-
在目标端(Quay)配置界面开启镜像同步功能

存成.tar.gz文件后记得在quay server上解开,并通过docker restart 将quay重启生效。
-
启动一个mirror-worker
docker run -d --name mirroring-worker -v /mnt/quay/config:/conf/stack quay.io/redhat/quay:v3.2.0 repomirror
-
配置robot账户

需要对目标端的镜像库开启写的权限。

-
在镜像库中Enable mirror
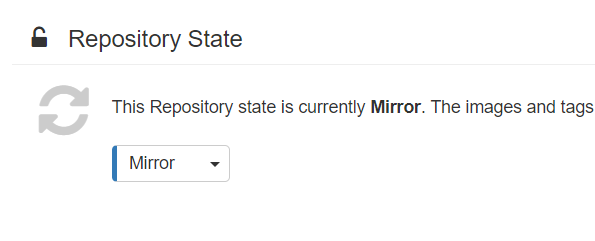
设置源端repository地址
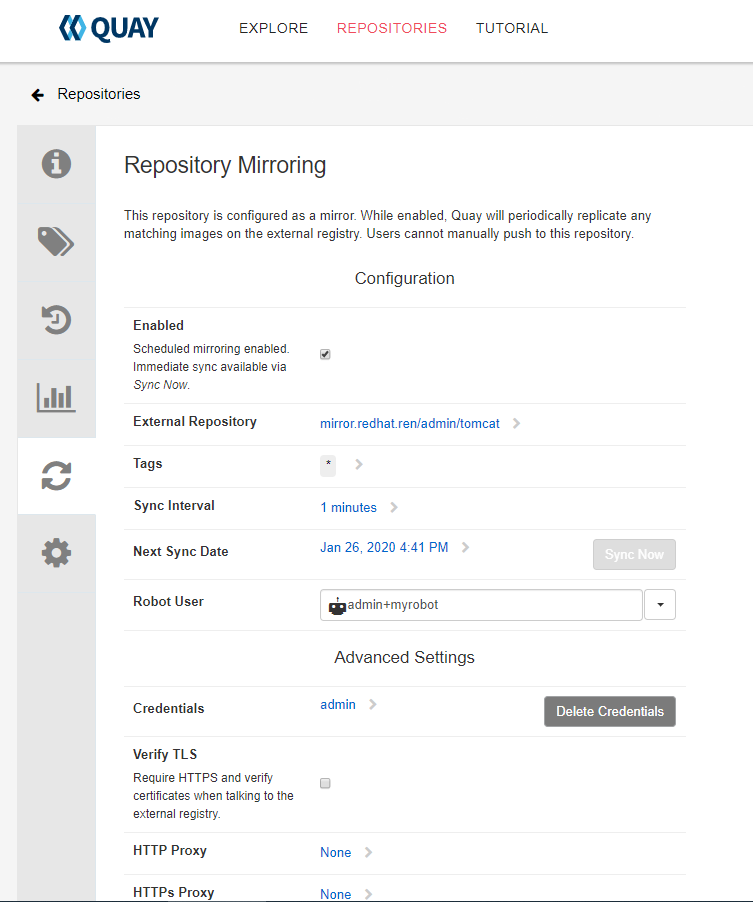
sync now,并且观察日志
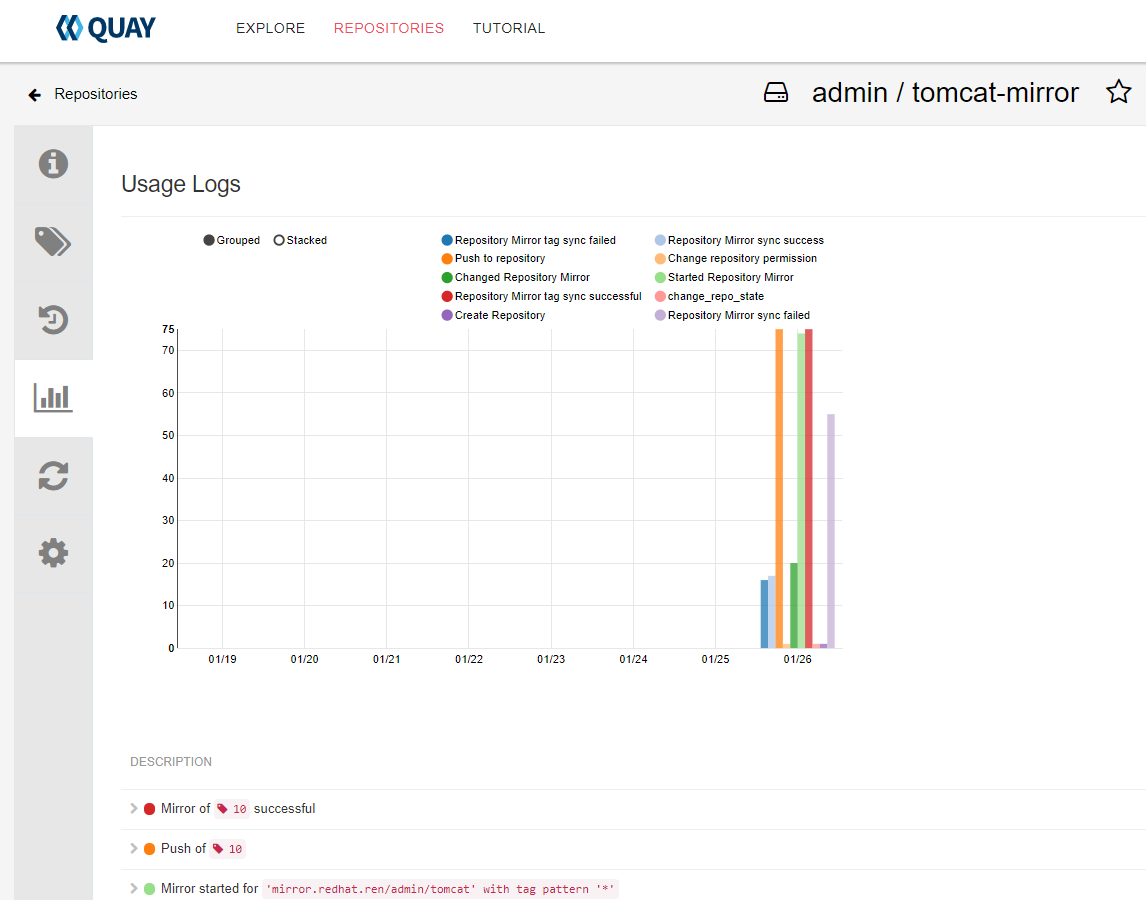
这里遇到几个坑。
- 无论是worker还是quay server在启动的时候都需要去解析镜像库的地址,比如registry.redhat.ren和mirror.redhat.ren,容器启动的时候会将宿主机/etc/resolv.conf里面的DNS设置作为DNS Server,所以必须在宿主机配置DNS Server,并且能够解析两边的Server域名。
如果解析不到,错误信息如下
Getting image source signatures time="2020-01-26T08:11:56Z" level=fatal msg="Error trying to reuse blob sha256:a5a6f2f73cd8abbdc55d0df0d8834f7262713e87d6c8800ea3851f103025e0f0 at destination: pinging docker registry returned: Get http://registry.redhat.ren/v2/: dial tcp: lookup registry.redhat.ren on 192.168.56.107:53: server misbehaving
- skepeo在运行中的X509报错
time="2020-01-26T08:03:37Z" level=fatal msg="pinging docker registry returned: Get https://mirror.redhat.ren/v2/: x509: certificate signed by unknown authority"
解决办法
mkdir -p /mnt/quay/config/extra_ca_certs
cp /etc/docker/certs.d/registry.redhat.ren/ca.crt /mnt/quay/config/extra_ca_certs/
[root@registry config]# tree /mnt/quay/config /mnt/quay/config ├── config.yaml ├── extra_ca_certs │?? └── ca.crt ├── quay-config-mir-config.tar.gz ├── ssl.cert └── ssl.key
然后docker restart containerid 重新启动worker就可以了。
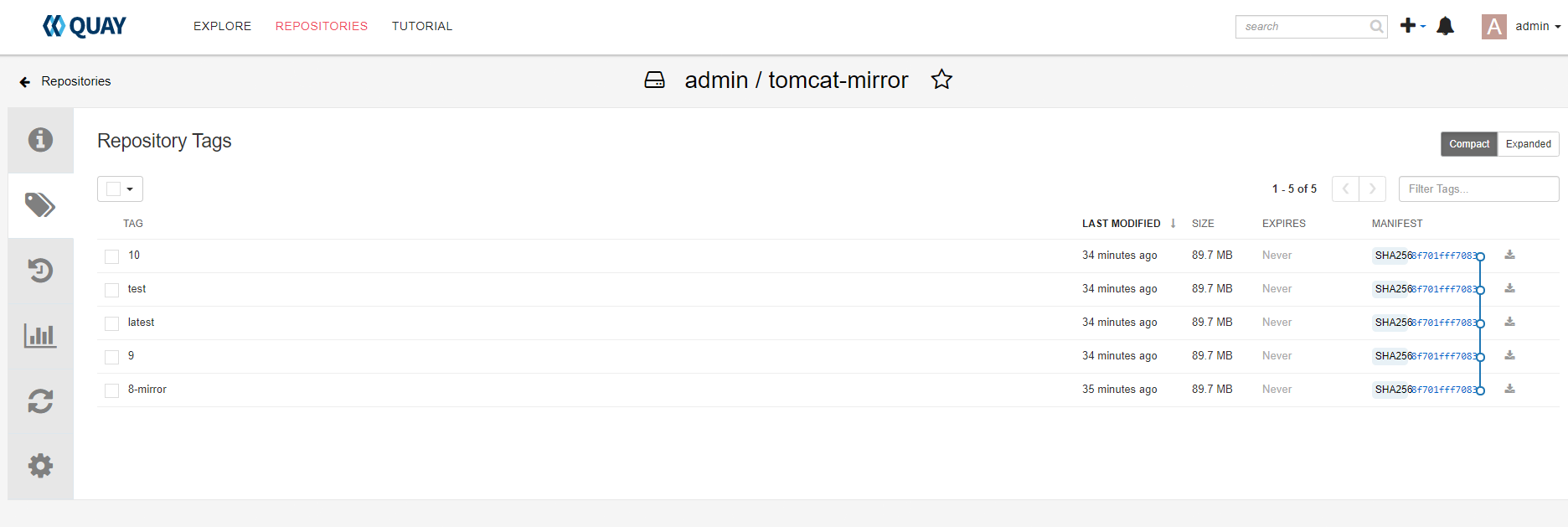
同步完成
-
DNS配置
注意allow-query和listen-on address.
[root@registry config]# cat /etc/named.conf // // named.conf // // Provided by Red Hat bind package to configure the ISC BIND named(8) DNS // server as a caching only nameserver (as a localhost DNS resolver only). // // See /usr/share/doc/bind*/sample/ for example named configuration files. // // See the BIND Administrator's Reference Manual (ARM) for details about the // configuration located in /usr/share/doc/bind-{version}/Bv9ARM.html options { listen-on port 53 { 192.168.56.107; }; listen-on-v6 port 53 { ::1; }; directory "/var/named"; dump-file "/var/named/data/cache_dump.db"; statistics-file "/var/named/data/named_stats.txt"; memstatistics-file "/var/named/data/named_mem_stats.txt"; recursing-file "/var/named/data/named.recursing"; secroots-file "/var/named/data/named.secroots"; allow-query { any; }; /* - If you are building an AUTHORITATIVE DNS server, do NOT enable recursion. - If you are building a RECURSIVE (caching) DNS server, you need to enable recursion. - If your recursive DNS server has a public IP address, you MUST enable access control to limit queries to your legitimate users. Failing to do so will cause your server to become part of large scale DNS amplification attacks. Implementing BCP38 within your network would greatly reduce such attack surface */ recursion yes; dnssec-enable yes; dnssec-validation yes; /* Path to ISC DLV key */ bindkeys-file "/etc/named.root.key"; managed-keys-directory "/var/named/dynamic"; pid-file "/run/named/named.pid"; session-keyfile "/run/named/session.key"; }; logging { channel default_debug { file "data/named.run"; severity dynamic; }; }; zone "." IN { type hint; file "named.ca"; }; zone "redhat.ren" IN { type master; file "redhat.ren"; }; zone "56.168.192.in-addr.arpa" IN { type master; file "192.168.56.db"; }; include "/etc/named.rfc1912.zones"; include "/etc/named.root.key";
[root@registry config]# cat /var/named/redhat.ren $TTL 1W @ IN SOA ns1.redhat.ren. root ( 2019052300 ; serial 3H ; refresh (3 hours) 30M ; retry (30 minutes) 2W ; expiry (2 weeks) 1W ) ; minimum (1 week) IN NS ns1.redhat.ren. IN MX 10 smtp.redhat.ren. ; ; ns1 IN A 192.168.56.107 smtp IN A 192.168.56.107 ; ; The api points to the IP of your load balancer registry IN A 192.168.56.107 mirror IN A 192.168.56.108 ; ;EOF
[root@registry config]# cat /var/named/192.168.56.db $TTL 1W @ IN SOA ns1.redhat.ren. root ( 2019052300 ; serial 3H ; refresh (3 hours) 30M ; retry (30 minutes) 2W ; expiry (2 weeks) 1W ) ; minimum (1 week) IN NS ns1.redhat.ren. ; ; syntax is "last octet" and the host must have fqdn with trailing dot 107 IN PTR registry.redhat.ren. 108 IN PTR mirror.redhat.ren. ; ; ;EOF