网络环境,客户端是路由下面的子网掩码的ROS(也就是没有公网IP,为城域网的ROS),服务端是具有公网IP的ROS。
该文章可以解决运营商对于只有城域网IP的ROS,对于各种隧道协议全部限速的问题,具体限速情况,可以看我其他的文章:
https://www.cnblogs.com/itfat/p/13326602.html
测速推荐工具:
https://www.cnblogs.com/itfat/p/13346324.html
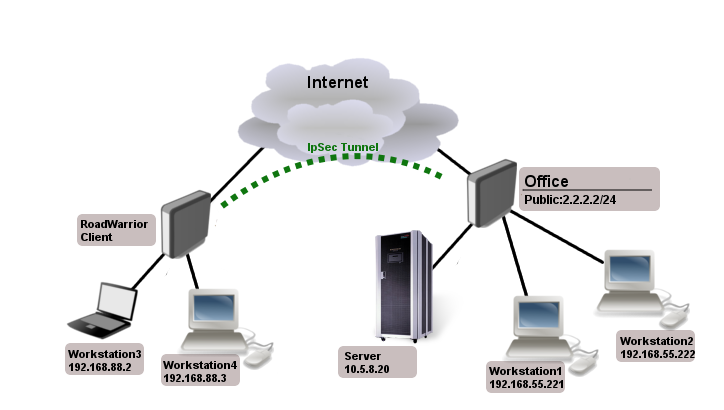
拓扑图:
配置的说明可以见我另外的文章:
https://www.cnblogs.com/itfat/p/13390467.html
服务端:
创建一个回环接口,这个ip用于创建ipsec隧道的服务端IP
/interface bridge
add name=loopback-ipsec
/ip address
add address=172.16.99.1 interface=loopback-ipsec network=172.16.99.1
/ip ipsec profile
add enc-algorithm=aes-256 hash-algorithm=sha256 name=ike2
/ip ipsec proposal
add auth-algorithms=sha256 enc-algorithms=aes-256-cbc name=ike2 pfs-group=none
子网掩码用30位,因为是点到点,那么下发IP,包括服务端就2个ip
/ip ipsec mode-config
add address=172.16.99.2 address-prefix-length=30 name=ike2-conf split-include=172.16.99.1/32 system-dns=no
/ip ipsec policy group
add name=ike2-policies
/ip ipsec policy
disable numbers=0
/ip ipsec policy
add dst-address=172.16.99.2/32 group=ike2-policies proposal=ike2 src-address=172.16.99.1/32 template=yes
/ip ipsec peer
add exchange-mode=ike2 name=ike2 passive=yes profile=ike2
/ip ipsec identity
add generate-policy=port-strict mode-config=ike2-conf peer=ike2 secret=密码 policy-template-group=ike2-policies
客户端:
/ip ipsec profile
add enc-algorithm=aes-256 hash-algorithm=sha256 name=ike2-rw
/ip ipsec proposal
add auth-algorithms=sha256 enc-algorithms=aes-256-cbc name=ike2-rw pfs-group=none
/ip ipsec policy group
add name=ike2-rw
/ip ipsec policy
disable numbers=0
/ip ipsec policy
add dst-address=172.16.99.1/32 src-address=172.16.99.2/32 group=ike2-rw proposal=ike2-rw template=yes
/ip ipsec peer
add address=ipsec服务端公网IP/32 exchange-mode=ike2 name=ike2-rw-client profile=ike2-rw
请注意,虽然我们客户端没有配置mode-config,但是这里必须写上默认的request-only
/ip ipsec identity
add generate-policy=port-strict mode-config=request-only peer=ike2-rw-client policy-template-group=ike2-rw secret=密码
上述就可以把ipsec隧道建立起来了,然后你再创建两边的GRE,同时创建隧道IP
服务端:
/interface gre
add local-address=172.16.99.1 name=gre-ipsec-to-yanfasanqu remote-address=172.16.99.2
/ip address
add address=172.16.101.1 interface=gre-ipsec-to-yanfasanqu network=172.16.101.2
最后起OSPF,点到点网络直接填对端IP
/routing ospf network
add area=backbone network=172.16.101.2/32
客户端
/interface gre
add local-address=172.16.99.2 name=gre-ipsec-to-hangzhou remote-address=172.16.99.1
/ip address
add address=172.16.101.2 interface=gre-ipsec-to-hangzhou network=172.16.101.1
/routing ospf network
add area=backbone network=172.16.101.1/32