LDAP简介
LDAP 代表 轻量级目录访问协议。在我的理解中ldap就是一个数据库。
在LDAP中,目录条目以分层树状结构排序。
传统上,这种结构反映了地理和组织边界,表示国家/地区的条目显示在树的顶部。下面是代表各州和国家组织的条目。它们下面可能是表示组织单位,人员,打印机,文档或您可以想到的任何其他内容的条目。图1.1显示了使用传统命令的实例LDAP目录树。

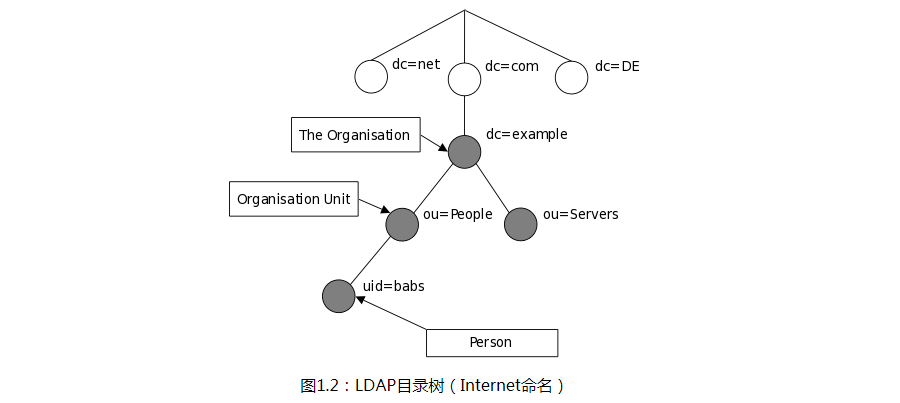
而现在一般使用基于域名来显示,因为它允许使用DNS定位目录服务。图1.2显示了使用基于域的命名的LDAP目录树示例。
LDAP使用场景
我暂时只用到了统一身份验证。
安装OPEN-LDAP
yum安装(首先需要epel源)
yum -y install openldap compat-openldap openldap-clients openldap-servers openldap-servers-sql openldap-devel migrationtools
目录结构
[root@zabbix1 openldap]# pwd /etc/openldap [root@zabbix1 openldap]# tree . ├── certs │ ├── cert8.db │ ├── key3.db │ ├── password │ └── secmod.db ├── check_password.conf ├── ldap.conf ├── schema │ ├── collective.ldif │ ├── collective.schema │ ├── corba.ldif │ ├── corba.schema │ ├── core.ldif │ ├── core.schema │ ├── cosine.ldif │ ├── cosine.schema │ ├── duaconf.ldif │ ├── duaconf.schema │ ├── dyngroup.ldif │ ├── dyngroup.schema │ ├── inetorgperson.ldif │ ├── inetorgperson.schema │ ├── java.ldif │ ├── java.schema │ ├── misc.ldif │ ├── misc.schema │ ├── nis.ldif │ ├── nis.schema │ ├── openldap.ldif │ ├── openldap.schema │ ├── pmi.ldif │ ├── pmi.schema │ ├── ppolicy.ldif │ └── ppolicy.schema └── slapd.d ├── cn=config │ ├── cn=schema │ │ ├── cn={0}core.ldif │ │ ├── cn={1}cosine.ldif │ │ ├── cn={2}nis.ldif │ │ └── cn={3}inetorgperson.ldif │ ├── cn=schema.ldif │ ├── olcDatabase={0}config.ldif │ ├── olcDatabase={-1}frontend.ldif │ ├── olcDatabase={1}monitor.ldif │ └── olcDatabase={2}hdb.ldif └── cn=config.ldif 5 directories, 42 files
/etc/openldap/slapd.conf:OpenLDAP的主配置文件,记录根域信息,管理员名称,密码,日志,权限等
/etc/openldap/slapd.d/*:这下面是/etc/openldap/slapd.conf配置信息生成的文件,每修改一次配置信息,这里的东西就要重新生成
/etc/openldap/schema/*:OpenLDAP的schema存放的地方
/var/lib/ldap/*:OpenLDAP的数据文件
/usr/share/openldap-servers/DB_CONFIG.example 模板数据库配置文件
/usr/share/openldap-servers/slapd.ldif 模板配置文件
OpenLDAP监听的端口:
默认监听端口:389(明文数据传输)
加密监听端口:636(密文数据传输)
初始化OpenLDAP的配置
修改CN,DC,DC,添加
olcRootPW 管理员密码 可以明文 可以密文 slappasswd生成密文密码
[root@zabbix1 openldap-servers]# cd /usr/share/openldap-servers
[root@zabbix1 lib]# cp /usr/share/openldap-servers/DB_CONFIG.example /var/lib/ldap/DB_CONFIG
[root@zabbix1 openldap-servers]# cat slapd.ldif # # See slapd-config(5) for details on configuration options. # This file should NOT be world readable. # dn: cn=config objectClass: olcGlobal cn: config olcArgsFile: /var/run/openldap/slapd.args olcPidFile: /var/run/openldap/slapd.pid # # TLS settings # olcTLSCACertificatePath: /etc/openldap/certs olcTLSCertificateFile: "OpenLDAP Server" olcTLSCertificateKeyFile: /etc/openldap/certs/password # # Do not enable referrals until AFTER you have a working directory # service AND an understanding of referrals. # #olcReferral: ldap://root.openldap.org # # Sample security restrictions # Require integrity protection (prevent hijacking) # Require 112-bit (3DES or better) encryption for updates # Require 64-bit encryption for simple bind # #olcSecurity: ssf=1 update_ssf=112 simple_bind=64 # # Load dynamic backend modules: # - modulepath is architecture dependent value (32/64-bit system) # - back_sql.la backend requires openldap-servers-sql package # - dyngroup.la and dynlist.la cannot be used at the same time # #dn: cn=module,cn=config #objectClass: olcModuleList #cn: module #olcModulepath: /usr/lib/openldap #olcModulepath: /usr/lib64/openldap #olcModuleload: accesslog.la #olcModuleload: auditlog.la #olcModuleload: back_dnssrv.la #olcModuleload: back_ldap.la #olcModuleload: back_mdb.la #olcModuleload: back_meta.la #olcModuleload: back_null.la #olcModuleload: back_passwd.la #olcModuleload: back_relay.la #olcModuleload: back_shell.la #olcModuleload: back_sock.la #olcModuleload: collect.la #olcModuleload: constraint.la #olcModuleload: dds.la #olcModuleload: deref.la #olcModuleload: dyngroup.la #olcModuleload: dynlist.la #olcModuleload: memberof.la #olcModuleload: pcache.la #olcModuleload: ppolicy.la #olcModuleload: refint.la #olcModuleload: retcode.la #olcModuleload: rwm.la #olcModuleload: seqmod.la #olcModuleload: smbk5pwd.la #olcModuleload: sssvlv.la #olcModuleload: syncprov.la #olcModuleload: translucent.la #olcModuleload: unique.la #olcModuleload: valsort.la # # Schema settings # dn: cn=schema,cn=config objectClass: olcSchemaConfig cn: schema include: file:///etc/openldap/schema/core.ldif # # Frontend settings # dn: olcDatabase=frontend,cn=config objectClass: olcDatabaseConfig objectClass: olcFrontendConfig olcDatabase: frontend # # Sample global access control policy: # Root DSE: allow anyone to read it # Subschema (sub)entry DSE: allow anyone to read it # Other DSEs: # Allow self write access # Allow authenticated users read access # Allow anonymous users to authenticate # #olcAccess: to dn.base="" by * read #olcAccess: to dn.base="cn=Subschema" by * read #olcAccess: to * # by self write # by users read # by anonymous auth # # if no access controls are present, the default policy # allows anyone and everyone to read anything but restricts # updates to rootdn. (e.g., "access to * by * read") # # rootdn can always read and write EVERYTHING! # # # Configuration database # dn: olcDatabase=config,cn=config objectClass: olcDatabaseConfig olcDatabase: config olcAccess: to * by dn.base="gidNumber=0+uidNumber=0,cn=peercred,cn=external,c n=auth" manage by * none # # Server status monitoring # dn: olcDatabase=monitor,cn=config objectClass: olcDatabaseConfig olcDatabase: monitor olcAccess: to * by dn.base="gidNumber=0+uidNumber=0,cn=peercred,cn=external,c n=auth" read by dn.base="cn=root,dc=test,dc=com" read by * none # # Backend database definitions # dn: olcDatabase=hdb,cn=config objectClass: olcDatabaseConfig objectClass: olcHdbConfig olcDatabase: hdb olcSuffix: dc=test,dc=com olcRootDN: cn=root,dc=test,dc=com olcRootPW: 1234qwer olcDbDirectory: /var/lib/ldap olcDbIndex: objectClass eq,pres olcDbIndex: ou,cn,mail,surname,givenname eq,pres,sub
导入配置数据库
[root@zabbix1 openldap-servers]# slapadd -n 0 -F /etc/openldap/slapd.d -l /usr/share/openldap-servers/slapd.ldif _#################### 100.00% eta none elapsed none fast! Closing DB...
启动slapd
1.第一种(因为上面我们使用了明文,所以这里有个警告)
[root@zabbix1 cn=config]# slapd -F /etc/openldap/slapd.d tlsmc_get_pin: INFO: Please note the extracted key file will not be protected with a PIN any more, however it will be still protected at least by file permissions.
2.第二种
[root@zabbix1 system]# systemctl status slapd ● slapd.service - OpenLDAP Server Daemon Loaded: loaded (/usr/lib/systemd/system/slapd.service; enabled; vendor preset: disabled) Active: failed (Result: exit-code) since Tue 2018-10-16 16:16:36 CST; 4min 43s ago Docs: man:slapd man:slapd-config man:slapd-hdb man:slapd-mdb file:///usr/share/doc/openldap-servers/guide.html Process: 16640 ExecStartPre=/usr/libexec/openldap/check-config.sh (code=exited, status=1/FAILURE) Main PID: 15521 (code=exited, status=0/SUCCESS) Oct 16 16:16:36 zabbix1 check-config.sh[16640]: Read/write permissions for DB file '/var/lib/ldap/log.0000000001' are required. Oct 16 16:16:36 zabbix1 runuser[16665]: pam_unix(runuser:session): session opened for user ldap by (uid=0) Oct 16 16:16:36 zabbix1 runuser[16665]: pam_unix(runuser:session): session closed for user ldap Oct 16 16:16:36 zabbix1 check-config.sh[16640]: Read/write permissions for DB file '/var/lib/ldap/id2entry.bdb' are required. Oct 16 16:16:36 zabbix1 runuser[16667]: pam_unix(runuser:session): session opened for user ldap by (uid=0) Oct 16 16:16:36 zabbix1 check-config.sh[16640]: Read/write permissions for DB file '/var/lib/ldap/dn2id.bdb' are required. Oct 16 16:16:36 zabbix1 systemd[1]: slapd.service: control process exited, code=exited status=1 Oct 16 16:16:36 zabbix1 systemd[1]: Failed to start OpenLDAP Server Daemon. Oct 16 16:16:36 zabbix1 systemd[1]: Unit slapd.service entered failed state. Oct 16 16:16:36 zabbix1 systemd[1]: slapd.service failed.
权限问题
[root@zabbix1 lib]# chown -R ldap.ldap /etc/openldap/ [root@zabbix1 lib]# chown -R ldap.ldap /var/lib/ldap/
[root@zabbix1 lib]# systemctl start slapd [root@zabbix1 lib]# systemctl status slapd ● slapd.service - OpenLDAP Server Daemon Loaded: loaded (/usr/lib/systemd/system/slapd.service; enabled; vendor preset: disabled) Active: active (running) since Tue 2018-10-16 16:24:19 CST; 2s ago Docs: man:slapd man:slapd-config man:slapd-hdb man:slapd-mdb file:///usr/share/doc/openldap-servers/guide.html Process: 16846 ExecStart=/usr/sbin/slapd -u ldap -h ${SLAPD_URLS} $SLAPD_OPTIONS (code=exited, status=0/SUCCESS) Process: 16817 ExecStartPre=/usr/libexec/openldap/check-config.sh (code=exited, status=0/SUCCESS) Main PID: 16849 (slapd) CGroup: /system.slice/slapd.service └─16849 /usr/sbin/slapd -u ldap -h ldapi:/// ldap:/// Oct 16 16:24:19 zabbix1 runuser[16835]: pam_unix(runuser:session): session opened for user ldap by (uid=0) Oct 16 16:24:19 zabbix1 runuser[16837]: pam_unix(runuser:session): session opened for user ldap by (uid=0) Oct 16 16:24:19 zabbix1 runuser[16839]: pam_unix(runuser:session): session opened for user ldap by (uid=0) Oct 16 16:24:19 zabbix1 runuser[16839]: pam_unix(runuser:session): session closed for user ldap Oct 16 16:24:19 zabbix1 runuser[16841]: pam_unix(runuser:session): session opened for user ldap by (uid=0) Oct 16 16:24:19 zabbix1 runuser[16843]: pam_unix(runuser:session): session opened for user ldap by (uid=0) Oct 16 16:24:19 zabbix1 slapd[16846]: @(#) $OpenLDAP: slapd 2.4.44 (May 16 2018 09:55:53) $ mockbuild@c1bm.rdu2.centos.org:/builddir/build/BUILD/openldap-2.4.44/openldap-2.4.44/servers/slapd Oct 16 16:24:19 zabbix1 slapd[16849]: slapd starting Oct 16 16:24:19 zabbix1 systemd[1]: Started OpenLDAP Server Daemon.
测试
[root@zabbix1 lib]# ldapsearch -x -b '' -s base '(objectclass=*)' namingContexts # extended LDIF # # LDAPv3 # base <> with scope baseObject # filter: (objectclass=*) # requesting: namingContexts # # dn: namingContexts: dc=test,dc=com # search result search: 2 result: 0 Success # numResponses: 2 # numEntries: 1
导入一些基本schema
默认已经导入了core.schema
[root@zabbix1 schema]# ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/cosine.ldif SASL/EXTERNAL authentication started SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth SASL SSF: 0 adding new entry "cn=cosine,cn=schema,cn=config" [root@zabbix1 schema]# ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/nis.ldif SASL/EXTERNAL authentication started SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth SASL SSF: 0 adding new entry "cn=nis,cn=schema,cn=config" [root@zabbix1 schema]# ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/inetorgperson.ldif SASL/EXTERNAL authentication started SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth SASL SSF: 0 adding new entry "cn=inetorgperson,cn=schema,cn=config"
创建用户
[root@zabbix1 ~]# cat base.ldif dn: dc=test,dc=com o: ilan com dc: test objectClass: top objectClass: dcObject objectclass: organization dn: cn=root,dc=test,dc=com cn: root objectClass: organizationalRole description: Directory Manager dn: ou=People,dc=test,dc=com ou: People objectClass: top objectClass: organizationalUnit dn: ou=Group,dc=test,dc=com ou: Group objectClass: top objectClass: organizationalUnit [root@zabbix1 ~]# ldapadd -x -w "1234qwer" -D "cn=root,dc=test,dc=com" -f /root/base.ldif adding new entry "dc=test,dc=com" adding new entry "cn=root,dc=test,dc=com" adding new entry "ou=People,dc=test,dc=com" adding new entry "ou=Group,dc=test,dc=com" [root@zabbix1 ~]# ldapadd -x -w "1234qwer" -D "cn=root,dc=test,dc=com" -f /root/user.ldif adding new entry "uid=test,ou=People,dc=test,dc=com" [root@zabbix1 ~]# cat user.ldif dn: uid=test,ou=People,dc=test,dc=com objectClass: inetOrgPerson objectClass: posixAccount objectClass: shadowAccount cn: test sn: test userPassword: 1234qwer loginShell: /bin/bash uidNumber: 10007 gidNumber: 10002 homeDirectory: /home/test mail: test@test.com
查看结果
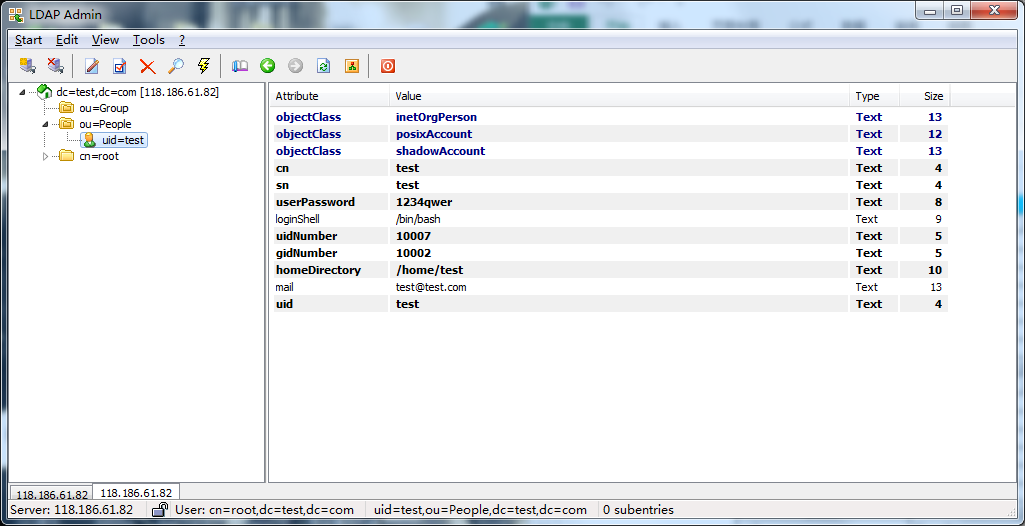
客户端工具为LDAP Admin