最新的wireshark可以直接识别出mptcp。
Wireshark is a widely used network analyzer that can capture network traffic, save the captured packets (*.pcap) for later analysis and most importantly helps with analyzing such packet traces. Wireshark supports many protocols, which means it is able to assign meaning to bytes (dissect in the wireshark nomenclature) and display it accordingly. In some cases as in the TCP dissector, Wireshark even builds some state to provide expert information, for instance to identify TCP retransmissions. So far, Wireshark supported stateless dissection of MPTCP, i.e., it could dissect MPTCP options correctly, without being able to identify Multipath TCP connections.
Since November 2015 and the following patch (i.e., starting from Wireshark >= 2.1), Wireshark now considers MPTCP as a separate protocol, and builds states for MPTCP as well, thus mimicking TCP dissection.
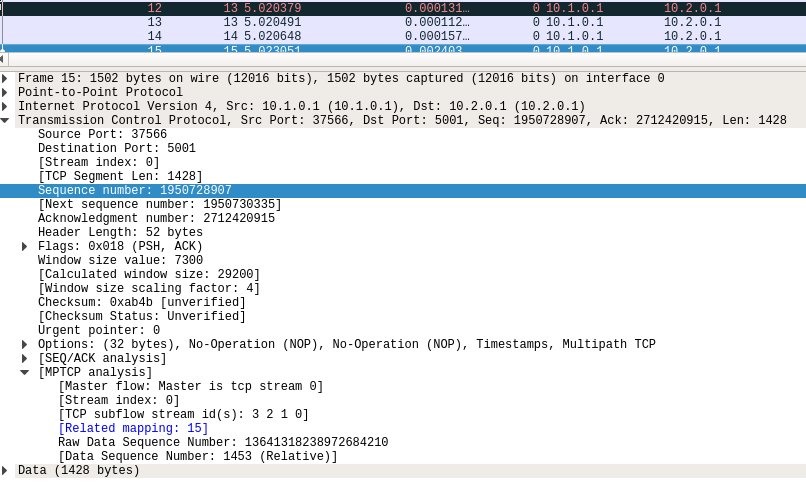
This means Wireshark is now able to (providing the matching features are enabled):
- map TCP subflows (tcp.stream) to MPTCP connections (mptcp.stream, see also mptcp.analysis.subflows).
- List MPTCP connections
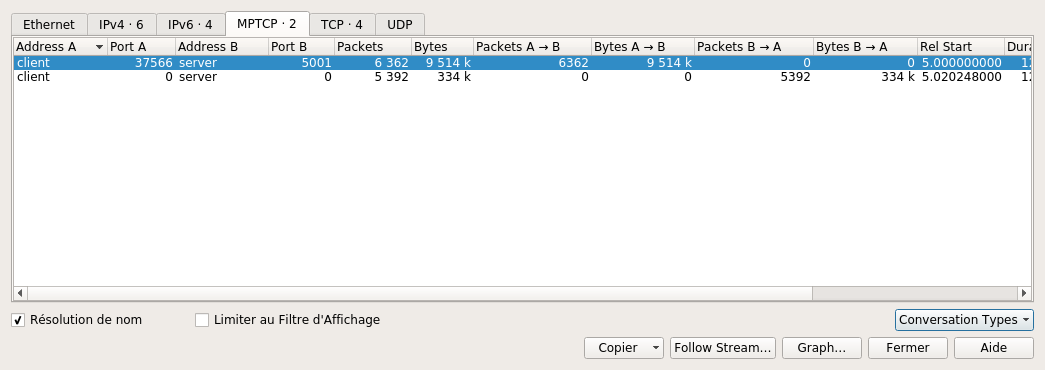
- identify the master subflows (*mptcp.master == 1*)
- check for mistmatched key/tokens and key/initial sequence data number (ISN)
- etc... start filtering packets with *mptcp.* and wireshark autocompletion should show the different possibilities
Full MPTCP dissection can be quite CPU-consuming, thus some options are disabled by default and can be enabled through the menu Edit -> Preferences -> Protocols ->MPTCP.
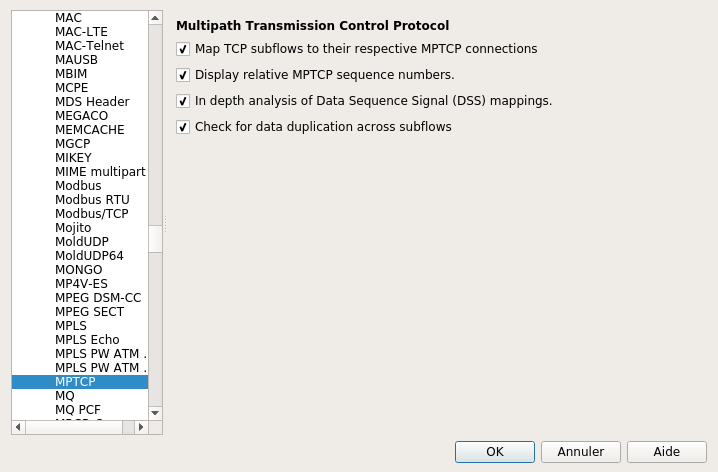
- Display relative MPTCP sequence numbers substracts the ISN to Data Sequence Numbers. This works only if the initial packets with the keys (3 way handshake) are captured and the wireshark option tcp relative sequence numbers is enabled.
- In depth analysis of data sequence signal (DSS) mappings tells wireshark to look for the packets which sent the DSS mappings that cover the current packet; wireshark then displays a clickable item that brings you to the packet. This feature enables the creation of interval trees (introduced especially for this feature), which should consume quite a bit of memory/CPU so use with care !
- Check for data duplication across subflows is a feature that was intended to help detect opportunistic reinjections or redundant schedulers but this is mostly experimental so use with care.
http://blog.multipath-tcp.org/blog/html/2016/08/23/mptcp_analyzer.html