转自:https://www.cnblogs.com/tanhangbo/p/4550455.html
重点学习如何一步步画出iptables关联表
这里将载有Openwrt的WR841N的路由表dump出来分析一下。
这个是dump出iptables的命令
root@OpenWrt:/etc/config# iptables-save
这里分为4部分:
1.NAT表
*nat :PREROUTING ACCEPT [37930:3638072] :INPUT ACCEPT [440:34479] :OUTPUT ACCEPT [1004:101848] :POSTROUTING ACCEPT [149:36868] :MINIUPNPD - [0:0] :delegate_postrouting - [0:0] :delegate_prerouting - [0:0] :postrouting_lan_rule - [0:0] :postrouting_rule - [0:0] :postrouting_wan_rule - [0:0] :prerouting_lan_rule - [0:0] :prerouting_rule - [0:0] :prerouting_wan_rule - [0:0] :zone_lan_postrouting - [0:0] :zone_lan_prerouting - [0:0] :zone_wan_postrouting - [0:0] :zone_wan_prerouting - [0:0] -A PREROUTING -j delegate_prerouting -A POSTROUTING -j delegate_postrouting -A delegate_postrouting -m comment --comment "user chain for postrouting" -j postrouting_rule -A delegate_postrouting -o br-lan -j zone_lan_postrouting -A delegate_postrouting -o eth0 -j zone_wan_postrouting -A delegate_postrouting -o pppoe-wan -j zone_wan_postrouting -A delegate_prerouting -m comment --comment "user chain for prerouting" -j prerouting_rule -A delegate_prerouting -i br-lan -j zone_lan_prerouting -A delegate_prerouting -i eth0 -j zone_wan_prerouting -A delegate_prerouting -i pppoe-wan -j zone_wan_prerouting -A zone_lan_postrouting -m comment --comment "user chain for postrouting" -j postrouting_lan_rule -A zone_lan_prerouting -m comment --comment "user chain for prerouting" -j prerouting_lan_rule -A zone_wan_postrouting -m comment --comment "user chain for postrouting" -j postrouting_wan_rule -A zone_wan_postrouting -j MASQUERADE -A zone_wan_prerouting -j MINIUPNPD -A zone_wan_prerouting -m comment --comment "user chain for prerouting" -j prerouting_wan_rule COMMIT
其中方括号里面的数据是当前所使用的流量(数据包数和byte数)。
总结为下图:
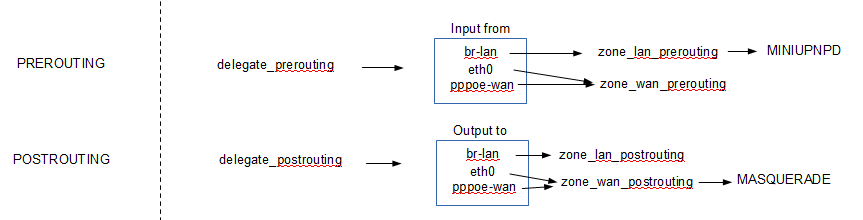
其中从LAN口流入的流量递交给了miniupnpd处理,这个工具有益于P2P下载。
往WAN口去的流量使用了MASQUERADE,是SNAT的增强型,可以转换源IP地址,这样的话就可以发挥路由器的NAT功能了,同时
支持多个客户端。
2.RAW表
*raw :PREROUTING ACCEPT [3358190:2718603756] :OUTPUT ACCEPT [14202:1858213] :notrack - [0:0] -A PREROUTING -j notrack COMMIT
这里基本上没有做什么,不进行分析
3.MANGLE表
*mangle :PREROUTING ACCEPT [3358190:2718603756] :INPUT ACCEPT [14538:1853317] :FORWARD ACCEPT [3342456:2716312729] :OUTPUT ACCEPT [14202:1858213] :POSTROUTING ACCEPT [3356900:2718229627] :ASSIGNOUT - [0:0] :NWANOUT - [0:0] :NWANPOS - [0:0] :NWANPRE - [0:0] :fwmark - [0:0] :mssfix - [0:0] -A PREROUTING -j ASSIGNOUT -A PREROUTING -j NWANPRE -A PREROUTING -j fwmark -A FORWARD -j mssfix -A OUTPUT -j NWANOUT -A POSTROUTING -j NWANPOS -A ASSIGNOUT -m state --state RELATED,ESTABLISHED -j RETURN -A NWANOUT -m conntrack --ctstate RELATED,ESTABLISHED -j CONNMARK --restore-mark --nfmask 0xffffffff --ctmask 0xffffffff -A NWANPOS -o pppoe-wan -m state --state NEW -j CONNMARK --set-xmark 0xa/0xffffffff -A NWANPRE -i pppoe-wan -m state --state NEW -j CONNMARK --set-xmark 0xa/0xffffffff -A NWANPRE -i br-lan -m conntrack --ctstate RELATED,ESTABLISHED -j CONNMARK --restore-mark --nfmask 0xffffffff --ctmask 0xffffffff -A mssfix -o eth0 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "wan (mtu_fix)" -j TCPMSS --clamp-mss-to-pmtu -A mssfix -o pppoe-wan -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "wan (mtu_fix)" -j TCPMSS --clamp-mss-to-pmtu COMMIT
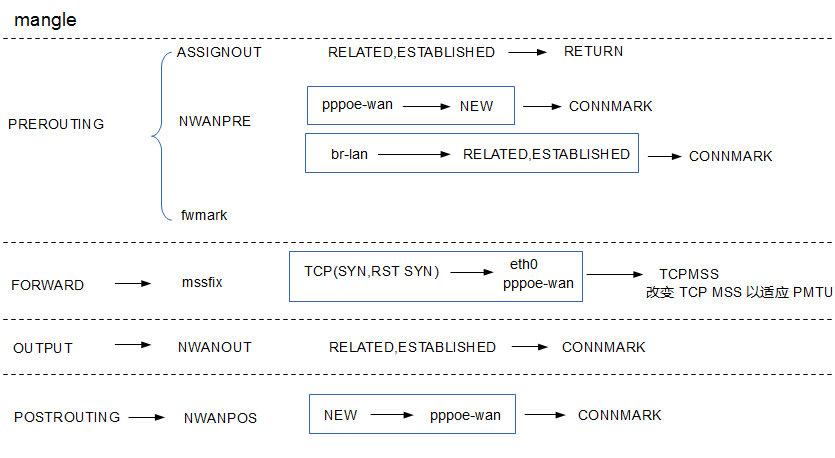
这里在prerouting,output和postrouting的时候做了CONNMRK,用于连接管理,比如做QOS管理。在转发的时候修改了MSS。
4.FILTER表
*filter :INPUT ACCEPT [0:0] :FORWARD DROP [0:0] :OUTPUT ACCEPT [0:0] :MINIUPNPD - [0:0] :delegate_forward - [0:0] :delegate_input - [0:0] :delegate_output - [0:0] :forwarding_lan_rule - [0:0] :forwarding_rule - [0:0] :forwarding_wan_rule - [0:0] :input_lan_rule - [0:0] :input_rule - [0:0] :input_wan_rule - [0:0] :output_lan_rule - [0:0] :output_rule - [0:0] :output_wan_rule - [0:0] :reject - [0:0] :syn_flood - [0:0] :zone_lan_dest_ACCEPT - [0:0] :zone_lan_forward - [0:0] :zone_lan_input - [0:0] :zone_lan_output - [0:0] :zone_lan_src_ACCEPT - [0:0] :zone_lan_src_REJECT - [0:0] :zone_wan_dest_ACCEPT - [0:0] :zone_wan_forward - [0:0] :zone_wan_input - [0:0] :zone_wan_output - [0:0] :zone_wan_src_REJECT - [0:0] -A INPUT -j delegate_input -A FORWARD -j delegate_forward -A OUTPUT -j delegate_output -A delegate_forward -m comment --comment "user chain for forwarding" -j forwarding_rule -A delegate_forward -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT -A delegate_forward -i br-lan -j zone_lan_forward -A delegate_forward -i eth0 -j zone_wan_forward -A delegate_forward -i pppoe-wan -j zone_wan_forward -A delegate_forward -j reject -A delegate_input -i lo -j ACCEPT -A delegate_input -m comment --comment "user chain for input" -j input_rule -A delegate_input -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT -A delegate_input -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -j syn_flood -A delegate_input -i br-lan -j zone_lan_input -A delegate_input -i eth0 -j zone_wan_input -A delegate_input -i pppoe-wan -j zone_wan_input -A delegate_output -o lo -j ACCEPT -A delegate_output -m comment --comment "user chain for output" -j output_rule -A delegate_output -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT -A delegate_output -o br-lan -j zone_lan_output -A delegate_output -o eth0 -j zone_wan_output -A delegate_output -o pppoe-wan -j zone_wan_output -A reject -p tcp -j REJECT --reject-with tcp-reset -A reject -j REJECT --reject-with icmp-port-unreachable -A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -j RETURN -A syn_flood -j DROP -A zone_lan_dest_ACCEPT -o br-lan -j ACCEPT -A zone_lan_forward -m comment --comment "user chain for forwarding" -j forwarding_lan_rule -A zone_lan_forward -m comment --comment "forwarding lan -> wan" -j zone_wan_dest_ACCEPT -A zone_lan_forward -j zone_lan_src_REJECT -A zone_lan_input -m comment --comment "user chain for input" -j input_lan_rule -A zone_lan_input -j zone_lan_src_ACCEPT -A zone_lan_output -m comment --comment "user chain for output" -j output_lan_rule -A zone_lan_output -j zone_lan_dest_ACCEPT -A zone_lan_src_ACCEPT -i br-lan -j ACCEPT -A zone_lan_src_REJECT -i br-lan -j reject -A zone_wan_dest_ACCEPT -o eth0 -j ACCEPT -A zone_wan_dest_ACCEPT -o pppoe-wan -j ACCEPT -A zone_wan_forward -j MINIUPNPD -A zone_wan_forward -m comment --comment "user chain for forwarding" -j forwarding_wan_rule -A zone_wan_forward -j zone_wan_src_REJECT -A zone_wan_input -m comment --comment "user chain for input" -j input_wan_rule -A zone_wan_input -p tcp -m tcp --dport 51413 -m comment --comment "51413" -j ACCEPT -A zone_wan_input -p udp -m udp --dport 51413 -m comment --comment "51413" -j ACCEPT -A zone_wan_input -p tcp -m tcp --dport 9091 -m comment --comment "9091" -j ACCEPT -A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "Allow-DHCP-Renew" -j ACCEPT -A zone_wan_input -p icmp -m icmp --icmp-type 8 -m comment --comment "Allow-Ping" -j ACCEPT -A zone_wan_input -j zone_wan_src_REJECT -A zone_wan_output -m comment --comment "user chain for output" -j output_wan_rule -A zone_wan_output -j zone_wan_dest_ACCEPT -A zone_wan_src_REJECT -i eth0 -j reject -A zone_wan_src_REJECT -i pppoe-wan -j reject COMMIT
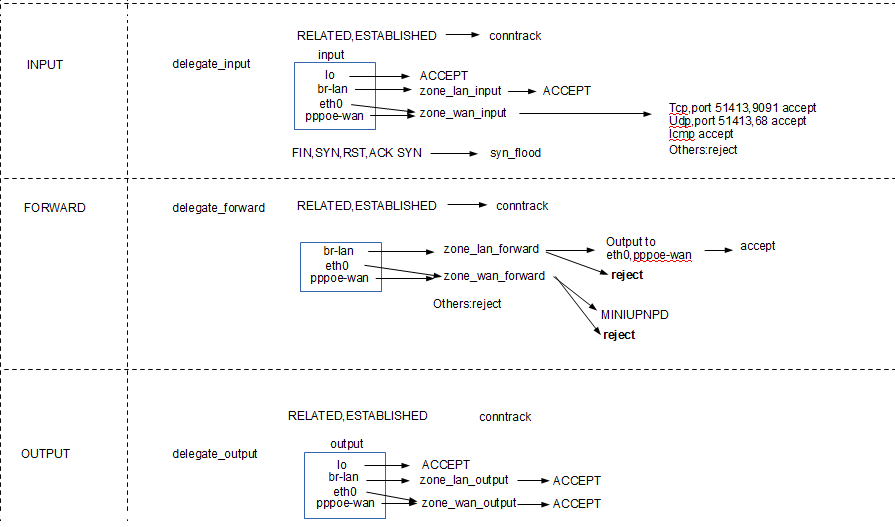
这里先不考虑eth0,从WAN口输入的数据要重点过滤,因为不能让internet的电脑随意攻击路由器,这里允许了ICMP,
51413、9091端口和transmission下载工具有关,68端口和DHCP服务有关。
对于FORWARD的流量,这里基本上已经全部屏蔽了。
对于王WAN口发送的流量全部放行。
5.总结
总的来说,这里做了SNAT实现路由器的基本功能,对连接跟踪可以管理各个连接。另外的一些策略有助于下载工具的运行。
