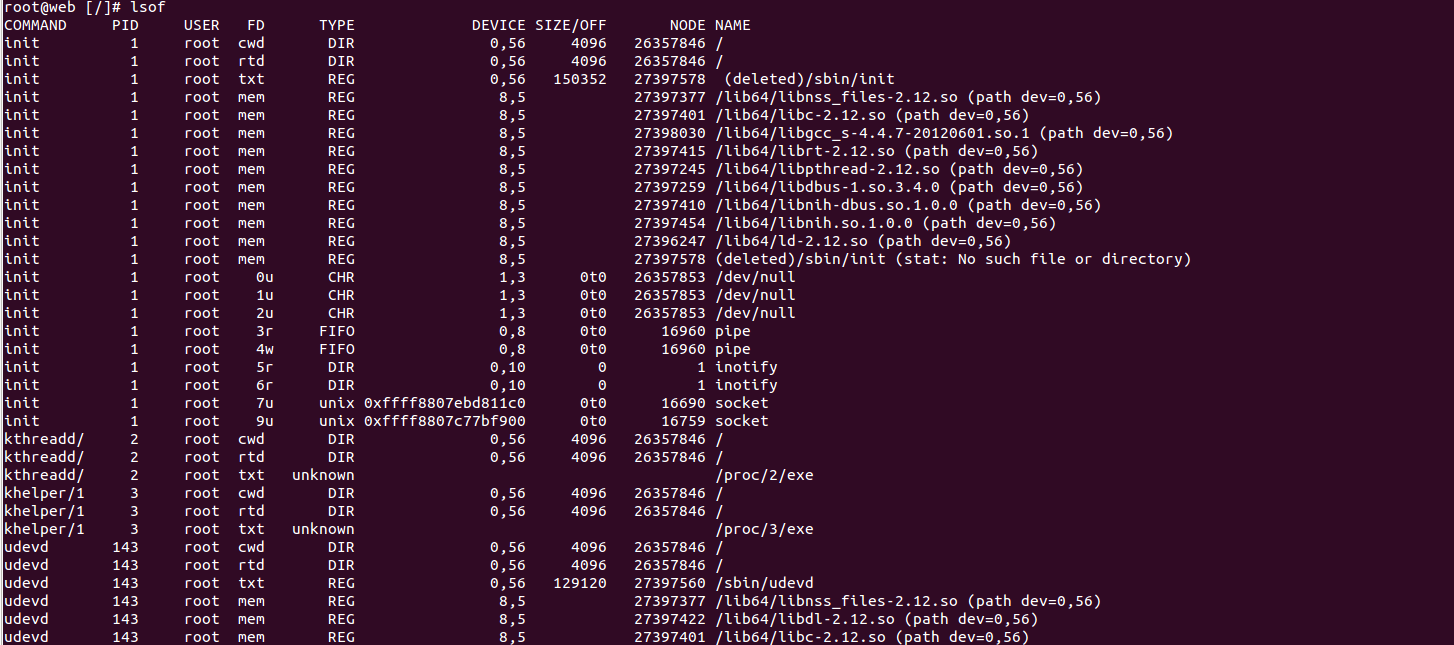
1, 使用 lsof 命令行列出所有打开的文件
# lsof
这可是一个很长的列表,包括打开的文件和网络
上述屏幕截图中包含很多列,例如 PID、user、FD 和 TYPE 等等。
FD - File descriptor
FD 列包含这样一些值
cwd - Current working directory
txt - Text file
mem - Memory Mapped file
mmap - Memory Mapped device
Number - It represent the actual file descriptor. For example, 0u, 1w and 3r
r 是读的意思,w 是写,u 代表读写
Type 代表文件类型,例如:
>REG - Regular file
>DIR - Directory
>CHR - Character special file
>FIFO - First in first out
2, 列出某个用户打开的文件
# lsof -u user_name
Example:
# lsof -u crybit
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
sshd 29609 crybit cwd DIR 144,233 4096 117711421 /
sshd 29609 crybit rtd DIR 144,233 4096 117711421 /
sshd 29609 crybit txt REG 144,233 409488 119020186 /usr/sbin/sshd
sshd 29609 crybit mem REG 144,241 2443001619 (deleted)/dev/zero (stat: No such file or directory)
sshd 29609 crybit mem REG 8,37 119021850 /lib64/libnss_dns-2.5.so (path dev=144,233)
sshd 29609 crybit mem REG 8,37 119021984 /lib64/security/pam_succeed_if.so (path dev=144,233)
sshd 29609 crybit mem REG 8,37 119022000 /lib64/security/pam_limits.so (path dev=144,233)
sshd 29609 crybit mem REG 8,37 119021960 /lib64/security/pam_keyinit.so (path dev=144,233)
sshd 29609 crybit mem REG 8,37 119021972 /lib64/security/pam_cracklib.so (path dev=144,233)
sshd 29609 crybit mem REG 8,37 119021987 /lib64/security/pam_nologin.so (path dev=144,233)
sshd 29609 crybit mem REG 8,37 119021988 /lib64/security/pam_deny.so (path dev=144,233)
sshd 29609 crybit mem REG 8,37 119019223 /usr/lib64/libcrack.so.2.8.0 (path dev=144,233)
.....
.....
3, 列出在某个端口运行的进程
# lsof -i :port_number
Example:
# lsof -i :22
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
sshd 769 root 3u IPv6 2281738844 0t0 TCP *:ssh (LISTEN)
sshd 769 root 4u IPv4 2281738846 0t0 TCP *:ssh (LISTEN)
# lsof -i :3306
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
mysqld 11106 mysql 10u IPv4 2340975114 0t0 TCP *:mysql (LISTEN)
4, 只列出使用 IPv4 的打开文件
# lsof -i 4 - For IPv4
Example:
# lsof -i 4
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
sshd 769 root 4u IPv4 2281738846 0t0 TCP *:ssh (LISTEN)
named 8362 named 20u IPv4 2334751017 0t0 TCP localhost.localdomain:domain (LISTEN)
named 8362 named 21u IPv4 2334751019 0t0 TCP crybit.com:domain (LISTEN)
named 8362 named 22u IPv4 2334751021 0t0 TCP localhost.localdomain:rndc (LISTEN)
named 8362 named 512u IPv4 2334751016 0t0 UDP localhost.localdomain:domain
named 8362 named 513u IPv4 2334751018 0t0 UDP crybit.com:domain
tcpserver 9975 root 3u IPv4 2335487959 0t0 TCP *:pop3 (LISTEN)
tcpserver 9978 root 3u IPv4 2335487967 0t0 TCP *:pop3s (LISTEN)
tcpserver 9983 root 3u IPv4 2335487997 0t0 TCP *:imap (LISTEN)
tcpserver 9987 root 3u IPv4 2335488014 0t0 TCP *:imaps (LISTEN)
xinetd 10413 root 5u IPv4 2336070983 0t0 TCP *:ftp (LISTEN)
xinetd 10413 root 6u IPv4 2336070984 0t0 TCP *:smtp (LISTEN)
mysqld 11106 mysql 10u IPv4 2340975114 0t0 TCP *:mysql (LISTEN)
# lsof -i 6
Example:
# lsof -i 6
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
sshd 769 root 3u IPv6 2281738844 0t0 TCP *:ssh (LISTEN)
named 8362 named 23u IPv6 2334751024 0t0 TCP localhost.localdomain:rndc (LISTEN)
httpd 29241 root 4u IPv6 2439777206 0t0 TCP *:http (LISTEN)
httpd 29241 root 6u IPv6 2439777211 0t0 TCP *:https (LISTEN)
httpd 29243 apache 4u IPv6 2439777206 0t0 TCP *:http (LISTEN)
httpd 29243 apache 6u IPv6 2439777211 0t0 TCP *:https (LISTEN)
httpd 29244 apache 4u IPv6 2439777206 0t0 TCP *:http (LISTEN)
httpd 29244 apache 6u IPv6 2439777211 0t0 TCP *:https (LISTEN)
httpd 29245 apache 4u IPv6 2439777206 0t0 TCP *:http (LISTEN)
httpd 29245 apache 6u IPv6 2439777211 0t0 TCP *:https (LISTEN)
httpd 29246 apache 4u IPv6 2439777206 0t0 TCP *:http (LISTEN)
5, 列出端口在 1-1024 之间的所有进程
# lsof -i :1-1024
Example:
# lsof -i :1-1024
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
sshd 769 root 3u IPv6 2281738844 0t0 TCP *:ssh (LISTEN)
sshd 769 root 4u IPv4 2281738846 0t0 TCP *:ssh (LISTEN)
named 8362 named 20u IPv4 2334751017 0t0 TCP localhost.localdomain:domain (LISTEN)
named 8362 named 21u IPv4 2334751019 0t0 TCP crybit.com:domain (LISTEN)
named 8362 named 22u IPv4 2334751021 0t0 TCP localhost.localdomain:rndc (LISTEN)
named 8362 named 23u IPv6 2334751024 0t0 TCP localhost.localdomain:rndc (LISTEN)
tcpserver 9975 root 3u IPv4 2335487959 0t0 TCP *:pop3 (LISTEN)
tcpserver 9978 root 3u IPv4 2335487967 0t0 TCP *:pop3s (LISTEN)
tcpserver 9983 root 3u IPv4 2335487997 0t0 TCP *:imap (LISTEN)
tcpserver 9987 root 3u IPv4 2335488014 0t0 TCP *:imaps (LISTEN)
xinetd 10413 root 5u IPv4 2336070983 0t0 TCP *:ftp (LISTEN)
xinetd 10413 root 6u IPv4 2336070984 0t0 TCP *:smtp (LISTEN)
httpd 29241 root 4u IPv6 2439777206 0t0 TCP *:http (LISTEN)
httpd 29241 root 6u IPv6 2439777211 0t0 TCP *:https (LISTEN)
httpd 29243 apache 4u IPv6 2439777206 0t0 TCP *:http (LISTEN)
....
....
6, 根据进程id来列出打开的文件
# lsof -p PID
Example:
# lsof -p 11106
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
mysqld 11106 mysql cwd DIR 144,233 4096 119025114 /var/lib/mysql
mysqld 11106 mysql rtd DIR 144,233 4096 117711421 /
mysqld 11106 mysql txt REG 144,233 9484782 119025094 /usr/libexec/mysqld
mysqld 11106 mysql mem REG 8,37 119025094 /usr/libexec/mysqld (path dev=144,233)
mysqld 11106 mysql mem REG 8,37 119021850 /lib64/libnss_dns-2.5.so (path dev=144,233)
mysqld 11106 mysql mem REG 8,37 119021830 /lib64/libnss_files-2.5.so (path dev=144,233)
mysqld 11106 mysql mem REG 8,37 119021841 /lib64/libsepol.so.1 (path dev=144,233)
mysqld 11106 mysql mem REG 8,37 119021801 /lib64/libselinux.so.1 (path dev=144,233)
mysqld 11106 mysql mem REG 8,37 119021785 /lib64/libresolv-2.5.so (path dev=144,233)
mysqld 11106 mysql mem REG 8,37 119021920 /lib64/libkeyutils-1.2.so (path dev=144,233)
mysqld 11106 mysql mem REG 8,37 119017006 /usr/lib64/libkrb5support.so.0.1 (path dev=144,233)
....
....
7, 杀掉某个用户的所有活动进程
# killall -9 `lsof -t -u username`
8, 列出某个目录中被打开的文件
# lsof +D path_of_the_directory
Example:
# lsof +D /var/log/
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
syslogd 9729 root 1w REG 144,233 0 119019158 /var/log/kernel
syslogd 9729 root 2w REG 144,233 350722 119021699 /var/log/messages
syslogd 9729 root 3w REG 144,233 591577 119019159 /var/log/secure
syslogd 9729 root 4w REG 144,233 591577 119019159 /var/log/secure
9, 根据进程名称列出打开的文件
# lsof -c process_name
Example:
# lsof -c ssh
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
sshd 483 root cwd DIR 8,9 4096 2 /
sshd 483 root rtd DIR 8,9 4096 2 /
sshd 483 root txt REG 8,9 523488 1193409 /usr/sbin/sshd
10, 列出所有网络连接
# lsof -i
该命令列出所有侦听和已建立的网络连接
Example:
# lsof -i
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
sshd 769 root 3u IPv6 2281738844 0t0 TCP *:ssh (LISTEN)
sshd 769 root 4u IPv4 2281738846 0t0 TCP *:ssh (LISTEN)
named 8362 named 20u IPv4 2334751017 0t0 TCP localhost.localdomain:domain (LISTEN)
named 8362 named 21u IPv4 2334751019 0t0 TCP crybit.com:domain (LISTEN)
named 8362 named 22u IPv4 2334751021 0t0 TCP localhost.localdomain:rndc (LISTEN)
named 8362 named 23u IPv6 2334751024 0t0 TCP localhost.localdomain:rndc (LISTEN)
named 8362 named 512u IPv4 2334751016 0t0 UDP localhost.localdomain:domain
就这些!