查看一下github地址,功能强大、且有丰富的插件、是动态调试程序的好工具,下面做一个调试CrackMe的尝鲜
An open-source binary debugger for Windows, aimed at malware analysis and reverse engineering of executables you do not have the source code for. There are many features available and a comprehensive plugin system to add your own. You can find more information on the blog!
简单写一个CrackMe
#include <stdio.h>
#include <Windows.h>
int main()
{
printf("请输入密码或注册码:");
TCHAR password[128];
_getws_s(password);
if (wcscmp(password, L"PASSWORD") == 0)
MessageBox(NULL, L"注册成功", L"CrakeMe", MB_OK);
else
MessageBox(NULL, L"注册失败", L"CrakeMe", MB_OK);
return 0;
}
编译生成exe
祭出x64dbg
1. 打开CrackMe,并向MessageBoxW设置断点
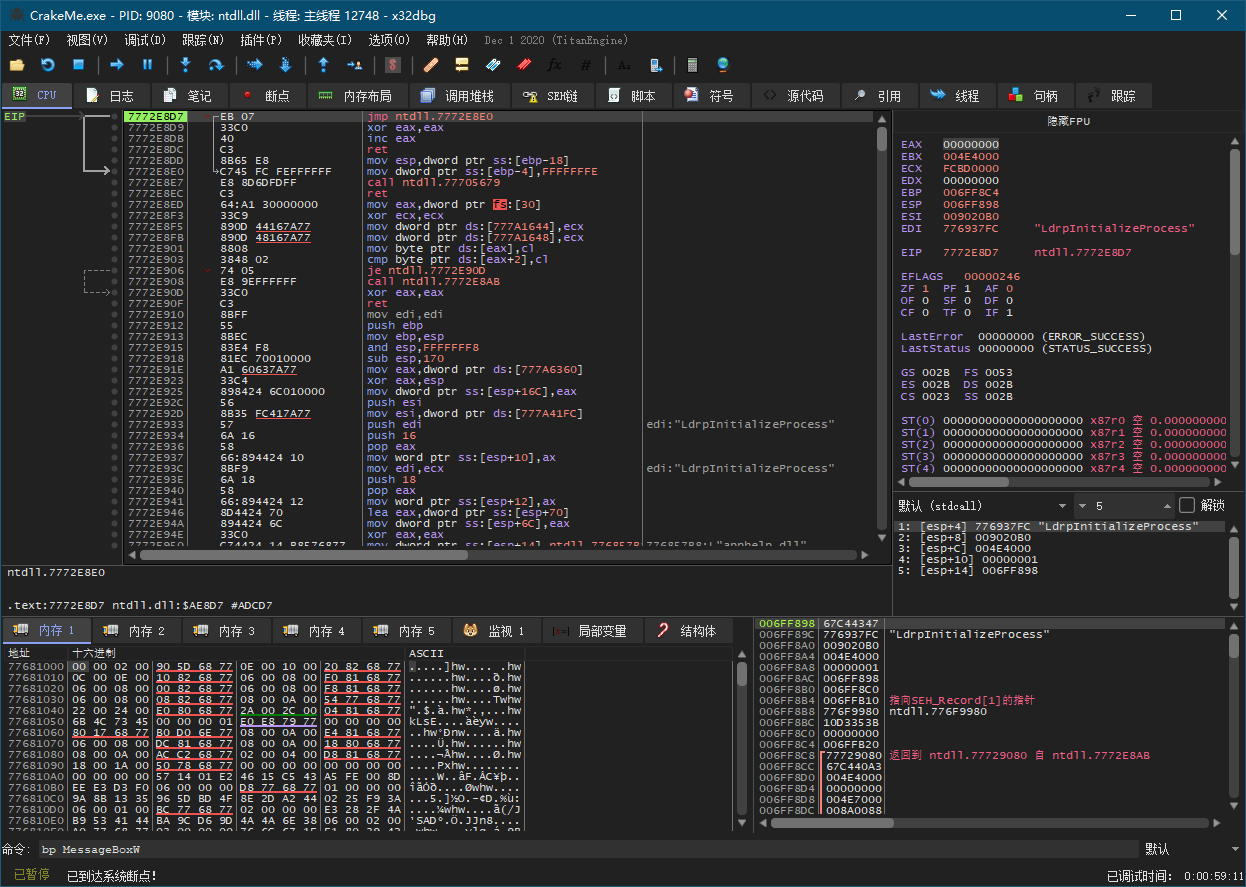
2. F9(运行),在CrackMe中随便输入内容并Enter,代码断点在调用MessageBoxW之前
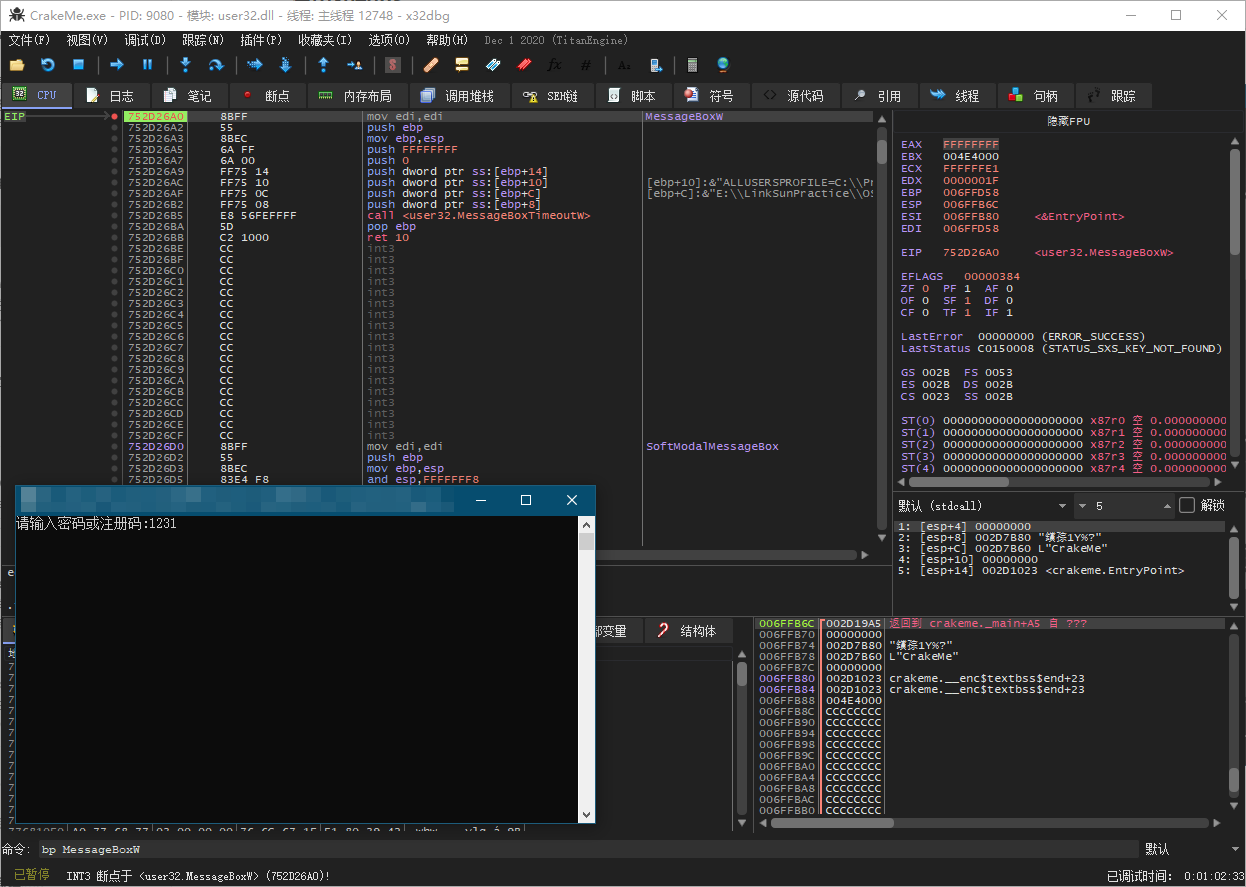
3. Enter进入用户代码,找到逻辑判断test eax eax,Space用nop填充

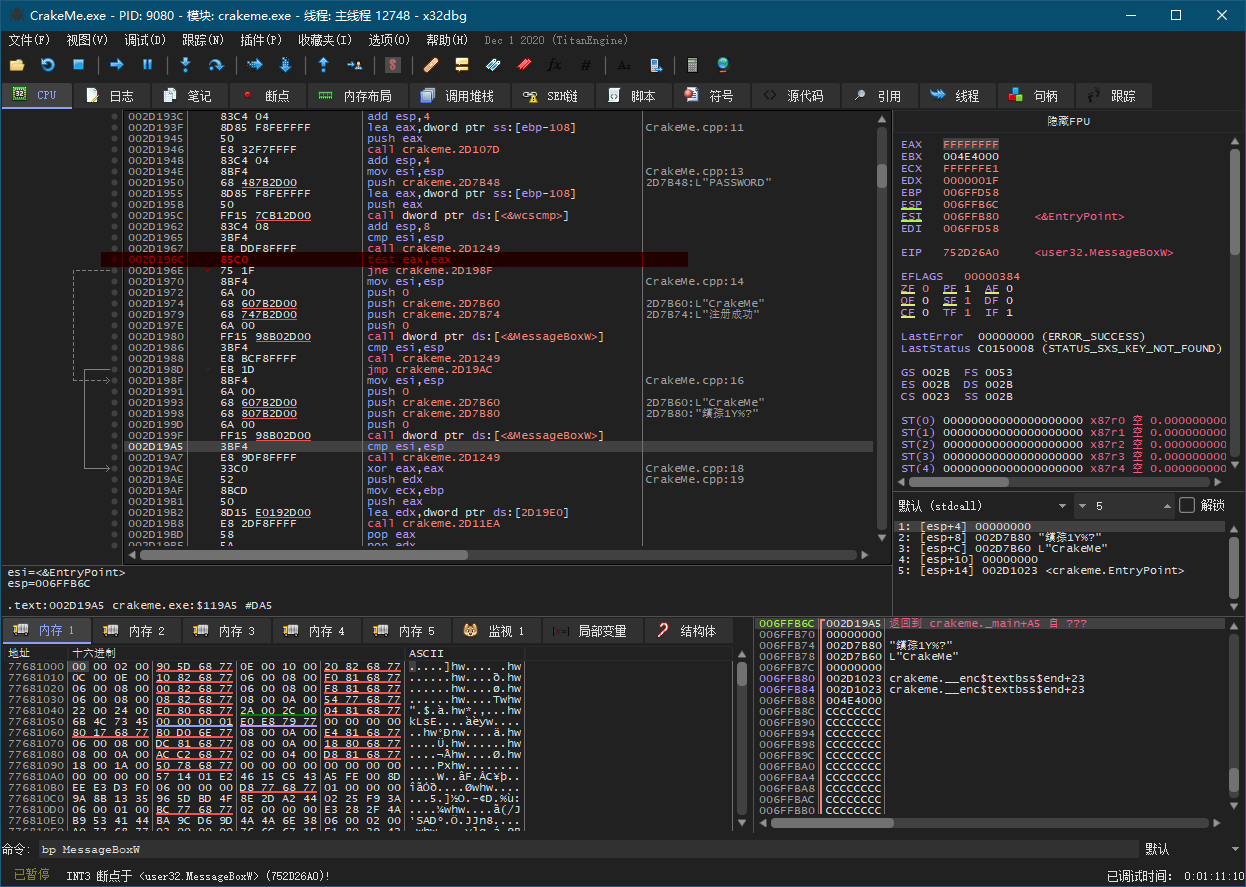
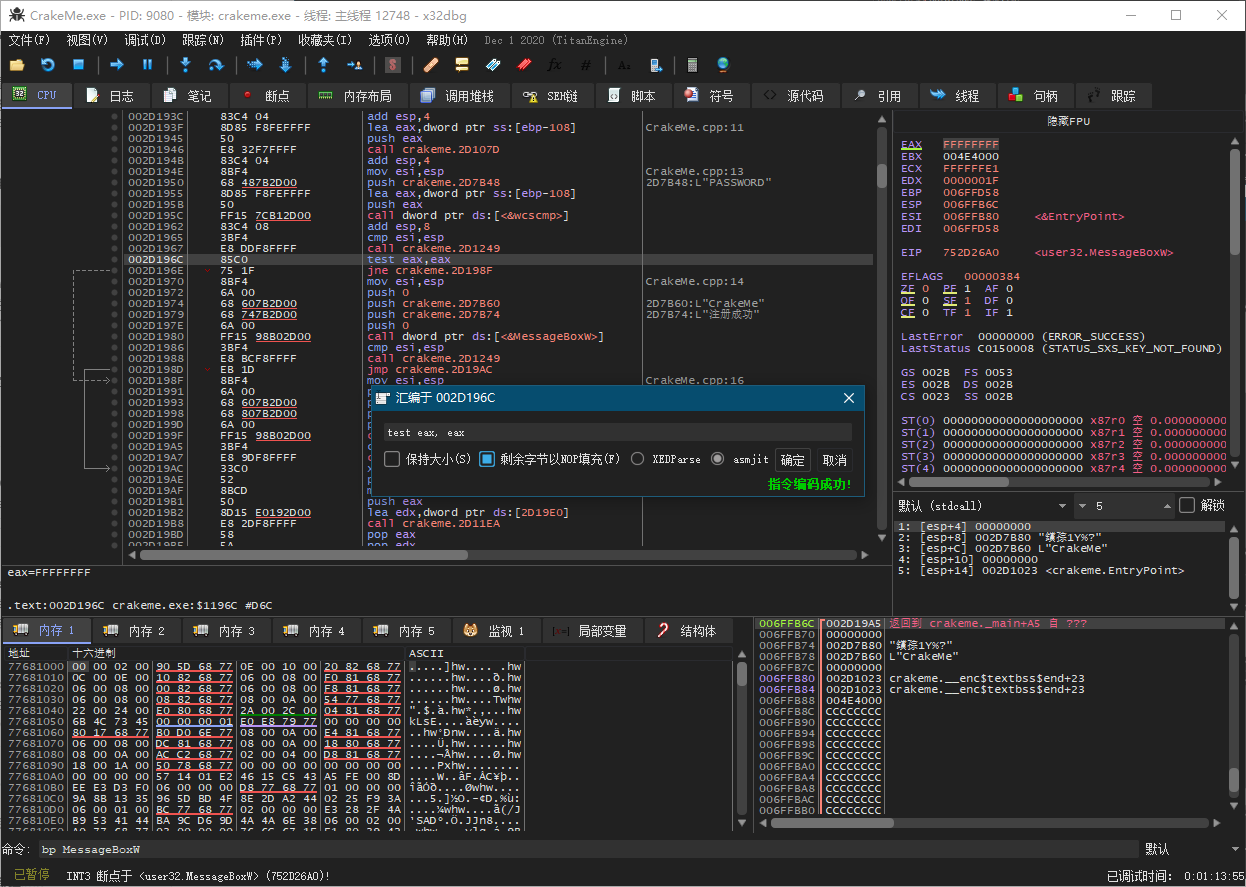
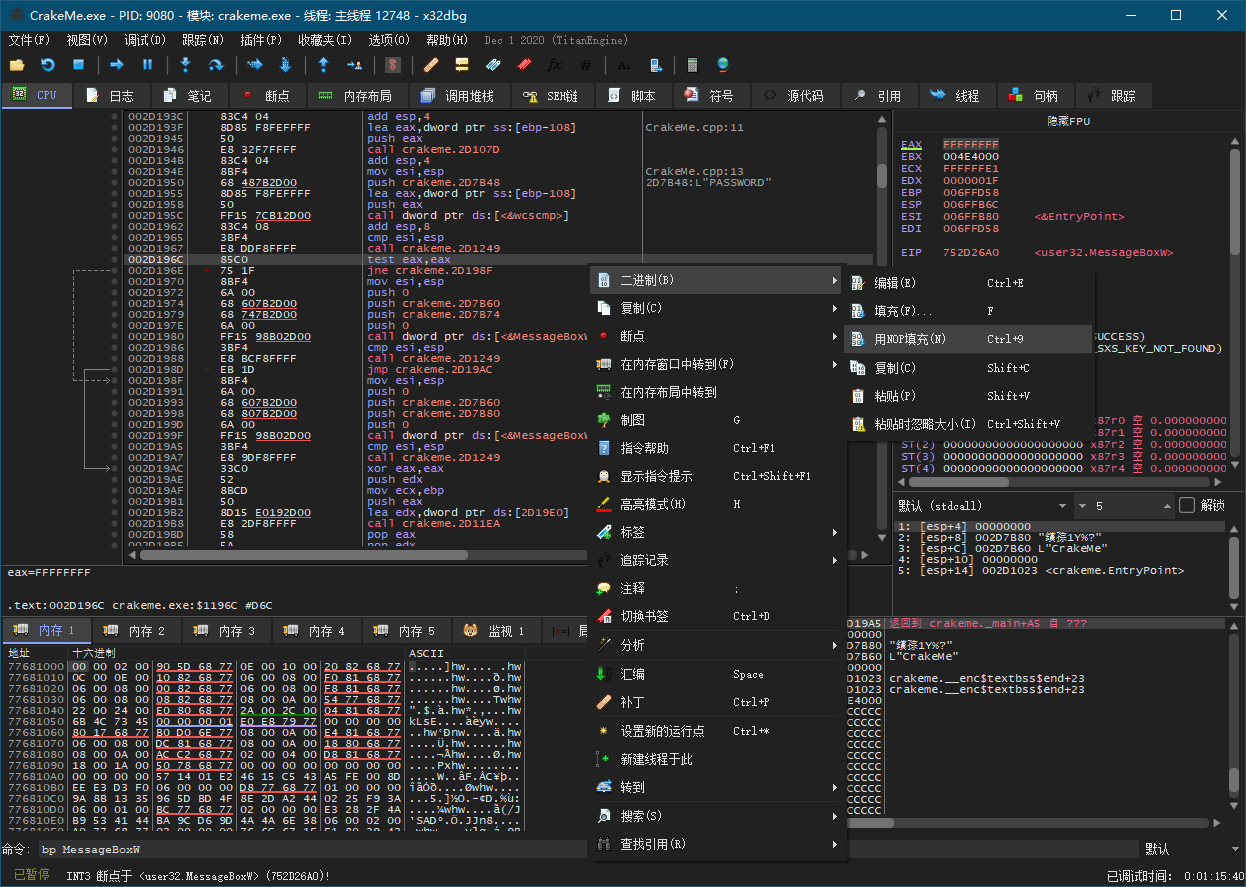
4. 保存修改到事先已复制的一个副本CrackMe - Cracked.exe
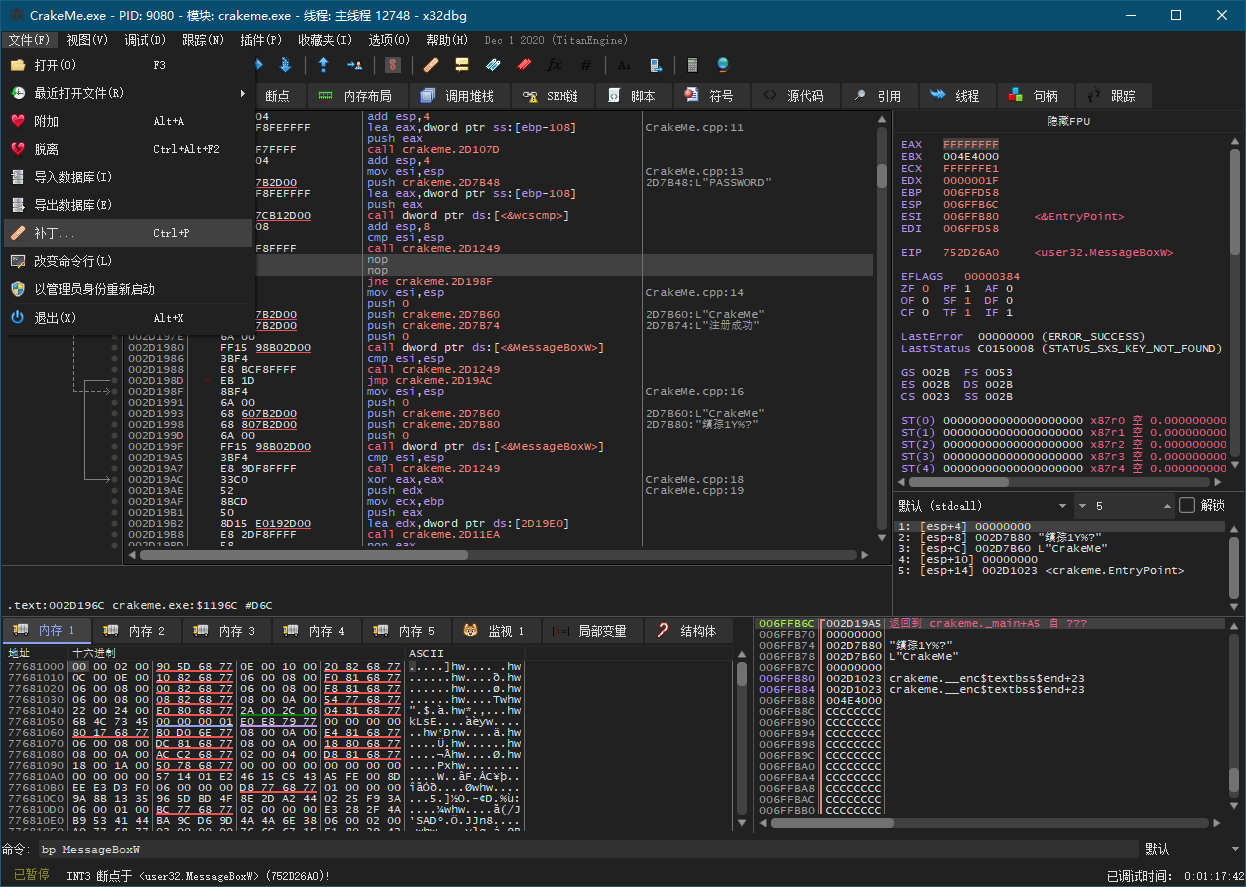
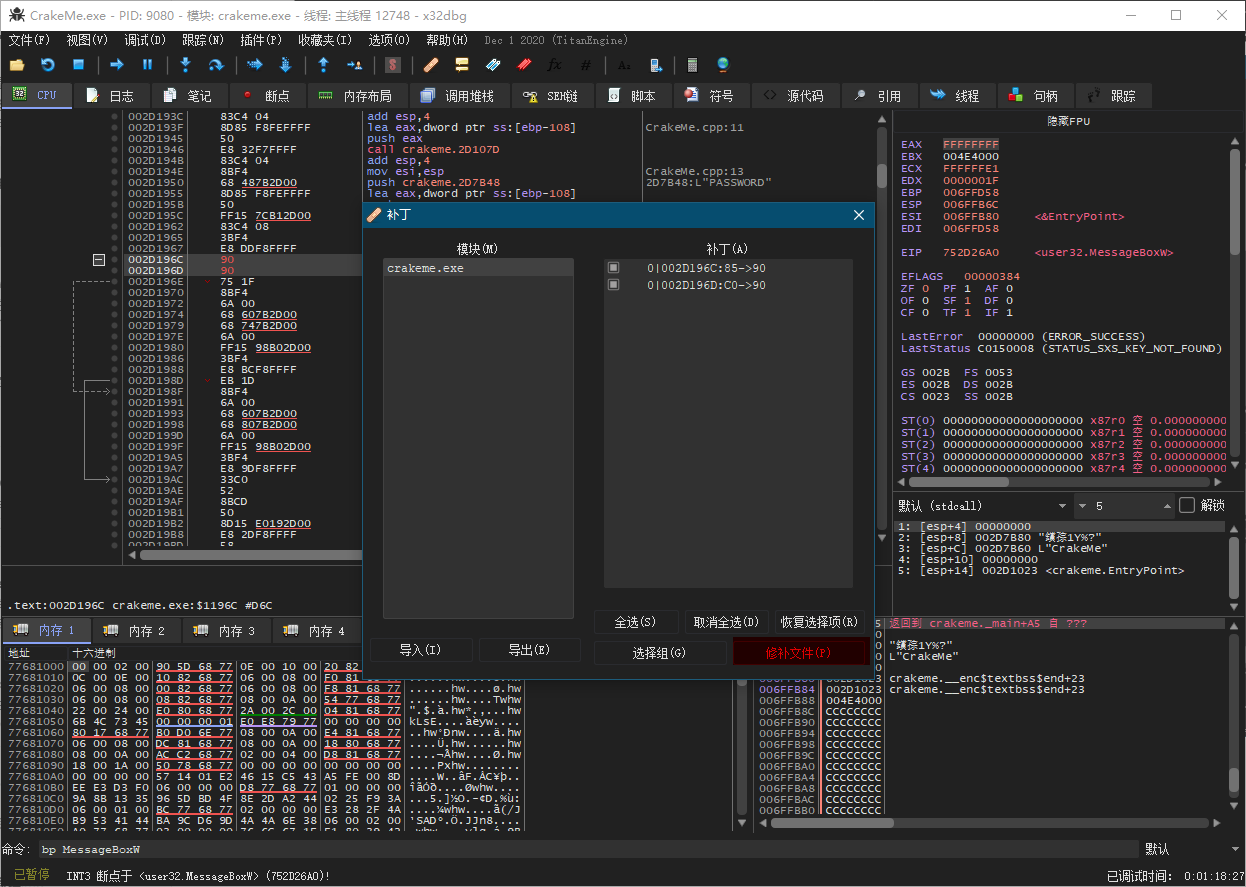
验证一下结果