环境
docker-ce-19.03.1-3.el7.x86_64
centos 7
一、Docker管理工具 (官方三剑客)
1、Docker Machine(学习的Openstack Heat)
Create Docker Machine主要包括三个Create过程。
(1)首先是Provider Create(libmachine/provider.go),此函数主要是在当前运行docker-machine命令主机上创建以machine name命名的文件夹,并将根证书,服务器证书以及用户证书拷贝到此文件夹。
(2)其次是Driver create(例如drivers/virtualbox/virtualbox.go)用来创建主机,
(3)最后是运行Host create(libmachine/host.go)通过SSH安装并配置Docker。目前在本地环境中使用的是boot2docker镜像,云端环境使用的是Ubuntu镜像。
其实真相是这样的:自动创建一个虚机并且安装好设置好Docker Engine.
作用:
(1)Docker Machine简化了部署的复杂度,无论是在本机的虚拟机上还是在公有云平台,只需要一条命令便可搭建好Docker主机
(2)Docker Machine提供了多平台多Docker主机的集中管理
(3)Docker Machine 使应用由本地迁移到云端变得简单,只需要修改一下环境变量即可和任意Docker主机通信部署应用
2、Swarm作为一个管理Docker集群的工具,可以单独部署于一个节点。 (抄Kubernetes)
Swarm的具体工作流程:Docker Client发送请求给Swarm;
Swarm处理请求并发送至相应的Docker Node;
Docker Node执行相应的操作并返回响应。
在某些点, Swarm将可以在主机故障时重调度容器.
Swarm可以很好地与第三方容器编配产品和运供应商提供的编配服务整合,如Mesos
3、Docker Compose (抄Kubernetes)
将所管理的容器分为三层,工程(project),服务(service)以及容器(contaienr)。
一个工程当中可包含多个服务,每个服务中定义了容器运行的镜像,参数,依赖。一个服务当中可包括多个容
器实例,Docker Compose并没有解决负载均衡的问题,因此需要借助其他工具实现服务发现及负载均衡。
Docker Compose中定义构建的镜像只存在在一台Docker Swarm主机上,无法做到多主机共享
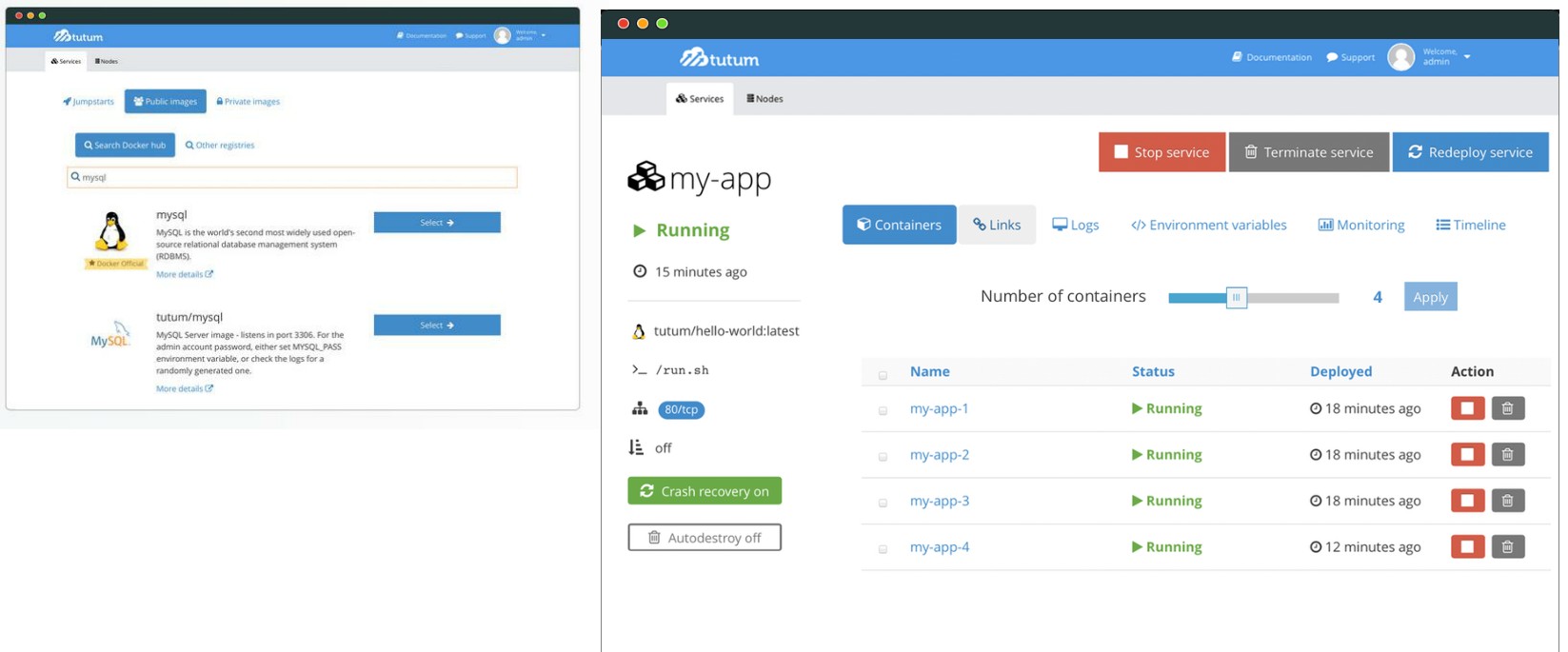
二、Tutum(收费的)
三、Shipyard入门(开源,可用于生产)
Shipyard 是一个基于 Web 的 Docker 管理工具,支持多 host,可以把多个 Docker host 上的 containers 统一管理;可以查看 images,甚至 build images;并提供 RESTful API 等等。
Shipyard 要管理和控制 Docker host 的话需要先修改 Docker host 上的默认配置使其支持远程管理。
Shipyard官网已停止了,Githup也不更新了,使用下面脚本来下载和安装:
#!/bin/bash if [ "$1" != "" ] && [ "$1" = "-h" ]; then echo "Shipyard Deploy uses the following environment variables:" echo " ACTION: this is the action to use (deploy, upgrade, node, remove)" echo " DISCOVERY: discovery system used by Swarm (only if using 'node' action)" echo " IMAGE: this overrides the default Shipyard image" echo " PREFIX: prefix for container names" echo " SHIPYARD_ARGS: these are passed to the Shipyard controller container as controller args" echo " TLS_CERT_PATH: path to certs to enable TLS for Shipyard" echo " PORT: specify the listen port for the controller (default: 8080)" echo " IP: specify the address at which the controller or node will be available (default: eth0 ip)" echo " PROXY_PORT: port to run docker proxy (default: 2375)" exit 1 fi if [ -z "`which docker`" ]; then echo "You must have the Docker CLI installed on your $PATH" echo " See http://docs.docker.com for details" exit 1 fi ACTION=${ACTION:-deploy} IMAGE=${IMAGE:-dockerclub/shipyard:latest} PREFIX=${PREFIX:-shipyard} SHIPYARD_ARGS=${SHIPYARD_ARGS:-""} TLS_CERT_PATH=${TLS_CERT_PATH:-} CERT_PATH="/etc/shipyard" PROXY_PORT=${PROXY_PORT:-2376} SWARM_PORT=3375 SHIPYARD_PROTOCOL=http SHIPYARD_PORT=${PORT:-8080} SHIPYARD_IP=${IP} DISCOVERY_BACKEND=etcd DISCOVERY_PORT=4001 DISCOVERY_PEER_PORT=7001 ENABLE_TLS=0 CERT_FINGERPRINT="" LOCAL_CA_CERT="" LOCAL_SSL_CERT="" LOCAL_SSL_KEY="" LOCAL_SSL_CLIENT_CERT="" LOCAL_SSL_CLIENT_KEY="" SSL_CA_CERT="" SSL_CERT="" SSL_KEY="" SSL_CLIENT_CERT="" SSL_CLIENT_KEY="" show_cert_help() { echo "To use TLS in Shipyard, you must have existing certificates." echo "The certs must be named ca.pem, server.pem, server-key.pem, cert.pem and key.pem" echo "If you need to generate certificates, see https://github.com/ehazlett/certm for examples." } check_certs() { if [ -z "$TLS_CERT_PATH" ]; then return fi if [ ! -e $TLS_CERT_PATH ]; then echo "Error: unable to find certificates in $TLS_CERT_PATH" show_cert_help exit 1 fi if [ "$PROXY_PORT" = "2375" ]; then PROXY_PORT=2376 fi SWARM_PORT=3376 SHIPYARD_PROTOCOL=https LOCAL_SSL_CA_CERT="$TLS_CERT_PATH/ca.pem" LOCAL_SSL_CERT="$TLS_CERT_PATH/server.pem" LOCAL_SSL_KEY="$TLS_CERT_PATH/server-key.pem" LOCAL_SSL_CLIENT_CERT="$TLS_CERT_PATH/cert.pem" LOCAL_SSL_CLIENT_KEY="$TLS_CERT_PATH/key.pem" SSL_CA_CERT="$CERT_PATH/ca.pem" SSL_CERT="$CERT_PATH/server.pem" SSL_KEY="$CERT_PATH/server-key.pem" SSL_CLIENT_CERT="$CERT_PATH/cert.pem" SSL_CLIENT_KEY="$CERT_PATH/key.pem" CERT_FINGERPRINT=$(openssl x509 -noout -in $LOCAL_SSL_CERT -fingerprint -sha256 | awk -F= '{print $2;}') if [ ! -e $LOCAL_SSL_CA_CERT ] || [ ! -e $LOCAL_SSL_CERT ] || [ ! -e $LOCAL_SSL_KEY ] || [ ! -e $LOCAL_SSL_CLIENT_CERT ] || [ ! -e $LOCAL_SSL_CLIENT_KEY ]; then echo "Error: unable to find certificates" show_cert_help exit 1 fi ENABLE_TLS=1 } # container functions start_certs() { ID=$(docker run -ti -d --restart=always --name $PREFIX-certs -v $CERT_PATH alpine sh) if [ $ENABLE_TLS = 1 ]; then docker cp $LOCAL_SSL_CA_CERT $PREFIX-certs:$SSL_CA_CERT docker cp $LOCAL_SSL_CERT $PREFIX-certs:$SSL_CERT docker cp $LOCAL_SSL_KEY $PREFIX-certs:$SSL_KEY docker cp $LOCAL_SSL_CLIENT_CERT $PREFIX-certs:$SSL_CLIENT_CERT docker cp $LOCAL_SSL_CLIENT_KEY $PREFIX-certs:$SSL_CLIENT_KEY fi } remove_certs() { docker rm -fv $PREFIX-certs > /dev/null 2>&1 } get_ip() { if [ -z "$SHIPYARD_IP" ]; then SHIPYARD_IP=`docker run --rm --net=host alpine ip route get 8.8.8.8 | awk '{ print $7; }'` fi } start_discovery() { get_ip ID=$(docker run -ti -d -p 4001:4001 -p 7001:7001 --restart=always --name $PREFIX-discovery microbox/etcd:latest -addr $SHIPYARD_IP:$DISCOVERY_PORT -peer-addr $SHIPYARD_IP:$DISCOVERY_PEER_PORT) } remove_discovery() { docker rm -fv $PREFIX-discovery > /dev/null 2>&1 } start_rethinkdb() { ID=$(docker run -ti -d --restart=always --name $PREFIX-rethinkdb rethinkdb) } remove_rethinkdb() { docker rm -fv $PREFIX-rethinkdb > /dev/null 2>&1 } start_proxy() { TLS_OPTS="" if [ $ENABLE_TLS = 1 ]; then TLS_OPTS="-e SSL_CA=$SSL_CA_CERT -e SSL_CERT=$SSL_CERT -e SSL_KEY=$SSL_KEY -e SSL_SKIP_VERIFY=1" fi # Note: we add SSL_SKIP_VERIFY=1 to skip verification of the client # certificate in the proxy image. this will pass it to swarm that # does verify. this helps with performance and avoids certificate issues # when running through the proxy. ultimately if the cert is invalid # swarm will fail to return. ID=$(docker run -ti -d -p $PROXY_PORT:$PROXY_PORT --hostname=$HOSTNAME --restart=always --name $PREFIX-proxy -v /var/run/docker.sock:/var/run/docker.sock -e PORT=$PROXY_PORT --volumes-from=$PREFIX-certs $TLS_OPTS shipyard/docker-proxy:latest) } remove_proxy() { docker rm -fv $PREFIX-proxy > /dev/null 2>&1 } start_swarm_manager() { get_ip TLS_OPTS="" if [ $ENABLE_TLS = 1 ]; then TLS_OPTS="--tlsverify --tlscacert=$SSL_CA_CERT --tlscert=$SSL_CERT --tlskey=$SSL_KEY" fi EXTRA_RUN_OPTS="" if [ -z "$DISCOVERY" ]; then DISCOVERY="$DISCOVERY_BACKEND://discovery:$DISCOVERY_PORT" EXTRA_RUN_OPTS="--link $PREFIX-discovery:discovery" fi ID=$(docker run -ti -d --restart=always --name $PREFIX-swarm-manager --volumes-from=$PREFIX-certs $EXTRA_RUN_OPTS swarm:latest m --replication --addr $SHIPYARD_IP:$SWARM_PORT --host tcp://0.0.0.0:$SWARM_PORT $TLS_OPTS $DISCOVERY) } remove_swarm_manager() { docker rm -fv $PREFIX-swarm-manager > /dev/null 2>&1 } start_swarm_agent() { get_ip if [ -z "$DISCOVERY" ]; then DISCOVERY="$DISCOVERY_BACKEND://discovery:$DISCOVERY_PORT" EXTRA_RUN_OPTS="--link $PREFIX-discovery:discovery" fi ID=$(docker run -ti -d --restart=always --name $PREFIX-swarm-agent $EXTRA_RUN_OPTS swarm:latest j --addr $SHIPYARD_IP:$PROXY_PORT $DISCOVERY) } remove_swarm_agent() { docker rm -fv $PREFIX-swarm-agent > /dev/null 2>&1 } start_controller() { #-v $CERT_PATH:/etc/docker:ro TLS_OPTS="" if [ $ENABLE_TLS = 1 ]; then TLS_OPTS="--tls-ca-cert $SSL_CA_CERT --tls-cert=$SSL_CERT --tls-key=$SSL_KEY --shipyard-tls-ca-cert=$SSL_CA_CERT --shipyard-tls-cert=$SSL_CERT --shipyard-tls-key=$SSL_KEY" fi ID=$(docker run -ti -d --restart=always --name $PREFIX-controller --link $PREFIX-rethinkdb:rethinkdb --link $PREFIX-swarm-manager:swarm -p $SHIPYARD_PORT:$SHIPYARD_PORT --volumes-from=$PREFIX-certs $IMAGE --debug server --listen :$SHIPYARD_PORT -d tcp://swarm:$SWARM_PORT $TLS_OPTS $SHIPYARD_ARGS) } wait_for_available() { set +e IP=$1 PORT=$2 echo Waiting for Shipyard on $IP:$PORT docker pull ehazlett/curl > /dev/null 2>&1 TLS_OPTS="" if [ $ENABLE_TLS = 1 ]; then TLS_OPTS="-k" fi until $(docker run --rm ehazlett/curl --output /dev/null --connect-timeout 1 --silent --head --fail $TLS_OPTS $SHIPYARD_PROTOCOL://$IP:$PORT/ > /dev/null 2>&1); do printf '.' sleep 1 done printf ' ' } remove_controller() { docker rm -fv $PREFIX-controller > /dev/null 2>&1 } if [ "$ACTION" = "deploy" ]; then set -e check_certs get_ip echo "Deploying Shipyard" echo " -> Starting Database" start_rethinkdb echo " -> Starting Discovery" start_discovery echo " -> Starting Cert Volume" start_certs echo " -> Starting Proxy" start_proxy echo " -> Starting Swarm Manager" start_swarm_manager echo " -> Starting Swarm Agent" start_swarm_agent echo " -> Starting Controller" start_controller wait_for_available $SHIPYARD_IP $SHIPYARD_PORT echo "Shipyard available at $SHIPYARD_PROTOCOL://$SHIPYARD_IP:$SHIPYARD_PORT" if [ $ENABLE_TLS = 1 ] && [ ! -z "$CERT_FINGERPRINT" ]; then echo "SSL SHA-256 Fingerprint: $CERT_FINGERPRINT" fi echo "Username: admin Password: shipyard" elif [ "$ACTION" = "node" ]; then set -e if [ -z "$DISCOVERY" ]; then echo "You must set the DISCOVERY environment variable" echo "with the discovery system used with Swarm" exit 1 fi check_certs echo "Adding Node" echo " -> Starting Cert Volume" start_certs echo " -> Starting Proxy" start_proxy echo " -> Starting Swarm Manager" start_swarm_manager $DISCOVERY echo " -> Starting Swarm Agent" start_swarm_agent echo "Node added to Swarm: $SHIPYARD_IP" elif [ "$ACTION" = "upgrade" ]; then set -e check_certs get_ip echo "Upgrading Shipyard" echo " -> Pulling $IMAGE" docker pull $IMAGE echo " -> Upgrading Controller" remove_controller start_controller wait_for_available $SHIPYARD_IP $SHIPYARD_PORT echo "Shipyard controller updated" elif [ "$ACTION" = "remove" ]; then # ignore errors set +e echo "Removing Shipyard" echo " -> Removing Database" remove_rethinkdb echo " -> Removing Discovery" remove_discovery echo " -> Removing Cert Volume" remove_certs echo " -> Removing Proxy" remove_proxy echo " -> Removing Swarm Agent" remove_swarm_agent echo " -> Removing Swarm Manager" remove_swarm_manager echo " -> Removing Controller" remove_controller echo "Done" else echo "Unknown action $ACTION" exit 1 fi
将以上脚本保存为deploy文件,并赋予执行权限,然后执行:
[root@node105 ~]# ll total 16 -rw-------. 1 root root 1779 Aug 15 14:39 anaconda-ks.cfg -rwxr-xr-x. 1 root root 10121 Aug 26 09:00 deploy drwxr-xr-x. 5 root root 41 Aug 25 10:16 nginx [root@node105 ~]# chmod +x deploy [root@node105 ~]# ./deploy Deploying Shipyard -> Starting Database -> Starting Discovery -> Starting Cert Volume -> Starting Proxy -> Starting Swarm Manager -> Starting Swarm Agent -> Starting Controller Unable to find image 'dockerclub/shipyard:latest' locally latest: Pulling from dockerclub/shipyard 4d06f2521e4f: Pulling fs layer 64100628847a: Pulling fs layer 36a170440d6d: Pulling fs layer a823ae228c2d: Pulling fs layer a3ed95caeb02: Pulling fs layer a3ed95caeb02: Waiting a823ae228c2d: Waiting 36a170440d6d: Verifying Checksum 36a170440d6d: Download complete 4d06f2521e4f: Verifying Checksum 4d06f2521e4f: Download complete 4d06f2521e4f: Pull complete a3ed95caeb02: Download complete 64100628847a: Verifying Checksum 64100628847a: Download complete a823ae228c2d: Verifying Checksum a823ae228c2d: Download complete 64100628847a: Pull complete 36a170440d6d: Pull complete a823ae228c2d: Pull complete a3ed95caeb02: Pull complete Digest: sha256:bd5ac58c556506012f7788db18fc6fed3bcefb294e469babbeb87ad7ef15e219 Status: Downloaded newer image for dockerclub/shipyard:latest Waiting for Shipyard on 192.168.118.105:8080 Shipyard available at http://192.168.118.105:8080 Username: admin Password: shipyard

参考:
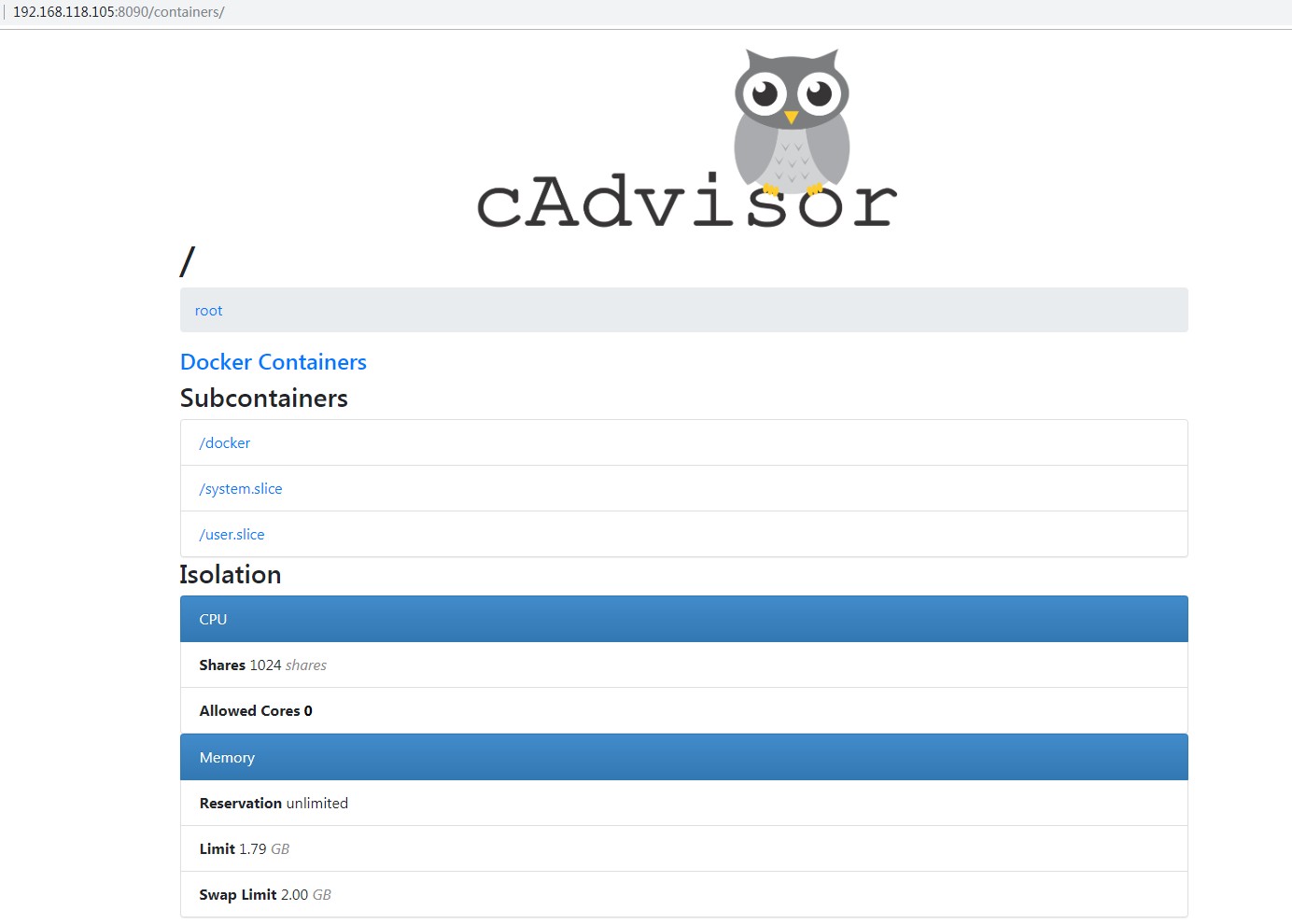
四、cAdvisor入门(google)
四、cAdvisor入门(google)
cAdvisor的监控图默认1秒刷新一次,显示最近一分钟的实时数据,不显示汇聚的和历史数据,也没有阀值告警功能,此外它也无法同时监控多个Docker主机,不过由于其简单方便,并且具备很好的实时性能监控能力,所以适合特殊情况下的性能监控和问题排查。
#拉取cAdvisor镜像
[root@node105 ~]# docker pull docker.io/google/cadvisor
#启动容器
[root@node105 ~]# docker run > --volume=/:/rootfs:ro > --volume=/var/run:/var/run:rw > --volume=/sys:/sys:ro > --volume=/var/lib/docker/:/var/lib/docker:ro > --publish=8090:8080 > --detach=true > --name=cadvisor > google/cadvisor:latest 7e730a8fa6d1ca0a98b471518d508a48d905b10c1418241269f33a9148ba9fb1
参考:
另外:还有portainer、docker ui