1. 部署dashboard
文档:https://www.jianshu.com/p/40c0405811ee
github地址: https://github.com/kubernetes/dashboard/blob/master/aio/deploy/recommended.yaml
1.1 下载部署文件recommended.yaml 并将镜像的地址改为本地镜像的地址
wget https://raw.githubusercontent.com/kubernetes/dashboard/v2.0.3/aio/deploy/recommended.yaml
1.2 下载镜像
docker pull kubernetesui/dashboard:v2.0.3
docker tag kubernetesui/dashboard:v2.0.3 harbor.od.com/k8s/dashboard:v2.0.3
docker push harbor.od.com/k8s/dashboard:v2.0.3
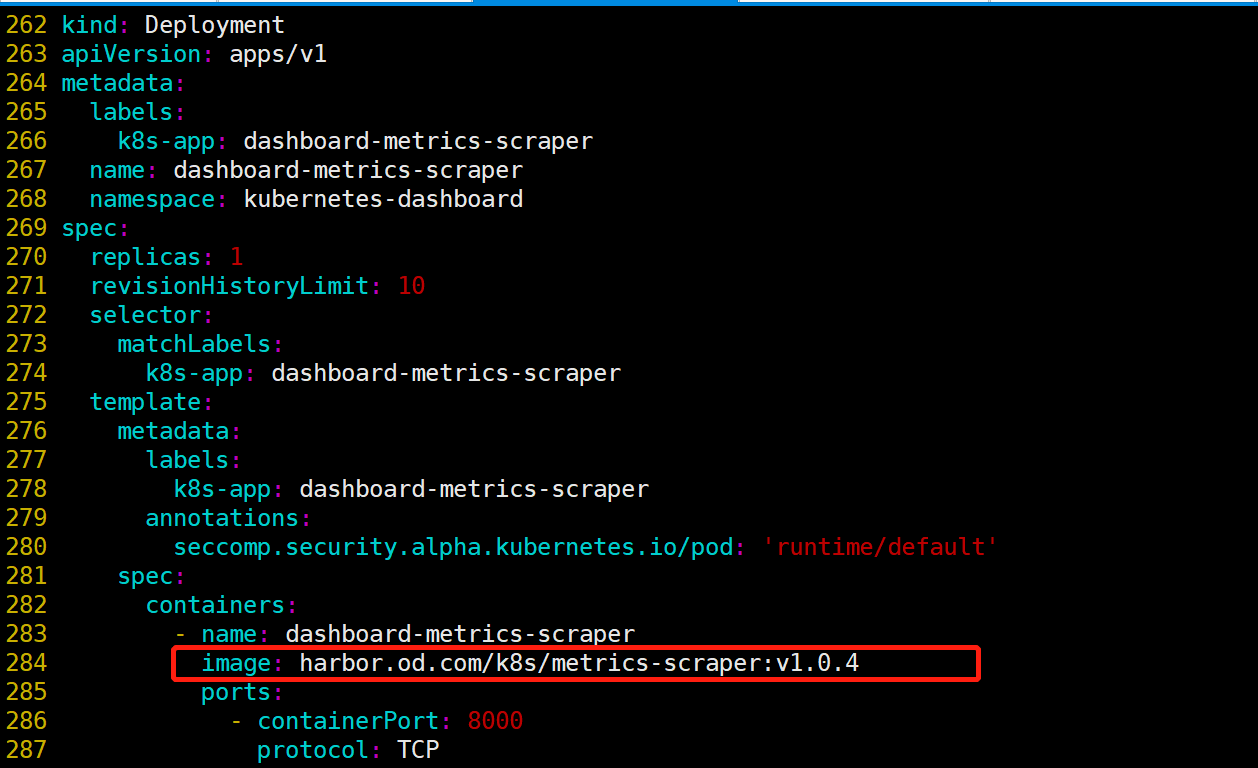
docker pull kubernetesui/metrics-scraper:v1.0.4
docker tag kubernetesui/metrics-scraper:v1.0.4 harbor.od.com/k8s/metrics-scraper:v1.0.4
docker push harbor.od.com/k8s/metrics-scraper:v1.0.4
1.3 修改yaml文件
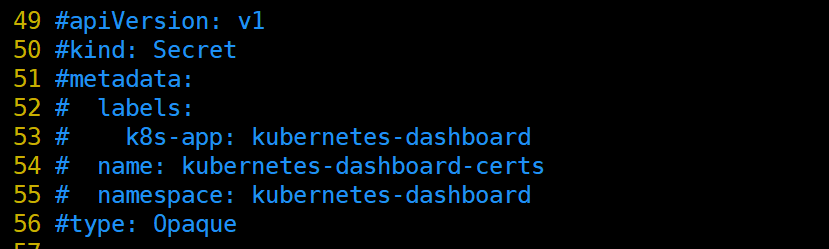
- 注释掉Dashboard Secret ,不然后面访问显示网页不安全,证书过期,我们自己生成证书
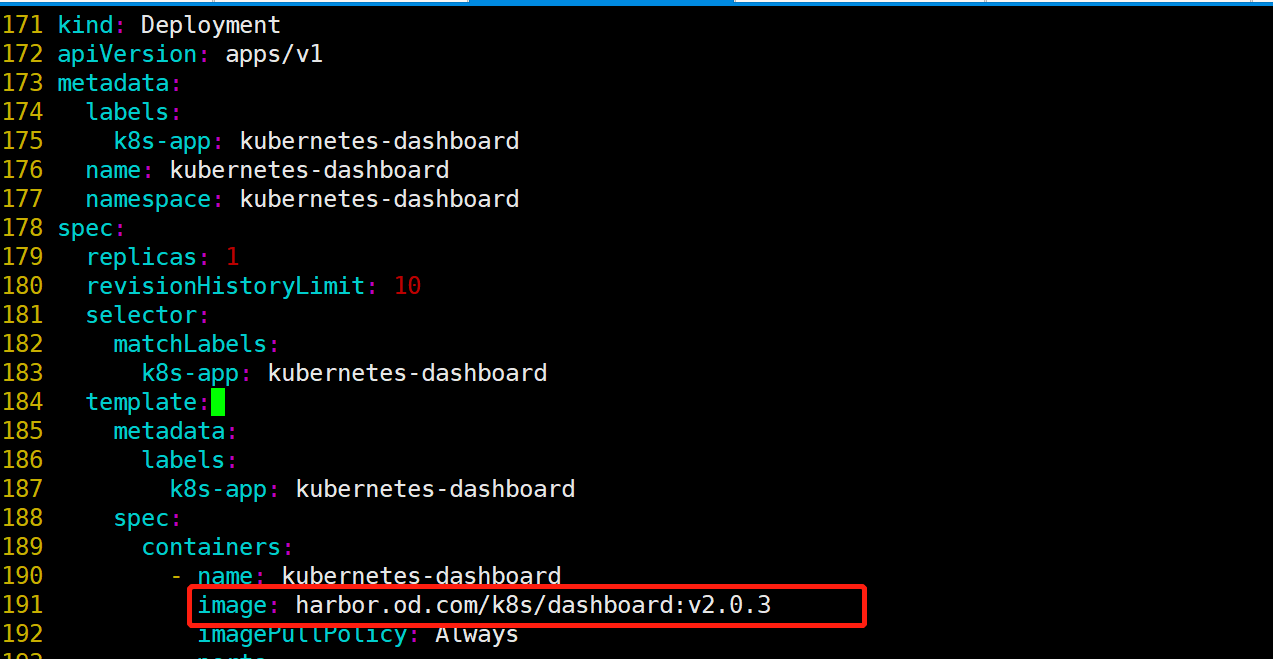
- 将镜像修改为镜像仓库地址
- 添加ingress配置
---
kind: Ingress
apiVersion: extensions/v1beta1
metadata:
name: kubernetes-dashboard-ingress
namespace: kubernetes-dashboard
annotations:
nginx.ingress.kubernetes.io/backend-protocol: HTTPS
spec:
rules:
- host: k8s-dashboard.paic.com.cn
http:
paths:
- path: /
backend:
serviceName: kubernetes-dashboard
servicePort: 443
-
生成新的secret
这里的secret必须在kubernetes-dashboard 名称空间生成, 否则dashboard会起不来, dashboard是启动在kubernetes-dashboard 这个名称空间, 所以secret 也必须在这个空间生成
mkdir key && cd key
openssl genrsa -out dashboard.key 2048
openssl req -new -out dashboard.csr -key dashboard.key -subj '/CN=192.168.31.10'
openssl x509 -req -in dashboard.csr -signkey dashboard.key -out dashboard.crt
kubectl create secret generic kubernetes-dashboard-certs --from-file=dashboard.key --from-file=dashboard.crt -n kubernetes-dashboard
- 部署dashboard
kubectl apply -f recommended.yaml
1.4 设置权限文件
- admin-user.yaml
CopyapiVersion: v1
kind: ServiceAccount
metadata:
name: admin-user
namespace: kube-system
- admin-user-role-binding.yaml
CopyapiVersion: rbac.authorization.k8s.io/v1beta1
kind: ClusterRoleBinding
metadata:
name: admin-user
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: admin-user
namespace: kube-system
- 部署权限文件
kubectl create -f admin-user.yaml
kubectl create -f admin-user-role-binding.yaml
1.5 访问dashboard
-
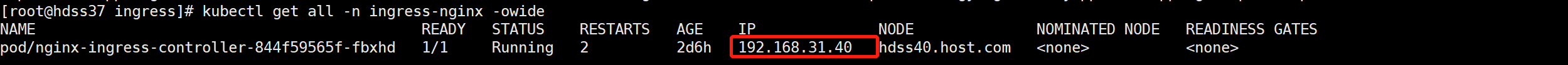
设置本地dns解析
因为dashboard是跑在ingress上, 域名所对应的ip设置成ingress-controller 所在的ip地址
kubectl get all -n ingress-nginx -owide
- 本地配置dns (
C:WindowsSystem32driversetchosts)
192.168.31.40 k8s-dashboard.paic.com.cn
- 访问
k8s-dashboard.paic.com.cn

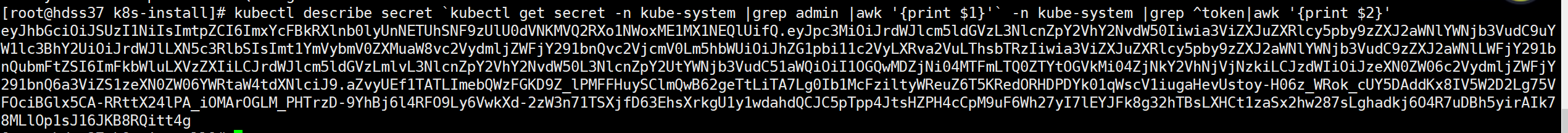
- master 上查看token
kubectl describe secret `kubectl get secret -n kube-system |grep admin |awk '{print $1}'` -n kube-system |grep ^token|awk '{print $2}'
2. dashboard 分权
根据名称空间访问相关资源, 下面的例子是ingress-nginx 和 kubernetes-dashboard的rbac部署文件,
ingress-nginx这里的secret只能在ingress-nginx 这个名称空间访问
kubernetes-dashboard 这里的secret只能在 kubernetes-dashboard 这个名称空间访问
mkdir dashboard-access-sa
cd dashboard-access-sa
2.1 编写部署文件
access-sa.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
name: ingress-nginx-sa
namespace: ingress-nginx
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: kubernetes-dashboard-sa
namespace: kubernetes-dashboard
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: namespace-readonly
rules:
- apiGroups: [""]
resources: ["namespaces"]
verbs: ["get", "list", "watch"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: namespace-readonly
subjects:
- kind: ServiceAccount
name: ingress-nginx-sa
namespace: ingress-nginx
apiGroup: ""
- kind: ServiceAccount
name: kubernetes-dashboard-sa
namespace: kubernetes-dashboard
apiGroup: ""
roleRef:
kind: ClusterRole
name: namespace-readonly
apiGroup: ""
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: non-admin-user
rules:
- apiGroups: ["", "extensions", "apps", "batch"]
resources: ["replicasets", "pods", "configmaps", "pods/log", 'daemonsets', "jobs", "cronjobs"]
verbs: ["get", "list", "watch", "create", "update", "patch", "delete"]
- apiGroups: ["", "extensions", "apps"]
resources: ["deployments","services", "replicationcontrollers", "secrets", "serviceaccounts", "statefulsets", "ingresses", "persistentvolumeclaims", "events"]
verbs: ["get", "list", "watch", "create", "update", "patch"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: ingress-nginx-sa-rolebinding
namespace: ingress-nginx
annotations:
rbac.authorization.kubernetes.io/autoupdate: "true"
subjects:
- kind: ServiceAccount
name: ingress-nginx-sa
namespace: ingress-nginx
roleRef:
kind: ClusterRole
name: non-admin-user
apiGroup: ""
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: kubernetes-dashboard-sa-rolebinding
namespace: kubernetes-dashboard
annotations:
rbac.authorization.kubernetes.io/autoupdate: "true"
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard-sa
namespace: kubernetes-dashboard
roleRef:
kind: ClusterRole
name: non-admin-user
apiGroup: ""
2.2 应用部署文件
kubectl apply -f access-sa.yaml
2.3 查看生成的secret
kubectl get secret -A |grep sa

使用各自的密钥登陆dashboard查看
ingress-nginx这里的secret只能在ingress-nginx 这个名称空间访问, 其他的名称空间无权限
kubernetes-dashboard 这里的secret只能在 kubernetes-dashboard 这个名称空间访问, 其他的名称空间无权限