一丶前言
因自己工作,可能后面会写ark工具.所以周六周日没事就逆向了一下进程回调数组. 虽然资料很多.但是自己动手自己明白.总比别人给的好.
所以记一下自己的分析思路以及逆向结果.
内核中 PsSetCreateProcessNotifyRoutine回调函数是用来设置进程监控的.
相应的还有一个Ex函数. ex函数没有逆向.简单的看了一下.这里说一下
进程回调的逆向把.
二丶逆向过程
1.windbg挂载 win7 32位.定位到函数反汇编位置
定位反汇编代码如下:
kd> uf PsSetCreateProcessNotifyRoutine
nt!PsSetCreateProcessNotifyRoutine:
83fd87de 8bff mov edi,edi
83fd87e0 55 push ebp
83fd87e1 8bec mov ebp,esp
83fd87e3 6a00 push 0
83fd87e5 ff750c push dword ptr [ebp+0Ch] 参数2 ---------> 是否删除
83fd87e8 ff7508 push dword ptr [ebp+8] 参数1 ---------> 回调函数地址
83fd87eb e809000000 call nt!PspSetCreateProcessNotifyRoutine (83fd87f9)
83fd87f0 5d pop ebp
83fd87f1 c20800 ret 8
可以看到 里面调用的函数为: PspSetCreateProcessNotifyRoutine
总共三个参数
伪代码
PspSetCreateProcessNotifyRoutine(0,你自己的回调函数地址,是否删除标记)
而逆向Ex系列的函数.发现变得仅仅是第一个函数参数. 0变为1了.
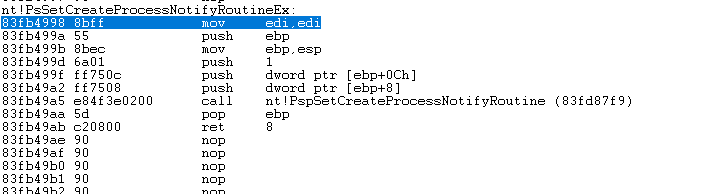
2.逆向 PspSetCreateProcessNotifyRoutine
底层函数调用的它,那么就逆向它.
kd> uf PspSetCreateProcessNotifyRoutine
nt!PspSetCreateProcessNotifyRoutine:
83fd87f9 8bff mov edi,edi
83fd87fb 55 push ebp
83fd87fc 8bec mov ebp,esp
83fd87fe 807d0c00 cmp byte ptr [ebp+0Ch],0 //判断是设置回调还是清除回调.
83fd8802 53 push ebx
83fd8803 56 push esi //保存寄存器环境.
83fd8804 57 push edi
83fd8805 0f84fa000000 je nt!PspSetCreateProcessNotifyRoutine+0x10a (83fd8905) 是否删除回调 == 0 跳转.也就是设置回调. 删除回调走上边.
====================> 删除回调走的位置
nt!PspSetCreateProcessNotifyRoutine+0x12:
83fd880b 648b3524010000 mov esi,dword ptr fs:[124h]
83fd8812 66ff8e84000000 dec word ptr [esi+84h]
83fd8819 33db xor ebx,ebx
83fd881b c7450ce06cf883 mov dword ptr [ebp+0Ch],offset nt!PspCreateProcessNotifyRoutine (83f86ce0) //获得回调函数数组地址.
nt!PspSetCreateProcessNotifyRoutine+0x29:
83fd8822 ff750c push dword ptr [ebp+0Ch] //数组地址压栈.
83fd8825 e88ea90d00 call nt!ExReferenceCallBackBlock (840b31b8) //逆向ExReferenceCallBackBlock
83fd882a 8bf8 mov edi,eax
83fd882c 85ff test edi,edi
83fd882e 7439 je nt!PspSetCreateProcessNotifyRoutine+0x6e (83fd8869)
nt!PspSetCreateProcessNotifyRoutine+0x37:
83fd8830 8b4f08 mov ecx,dword ptr [edi+8]
83fd8833 e81b3cf2ff call nt!ExGetCallBackBlockRoutine (83efc453)
83fd8838 3b4508 cmp eax,dword ptr [ebp+8]
83fd883b 7522 jne nt!PspSetCreateProcessNotifyRoutine+0x64 (83fd885f)
nt!PspSetCreateProcessNotifyRoutine+0x44:
83fd883d 85c9 test ecx,ecx
83fd883f 7509 jne nt!PspSetCreateProcessNotifyRoutine+0x4f (83fd884a)
nt!PspSetCreateProcessNotifyRoutine+0x48:
83fd8841 384d10 cmp byte ptr [ebp+10h],cl
83fd8844 7519 jne nt!PspSetCreateProcessNotifyRoutine+0x64 (83fd885f)
nt!PspSetCreateProcessNotifyRoutine+0x4d:
83fd8846 eb08 jmp nt!PspSetCreateProcessNotifyRoutine+0x55 (83fd8850)
nt!PspSetCreateProcessNotifyRoutine+0x4f:
83fd884a 807d1000 cmp byte ptr [ebp+10h],0
83fd884e 740f je nt!PspSetCreateProcessNotifyRoutine+0x64 (83fd885f)
nt!PspSetCreateProcessNotifyRoutine+0x55:
83fd8850 8b450c mov eax,dword ptr [ebp+0Ch]
83fd8853 57 push edi
83fd8854 33c9 xor ecx,ecx
83fd8856 e8abfeffff call nt!ExCompareExchangeCallBack (83fd8706)
83fd885b 84c0 test al,al
83fd885d 7547 jne nt!PspSetCreateProcessNotifyRoutine+0xab (83fd88a6)
nt!PspSetCreateProcessNotifyRoutine+0x64:
83fd885f 8b450c mov eax,dword ptr [ebp+0Ch]
83fd8862 8bcf mov ecx,edi
83fd8864 e883aa0d00 call nt!ExDereferenceCallBackBlock (840b32ec)
nt!PspSetCreateProcessNotifyRoutine+0x6e:
83fd8869 83450c04 add dword ptr [ebp+0Ch],4
83fd886d 43 inc ebx
83fd886e 83fb40 cmp ebx,40h
83fd8871 72af jb nt!PspSetCreateProcessNotifyRoutine+0x29 (83fd8822)
nt!PspSetCreateProcessNotifyRoutine+0x78:
83fd8873 66ff8684000000 inc word ptr [esi+84h]
83fd887a 0fb78684000000 movzx eax,word ptr [esi+84h]
83fd8881 6685c0 test ax,ax
83fd8884 7516 jne nt!PspSetCreateProcessNotifyRoutine+0xa1 (83fd889c)
nt!PspSetCreateProcessNotifyRoutine+0x8b:
83fd8886 8d4640 lea eax,[esi+40h]
83fd8889 3900 cmp dword ptr [eax],eax
83fd888b 740f je nt!PspSetCreateProcessNotifyRoutine+0xa1 (83fd889c)
nt!PspSetCreateProcessNotifyRoutine+0x92:
83fd888d 6683be8600000000 cmp word ptr [esi+86h],0
83fd8895 7505 jne nt!PspSetCreateProcessNotifyRoutine+0xa1 (83fd889c)
nt!PspSetCreateProcessNotifyRoutine+0x9c:
83fd8897 e8fd3be9ff call nt!KiCheckForKernelApcDelivery (83e6c499)
nt!PspSetCreateProcessNotifyRoutine+0xa1:
83fd889c b87a0000c0 mov eax,0C000007Ah
83fd88a1 e9c5000000 jmp nt!PspSetCreateProcessNotifyRoutine+0x170 (83fd896b)
nt!PspSetCreateProcessNotifyRoutine+0xab:
83fd88a6 83c9ff or ecx,0FFFFFFFFh
83fd88a9 807d1000 cmp byte ptr [ebp+10h],0
83fd88ad b8e46df883 mov eax,offset nt!PspCreateProcessNotifyRoutineCount (83f86de4)
83fd88b2 7405 je nt!PspSetCreateProcessNotifyRoutine+0xbe (83fd88b9)
nt!PspSetCreateProcessNotifyRoutine+0xb9:
83fd88b4 b8e06df883 mov eax,offset nt!PspCreateProcessNotifyRoutineExCount (83f86de0)
nt!PspSetCreateProcessNotifyRoutine+0xbe:
83fd88b9 f00fc108 lock xadd dword ptr [eax],ecx
83fd88bd 8d049de06cf883 lea eax,nt!PspCreateProcessNotifyRoutine (83f86ce0)[ebx*4]
83fd88c4 8bcf mov ecx,edi
83fd88c6 e821aa0d00 call nt!ExDereferenceCallBackBlock (840b32ec)
83fd88cb 66ff8684000000 inc word ptr [esi+84h]
83fd88d2 0fb78684000000 movzx eax,word ptr [esi+84h]
83fd88d9 6685c0 test ax,ax
83fd88dc 7516 jne nt!PspSetCreateProcessNotifyRoutine+0xf9 (83fd88f4)
nt!PspSetCreateProcessNotifyRoutine+0xe3:
83fd88de 8d4640 lea eax,[esi+40h]
83fd88e1 3900 cmp dword ptr [eax],eax
83fd88e3 740f je nt!PspSetCreateProcessNotifyRoutine+0xf9 (83fd88f4)
nt!PspSetCreateProcessNotifyRoutine+0xea:
83fd88e5 6683be8600000000 cmp word ptr [esi+86h],0
83fd88ed 7505 jne nt!PspSetCreateProcessNotifyRoutine+0xf9 (83fd88f4)
nt!PspSetCreateProcessNotifyRoutine+0xf4:
83fd88ef e8a53be9ff call nt!KiCheckForKernelApcDelivery (83e6c499)
nt!PspSetCreateProcessNotifyRoutine+0xf9:
83fd88f4 8bcf mov ecx,edi
83fd88f6 e890f41600 call nt!ExWaitForCallBacks (84147d8b)
83fd88fb 57 push edi
83fd88fc e814780e00 call nt!SepFreeCapturedString (840c0115)
nt!PspSetCreateProcessNotifyRoutine+0x106:
83fd8901 33c0 xor eax,eax
83fd8903 eb66 jmp nt!PspSetCreateProcessNotifyRoutine+0x170 (83fd896b)
// 设置回调会走的路线.
nt!PspSetCreateProcessNotifyRoutine+0x10a:
83fd8905 807d1000 cmp byte ptr [ebp+10h],0 //判断第三个参数是否为0
83fd8909 7413 je nt!PspSetCreateProcessNotifyRoutine+0x123 (83fd891e)
nt!PspSetCreateProcessNotifyRoutine+0x110:
83fd890b ff7508 push dword ptr [ebp+8]
83fd890e e856affdff call nt!MmVerifyCallbackFunction (83fb3869)
83fd8913 85c0 test eax,eax
83fd8915 7507 jne nt!PspSetCreateProcessNotifyRoutine+0x123 (83fd891e)
nt!PspSetCreateProcessNotifyRoutine+0x11c:
83fd8917 b8220000c0 mov eax,0C0000022h
83fd891c eb4d jmp nt!PspSetCreateProcessNotifyRoutine+0x170 (83fd896b)
//第三个参数是默认Push 0.会到这里.
nt!PspSetCreateProcessNotifyRoutine+0x123:
83fd891e 33c0 xor eax,eax
83fd8920 384510 cmp byte ptr [ebp+10h],al
83fd8923 0f95c0 setne al // == 0 则设置al位. 如果比较滞后 ==0 相等.(zf=1) 则设置al位0 .如果不相等则al = 1.
83fd8926 50 push eax 0
83fd8927 ff7508 push dword ptr [ebp+8] 回调函数地址.
83fd892a e8a8fdffff call nt!ExAllocateCallBack (83fd86d7)
83fd892f 8bd8 mov ebx,eax
83fd8931 85db test ebx,ebx //判断ebx结果是否是0. 不是0 跳转.
83fd8933 7507 jne nt!PspSetCreateProcessNotifyRoutine+0x141 (83fd893c)
nt!PspSetCreateProcessNotifyRoutine+0x13a:
83fd8935 b89a0000c0 mov eax,0C000009Ah
83fd893a eb2f jmp nt!PspSetCreateProcessNotifyRoutine+0x170 (83fd896b)
nt!PspSetCreateProcessNotifyRoutine+0x141:
83fd893c bee06cf883 mov esi,offset nt!PspCreateProcessNotifyRoutine (83f86ce0) //不是0跳转到此位置. 获取数组.
83fd8941 33ff xor edi,edi
nt!PspSetCreateProcessNotifyRoutine+0x148:
83fd8943 6a00 push 0
83fd8945 8bcb mov ecx,ebx ecx = ExAllocateCallBack 返回值.
83fd8947 8bc6 mov eax,esi eax = 数组
83fd8949 e8b8fdffff call nt!ExCompareExchangeCallBack (83fd8706) //应该是遍历数组.进行比较.设置回调.
83fd894e 84c0 test al,al
83fd8950 7520 jne nt!PspSetCreateProcessNotifyRoutine+0x177 (83fd8972)
nt!PspSetCreateProcessNotifyRoutine+0x157:
83fd8952 83c704 add edi,4
83fd8955 83c604 add esi,4
83fd8958 81ff00010000 cmp edi,100h
83fd895e 72e3 jb nt!PspSetCreateProcessNotifyRoutine+0x148 (83fd8943)
nt!PspSetCreateProcessNotifyRoutine+0x165:
83fd8960 53 push ebx
83fd8961 e8af770e00 call nt!SepFreeCapturedString (840c0115)
83fd8966 b80d0000c0 mov eax,0C000000Dh
nt!PspSetCreateProcessNotifyRoutine+0x170:
83fd896b 5f pop edi
83fd896c 5e pop esi
83fd896d 5b pop ebx
83fd896e 5d pop ebp
83fd896f c20c00 ret 0Ch
nt!PspSetCreateProcessNotifyRoutine+0x177:
83fd8972 33c9 xor ecx,ecx
83fd8974 41 inc ecx
83fd8975 807d1000 cmp byte ptr [ebp+10h],0
83fd8979 7525 jne nt!PspSetCreateProcessNotifyRoutine+0x1a5 (83fd89a0)
nt!PspSetCreateProcessNotifyRoutine+0x180:
83fd897b b8e46df883 mov eax,offset nt!PspCreateProcessNotifyRoutineCount (83f86de4)
83fd8980 f00fc108 lock xadd dword ptr [eax],ecx
83fd8984 a1786bf883 mov eax,dword ptr [nt!PspNotifyEnableMask (83f86b78)]
83fd8989 a802 test al,2
83fd898b 0f8570ffffff jne nt!PspSetCreateProcessNotifyRoutine+0x106 (83fd8901)
nt!PspSetCreateProcessNotifyRoutine+0x196:
83fd8991 b8786bf883 mov eax,offset nt!PspNotifyEnableMask (83f86b78)
83fd8996 f00fba2801 lock bts dword ptr [eax],1
83fd899b e961ffffff jmp nt!PspSetCreateProcessNotifyRoutine+0x106 (83fd8901)
nt!PspSetCreateProcessNotifyRoutine+0x1a5:
83fd89a0 b8e06df883 mov eax,offset nt!PspCreateProcessNotifyRoutineExCount (83f86de0)
83fd89a5 f00fc108 lock xadd dword ptr [eax],ecx
83fd89a9 a1786bf883 mov eax,dword ptr [nt!PspNotifyEnableMask (83f86b78)]
83fd89ae a804 test al,4
83fd89b0 0f854bffffff jne nt!PspSetCreateProcessNotifyRoutine+0x106 (83fd8901)
nt!PspSetCreateProcessNotifyRoutine+0x1bb:
83fd89b6 b8786bf883 mov eax,offset nt!PspNotifyEnableMask (83f86b78)
83fd89bb f00fba2802 lock bts dword ptr [eax],2
83fd89c0 e93cffffff jmp nt!PspSetCreateProcessNotifyRoutine+0x106 (83fd8901)
<===================================================================================>
通过上面可以看到 获得的回调函数数组. 并且函数数组入栈. 那么就需要逆向一下新的函数了
首先看下回调函数数组里面的内容.
83f86ce0 = 回调函数数组
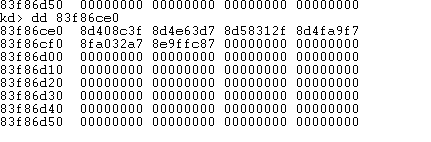
找到回调函数数组会发现这个值不是回调函数地址.
下面回调 ExReferenceCallBackBlock 传入回调函数地址.所以肯定有对 其的操作
3.逆向 ExReferenceCallBackBlock
kd> uf ExReferenceCallBackBlock
nt!ExReferenceCallBackBlock:
840b31b8 8bff mov edi,edi
840b31ba 55 push ebp
840b31bb 8bec mov ebp,esp
840b31bd 8b5508 mov edx,dword ptr [ebp+8] edx = 数组地址
840b31c0 8b0a mov ecx,dword ptr [edx] ecx = 数组[0] 第一项.
840b31c2 53 push ebx
840b31c3 56 push esi
840b31c4 57 push edi
840b31c5 6a07 push 7
840b31c7 5b pop ebx ebx = 7
840b31c8 84cb test bl,cl 判断bl 跟 cl 肯定不等于 0 .
840b31ca 7417 je nt!ExReferenceCallBackBlock+0x2b (840b31e3)
// bl cl 不会 = 0,所以走此位置.
nt!ExReferenceCallBackBlock+0x14:
840b31cc 8d41ff lea eax,[ecx-1] 不相等的情况 eax = [ecx - 1] 的地址. eax = &(数组[0]+1)的地址 例如数组内容为: 8d408c3f 现在成了 8d408c3E
840b31cf 8bf0 mov esi,eax esi = [ecx - 1]
840b31d1 8bfa mov edi,edx edi = 数组地址
840b31d3 8bc1 mov eax,ecx eax = 数组[0]
840b31d5 f00fb137 lock cmpxchg dword ptr [edi],esi 数组[0] = &([数组[0] +1] 的值.
840b31d9 3bc1 cmp eax,ecx 数组[0] == 数组[0]
840b31db 7406 je nt!ExReferenceCallBackBlock+0x2b (840b31e3)
nt!ExReferenceCallBackBlock+0x25:
840b31dd 8bc8 mov ecx,eax
840b31df 84c3 test bl,al
840b31e1 75e9 jne nt!ExReferenceCallBackBlock+0x14 (840b31cc)
都相等会跳转此处.
nt!ExReferenceCallBackBlock+0x2b:
840b31e3 85c9 test ecx,ecx ecx = &(数组[0] + 1)
840b31e5 7507 jne nt!ExReferenceCallBackBlock+0x36 (840b31ee) //大部分情况下会跳转.因为数组内容可能不为0
nt!ExReferenceCallBackBlock+0x2f:
840b31e7 33c0 xor eax,eax
840b31e9 e9f2000000 jmp nt!ExReferenceCallBackBlock+0x122 (840b32e0)
//跳转位置.
nt!ExReferenceCallBackBlock+0x36:
840b31ee 8bc1 mov eax,ecx eax = 数组[0]
840b31f0 23c3 and eax,ebx eax = 数组[0] & 7; eax = 7;
840b31f2 0f859a000000 jne nt!ExReferenceCallBackBlock+0xd4 (840b3292)
nt!ExReferenceCallBackBlock+0x40:
840b31f8 648b3524010000 mov esi,dword ptr fs:[124h]
840b31ff 66ff8e86000000 dec word ptr [esi+86h]
840b3206 6a11 push 11h
840b3208 b9d807f883 mov ecx,offset nt!ExpCallBackFlush (83f807d8)
840b320d 5f pop edi
840b320e 8bd9 mov ebx,ecx
840b3210 f00fb13b lock cmpxchg dword ptr [ebx],edi
840b3214 85c0 test eax,eax
840b3216 7408 je nt!ExReferenceCallBackBlock+0x68 (840b3220)
nt!ExReferenceCallBackBlock+0x60:
840b3218 e80c56e4ff call nt!ExfAcquirePushLockShared (83ef8829)
840b321d 8b5508 mov edx,dword ptr [ebp+8]
nt!ExReferenceCallBackBlock+0x68:
840b3220 8b3a mov edi,dword ptr [edx]
840b3222 83e7f8 and edi,0FFFFFFF8h
840b3225 7423 je nt!ExReferenceCallBackBlock+0x92 (840b324a)
nt!ExReferenceCallBackBlock+0x6f:
840b3227 8b0f mov ecx,dword ptr [edi]
840b3229 83e1fe and ecx,0FFFFFFFEh
840b322c 8d4102 lea eax,[ecx+2]
840b322f 8bd0 mov edx,eax
840b3231 8bdf mov ebx,edi
840b3233 8bc1 mov eax,ecx
840b3235 f00fb113 lock cmpxchg dword ptr [ebx],edx
840b3239 3bc1 cmp eax,ecx
840b323b 740d je nt!ExReferenceCallBackBlock+0x92 (840b324a)
nt!ExReferenceCallBackBlock+0x85:
840b323d 8bcf mov ecx,edi
840b323f e806a5e2ff call nt!ExfAcquireRundownProtection (83edd74a)
840b3244 84c0 test al,al
840b3246 7502 jne nt!ExReferenceCallBackBlock+0x92 (840b324a)
nt!ExReferenceCallBackBlock+0x90:
840b3248 33ff xor edi,edi
nt!ExReferenceCallBackBlock+0x92:
840b324a b9d807f883 mov ecx,offset nt!ExpCallBackFlush (83f807d8)
840b324f 6a11 push 11h
840b3251 33d2 xor edx,edx
840b3253 8bd9 mov ebx,ecx
840b3255 58 pop eax
840b3256 f00fb113 lock cmpxchg dword ptr [ebx],edx
840b325a 83f811 cmp eax,11h
840b325d 7405 je nt!ExReferenceCallBackBlock+0xac (840b3264)
nt!ExReferenceCallBackBlock+0xa7:
840b325f e80a54e4ff call nt!ExfReleasePushLockShared (83ef866e)
nt!ExReferenceCallBackBlock+0xac:
840b3264 66ff8686000000 inc word ptr [esi+86h]
840b326b 0fb78686000000 movzx eax,word ptr [esi+86h]
840b3272 6685c0 test ax,ax
840b3275 750c jne nt!ExReferenceCallBackBlock+0xcb (840b3283)
nt!ExReferenceCallBackBlock+0xbf:
840b3277 83c640 add esi,40h
840b327a 3936 cmp dword ptr [esi],esi
840b327c 7405 je nt!ExReferenceCallBackBlock+0xcb (840b3283)
nt!ExReferenceCallBackBlock+0xc6:
840b327e e81692dbff call nt!KiCheckForKernelApcDelivery (83e6c499)
nt!ExReferenceCallBackBlock+0xcb:
840b3283 85ff test edi,edi
840b3285 0f845cffffff je nt!ExReferenceCallBackBlock+0x2f (840b31e7)
nt!ExReferenceCallBackBlock+0xd3:
840b328b eb51 jmp nt!ExReferenceCallBackBlock+0x120 (840b32de)
//跳转到此位置.
nt!ExReferenceCallBackBlock+0xd4:
840b3292 83e1f8 and ecx,0FFFFFFF8h ecx = 数组[0] & 0xFFFFFFF8 结果得出是一个地址. 数组里面的值已经不是以前的值了. 8d408c3f 变成了 8d408c3E
840b3295 8bf9 mov edi,ecx 结果给 edi保存
840b3297 83f801 cmp eax,1
840b329a 7542 jne nt!ExReferenceCallBackBlock+0x120 (840b32de)
nt!ExReferenceCallBackBlock+0xde:
840b329c 8bd3 mov edx,ebx
840b329e e8f1c4e1ff call nt!ExAcquireRundownProtectionEx (83ecf794)
840b32a3 84c0 test al,al
840b32a5 7437 je nt!ExReferenceCallBackBlock+0x120 (840b32de)
nt!ExReferenceCallBackBlock+0xe9:
840b32a7 8b4508 mov eax,dword ptr [ebp+8]
840b32aa 8b08 mov ecx,dword ptr [eax]
840b32ac 8bc1 mov eax,ecx
840b32ae eb1d jmp nt!ExReferenceCallBackBlock+0x10f (840b32cd)
nt!ExReferenceCallBackBlock+0xf2:
840b32b0 8bc1 mov eax,ecx
840b32b2 83e0f8 and eax,0FFFFFFF8h
840b32b5 3bf8 cmp edi,eax
840b32b7 751c jne nt!ExReferenceCallBackBlock+0x117 (840b32d5)
nt!ExReferenceCallBackBlock+0xfb:
840b32b9 8b7508 mov esi,dword ptr [ebp+8]
840b32bc 8d4107 lea eax,[ecx+7]
840b32bf 8bd0 mov edx,eax
840b32c1 8bc1 mov eax,ecx
840b32c3 f00fb116 lock cmpxchg dword ptr [esi],edx
840b32c7 3bc1 cmp eax,ecx
840b32c9 7413 je nt!ExReferenceCallBackBlock+0x120 (840b32de)
nt!ExReferenceCallBackBlock+0x10d:
840b32cb 8bc8 mov ecx,eax
nt!ExReferenceCallBackBlock+0x10f:
840b32cd 23c3 and eax,ebx
840b32cf 03c3 add eax,ebx
840b32d1 3bc3 cmp eax,ebx
840b32d3 76db jbe nt!ExReferenceCallBackBlock+0xf2 (840b32b0)
nt!ExReferenceCallBackBlock+0x117:
840b32d5 8bd3 mov edx,ebx
840b32d7 8bcf mov ecx,edi
840b32d9 e8f96cdcff call nt!ExReleaseRundownProtectionEx (83e79fd7)
//eax = 7 不是1.所以直接跳转到结束位置
nt!ExReferenceCallBackBlock+0x120:
840b32de 8bc7 mov eax,edi 结果给eax.进行返回.
nt!ExReferenceCallBackBlock+0x122:
840b32e0 5f pop edi
840b32e1 5e pop esi
840b32e2 5b pop ebx
840b32e3 5d pop ebp
840b32e4 c20400 ret 4
通过逆向次函数可以得知. 函数数组[0]的内容被修改了. 修改为 -1的值. 如上面看到的数组的内容为:

现在首内容 0x8d408c3f的值会变为 0x8d408c3e
往下有很多分支没有走. 最后会进行解密操作得出函数地址.
如: 0x8d408c3e & 0xFFFFFFF8 = 函数地址表.
如下:
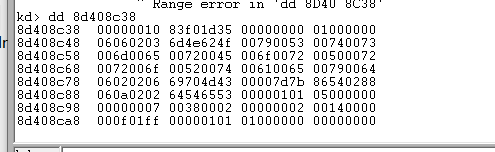
这个函数地址表的第二项就是我们要找的函数地址.
现在是0x83f01d35 去pchunter中查看.

但是上面会有一个问题. 0x8d408c3f的值会变为 0x8d408c3e 直接用 0x8d408c3f & 0xFFFFFFF8 的结果也是一样的.
所以可以忽略上面修改值的事情.
可以得出一个公式 函数地址 = *((数组[n] & 0xFFFFFFF8) + 4);
可以套用一下公式.进行一次计算.
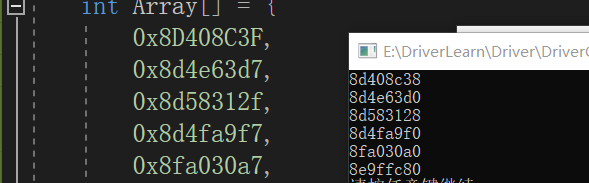
使用代码可以遍历出函数地址表. 表中第二项才是函数地址. 随便找一个举例

它的第二项是8c5f89d8 说明找对了.
三丶总结
通过逆向可以找到数组. 那么可以进行如下操作
1.摘除数组.传入函数地址.调用 PsSetCreateProcessNotifyRoutine 第二个参数为TRUE即可摘掉.你也可以自己摘.就是相当于自己实现了一下这个函数摘除钩子的代码
2.进程回调优先级.可以找到数组.将你的回调写入到数组第一项.这样你的就会优先到来. 这个没试过.算是一个思路吧.
后面逆向下64位的.