . 5F pop edi
0042667C . 5B pop ebx
0042667D . 8A85 FBFFFEFF mov al, byte ptr [ebp+FFFEFFFB]
00426683 . 2C 01 sub al, 1 ; Switch (cases 0..2)
00426685 . 72 08 jb short 0042668F
00426687 . 74 4A je short 004266D3
00426689 . FEC8 dec al
0042668B . 74 58 je short 004266E5
0042668D . EB 66 jmp short 004266F5
0042668F > BA 80674200 mov edx, 00426780 ; ASCII "Valid Key file found!"; Case 0 of switch 00426683
00426694 . 8B83 B0010000 mov eax, dword ptr [ebx+1B0]
0042669A . E8 F5B5FEFF call 00411C94
0042669F . BA A0674200 mov edx, 004267A0 ; ASCII "Registered to: "
004266A4 . 8D85 A4FEFEFF lea eax, dword ptr [ebp+FFFEFEA4]
004266AA . E8 05CCFDFF call 004032B4
004266AF . 8D85 A4FEFEFF lea eax, dword ptr [ebp+FFFEFEA4]
004266B5 . 8B95 F4FFFEFF mov edx, dword ptr [ebp+FFFEFFF4]
004266BB . E8 DCCCFDFF call 0040339C
004266C0 . 8B95 A4FEFEFF mov edx, dword ptr [ebp+FFFEFEA4]
004266C6 . 8B83 C0010000 mov eax, dword ptr [ebx+1C0]
004266CC . E8 C3B5FEFF call 00411C94
004266D1 . EB 22 jmp short 004266F5
004266D3 > BA B8674200 mov edx, 004267B8 ; ASCII "Key file contains wrong serial!"; Case 1 of switch 00426683
004266D8 . 8B83 B0010000 mov eax, dword ptr [ebx+1B0]
004266DE . E8 B1B5FEFF call 00411C94
004266E3 . EB 10 jmp short 004266F5
004266E5 > BA E0674200 mov edx, 004267E0 ; ASCII "Key file is not valid!"; Case 2 of switch 00426683
004266EA . 8B83 B0010000 mov eax, dword ptr [ebx+1B0]
004266F0 . E8 9FB5FEFF call 00411C94
004266F5 > 8D85 A8FEFEFF lea eax, dword ptr [ebp+FFFEFEA8] ; Default case of switch 00426683
总结算法:
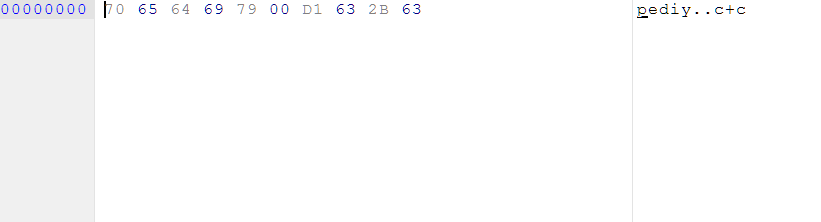
1.KeyFile文件名应为“ctm_cm02.key”.
2.KeyFile以用户名开头,用0x0作为用户名的结束符号。若是文件内容为空或者用户名没有用0x0作为结尾,则失败。
3.迭代用户名字串并根据字串的内容生成一个值,将该值与0x0之后的四个字节的数据进行比对,如果相同,则KeyFIle是有效的。
如果用户名为“pediy”,那么相对应的KeyFile内容应该是:
运行效果: