1.环境准备
apt安装
sudo apt-get update -y sudo apt-get dist-upgrade -y sudo apt-get install -y zlib1g-dev liblzma-dev openssl libssl-dev sudo apt-get install -y build-essential bison flex sudo apt-get install -y libpcap-dev libpcre3-dev libdumbnet-dev libnghttp2-dev sudo apt-get install -y mysql-server libmysqlclient-dev mysql-client autoconf libtool sudo apt-get install -y libcrypt-ssleay-perl liblwp-useragent-determined-perl libwww-perl sudo add-apt-repository ppa:ondrej/php sudo apt-get update -y sudo apt-get install -y apache2 libapache2-mod-php5.6 php5.6 php5.6-common php5.6-gd php5.6-cli php5.6-xml php5.6-mysql sudo apt-get install -y php-pear libphp-adodb
wget从网站下载压缩包
wget https://www.snort.org/downloads/archive/snort/daq-2.0.6.tar.gz wget https://www.snort.org/downloads/archive/snort/snort-2.9.9.0.tar.gz wget https://github.com/firnsy/barnyard2/archive/v2-1.13.tar.gz -O barnyard2-2-1.13.tar.gz wget https://github.com/shirkdog/pulledpork/archive/v0.7.3.tar.gz -O pulledpork-v0.7.3.tar.gz wget https://sourceforge.net/projects/adodb/files/adodb-php5-only/adodb-520-for-php5/adodb-5.20.8.tar.gz wget http://sourceforge.net/projects/secureideas/files/BASE/base-1.4.5/base-1.4.5.tar.gz
2.开始安装
(1)安装daq
tar -xvzf daq-2.0.6.tar.gz cd daq-2.0.6 ./configure sudo make sudo make install
(2)安装snort
tar -xvzf snort-2.9.9.tar.gz cd snort-2.9.9 ./configure --enable-sourcefire make sudo make install
测试
snort -V
创建用户环境
# Create the snort user and group: sudo groupadd snort sudo useradd snort -r -s /sbin/nologin -c SNORT_IDS -g snort # Create the Snort directories: sudo mkdir /etc/snort sudo mkdir /etc/snort/rules sudo mkdir /etc/snort/rules/iplists sudo mkdir /etc/snort/preproc_rules sudo mkdir /usr/local/lib/snort_dynamicrules sudo mkdir /etc/snort/so_rules # Create some files that stores rules and ip lists sudo touch /etc/snort/rules/iplists/black_list.rules sudo touch /etc/snort/rules/iplists/white_list.rules sudo touch /etc/snort/rules/local.rules sudo touch /etc/snort/sid-msg.map # Create our logging directories: sudo mkdir /var/log/snort sudo mkdir /var/log/snort/archived_logs # Adjust permissions: sudo chmod -R 5775 /etc/snort sudo chmod -R 5775 /var/log/snort sudo chmod -R 5775 /var/log/snort/archived_logs sudo chmod -R 5775 /etc/snort/so_rules sudo chmod -R 5775 /usr/local/lib/snort_dynamicrules # Change Ownership on folders: sudo chown -R snort:snort /etc/snort sudo chown -R snort:snort /var/log/snort sudo chown -R snort:snort /usr/local/lib/snort_dynamicrules
复制配置文件
cd ~/snort-2.9.9/etc/ sudo cp *.conf* /etc/snort sudo cp *.map /etc/snort sudo cp *.dtd /etc/snort cd ~/snort-2.9.9/src/dynamic-preprocessors/build/usr/local/lib/snort_dynamicpreprocessor/ sudo cp * /usr/local/lib/snort_dynamicpreprocessor/
注释掉snort.conf中引用的规则文件,换为PulledPork
sudo sed -i "s/include $RULE\_PATH/#include $RULE\_PATH/" /etc/snort/snort.conf
修改snort.conf的配置
sudo vi /etc/snort/snort.conf #第45行,ipvar HOME_NET修改为本机的内部网络 ipvar HOME_NET 192.168.89.138/24 #第104行,设置以下配置文件路径 var RULE_PATH /etc/snort/rules var SO_RULE_PATH /etc/snort/so_rules var PREPROC_RULE_PATH /etc/snort/preproc_rules var WHITE_LIST_PATH /etc/snort/rules/iplists var BLACK_LIST_PATH /etc/snort/rules/iplists #第521行添加 # output unified2: filename merged.log, l imit 128, nostamp, mpls event types, vlan event types } output unified2: filename snort.u2, limit 128 #第546行取消注释,启用local.rules文件 include $RULE_PATH/local.rules
添加本地规则
sudo vi /etc/snort/rules/local.rules alert icmp any any -> $HOME_NET any (msg:"ICMP Test detected!!!"; classtype:icmp-event; sid:10000001; rev:001; GID:1; )
sudo vi /etc/snort/sid-msg.map 1 || 10000001 || 001 || icmp-event || 0 || ICMP Test detected || url,tools.ietf.org/html/rfc792
测试配置文件
sudo snort -T -c /etc/snort/snort.conf -i eth1
测试功能,此时从外面ping网口ens32的IP,snort会记录受到攻击,信息保存在/var/log/snort中,文件名为snort.log.xxx
sudo snort -A console -q -u snort -g snort -c /etc/snort/snort.conf -i ens32
3.安装Barnyard2
解压编译
tar zxvf barnyard2-2-1.13.tar.gz cd barnyard2-2-1.13 autoreconf -fvi -I ./ # Choose ONE of these two commands to run ./configure --with-mysql --with-mysql-libraries=/usr/lib/x86_64-linux-gnu ./configure --with-mysql --with-mysql-libraries=/usr/lib/i386-linux-gnu sudo make sudo make install
测试
barnyard2 -V
配置文件
sudo cp ~/barnyard2-2-1.13/etc/barnyard2.conf /etc/snort/ # the /var/log/barnyard2 folder is never used or referenced # but barnyard2 will error without it existing sudo mkdir /var/log/barnyard2 sudo chown snort.snort /var/log/barnyard2 sudo touch /var/log/snort/barnyard2.waldo sudo chown snort.snort /var/log/snort/barnyard2.waldo
配置数据库
ubuntu@ubuntu:~$ mysql -u root -p mysql> create database snort; mysql> use snort; mysql> source ~/barnyard2-2-1.13/schemas/create_mysql; mysql> CREATE USER 'snort'@'localhost' IDENTIFIED BY '123456'; mysql> grant create, insert, select, delete, update on snort.* to 'snort'@'localhost'; mysql> exit;
添加数据库位置
sudo vi /etc/snort/barnyard2.conf #在末尾添加数据库配置 output database: log, mysql, user=snort password=123456 dbname=snort host=localhost sensor name=sensor01
测试,开启snort,并向ens32发送ping数据包
sudo snort -q -u snort -g snort -c /etc/snort/snort.conf -i ens32
# 开启barnyard2,将日志信息存入数据库 # 1.连续处理模式,设置barnyard2.waldo为书签 sudo barnyard2 -c /etc/snort/barnyard2.conf -d /var/log/snort -f snort.u2 -w /var/log/snort/barnyard2.waldo -g snort -u snort # 2.文件处理模式,处理单个日志文件 sudo barnyard2 -c /etc/snort/barnyard2.conf -o /var/log/snort/snort.u2.xxx
# 查看数据库条目数量,看是否增加 mysql -u snort -p -D snort -e "select count(*) from event"
4.安装PulledPork
解压安装
tar xzvf pulledpork-v0.7.3.tar.gz cd pulledpork-v0.7.3/ sudo cp pulledpork.pl /usr/local/bin sudo chmod +x /usr/local/bin/pulledpork.pl sudo cp etc/*.conf /etc/snort
测试
ubuntu@ubuntu:~$ pulledpork.pl -V PulledPork v0.7.3 - Making signature updates great again!
配置文件更改
sudo vi /etc/snort/pulledpork.conf #第19行:输入注册账户生成的oinkcode,若没有则注释掉 #第29行:取消注释可下载针对新兴威胁的规则 #第74行:更改为: rule_path = /etc/snort/rules/snort.rules #第89行:更改为: local_rules = /etc/snort/rules/local.rules #第92行:更改为: sid_msg = /etc/snort/sid-msg.map #第96行:更改为: sid_msg_version = 2 #第119行:更改为: config_path = /etc/snort/snort.conf #第133行:更改为: distro = Ubuntu-12-04 #第141行:更改为: black_list = /etc/snort/rules/iplists/black_list.rules #第150行:更改为: IPRVersion = /etc/snort/rules/iplists
sudo vi /etc/snort/snort.conf #第548行添加 include $RULE_PATH/snort.rules
更新测试规则
sudo /usr/local/bin/pulledpork.pl -c /etc/snort/pulledpork.conf -l sudo snort -T -c /etc/snort/snort.conf -i ens32
5.创建服务
snort服务
#创建服务配置文件 sudo vi /lib/systemd/system/snort.service [Unit] Description=Snort NIDS Daemon After=syslog.target network.target [Service] Type=simple Restart=always ExecStart=/usr/local/bin/snort -q -u snort -g snort -c /etc/snort/snort.conf -i eth1 [Install] WantedBy=multi-user.target #设置开机启动 sudo systemctl enable snort #启动服务 sudo systemctl start snort #检查服务状态 sudo systemctl status snort
Barnyard2服务
#创建服务配置文件 sudo vi /lib/systemd/system/barnyard2.service [Unit] Description=Barnyard2 Daemon After=syslog.target network.target [Service] Type=simple Restart=always ExecStart=/usr/local/bin/barnyard2 -c /etc/snort/barnyard2.conf -d /var/log/snort -f snort.u2 -q -w /var/log/snort/barnyard2.waldo -g snort -u snort -D -a /var/log/snort/archived_logs --pid-path=/var/run [Install] WantedBy=multi-user.target #设置开机启动 sudo systemctl enable barnyard2 #启动服务 sudo systemctl start barnyard2 #检查服务状态 sudo systemctl status barnyard2
6.安装BASE
解压后获得网站目录,移到apache2目录
tar xzvf base-1.4.5.tar.gz sudo mv base-1.4.5 /var/www/html/base/
配置
cd /var/www/html/base sudo cp base_conf.php.dist base_conf.php sudo vi /var/www/html/base/base_conf.php $BASE_Language = 'chinese'; # line 27 $BASE_urlpath = '/base'; # line 50 $DBlib_path = '/usr/share/php/adodb/'; #line 80 $alert_dbname = 'snort'; # line 102 $alert_host = 'localhost'; $alert_port = ''; $alert_user = 'snort'; $alert_password = '123456'; # line 106 // $graph_font_name = "Verdana"; // $graph_font_name = "DejaVuSans"; // $graph_font_name = "Image_Graph_Font"; $graph_font_name = ""; sudo chown -R www-data:www-data /var/www/html/base sudo chmod o-r /var/www/html/base/base_conf.php sudo service apache2 restart
测试
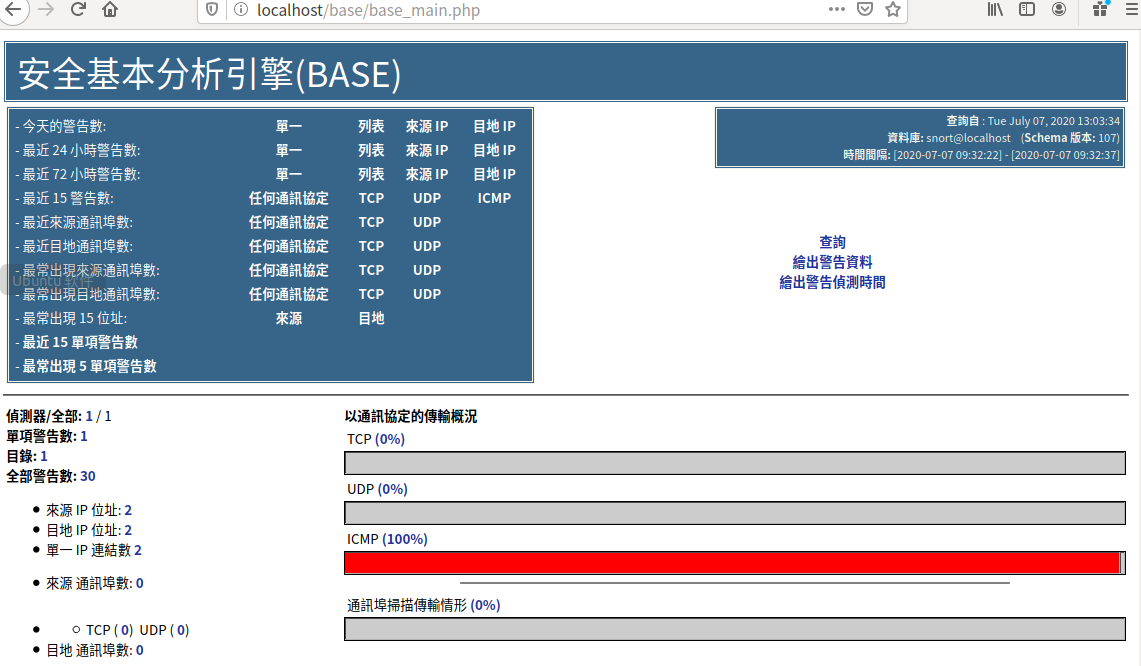
浏览器输入localhost/base
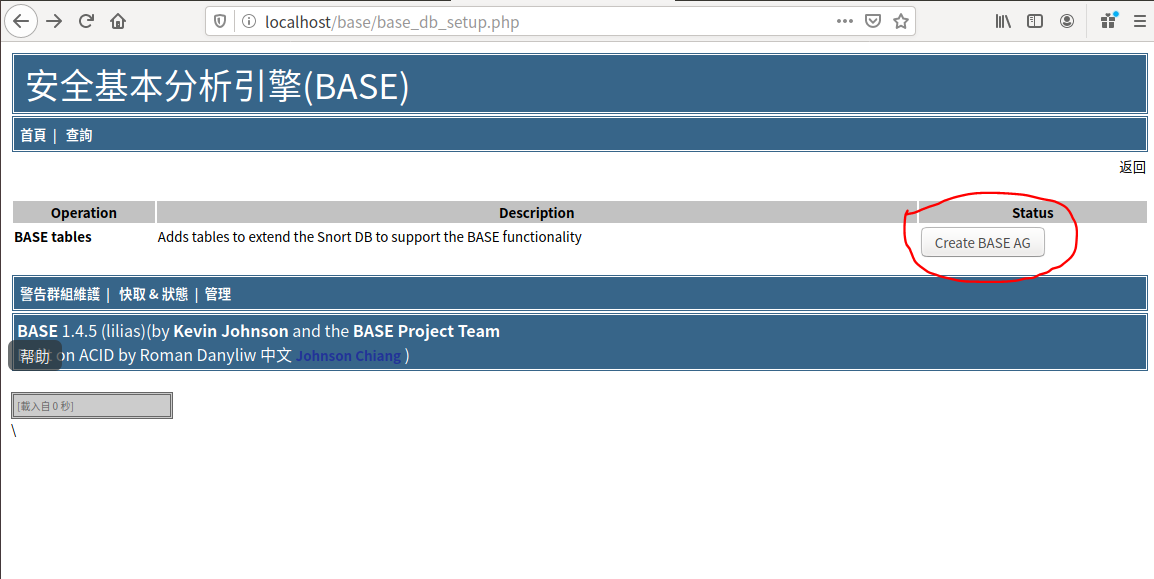
点击Create BASE AG