root@mpls1:~# tcpdump -i enp8s0 arp -env tcpdump: listening on enp8s0, link-type EN10MB (Ethernet), capture size 262144 bytes ^C 0 packets captured 0 packets received by filter 0 packets dropped by kernel root@mpls1:~# tcpdump -i enp8s0 -env tcpdump: listening on enp8s0, link-type EN10MB (Ethernet), capture size 262144 bytes 15:54:42.224675 52:54:00:d9:52:82 > 33:33:ff:00:10:02, ethertype IPv6 (0x86dd), length 86: (hlim 255, next-header ICMPv6 (58) payload length: 32) 2000:2001::1001 > ff02::1:ff00:1002: [icmp6 sum ok] ICMP6, neighbor solicitation, length 32, who has 2000:2001::1002 source link-address option (1), length 8 (1): 52:54:00:d9:52:82 15:54:42.686972 fe:54:00:ff:18:f4 > 01:80:c2:00:00:00, 802.3, length 38: LLC, dsap STP (0x42) Individual, ssap STP (0x42) Command, ctrl 0x03: STP 802.1d, Config, Flags [none], bridge-id 8000.4e:71:31:c9:4e:aa.8011, length 35 message-age 0.00s, max-age 20.00s, hello-time 2.00s, forwarding-delay 2.00s root-id 8000.4e:71:31:c9:4e:aa, root-pathcost 0 15:54:43.259407 52:54:00:d9:52:82 > 33:33:ff:00:10:02, ethertype IPv6 (0x86dd), length 86: (hlim 255, next-header ICMPv6 (58) payload length: 32) 2000:2001::1001 > ff02::1:ff00:1002: [icmp6 sum ok] ICMP6, neighbor solicitation, length 32, who has 2000:2001::1002 source link-address option (1), length 8 (1): 52:54:00:d9:52:82 ^C 3 packets captured 3 packets received by filter 0 packets dropped by kernel root@mpls1:~#
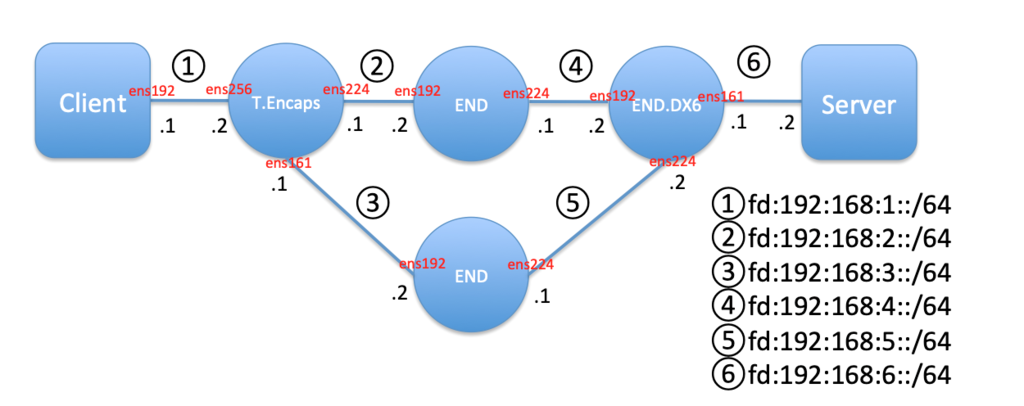
動作イメージ
SRv6の設定
共通設定 (R1,R2,R3,R4)
SRv6を起動するサーバには、全て下記を設定。環境に応じて適宜書き換え。
root@srv6:/home/uchy# vim /etc/sysctl.conf
net.ipv6.conf.all.forwarding = 1
net.ipv6.conf.all.seg6_enabled = 1
net.ipv6.conf.default.seg6_enabled = 1
net.ipv6.conf.ens161.seg6_enabled = 1
net.ipv6.conf.ens224.seg6_enabled = 1
root@srv6:/home/uchy# sysctl -p
Client
sudo ip -6 route add fd:192:168:6::/64 via fd:192:168:1::2 dev ens192
R1(SRv6-1)
root@srv6-1:/home/uchy# vim /etc/iproute2/rt_tables
100 local1
101 local2
ip -6 route add fd:192:168:6::/64 encap seg6 mode encap segs fd:192:168:2::2,fd:192:168:4::2 dev ens224 table local1
ip -6 route add fd:192:168:6::/64 encap seg6 mode encap segs fd:192:168:3::2,fd:192:168:5::2 dev ens161 table local2
sudo ip -6 route add fd:192:168:2::1 encap seg6local action End.DX6 nh6 fd:192:168:1::1 dev ens256
sudo ip -6 route add fd:192:168:3::1 encap seg6local action End.DX6 nh6 fd:192:168:1::1 dev ens256
サービスチェイニング設定(AまたはBの設定を投入)
A: sudo ip -6 rule add from fd:192:168:1::1 table local1
B: sudo ip -6 rule add from fd:192:168:1::1 table local2
R2(SRv6-2)
sudo ip -6 route add fd:192:168:2::2 encap seg6local action End dev ens224
sudo ip -6 route add fd:192:168:4::1 encap seg6local action End dev ens192
R3(SRv6-3)
sudo ip -6 route add fd:192:168:3::2 encap seg6local action End dev ens224
sudo ip -6 route add fd:192:168:5::1 encap seg6local action End dev ens192
R4(SRv6-4)
root@srv6-4:/home/uchy# vim /etc/iproute2/rt_tables
100 local1
101 local2
sudo ip -6 route add fd:192:168:1::/64 encap seg6 mode encap segs fd:192:168:4::1,fd:192:168:2::1 dev ens224 table local1
sudo ip -6 route add fd:192:168:1::/64 encap seg6 mode encap segs fd:192:168:5::1,fd:192:168:3::1 dev ens224 table local2
sudo ip -6 route add fd:192:168:4::2 encap seg6local action End.DX6 nh6 fd:192:168:6::2 dev ens161
sudo ip -6 route add fd:192:168:5::2 encap seg6local action End.DX6 nh6 fd:192:168:6::2 dev ens161
サービスチェイニング設定(AまたはBの設定を投入)
A: sudo ip -6 rule add from fd:192:168:6::2 table local1
B: sudo ip -6 rule add from fd:192:168:6::2 table local2
※アドレスがfd00:xx::xxではなく、fd:xx::xxになっているのは見間違いです。。
SRv6の疎通性確認
Client -> R1 -> R3 -> R4 -> Serverの経路のキャプチャ
R1->R3間のキャプチャ
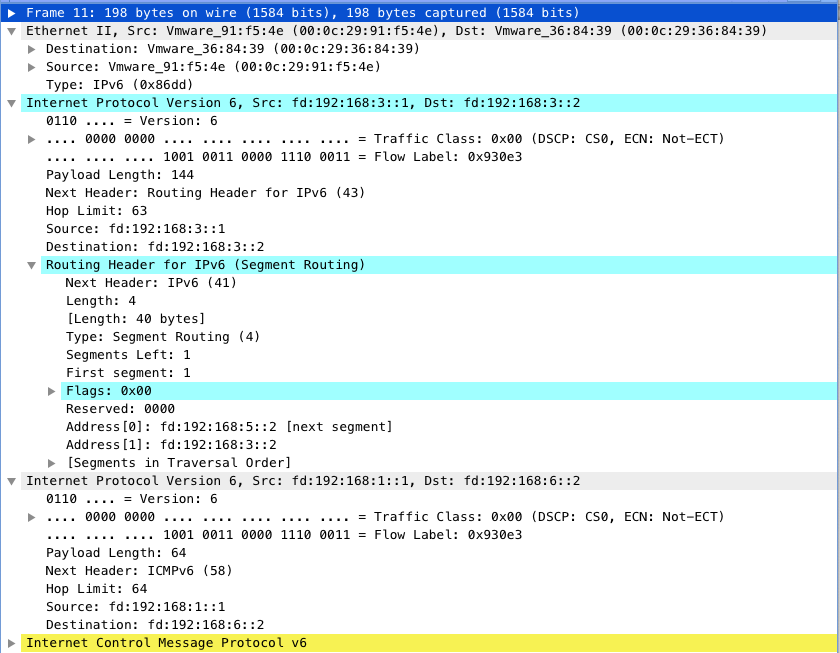
R3->R5間のキャプチャ
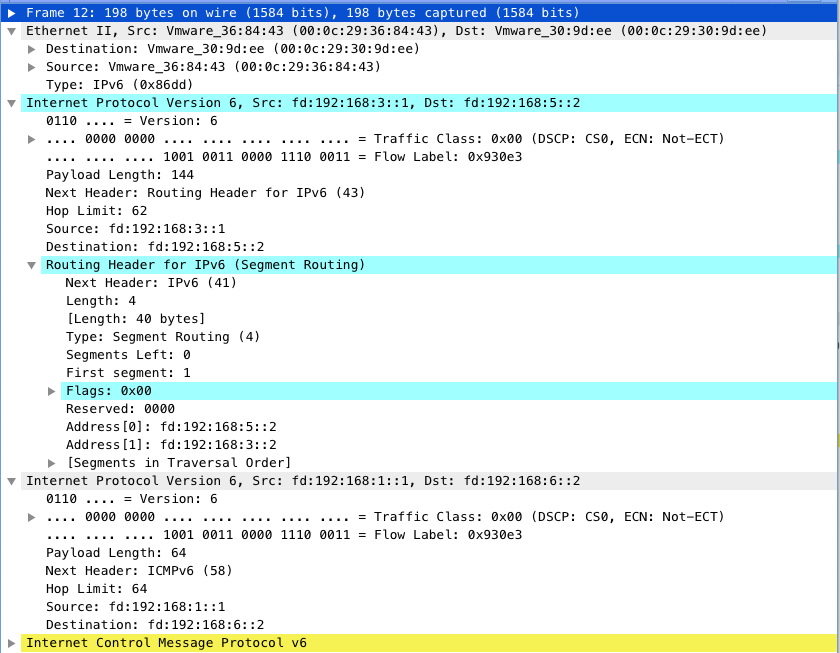
IPv6ヘッダのRouting HeaderにSIDのリストが格納されていることが分かります。
まとめ
JANOG43の発表を元にSRv6を動かして見ました。本ブログでは設定内容がほとんどでSRv6の動作の解説を特に行っていません。 詳しくはInternet-DraftやJanog43のDAY1の資料をご覧ください。とりあえず手を動かして動作を確認してみたいという方のお役に立てれば良いと思います。
R1
添加路由表
root@mpls1:~# vim /etc/iproute2/rt_tables # # reserved values # 255 local 254 main 253 default 0 unspec 100 srv6
root@mpls1:~# ip route add 20.20.20.0/24 encap seg6 mode encap segs 3000::2,3000::4 dev enp7s0 table 100 RTNETLINK answers: File exists root@mpls1:~# ip route del 20.20.20.0/24 encap seg6 mode encap segs 3000::2,3000::4 dev enp7s0 table 100 root@mpls1:~# ip route add 20.20.20.0/24 encap seg6 mode encap segs 3000::2,3000::4 dev enp7s0 table 100 root@mpls1:~#
root@mpls1:~# ip -6 route show table 100 --------------------什么都没有 root@mpls1:~#
root@mpls1:~# tcpdump -i enp7s0 ip6 -env tcpdump: listening on enp7s0, link-type EN10MB (Ethernet), capture size 262144 bytes 19:12:50.427383 52:54:00:d9:52:82 > 52:54:00:ea:64:6e, ethertype IPv6 (0x86dd), length 178: (hlim 63, next-header Routing (43) payload length: 124) 2000:2001::1001 > 3000::2: srcrt (len=4, type=4, segleft=1[|srcrt] 19:12:51.451383 52:54:00:d9:52:82 > 52:54:00:ea:64:6e, ethertype IPv6 (0x86dd), length 178: (hlim 63, next-header Routing (43) payload length: 124) 2000:2001::1001 > 3000::2: srcrt (len=4, type=4, segleft=1[|srcrt] 19:12:52.451151 52:54:00:d9:52:82 > 52:54:00:ea:64:6e, ethertype IPv6 (0x86dd), length 178: (hlim 63, next-header Routing (43) payload length: 124) 2000:2001::1001 > 3000::2: srcrt (len=4, type=4, segleft=1[|srcrt] 19:12:53.467363 52:54:00:d9:52:82 > 52:54:00:ea:64:6e, ethertype IPv6 (0x86dd), length 178: (hlim 63, next-header Routing (43) payload length: 124) 2000:2001::1001 > 3000::2: srcrt (len=4, type=4, segleft=1[|srcrt] 19:12:54.491383 52:54:00:d9:52:82 > 52:54:00:ea:64:6e, ethertype IPv6 (0x86dd), length 178: (hlim 63, next-header Routing (43) payload length: 124) 2000:2001::1001 > 3000::2: srcrt (len=4, type=4, segleft=1[|srcrt] 19:12:54.896658 52:54:00:d9:52:82 > 52:54:00:ea:64:6e, ethertype IPv6 (0x86dd), length 86: (hlim 255, next-header ICMPv6 (58) payload length: 32) fe80::5054:ff:fed9:5282 > fe80::5054:ff:feea:646e: [icmp6 sum ok] ICMP6, neighbor solicitation, length 32, who has fe80::5054:ff:feea:646e source link-address option (1), length 8 (1): 52:54:00:d9:52:82 19:12:54.896764 52:54:00:ea:64:6e > 52:54:00:d9:52:82, ethertype IPv6 (0x86dd), length 78: (hlim 255, next-header ICMPv6 (58) payload length: 24) fe80::5054:ff:feea:646e > fe80::5054:ff:fed9:5282: [icmp6 sum ok] ICMP6, neighbor advertisement, length 24, tgt is fe80::5054:ff:feea:646e, Flags [router, solicited] ^C

R1 先在各个接口上配置IPv6地址,和主机a邻接的接口需要一个IPv4地址 ip addr add 30.30.30.2/24 dev ens36 ip addr add 2000:2001::1001/120 dev ens34 ip addr add 2000:2003::1001/120 dev ens35 ip addr add 3000::11/128 dev lo 增加一个策略路由表,应用到所有从30.30.30.1(主机a)发来的数据包。(这一步是为将来实现多路径VPN做准备,当前这个例子可以不用) 在策略路由表中增加T.Encaps操作(SRv6流量工程),将去往20.20.20.0/24的数据包,封装入SRv6,并配置SRH包含的Segment列表(->3002::2->3000::4) ip rule add from 30.30.30.1/32 table 100 ip route add 20.20.20.0/24 encap seg6 mode encap segs 3000::2,3000::4 dev ens34 table 100 这里的3000::2和3000::4是SRv6的segment,后面会在R2,R3和R4上定义。 同时在配置针对回程数据包的End.DX4操作,让去往主机a的数据包在R1做IPv6的解封装,解出IPv4数据包后发送给主机a ip -6 route add 3000::1/128 encap seg6local action End.DX4 nh4 30.30.30.1 dev ens36 最后还有重要一步,需要配置一条普通的IPv6路由: ip -6 route add 3000::2/128 via 2000:2001::1002 为什么需要这条路由呢? 答案如下:经过T.Encaps操作的数据包的IPv6报文中的目的地址填的是segment list中的第一跳,并且这个报文会发回到本地路由表进行寻址操作,所以我们需要这么一条普通IPv6来将数据包送到R2. (请回顾上一章节的SRv6转发规则)

R2
R2从enp5s0接收R1发来的sr报文,剥掉一层后,从enp6s0转发出去
root@mpls2:~# tcpdump -i enp5s0 ip6 -env tcpdump: listening on enp5s0, link-type EN10MB (Ethernet), capture size 262144 bytes 19:23:29.018373 52:54:00:d9:52:82 > 52:54:00:ea:64:6e, ethertype IPv6 (0x86dd), length 178: (hlim 63, next-header Routing (43) payload length: 124) 2000:2001::1001 > 3000::2: srcrt (len=4, type=4, segleft=1[|srcrt] 19:23:30.047078 52:54:00:d9:52:82 > 52:54:00:ea:64:6e, ethertype IPv6 (0x86dd), length 178: (hlim 63, next-header Routing (43) payload length: 124) 2000:2001::1001 > 3000::2: srcrt (len=4, type=4, segleft=1[|srcrt] 19:23:31.071054 52:54:00:d9:52:82 > 52:54:00:ea:64:6e, ethertype IPv6 (0x86dd), length 178: (hlim 63, next-header Routing (43) payload length: 124) 2000:2001::1001 > 3000::2: srcrt (len=4, type=4, segleft=1[|srcrt] 19:23:32.095077 52:54:00:d9:52:82 > 52:54:00:ea:64:6e, ethertype IPv6 (0x86dd), length 178: (hlim 63, next-header Routing (43) payload length: 124) 2000:2001::1001 > 3000::2: srcrt (len=4, type=4, segleft=1[|srcrt] 19:23:33.119068 52:54:00:d9:52:82 > 52:54:00:ea:64:6e, ethertype IPv6 (0x86dd), length 178: (hlim 63, next-header Routing (43) payload length: 124) 2000:2001::1001 > 3000::2: srcrt (len=4, type=4, segleft=1[|srcrt] 19:23:34.100341 52:54:00:d9:52:82 > 52:54:00:ea:64:6e, ethertype IPv6 (0x86dd), length 86: (hlim 255, next-header ICMPv6 (58) payload length: 32) fe80::5054:ff:fed9:5282 > 2000:2001::1002: [icmp6 sum ok] ICMP6, neighbor solicitation, length 32, who has 2000:2001::1002
4: enp6s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000 link/ether 52:54:00:d7:a1:de brd ff:ff:ff:ff:ff:ff inet6 2000:2002::1002/120 scope global valid_lft forever preferred_lft forever inet6 fe80::5054:ff:fed7:a1de/64 scope link valid_lft forever preferred_lft forever
root@mpls2:~# tcpdump -i enp6s0 ip6 -env tcpdump: listening on enp6s0, link-type EN10MB (Ethernet), capture size 262144 bytes 19:14:35.999083 52:54:00:d7:a1:de > 52:54:00:2e:96:79, ethertype IPv6 (0x86dd), length 178: (hlim 62, next-header Routing (43) payload length: 124) 2000:2001::1001 > 3000::4: srcrt (len=4, type=4, segleft=0[|srcrt] 19:14:36.111879 52:54:00:d7:a1:de > 52:54:00:2e:96:79, ethertype IPv6 (0x86dd), length 86: (hlim 255, next-header ICMPv6 (58) payload length: 32) fe80::5054:ff:fed7:a1de > 2000:2002::1004: [icmp6 sum ok] ICMP6, neighbor solicitation, length 32, who has 2000:2002::1004 source link-address option (1), length 8 (1): 52:54:00:d7:a1:de 19:14:36.112000 52:54:00:2e:96:79 > 52:54:00:d7:a1:de, ethertype IPv6 (0x86dd), length 78: (hlim 255, next-header ICMPv6 (58) payload length: 24) 2000:2002::1004 > fe80::5054:ff:fed7:a1de: [icmp6 sum ok] ICMP6, neighbor advertisement, length 24, tgt is 2000:2002::1004, Flags [router, solicited] 19:14:37.023051 52:54:00:d7:a1:de > 52:54:00:2e:96:79, ethertype IPv6 (0x86dd), length 178: (hlim 62, next-header Routing (43) payload length: 124) 2000:2001::1001 > 3000::4: srcrt (len=4, type=4, segleft=0[|srcrt] 19:14:38.047044 52:54:00:d7:a1:de > 52:54:00:2e:96:79, ethertype IPv6 (0x86dd), length 178: (hlim 62, next-header Routing (43) payload length: 124) 2000:2001::1001 > 3000::4: srcrt (len=4, type=4, segleft=0[|srcrt] ^C 5 packets captured 5 packets received by filter 0 packets dropped by kernel
root@mpls4:~# tcpdump -i enp7s0 ip6 -env tcpdump: listening on enp7s0, link-type EN10MB (Ethernet), capture size 262144 bytes 19:19:05.071085 52:54:00:d7:a1:de > 52:54:00:2e:96:79, ethertype IPv6 (0x86dd), length 118: (flowlabel 0x32eba, hlim 64, next-header ICMPv6 (58) payload length: 64) 2000:2002::1002 > 2000:2002::1004: [icmp6 sum ok] ICMP6, echo request, seq 1 19:19:05.071113 52:54:00:2e:96:79 > 52:54:00:d7:a1:de, ethertype IPv6 (0x86dd), length 118: (flowlabel 0xae50c, hlim 64, next-header ICMPv6 (58) payload length: 64) 2000:2002::1004 > 2000:2002::1002: [icmp6 sum ok] ICMP6, echo reply, seq 1 19:19:06.074059 52:54:00:d7:a1:de > 52:54:00:2e:96:79, ethertype IPv6 (0x86dd), length 118: (flowlabel 0x32eba, hlim 64, next-header ICMPv6 (58) payload length: 64) 2000:2002::1002 > 2000:2002::1004: [icmp6 sum ok] ICMP6, echo request, seq 2 19:19:06.074072 52:54:00:2e:96:79 > 52:54:00:d7:a1:de, ethertype IPv6 (0x86dd), length 118: (flowlabel 0xae50c, hlim 64, next-header ICMPv6 (58) payload length: 64) 2000:2002::1004 > 2000:2002::1002: [icmp6 sum ok] ICMP6, echo reply, seq 2 19:19:10.246325 52:54:00:2e:96:79 > 52:54:00:d7:a1:de, ethertype IPv6 (0x86dd), length 86: (hlim 255, next-header ICMPv6 (58) payload length: 32) fe80::5054:ff:fe2e:9679 > 2000:2002::1002: [icmp6 sum ok] ICMP6, neighbor solicitation, length 32, who has 2000:2002::1002