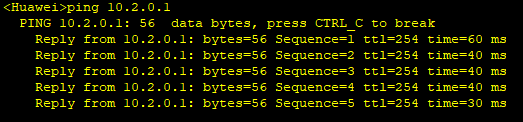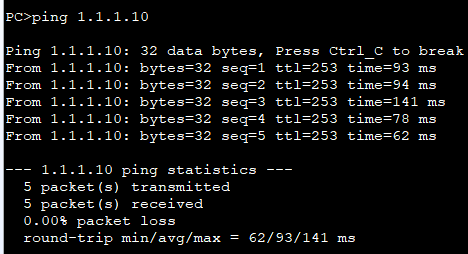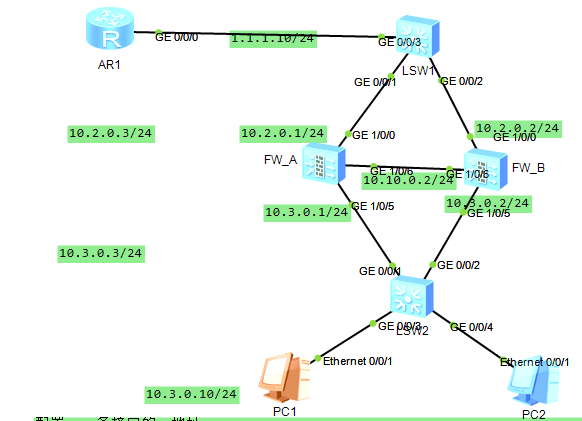
将FW_A各接口加入相应的安全区域
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/5
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/0
#
firewall zone dmz
set priority 50
add interface GigabitEthernet1/0/6
将FW_B各接口加入相应的安全区域
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/5
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/0
#
firewall zone dmz
set priority 50
add interface GigabitEthernet1/0/6
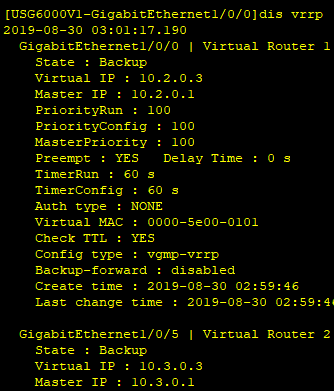
在FW_A上行业务接口GE1/0/0上配置VRRP备份组1,并设置其状态为Active
在FW_A下行业务接口GE1/0/5上配置VRRP备份组2,并设置其状态为Active
interface GigabitEthernet1/0/0
undo shutdown
ip address 10.2.0.1 255.255.255.0
vrrp vrid 1 virtual-ip 10.2.0.3 active
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
interface GigabitEthernet1/0/5
undo shutdown
ip address 10.3.0.1 255.255.255.0
vrrp vrid 2 virtual-ip 10.3.0.3 active
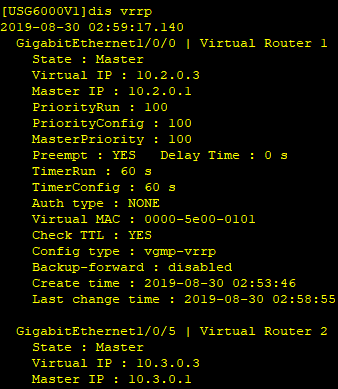
在FW_B上行业务接口GE1/0/0上配置VRRP备份组1,并设置其状态为Standby
在FW_B下行业务接口GE1/0/5上配置VRRP备份组2,并设置其状态为Standby
interface GigabitEthernet1/0/0
undo shutdown
ip address 10.2.0.2 255.255.255.0
vrrp vrid 1 virtual-ip 10.2.0.3 standby
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
interface GigabitEthernet1/0/5
undo shutdown
ip address 10.3.0.2 255.255.255.0
vrrp vrid 2 virtual-ip 10.3.0.3 standby
在FW_A上指定心跳口并启用双机热备功能。
hrp interface g1/0/6 remote 10.10.0.2(对端ip)
hrp enable

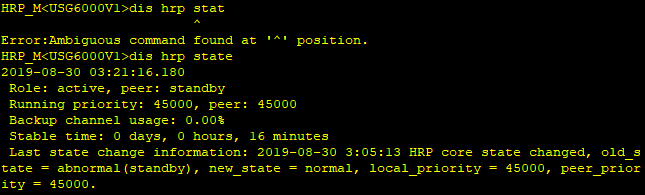
在FW_B上指定心跳口并启用双机热备功能。
hrp interface g1/0/6 remote 10.10.0.1
hrp enable

在FW_A上配置安全策略。双机热备状态成功建立后,FW_A的安全策略配置会自动备份到FW_B上
配置安全策略,允许内网用户访问Internet
HRP_M[USG6000V1]security-policy (+B)
HRP_M[USG6000V1-policy-security]dis this
2019-08-30 03:26:34.740
#
security-policy
rule name permit_trust_untrust
source-zone trust
destination-zone untrust
service icmp
action permit
在FW_A上配置NAT策略。双机热备状态成功建立后,FW_A的NAT策略配置会自动备份到FW_B上

nat address-group group1
section 0 1.1.1.2 1.1.1.5
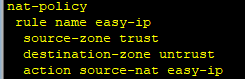
nat-policy
rule name policy_nat1
source-zone trust
destination-zone untrust
source-address 10.3.0.0 mask 255.255.0.0
action source-nat address-group group1
现在要求全网通:
AR1:
ip route-static 10.2.0.0 255.255.255.0 1.1.1.1
LSW1;
interface Vlanif100
ip address 1.1.1.1 255.255.255.0
#
interface Vlanif200
ip address 10.2.0.5 255.255.255.0
#
interface MEth0/0/1
#
interface GigabitEthernet0/0/1
port link-type access
port default vlan 200
#
interface GigabitEthernet0/0/2
port link-type access
port default vlan 200
#
interface GigabitEthernet0/0/3
port link-type access
port default vlan 100
ip route-static 0.0.0.0 0.0.0.0 1.1.1.10
FW_A:
interface GigabitEthernet1/0/0
undo shutdown
ip address 10.2.0.1 255.255.255.0
vrrp vrid 1 virtual-ip 10.2.0.3 active
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
#
interface GigabitEthernet1/0/5
undo shutdown
ip address 10.3.0.1 255.255.255.0
vrrp vrid 2 virtual-ip 10.3.0.3 active
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
#
interface GigabitEthernet1/0/6
undo shutdown
ip address 10.10.0.1 255.255.255.0
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/5
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/0
#
firewall zone dmz
set priority 50
add interface GigabitEthernet1/0/6
#
ip route-static 0.0.0.0 0.0.0.0 10.2.0.5
#
security-policy
rule name permit_trust_untrust
source-zone trust
destination-zone untrust
service icmp
action permit
rule name untrust_local
source-zone untrust
destination-zone local
service icmp
action permit
最后的nat策略 easy-ip:
LSW2:
interface GigabitEthernet0/0/1
port link-type trunk
port trunk allow-pass vlan 2 to 4094
#
interface GigabitEthernet0/0/2
port link-type trunk
port trunk allow-pass vlan 2 to 4094
#
interface GigabitEthernet0/0/3
port link-type trunk
port trunk allow-pass vlan 2 to 4094
#
interface GigabitEthernet0/0/4
port link-type trunk
port trunk allow-pass vlan 2 to 4094
AR1: