一.查壳
jeb载入发现没有代码,怀疑加壳

用查壳工具查壳 (爱加密)

apktool解包

得到其
package name: loading.androidmanual
main activity name: .BeginningActivity
二.调试启动APP
安装APK到AVD模拟器
配置好IDA调试so环境(略过)
调试启动
adb shell am start -D -n 包名/包名+类名
adb shell am start -D -W -n loading.androidmanual/loading.androidmanual.BeginningActivity

设置调试模式
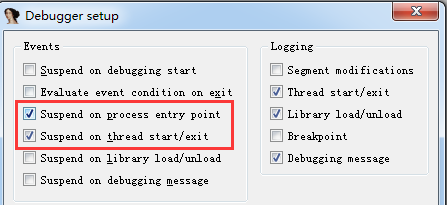
记录下ID为506,附加上调试器

在libdvm.so中找到dvmDexFileOpenPartial.....
并在函数头部下好断点 F9运行起来

设置jdb调试,执行后程序断下来


此时寄存器R0为dex文件的起始地址,R1为大小

R0 = 0x4C38E7B4
R1 = 0x000FAEB4
内存窗口可以清楚的看到文件头

三.dump dex file
IDA->File->scrpit command在弹出的对话框中粘贴我们的dump脚本
Message("start dump ");
auto fp,dex_addr,addr_begin,data_len,addr_end;
addr_begin=0x4C38E7B4;
data_len=0x000FAEB4;
addr_end=addr_begin+data_len;
fp=fopen("D:\dump.dex","wb");
for (dex_addr=addr_begin;dex_addr < addr_end;dex_addr++)
{
fputc(Byte(dex_addr),fp);
}
Message("end dump ");
运行脚本文件

脚本运行完毕后会在指定目录生成dump.dex文件

在用JEB打开就可以分析dex文件了
