What chances do you think to acquire suspect's data from his/her iDevice? If suspects also use iTunes or iCloud, I will say it's in the bag.
What's inside a seized iPhone? Suspect refused to tell us and he was very confident that no one could unlock his iPhone.

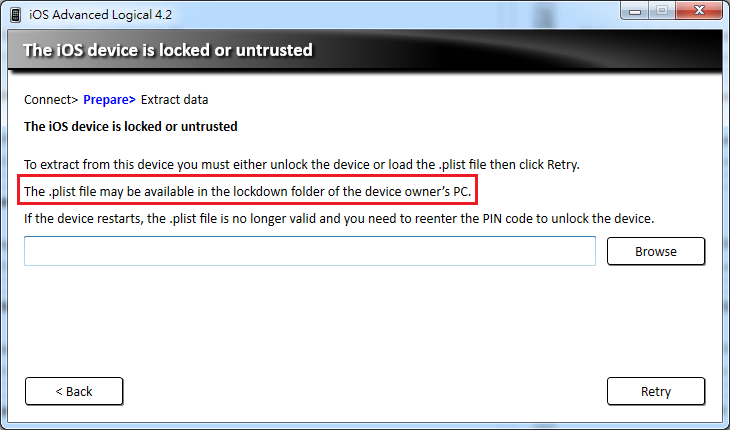
Fortuneately we got suspect's Laptop and found our best friend "iTunes". Why iTunes is our best friend? Because when you connect your iDevice to the PC/Mac/laptop with iTunes installed, iTunes will sync and backup data from iDevice. The "secret" is the plist in the lockdown folder. If you got this plist of suspect's iDevice, you could take advantage of it to establish "Trust" relationship between your forensic workstation and suspect's iDevice. Of course a plist file corresponds to certain iDevice.

Copy those plist files to the lockdown folder on forensic workstation, and connect suspect's iPhone to the forensic workstation. The Magic works~ You don't have to press any buttion on that iPhone. The "Trust" relationship is already there. Now we could use iTunes to backup data from suspect's iPhone, and we don't need to unlock supsect's iphone. After backup completed, you could got everything in suspect's iPhone now.

Congraulations!!! Even you don't have any forensic tools, you could use iTunes to restore that backup file to another iPhone. So you will know whether there is any clue or not.
Never doubt that~ Even you use commercial mobile forensic tool, the secret is still the plist file.