‘坏兔子’勒索软件潜入俄罗斯,乌克兰
This post was researched and written by Christiaan Beek, Tim Hux, David Marcus, Charles McFarland, Douglas McKee, and Raj Samani.
McAfee is currently investigating a ransomware campaign known as BadRabbit, which initially infected targets in Russia and the Ukraine. We are also investigating reports of infected systems in Germany, Turkey, and Bulgaria and will provide updates as more information becomes available. For McAfee product coverage, please see “How McAfee Products Can Protect Against BadRabbit Ransomware.”
When victims visit the following site, a dropper is downloaded:
hxxp://1dnscontrol[dot]com/flash_install.php
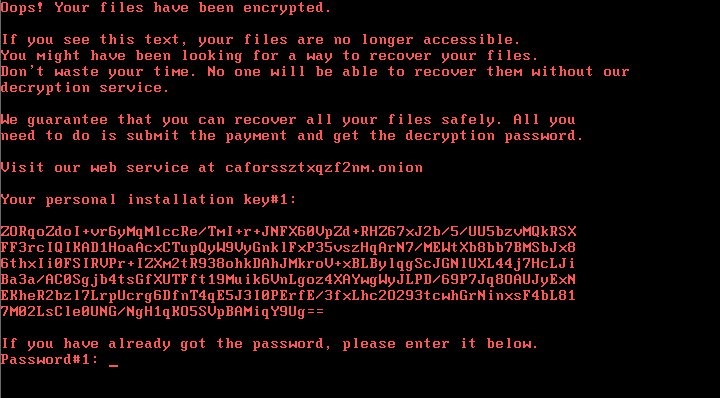
After infection, the victim sees the following screen:

这篇文章由Christiaan Beek, Tim Hux, David Marcus, Charles McFarland, Douglas McKee和 Raj Samani研究撰写。 麦咖啡目前正在调查一个称为坏兔子的勒索活动,最初的感染目标是在俄罗斯和乌克兰。我们也在调查德国,土耳其和保加利亚受感染系统的报告,并将提供更多的有效信息。对于麦咖啡的产品,请查看“麦咖啡的产品如何防御坏兔子勒索软件”。 当受害者访问下面的网站时,一个程序释放器将会被下载: hxxp://1dnscontrol[dot]com/flash_install.php 被感染后,受害者的屏幕会显示如下:
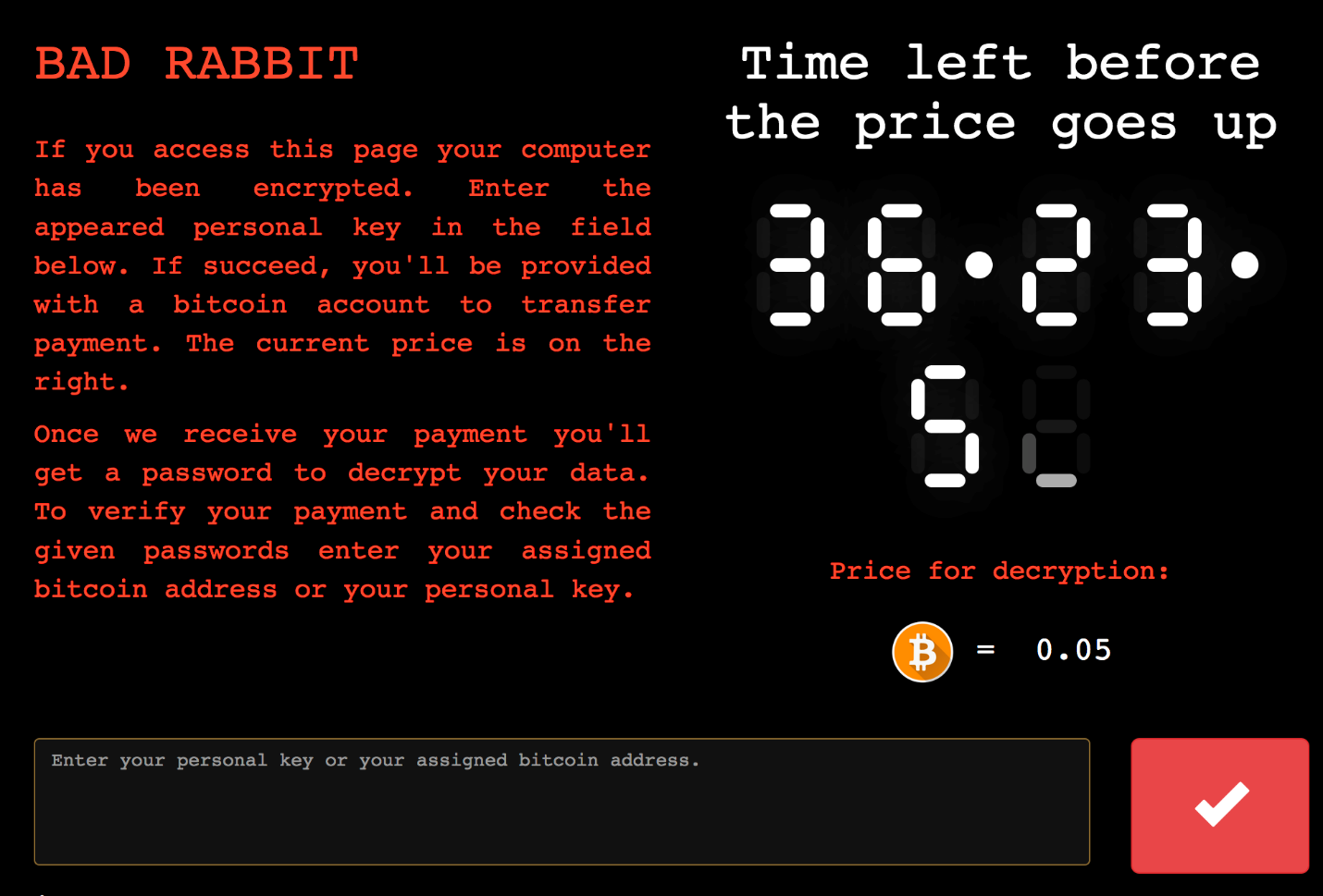
The ransomware is currently charging 0.05 Bitcoin; however, there is no confirmation that paying the ransom will result in a decryption key being provided.
A decryption site at the following .onion (Tor) domain displays the time that victims have left before the price goes up:
caforssztxqzf2nm[dot]onion

勒索软件目前的收费是0.05比特币;然而支付赎金后可否获取解密秘钥还无法确认。 下面是个解密网站。Tor域显示了距离价格上涨,受害者还有多少时间: caforssztxqzf2nm[dot]onion

勒索软件目前的收费是0.05比特币;然而支付赎金后可否获取解密秘钥还无法确认。 下面这个.onion(Tor)域名的解密网站,显示了距离价格上涨,受害者还有多少时间: caforssztxqzf2nm.onion
Files with the following extensions are encrypted:

如下的扩展文件会被加密
.3ds.7z.accdb.ai.asm.asp.aspx.avhd.back.bak.bmp.brw.c.cab.cc.cer.cfg.conf.cpp.crt.cs.ctl.cxx.dbf .der.dib.disk.djvu.doc.docx.dwg.eml.fdb.gz.h.hdd.hpp.hxx.iso.java.jfif.jpe.jpeg.jpg.js.kdbx.key .mail.mdb.msg.nrg.odc.odf.odg.odi.odm.odp.ods.odt.ora.ost.ova.ovf.p12.p7b.p7c.pdf.pem.pfx .php.pmf.png.ppt.pptx.ps1.pst.pvi.py.pyc.pyw.qcow.qcow2.rar.rb.rtf.scm.sln.sql.tar.tib.tif.tiff .vb.vbox.vbs.vcb.vdi.vfd.vhd.vhdx.vmc.vmdk.vmsd.vmtm.vmx.vsdx.vsv.work.xls.xlsx.xml.xvd.zip.
The malware starts a command-line with following values:

恶意软件以下面的值启动命令行:
Cmd /c schtasks /Create /RU SYSTEM /SC ONSTART /TN rhaegal /TR “C:Windowssystem32cmd.exe /C Start ”” ”C:Windowsdispci.exe” -id 1082924949 && exit”
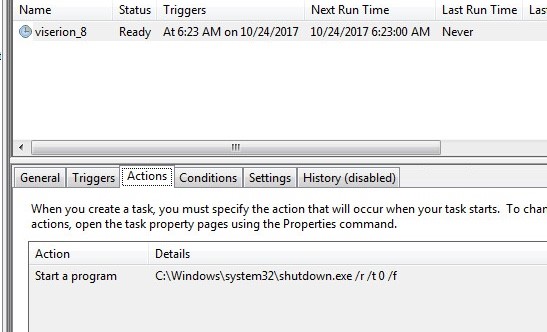
“/TN rheagal” refers to a system account with the name rhaegal used to create the scheduled task and start the ransomware file dispci.exe. Rhaegal is likely a reference to a dragon from the popular TV show “Game of Thrones.” In fact, three dragon names—Rhaegal, Viserion, and Drogon—are used in relation to the following scheduled tasks:

“/TN rheagal”指的是一个名为“rhaegal”的系统账户,用于创建计划任务并启动勒索软件“dispci.exe”。 “Rhaegal”可能是引用自著名电视节目“权利的游戏”中的dragon。事实上三条龙的名字是-Rhaegal, Viserion和Drogon,它们都被用于如下的计划任务:
The malware then uses the following commands to clear security logs and delete the update sequence number (USN) change journal, which is used to recover files, for example:
Cmd /c wevtutil cl Setup & wevtutil cl System & wevtutil cl Security & wevtutil cl Application & fsutil usn deletejournal /D C:
The USN change journal provides a persistent log of all changes made to files on the volume, according to the Microsoft Developer Network. As files, directories, and other NTFS objects are added, deleted, and modified, NTFS enters records into the USN change journal, one for each volume on the computer. Each record indicates the type of change and the object changed. New records are appended to the end of the stream.
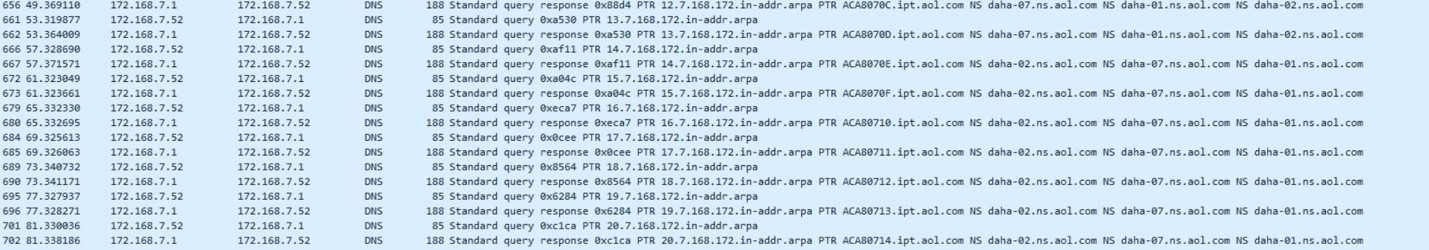
We also found a DNS query to ACA807(x)ipt.aol[dot]com, in which the “##” is a two-digit hex number from 00-FF ACA807##.ipt.aol[dot]com.

然后恶意软件使用下面的命令清除安全日志,并删除更新序列号更改日志,用以恢复文件,例如: Cmd /c wevtutil cl Setup & wevtutil cl System & wevtutil cl Security & wevtutil cl Application & fsutil usn deletejournal /D C: 根据微软开发者网络,USN更改日志,为受害者所有文件的修改提供了持久日志。对于电脑上的每一个受害者,当文件,目录和其他NTFS对象呗添加,删除和修改的时候,NTFS会进入更改日志中。每个报告指出了更改类型和对象的更改。新的报告被添加到末尾。 我们还发现一个DNS查询ACA807(x)ipt.aol[dot]com, 从00-FF ACA807##.ipt.aol[dot]com,其中的“##”事一个2位数的十六进制数。
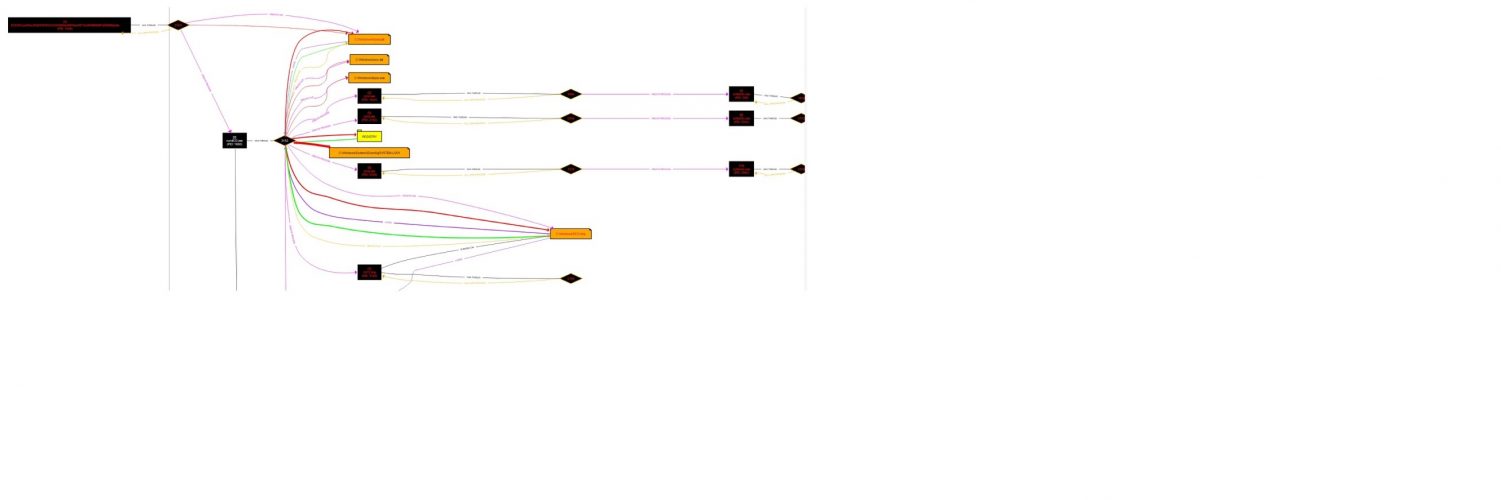
We created a graph of the events occurring during an infection by one of the BadRabbit samples. The initial binary loads itself into memory and kills the initial process. Further processes drop configuration, services files, and other artifacts used in the attacks. The graph ends with the creation of the preceding scheduled tasks.

我们创建了一幅图,记录了一个被坏兔子样本感染的事件。初始二进制文件把自己加载到内存,然后杀死初始进程。进一步处理掉攻击配置,服务文件和攻击中的其他手段。图在创建了预定计划任务结束。
Embedded Credentials
One of the samples (579fd8a0385482fb4c789561a30b09f25671e86422f40ef5cca2036b28f99648) seems to contain a list of default credentials with an attempt to brute-force credentials and get the scheduled tasks to execute the ransomware:

其中一个样本(579fd8a0385482fb4c789561a30b09f25671e86422f40ef5cca2036b28f99648)似乎包含了一个默认证书列表,这些证书是试图暴力破解的目标,并且获得一个执行恶意软件的计划任务:
- secret
- 123321
- zxc321
- zxc123
- qwerty123
- qwerty
- qwe321
- qwe123
- 111111
- password
- test123
- admin123Test123
- Admin123
- user123
- User123
- guest123
- Guest123
- administrator123
- Administrator123
- 1234567890
- 123456789
- 12345678
- 1234567
- 123456
- adminTest
- administrator
- netguest
- superuser
- nasadmin
- nasuser
- ftpadmin
- ftpuser
- backup
- operator
- other user
- support
- manager
- rdpadmin
- rdpuser
- user-1
- Administrator
Game of Thrones Fans?
It is common for attackers to use pop-culture references in their attacks. These attackers seem to have an interest in “Game of Thrones,” with at least three references to the series. Viserion, Rhaegal, and Drogon are names of scheduled tasks. GrayWorm, the name of a “Game of Thrones” commander, is the product name in the binary’s EXIF data.

《权利的游戏》的粉丝? 攻击者在他们的攻击中引用流行文化是很常见的。这些攻击者似乎对“权力的游戏”很感兴趣,至少有三次引用了该系列。Viserion, Rhaegal和Drogon是计划任务的名字。GrayWorm,一个“权力的游戏”中的指挥官,是二进制中 EXIF数据的产品名字。
Detection
There are currently three samples associated with this ransomware campaign, representing the dropper and the main executable. McAfee detects all three:

目前有三个与此勒索活动相关的样本,表示了程序释放器和主要可执行文件。麦咖啡检测到的三个如下:
- 630325cac09ac3fab908f903e3b00d0dadd5fdaa0875ed8496fcbb97a558d0da
- 8ebc97e05c8e1073bda2efb6f4d00ad7e789260afa2c276f0c72740b838a0a93
- 579fd8a0385482fb4c789561a30b09f25671e86422f40ef5cca2036b28f99648
