Cable TV Network
| Time Limit: 1000MS | Memory Limit: 30000K | |
| Total Submissions: 4690 | Accepted: 2170 |
Description
The interconnection of the relays in a cable TV network is bi-directional. The network is connected if there is at least one interconnection path between each pair of relays present in the network. Otherwise the network is disconnected. An empty network or a network with a single relay is considered connected. The safety factor f of a network with n relays is:
1. n, if the net remains connected regardless the number of relays removed from the net.
2. The minimal number of relays that disconnect the network when removed.
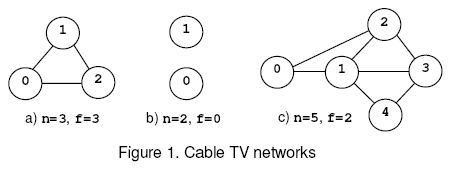
For example, consider the nets from figure 1, where the circles mark the relays and the solid lines correspond to interconnection cables. The network (a) is connected regardless the number of relays that are removed and, according to rule (1), f=n=3. The network (b) is disconnected when 0 relays are removed, hence f=0 by rule (2). The network (c) is disconnected when the relays 1 and 2 or 1 and 3 are removed. The safety factor is 2.
1. n, if the net remains connected regardless the number of relays removed from the net.
2. The minimal number of relays that disconnect the network when removed.

For example, consider the nets from figure 1, where the circles mark the relays and the solid lines correspond to interconnection cables. The network (a) is connected regardless the number of relays that are removed and, according to rule (1), f=n=3. The network (b) is disconnected when 0 relays are removed, hence f=0 by rule (2). The network (c) is disconnected when the relays 1 and 2 or 1 and 3 are removed. The safety factor is 2.
Input
Write a program that reads several data sets from the standard input and computes the safety factor for the cable networks encoded by the data sets. Each data set starts with two integers: 0<=n<=50,the number of relays in the net, and m, the number of cables in the net. Follow m data pairs (u,v), u < v, where u and v are relay identifiers (integers in the range 0..n-1). The pair (u,v) designates the cable that interconnects the relays u and v. The pairs may occur in any order.Except the (u,v) pairs, which do not contain white spaces, white spaces can occur freely in input. Input data terminate with an end of file and are correct.
Output
For each data set, the program prints on the standard output, from the beginning of a line, the safety factor of the encoded net.
Sample Input
0 0 1 0 3 3 (0,1) (0,2) (1,2) 2 0 5 7 (0,1) (0,2) (1,3) (1,2) (1,4) (2,3) (3,4)
Sample Output
0 1 3 0 2
Hint
The first data set encodes an empty network, the second data set corresponds to a network with a single relay, and the following three data sets encode the nets shown in figure 1.
Source
题意:
给出一张无向图,求其点连通度
点联通度:
最少去掉多少个点可以使得无向图不联通,貌似这道题规定如果ans=n-1输出n...
分析:
网络流的点边转化:把点拆成两个点,中间连一条边,记录点的信息
我们枚举一个源点一个汇点,然后对于每个非源汇点从入点到出点连一条容量为1的边,源点汇点出入点之间的边为inf,然后对于原图中的边(u,v),我们从u的出点向v的入点连一条容量为inf的边,然后可以建一个超级源点一个超级汇点,超级源点向源点的入点连边,汇点的出点向超级汇点连边...
代码:

1 #include<algorithm> 2 #include<iostream> 3 #include<cstring> 4 #include<cstdio> 5 //by NeighThorn 6 #define inf 0x3f3f3f3f 7 using namespace std; 8 //大鹏一日同风起,扶摇直上九万里 9 10 const int maxn=200+5,maxm=maxn*maxn*2+5; 11 12 int n,m,S,T,cnt,hd[maxn],to[maxm],fl[maxm],mp[maxn][maxn],nxt[maxm],pos[maxn]; 13 14 inline void add(int s,int x,int y){ 15 fl[cnt]=s;to[cnt]=y;nxt[cnt]=hd[x];hd[x]=cnt++; 16 fl[cnt]=0;to[cnt]=x;nxt[cnt]=hd[y];hd[y]=cnt++; 17 } 18 19 inline bool bfs(void){ 20 memset(pos,-1,sizeof(pos)); 21 int head=0,tail=0,q[maxn]; 22 q[0]=S,pos[S]=0; 23 while(head<=tail){ 24 int top=q[head++]; 25 for(int i=hd[top];i!=-1;i=nxt[i]) 26 if(pos[to[i]]==-1&&fl[i]) 27 pos[to[i]]=pos[top]+1,q[++tail]=to[i]; 28 } 29 return pos[T]!=-1; 30 } 31 32 inline int find(int v,int f){ 33 if(v==T) 34 return f; 35 int res=0,t; 36 for(int i=hd[v];i!=-1&&f>res;i=nxt[i]) 37 if(pos[to[i]]==pos[v]+1&&fl[i]) 38 t=find(to[i],min(fl[i],f-res)),fl[i]-=t,fl[i^1]+=t,res+=t; 39 if(!res) 40 pos[v]=-1; 41 return res; 42 } 43 44 inline int dinic(void){ 45 int res=0,t; 46 while(bfs()) 47 while(t=find(S,inf)) 48 res+=t; 49 return res; 50 } 51 52 signed main(void){ 53 while(scanf("%d%d",&n,&m)!=EOF){ 54 memset(mp,0,sizeof(mp)); 55 int ans=inf;S=0,T=n*2+1; 56 for(int i=1,x,y;i<=m;i++) 57 scanf(" (%d,%d)",&x,&y),x++,y++,mp[x][y]=1; 58 for(int i=1;i<=n;i++) 59 for(int j=1;j<=n;j++) 60 if(i!=j){ 61 memset(hd,-1,sizeof(hd));cnt=0; 62 for(int x=1;x<=n;x++) 63 if(x!=i&&x!=j) 64 add(1,x,x+n); 65 for(int x=1;x<=n;x++) 66 for(int y=1;y<=n;y++) 67 if(mp[x][y]) 68 add(inf,x+n,y),add(inf,y+n,x); 69 add(inf,i,i+n),add(inf,j,j+n),add(inf,S,i),add(inf,j+n,T);ans=min(ans,dinic()); 70 } 71 if(ans>=inf) 72 ans=n; 73 printf("%d ",ans); 74 } 75 return 0; 76 }//Cap ou pas cap. Cap.
By NeighThorn
