实验任务1:ospf单区域配置
略
实验任务2:ospf多区域配置
1.建立物理连接
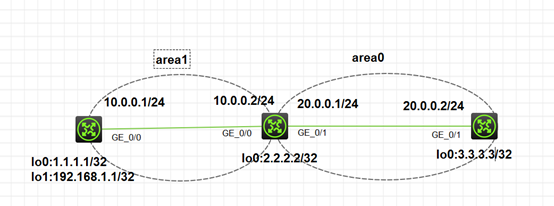
2.RTA,RTB,RTC运行ospf
[RTA-ospf-1-area-0.0.0.1]network 1.1.1.1 0.0.0.0
[RTA-ospf-1-area-0.0.0.1]network 10.0.0.0 0.0.0.255
[RTB-ospf-1-area-0.0.0.1]network 10.0.0.0 0.0.0.255
[RTB-ospf-1-area-0.0.0.0]network 2.2.2.2 0.0.0.0
[RTB-ospf-1-area-0.0.0.0]network 20.0.0.0 0.0.0.255
[RTC-ospf-1-area-0.0.0.0]network 20.0.0.0 0.0.0.255
[RTC-ospf-1-area-0.0.0.0]network 3.3.3.3 0.0.0.0
注:一般loopback接口宣告在骨干区域area0上
实验任务3:router id的选举
-
多个loopback口存在的时候,查看router id
[RTB]display ospf peerOSPF Process 1 with Router ID 2.2.2.2 Neighbor Brief Information
Area: 0.0.0.0
Router ID Address Pri Dead-Time State Interface
3.3.3.3 20.0.0.2 1 32 Full/DR GE0/1
Area: 0.0.0.1
Router ID Address Pri Dead-Time State Interface
192.168.1.1 10.0.0.1 1 35 Full/DR GE0/0
选举最大的ip地址做router id。
2.取消的了RTA的loopback1接口,查看ospf邻居表
[RTB]display ospf peer
OSPF Process 1 with Router ID 2.2.2.2
Neighbor Brief Information
Area: 0.0.0.0
Router ID Address Pri Dead-Time State Interface
3.3.3.3 20.0.0.2 1 31 Full/DR GE0/1
Area: 0.0.0.1
Router ID Address Pri Dead-Time State Interface
192.168.1.1 10.0.0.1 1 35 Full/DR GE0/0
RTA的router id没有变化
3.重启ospf进程
[RTB]display ospf peer
OSPF Process 1 with Router ID 2.2.2.2
Neighbor Brief Information
Area: 0.0.0.0
Router ID Address Pri Dead-Time State Interface
3.3.3.3 20.0.0.2 1 38 Full/DR GE0/1
Area: 0.0.0.1
Router ID Address Pri Dead-Time State Interface
1.1.1.1 10.0.0.1 1 33 Full/BDR GE0/0
一旦选举了router id,只有重启ospf进程才能重新选举router id